
The Good
Strong coordinated action was apparent this week when an international law enforcement operation targeted the sellers and users of the Imminent Monitor Remote Access Trojan (IM-RAT). The operation was led by the Australian Federal Police (AFP), with international activity coordinated by Europol and Eurojust, and resulted in disabling IM-RAT, which was used across 124 countries and sold to more than 14,500 buyers. IM-RAT can no longer be used by those who bought it. This insidious RAT, which was able to disable anti-virus, record keystrokes, steal data and passwords and watch the victims via their webcams, was sold for as little as $25 (!!!) per license. The takedown netted the developer, an IM-RAT employee and 13 of the most prolific users of this Remote Access Trojan (RAT), spanning the entire globe – Australia, Colombia, Czechia, the Netherlands, Poland, Spain, Sweden and the United Kingdom.
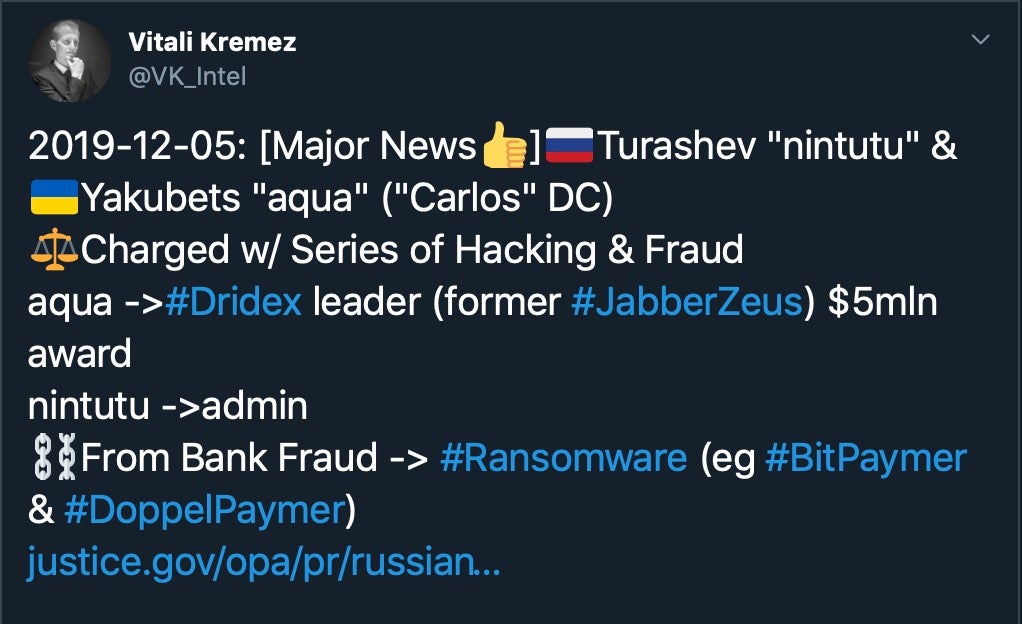
In what might turn out to be the biggest news in cybercrime of 2019, the FBI and US DoJ have named two individuals, Maksim Yakubets and Igor Turashev, as being behind the ‘Evil Corp’ hacking group responsible for distributing the Dridex banking trojan. Authorities have offered an unprecedented US $5m reward for information leading to the arrest of Yakubets, who is also thought to be behind the notorious Zeus banking malware. Yakubets is widely believed to be hiding in Russia, so prospects of an arrest any time soon remain slim.
The Bad
A targeted ransomware attack has hit one of America’s largest data center providers, CyrusOne, with the REvil (Sodinokibi) ransomware. Unlike other ransomware attacks that hit US entities this week – like the very “evil” attack that hit the Shakespeare Theatre in Madison causing it to cancel Wednesday night’s performance of Charles Dickens’ “A Christmas Carol” – the CyrusOne attack is more significant since it immediately impacts several downstream entities. The company’s initial assessment found that six MSPs (Managed Service Providers) suffered denial of service issues. Attacks that target service providers, often thought to have better security than smaller, less-technical companies, are more sophisticated and in the long run can proliferate and impact many client organizations.
The Ugly
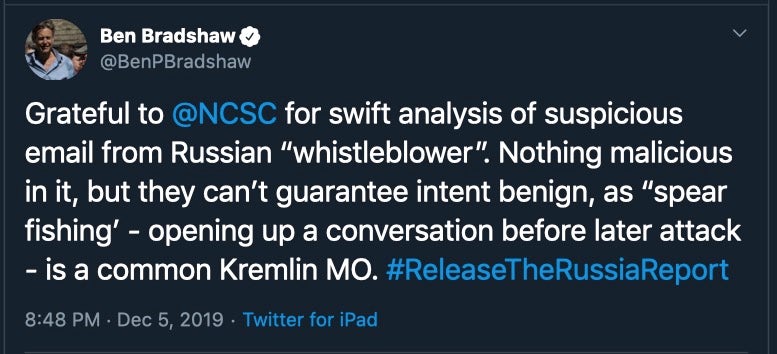
This week, Kremlin critic Ben Bradshaw (UK, Labour Party) claimed he was the target of a Russian cyber-attack after receiving a suspicious email from Moscow. According to a news story in the Guardian, the email – supposedly from a Russian whistleblower – contained a number of documents that appeared to be genuine. The files showed how the Kremlin had set up a secret “fake news unit” to suppress negative stories and boost pro-government sentiment in its far east region. The Guardian reported that Bradshaw had sent the documents to “cyber experts” for analysis and that they had confirmed two of the documents carried malicious code. However, subsequent analysis by the UK’s National Cyber Security Centre (NCSC) appears to have failed to find anything malicious.
Bradshaw himself seems to believe the email may have been just the opening shot in an attempt at gaining trust, and that his vigilance may have prevented a subsequent spear-phishing attack. We’d certainly agree with the need for caution when dealing with email attachments, by far the most common vector of malware infections for both individuals and organizations. Whether the British politician was really targeted or not, there’s no doubt that increasing meddling in political affairs through cybercrime is the ugly price of today’s wired world. Those tasked with protecting the integrity of the US 2020 election should be watching closely how the UK 2019 election unfolds.

