The Good
Drupal have patched a critical bug that could let hackers take over sites powered by the popular, open-source web content management platform. The vulnerability, CVE-2019-6342, only affects Drupal 8.7.4, and only when the experimental Workspaces module is enabled. Although there’s no known exploit for this vulnerability to date, updating to version 8.7.5 is strongly recommended.
The first half of 2019 saw record investment in Israeli tech companies reaching a record-breaking $3.9 billion. The three biggest deals, leading the way in a total of 250 deals that attracted investors in the first six months of 2019, were with firms Lemonade, Monday, and SentinelOne.
The Bad
According to a report by the FBI this week, Business Email Compromises are on the rise, with cybercriminals raking in as much as $300 million last year alone, a figure that’s three times the amount stolen just two years ago. Top targets are manufacturing and construction businesses, commercial services and real estate outfits. Criminals typically pose as a customer or senior management and fool unsuspecting employees into paying phoney invoices or making other fraudulent wire transfers. Attackers use phishing campaigns and spyware to steal the data necessary to compromise email accounts.
There was also bad news for internet users in Kazakhstan this week, and a warning of a dangerous precedent that should worry us all. In an anti-privacy move, the government there has made it mandatory for all ISPs to use a national MITM Certificate Agency to intercept all encrypted HTTPS traffic. End users have been told to install a government-issued certificate authority on all devices and all browsers. Government-spying or necessary for national security? Where have we had that debate before…
The Ugly
Seems like Cylance found out the hard way this week something we’ve been saying for a long time. Next-Gen security solutions need to use a layered model that is updated frequently and not simply rely on one supposedly “killer” feature. The point was impressively proven by Australian researchers who easily tricked the Cylance engine into tagging a malicious file as benign simply by appending some strings to the end of a WannaCry sample. The benign strings caused the Cylance engine to give more weight to the appended strings and mis-categorize the ransomware as safe.
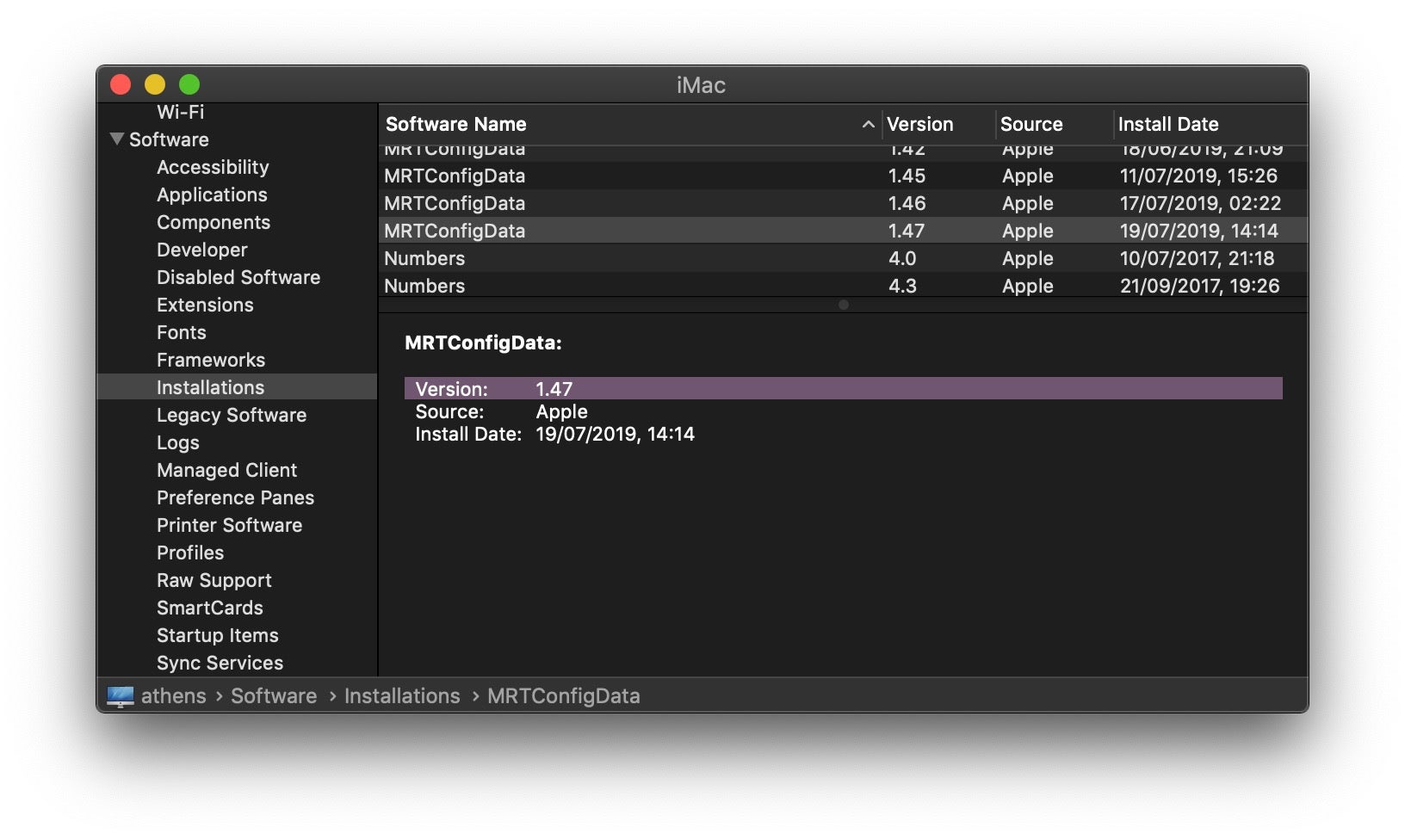
Continuing on from last week’s Zoom saga, Apple have since released TWO more updates for MRT.app in the last few days, in a continuing effort to nail the RCE vulnerability found to exist in many spin-off (White label) versions of the popular video conferencing app. If your head’s also in a bit of a spin trying to keep up with all these updates, you should (at the time of publishing this) currently be on v1.47. Here’s how to check from the command line:
system_profiler SPInstallHistoryDataType | grep -A4 MRTConfig
Alternatively, from the Apple menu, choose “About This Mac” and click the System Report button. Scroll down to Software > Installations, then type “MR” to find the start of the listing for MRTConfigData.
⬅️ Subscribe to our email digest and get a weekly email including similar news summary and other posts on the SentinelOne blog.


