A short while back we posted a two-part blog series on a new RaaS (Ransomware as a Service) offering, “Project Root”. If you have not had a chance to peruse Part 1 and Part 2 of that series, we highly recommend doing so. That aside, “Project Root” happens to be just one of many in a recent uptick in “publicly” available RaaS offerings. In recent months, we have been tracking others as well and would like to take this opportunity to provide a high-level overview of three of the more notable examples, all of which market themselves with a style and pitch typical of legitimate consumer marketing. In this post, we will explore the following:
- Recoil Ransomware
- Cryptonite
- Ghostly (aka Ghostly Locker)

Recoil Ransomware
Recoil popped up for sale in various forums in early November 2019. Like Project Root, the main draw is a low buy-in price and a fairly standard feature set.

Early advertisements for Recoil touted the following:
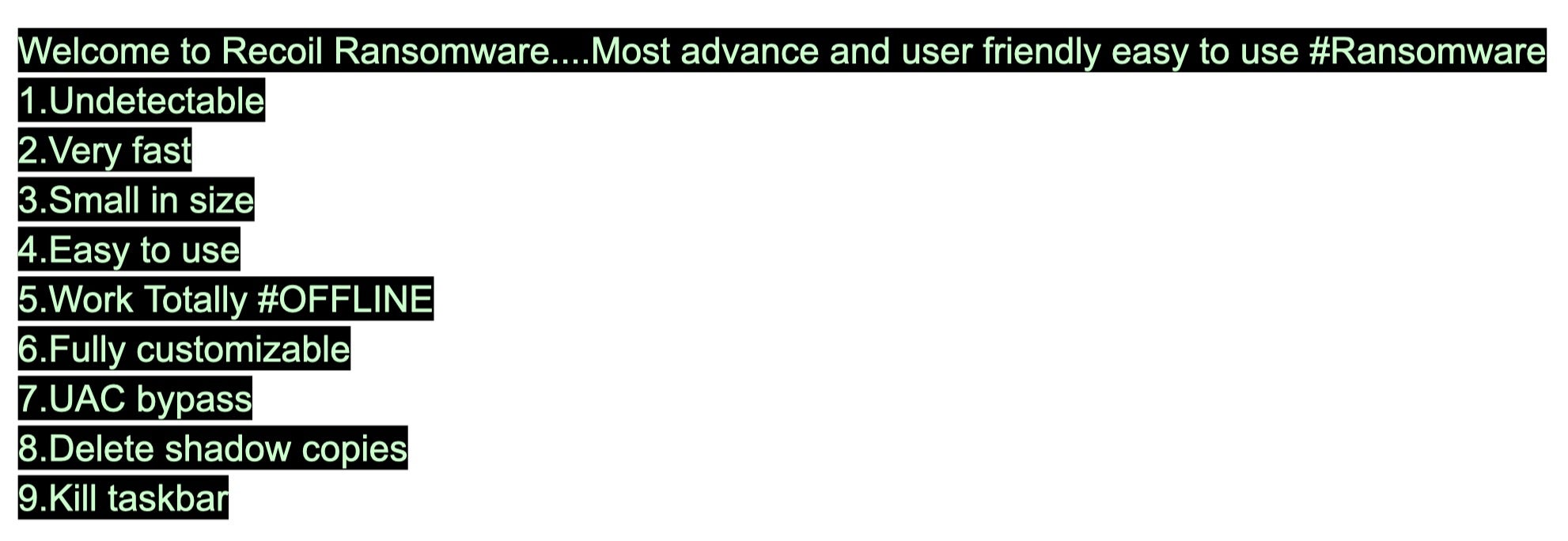
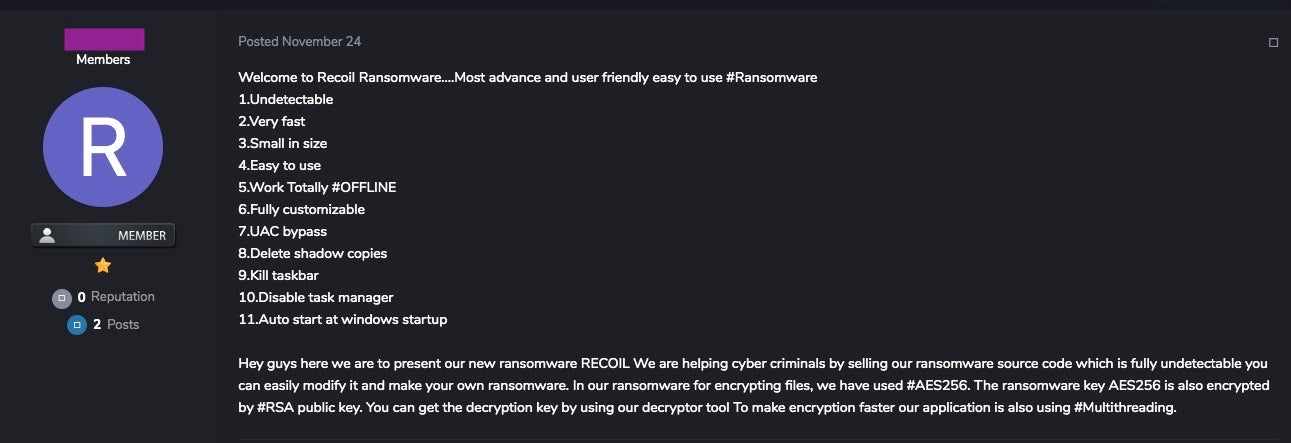
All these features are fairly standard for a modern RaaS service and should be taken with a healthy dose of scepticism. Claims to be “fully undetectable” (aka FUD) are misleading and only indicate two possible anti-detection capabilities. First, the developers can provide the buyer with a uniquely compiled stub that has yet to be subjected to public testing sites like VirusTotal. That means legacy AV solutions that rely on reputation for detection, such as by checking the binary’s hash, can indeed be easily bypassed. Second, some ransomware vendors offer to frequently update their code/stubs in order to stay ahead of the ‘detection curve’ – signature rules like Yara and similar that rely on detecting particular sequences of bytes or strings in an executable. However, neither of these avoidance techniques give the ransomware true “FUD” capabilities if the security solution uses advanced behavioural detection.
