
Earlier this year we started a Friday round-up of the most important cyber news occurring each week, focusing on stories that fell into one of three broadly defined categories: good news that boded well for the industry and users, bad news that reflected the impact of attacks, hacks and vulnerabilities on enterprise and end users, and, of course, the ugly: avoidable failures, controversial decisions and unfortunate circumstances. As we close out the year, let’s take a look at some of the highlights of our Good, the Bad and the Ugly digests. Here then, is the best, the worst, and the ugliest in cybersecurity of 2019.
The Best
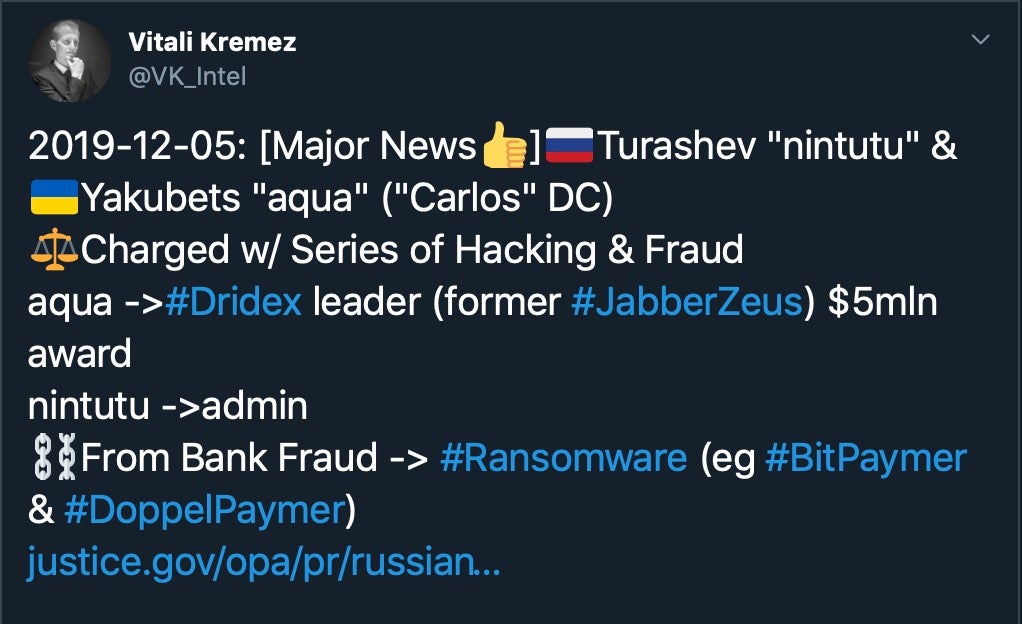
There’s been some great news in cybersecurity this year, from the establishment of the offensive Cybersecurity Directorate (Wk30) to botnet (Wk40) and RAT (Wk49) platform takedowns. The identification of two men behind the notorious Dridex malware (Wk49) and the sentencing of criminals behind the Bayrob (Wk50) scam and those responsible for GozNym malware (Wk52) are all good news for cyber security going into 2020.
The good cause should be further enhanced by the uptick in investment in businesses providing cybersecurity solutions (Wk29, Wk32), a trend that looks set to continue this coming year.
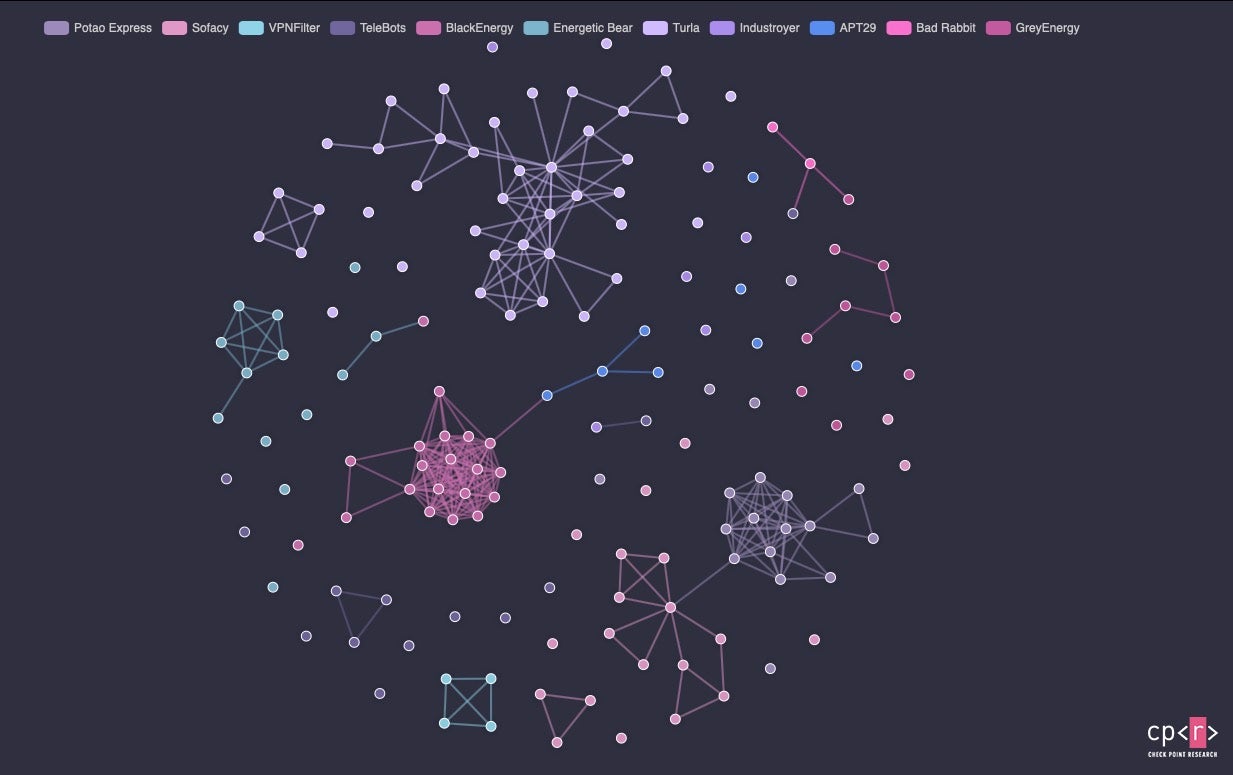
But perhaps the best news for enterprise and end users alike has been the expansion of bug bounty programs by the major players, which should lead to improved security across many of the main digital products and services we all use and rely on. Microsoft announced the Edge Insider Bounty Program (Wk34) just a week before Google (Wk35) initiated a new program to reward the reporting of data abuse issues in Android apps. Apple promised to open up its iOS bug bounty program to all (Wk32) as well as offer a macOS bug bounty program for the first time; the company delivered on those promises just in the nick of time (Wk51). Also worth mentioning among the good news was the publication of an interactive Russian APT map (Wk39), which if nothing else is perhaps the prettiest of all the good news we saw in 2019!
