The Good
Governments using mass surveillance to monitor and control the public is, unfortunately, no longer a theoretical fear born out of reading too much George Orwell, but something that is a fact of life for many. Good news for civil liberties, then, that California this week took a decisive step in favor of protecting citizens’ right to privacy by banning law enforcement officers from using facial recognition in body cams. Dragnet surveillance that is “the functional equivalent of requiring every person to show a personal photo id card at all times” was called out as “a violation of recognized constitutional rights” and can be used to track individuals and their personal associations without their consent. Aside from concerns about the use and security of massive databases cataloging the lives of law-abiding citizens, the bill also recognizes that facial recognition technology has a high rate of “false positives” that could pose elevated risks to people misidentified as someone else.
The Bad
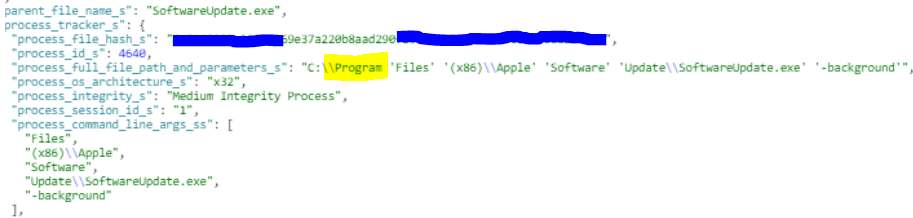
A Bonjour vulnerability allowed BitPaymer ransomware to target Windows machines that have, or once had, Apple’s iTunes or iCloud for Windows installed. The Bonjour updater used an unquoted string to specify the path to an executable in the C:\Program Files directory. Without quotes, the space in the path name causes the program to ignore the rest of the path after the space, and therefore to look for and execute anything at C:\Program. By placing a malicious executable at just that path, the attackers were able to manipulate the Bonjour updater to spawn their own code as a child process of a legitimate system process. That didn’t give the attackers elevated privileges, but it was enough to bypass certain types of legacy security solutions that whitelist execution chains of signed software. It just goes to show that whitelisting based on identity has a habit of coming back to bite you in the end.
There’s a kicker, too, for those that are feeling safe on account of having uninstalled the Apple apps in the past: even if iTunes and iCloud for Windows have been uninstalled, the device could still be vulnerable to the exploit as Bonjour is a different component and needs to be separately removed. For those that haven’t uninstalled the Apple programs and the Bonjour updater, updating iTunes or iCloud for Windows to the latest version will also patch the Bonjour vulnerability.
The Ugly
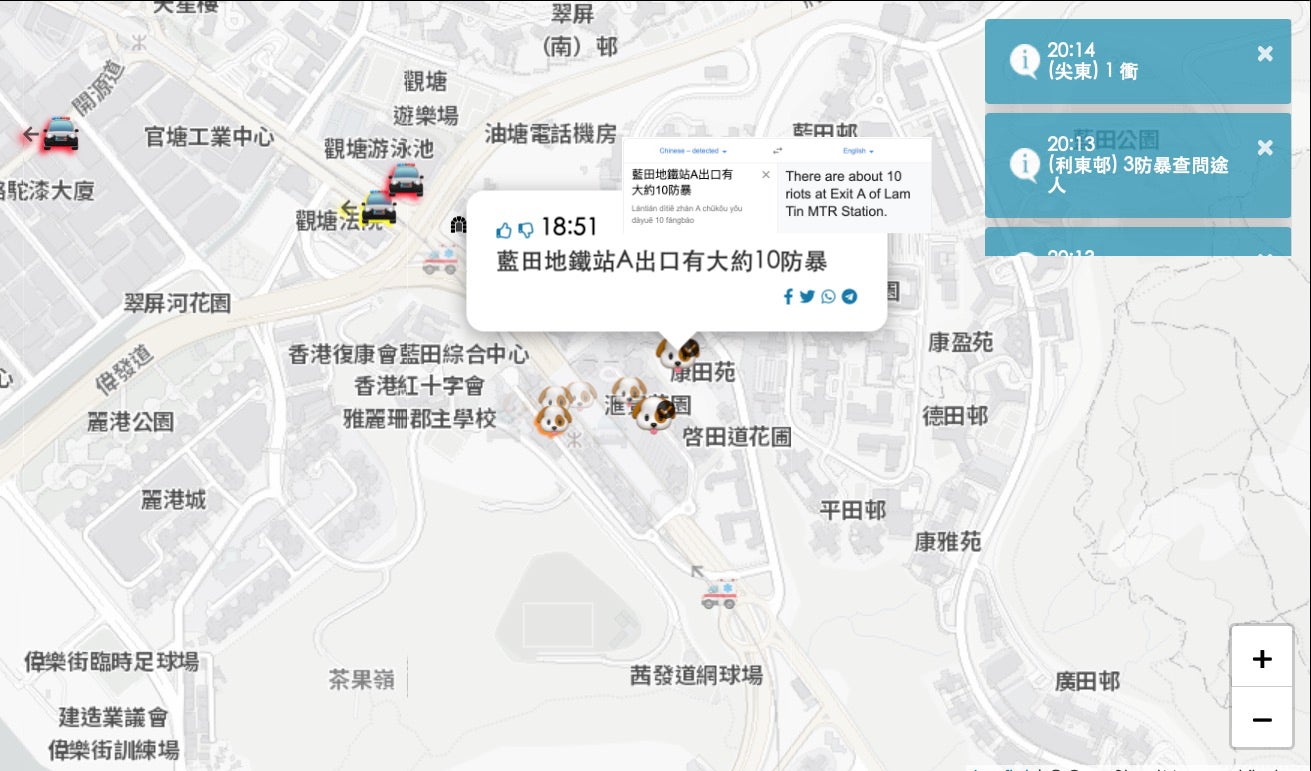
US companies have long had to tread a fine line when it comes to trading in China. After the Eastern superpower this week pressurized the NBA over its perceived support of Hong Kong protesters, Apple were next in line to feel the squeeze as the economic giant criticized the Californian tech company for hosting the HKmap.Live app on its App Store. Stating reasons widely disputed by protesters on the ground and in conflict with the app’s apparent functionality, Apple CEO Tim Cook pulled the app from the store, claiming it was being used to target individual police officers and to victimize residents. Banning the app, which has both an online and Android counterpart, is unlikely to have any real impact on the running battles between protesters and police, critics say. However, Apple’s willingness to cite uncorroborated claims from Hong Kong authorities as the reason for their decision has caused dismay among those who feel US companies bow a little too readily to Chinese censorship.