Recoil also offers the ability to function (i.e. encrypt) offline, which is attractive to criminals for a few reasons, not the least of which is that it can make the payloads less ‘noisy’. That is, if there is no anomalous traffic reaching out to obviously suspicious .onion sites, then simple security controls that would be triggered by that sort of thing (IPS/IDS/Firewalls, etc.) can fail to generate alerts. Beyond that, staying offline may offer some improvement in speed by forgoing network status checks or delays while reaching out to an attacker’s server each time the payload executes.
As stated, Recoil’s feature set is rather standard. The deletion of shadow copies is very common and can greatly impact a victim’s ability to recover from such an attack if they are not able to restore from another form of known-good backup or if they lack a modern security solution that blocks that behavour at source.
Current data indicates that Recoil supports Windows (x86 / x64) as well as Android. The developers are hoping to net $500.00 USD per sale, which – they say – includes support for Windows and Android platforms.
Cryptonite Ransomware

Cryptonite began advertising in forums (.onion based) a little later than Recoil, in early December 2019. They tout a fairly robust feature set, as well as a ‘deal’ to preview the system before committing to purchasing a full subscription package. By creating an account on their system, would-be ransomware criminals are able to get ‘preview’ builds which are fully functional. The idea here seems to be to offer the ability to generate income from the preview that the “buyers” would in turn use to pay for the full package.