The Worst
Inevitably, there was plenty of bad news this past year, too. BlueKeep (Wk31) and a universal Windows privilege escalation (Wk33) had enterprises on high alert. Thankfully, the predictions of another Eternalblue/Wannacry meltdown have not come to pass, thus far. But that isn’t to say the danger is behind us with so many vulnerable devices still out there.
There’s no doubt that this year we’ve covered more stories regarding ransomware than any other topic (Wk34, Wk35, Wk41, Wk44, Wk45, Wk49, Wk52), and among those Ryuk (Wk36, Wk37, Wk40, Wk47, Wk52) has been the most rampant, with RobinHood (Wk30), Sodinokibi (Wk35) and Maze (Wk46, Wk52) ransomware variants also causing havoc across public and private organizations in the US and abroad. As ransomware as a service continues to spread and make the threat available to a wider, less-technical, criminal audience, it only looks like 2020 will see more of the same.
But perhaps the worst thing we saw this year was the attack on the Kudankulam Nuclear Power Plant in India (Wk44). The sheer recklessness of attacking nuclear power plants, whose safe operation is critical to the safety and health of the entire world, presents the gravest of threats to us all.

Image Credit: indiawaterportal.org/The Kudankulam Nuclear Power Plant (KKNPP)/Wikimedia Commons
The Ugliest
Things got ugly for Samsung this year when a bug in their fingerprint reader in the Galaxy S10 (Wk42) allowed anyone to bypass it with a clear piece of plastic. Nord VPN (Wk43) were also widely criticized not only for weak security that allowed hackers free reign inside servers belonging to the virtual private network provider but also for failing to disclose the breach to clients for over 18 months. Fortinet, who were targeted by a Chinese APT (Wk36), were also on the receiving end of some harsh comments after it emerged (Wk48) that the company hardcoded an encryption key into several of its products and also failed to fix the bug for a year and a half.