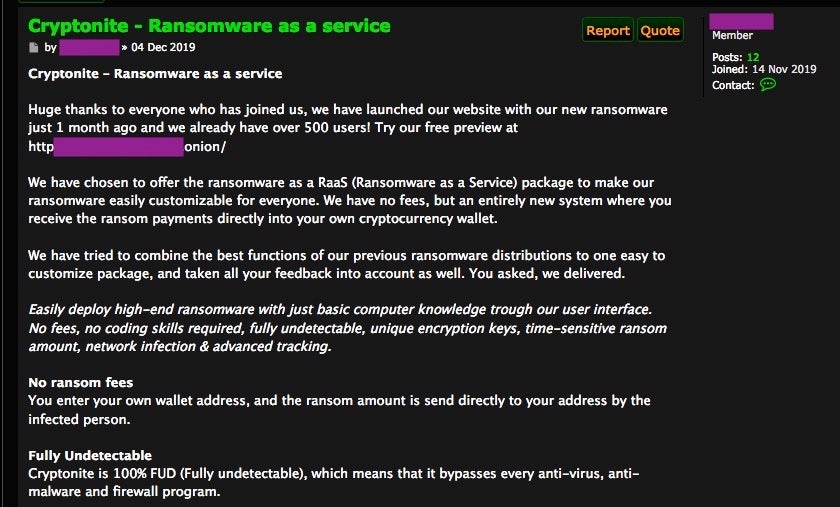
The developers behind Cryptonite also appear to be offering a special deal to the first 1000 customers. The marketing is somewhat fascinating (from a security research perspective) in that they are highlighting “features” which very much focus on the exact points that security professionals recognize as the most dangerous.
Specifically, they repeatedly highlight the point that “No Coding Skill” is required. That particular aspect is one of the main reasons we call attention to these. The barrier to entry is almost zero, meaning anyone tempted by criminal gains can rapidly cause a great deal of damage in very little time (seconds). The greatest danger with these kind of RaaS offerings is that an attacker only needs to know how to download files to start the infectious ball rolling.
Cryptonite is currently advertising the following core features:
-
-
-
- Zero ransom fees – Packages are based on “infection credits”
- Fully Undetectable – AV Evasion
- Unique Encryption Keys – Unique encryption keys for each infection. This aims to prevent decryption tools or use of leaked keys
- No Coding Skills Needed – Buyers build and download payloads from the portal. No programming / coding required
- Increasing Ransom – Ransom increases over time or per defined criteria
- Custom File infection (append your own binaries)
- VSS / Shadow Copy Disabling / Deletion – Attempts to delete Volume Shadow Copies to prevent OS-based remediation
- Network Infection Option – Worm’esque feature. Attempts to identify open network shares to spread to and infect.
- Windows Only (x86/x64)
-
-
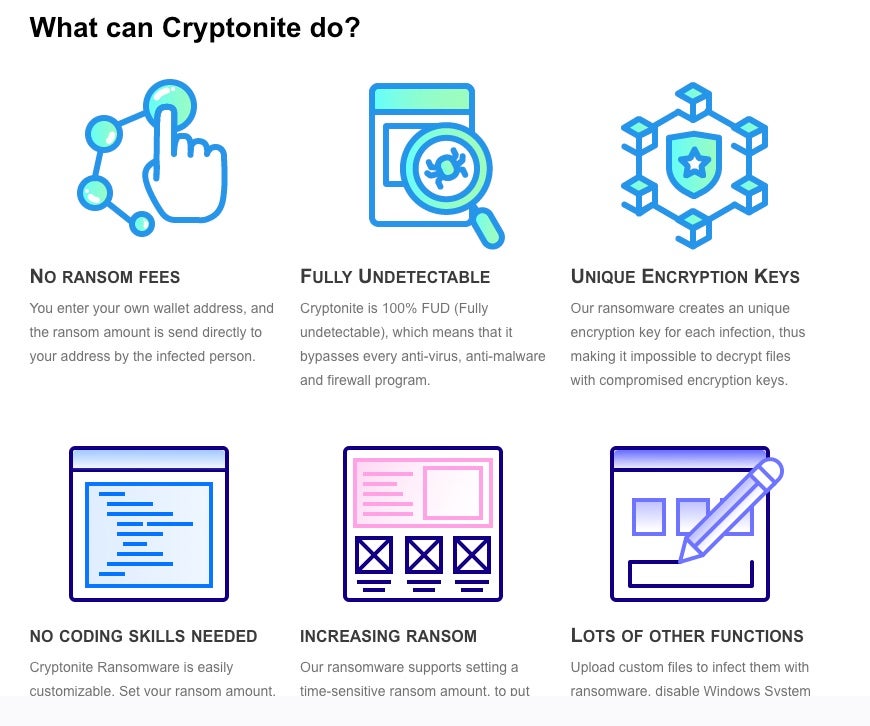
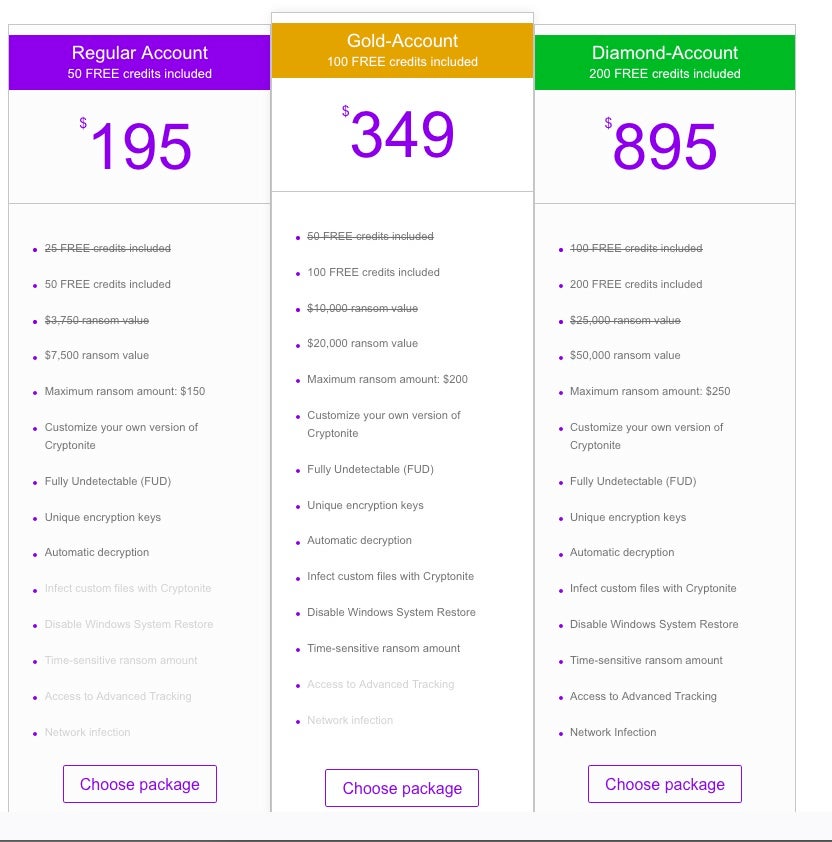
Cryptonite offers a full management and tracking portal and a number of features which put it ahead of Recoil in terms of attractiveness to a criminal audience. The pricing model is a little different with Cryptonite as well. Rather than taking a cut from each received ransom or charging an “entry fee”, they sell packages of what they refer to as “infection credits”. Each infected victim equals one credit. Would-be threat actors pay more for a package that allows them to infect more victims.
Cryptonite pricing currently ranges from $195.00 to $895.00 USD and sets a limit on the amount of ransom that can be demanded per victim in each tier, from $150 to $250. For that, would-be criminals can infect between 50 and 200 victims and potentially make between $7,500 – $50,000 in total.
The network infection and “advanced tracking” features are only included in the highest-price tier.
Along with all this, Cryptonite claims to offer 24×7 “support” via email, web-form, or even chat (when the admins are online).
Ghostly Locker Ransomware
Rounding out our overview of RaaS projects is Ghostly, aka Ghostly Locker, ransomware.

Ghostly first appeared for sale in mid-November 2019. Similar to Recoil and Cryptonite, it is presented as a very slick and full-featured offering.