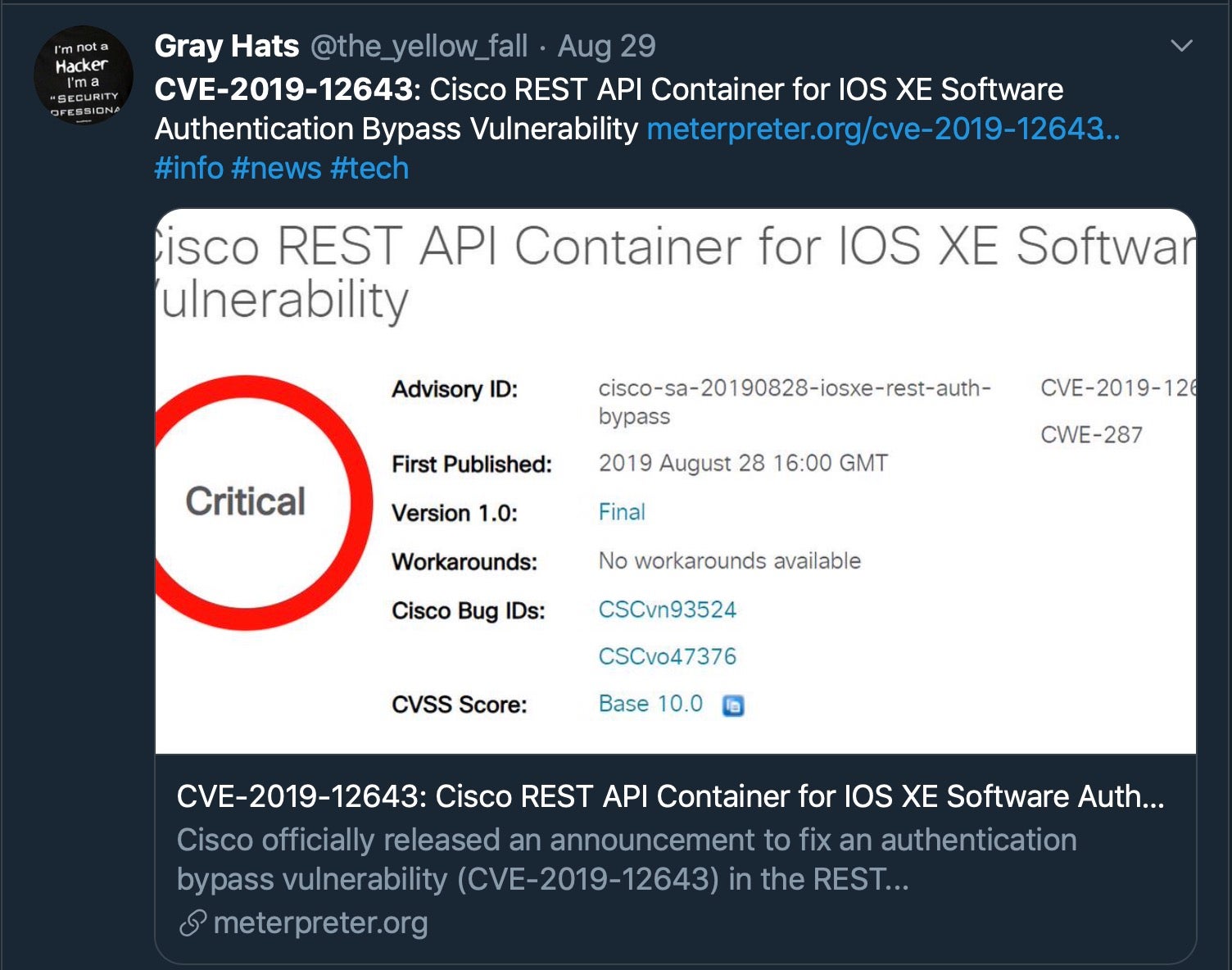
Perhaps the company that’s had the ugliest of cyber security times in 2019 was Cisco. Awarded a 10/10 for severity on the Common Vulnerability Scoring System (CVSS), CVE-2019-12643 (Wk35) allows malicious HTTP requests to bypass authentication and gives attackers the ability to login and execute privileged actions. In more bad news for the company, but good news for corporate whistleblower James Glen, the company were penalized to the tune of $8m (Wk31) by US courts under the False Claims Act after being found guilty of shipping products with known vulnerabilities for several years. Finally, Cisco look set to face challenging times doing business in mainland China after new cybersecurity laws were passed (Wk31) in Beijing putting restrictions on the purchase of US networking equipment, data storage and ‘critical information infrastructure’ hardware. One can only hope for both Cisco and the millions who rely on their products that 2020 will be a better year all round.
Coming Next…
That’s it for this year, but of course, we’ll be back in 2020 with a new series of the Good, the Bad and the Ugly, starting on Friday 3rd, January. Follow us on LinkedIn, Twitter, YouTube or Facebook or sign up for our weekly Blog newsletter and receive these posts right in your inbox. Until then, from all of us at SentinelOne, have a happy and secure New Year 2020!