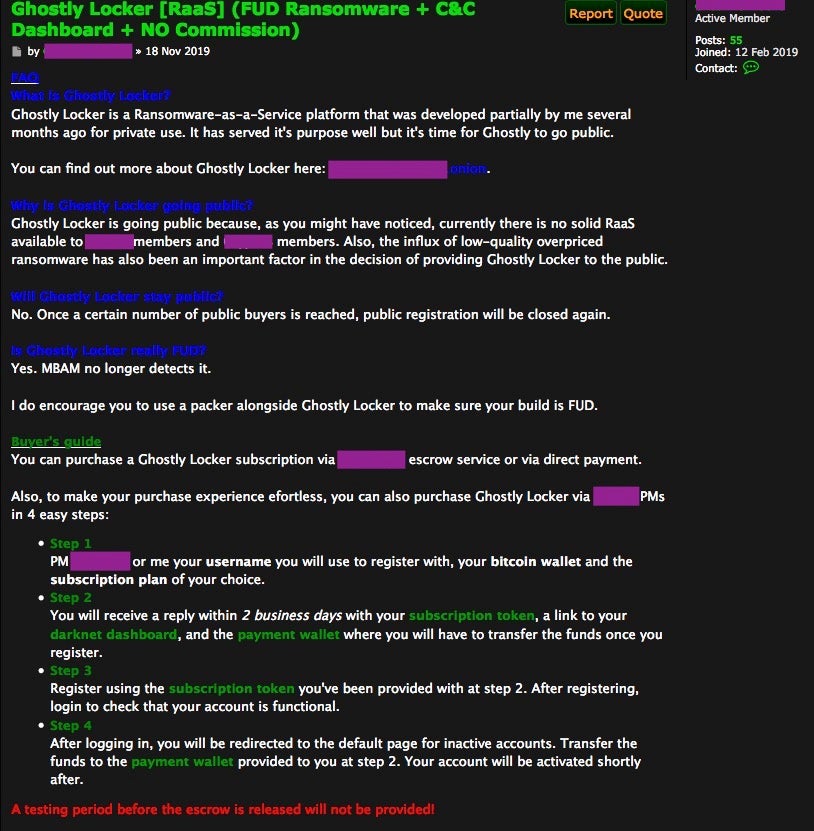
Currently, Ghostly Locker claims to provide the following primary feature set:
-
-
-
- Silent, Multi-Threaded Encryption
- Customizable Disk Encryption (full or partial)
- Customizable Target Extension List
- Automation of Client Payments
- Ransom Amount Doubling (after 72 hours)
- TOR Portal-based Infection Tracking and Management
- Detailed Campaign Statistics
- Windows Only Support (x86/x64)
- Purchase via Direct Payment (BTC) or Escrow via specific advertised forums.
-
-
Ghostly’s pricing model is more ‘traditional’ in that they require an up-front entry fee from those looking to buy ransomware. The more a buyer is willing to pay, the more features they are offered, as well as more time and greater volume of potential infections.
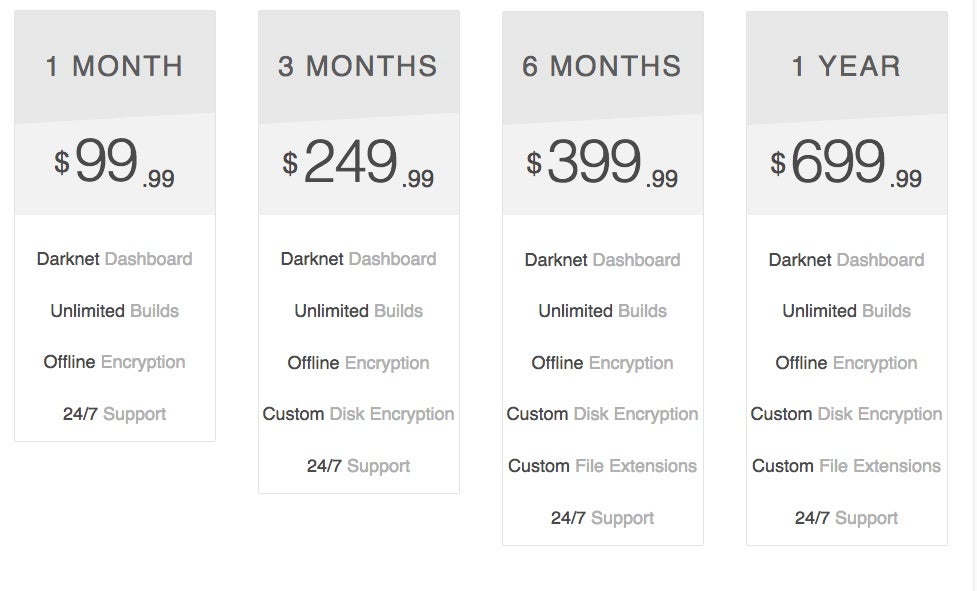
The Ghostly Locker FAQ provides further detail on specific features as well as information around their pricing plans and payment processing.
The Ghostly Locker dashboard is bloat-free and functional.
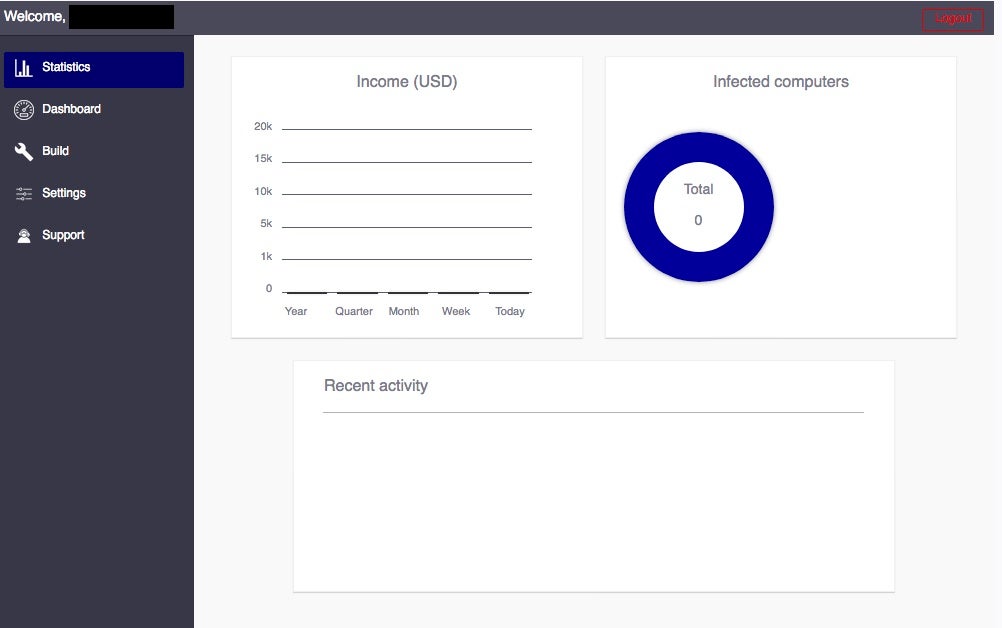
The ‘Build’ section is where the magic happens. Short and to the point, it does the job. The user has options to enter or update the payment bitcoin address, as well as the payment amount.
It is also possible to toggle between full or partial disk encryption. Full disk encryption is slower, and according to the RaaS developer, should be used “when you want to make sure that the files are never recovered.” They notably also state that Full Disk Encryption is “ideal for targeted campaigns”. Ghostly Locker claims to run though encryption on a disk in 1 minute, on average. This is common with most modern ransomware families. It takes very little time to do a great deal of damage. If you think you have a minute of two to adjust and avoid encryption, or if your EDR solution relies on cloud-lookups to convict bad behavior, that can become a problem, very quickly.
We will cover details on the payloads generated from Ghostly Locker in a separate, upcoming, blog post.
Conclusion
What is particularly concerning about this latest rash of ransomware projects is the way they borrow ideas from modern marketing practice in a clear effort to attract first-time buyers and to increase confidence among individuals who might otherwise have only been curious. When highly-skilled criminals are broadening their appeal to zero-skill, would-be villains with slick and seductive marketing tricks, it is a worrying sign that 2019’s wave of ransomware attacks looks likely not only to continue, but – if these kinds of RaaS campaigns are successful – threaten to become worse in 2020.
Whether the highly-skilled actors behind these kinds of projects are just themselves ordinary criminals or also have a vested interest in encouraging an increase in ransomware attacks for other purposes is an interesting question in light of our recent discovery of links between APTs and crimeware.
However that may be, SentinelOne’s on-device, endpoint protection is fully capable of preventing infection from Ghostly Locker, Recoil, Cryptonite and other forms of ransomware without reliance on cloud detection. Organizations that have moved beyond depending on legacy AV suites can avoid falling victim to the ransomware plague, but those that haven’t need to catch up quick. As this review shows, the criminals sense a “goldrush” and some of them are only too happy to sell the shovels.


