Over the last month a number of interesting leaks have occurred within the ransomware-market ecosystem pertaining to the likes of BlackCat and Zeppelin. We saw some familiar names dominate the ransomware landscape in terms of volume and visibility, among them Play, BlackCat/AlphV, LockBit, Phobos (8base) and Akira.
In this month’s update we also discuss some of the vulnerabilities being weaponized by these actors over the last month below, with high profile enterprises Microsoft SQL and SharePoint among the targets.
Crypto drainers, DaaS, and associated scams came to the forefront over the last few weeks with associated hacks being observed across multiple high-profile social media accounts. We will touch base on these recent scams and discuss how these attacks are occurring.
We will round out our discussion this month covering a short update on access-brokers and malicious tools targeting EDR platforms along with some positive news around law enforcement and the release of a Babuk decryptor.

Ongoing Exploitation of N-Day and 0-Day Vulnerabilities
Multiple threat actors have been observed targeting CVE-2023-29357, a critical privilege escalation vulnerability in Microsoft SharePoint. The ongoing exploitation of this flaw, along with the emergence of public PoC code, motivated CISA to add this flaw to its Known Exploited Vulnerabilities Catalog.
In early January, details began to emerge regarding the ongoing exploitation of at least two zero day flaws in the Ivanti platforms (Ivanti Connect Secure and Ivanti Policy Secure Gateways). The newly identified vulnerabilities, CVE-2023-46805 and CVE-2024-21887, allow for unauthorized command-injection attacks, exposing the systems to (unauthenticated) attackers.
According to initial reports, the Ivanti vulnerabilities have been targeted by an espionage-focused threat group (UNC5221) and used to drop a variety of malware including backdoors, webshells and credential harvesters, along with post-exploitation tools such as PySoxy (tunneling proxy) and BusyBox. Almost 20,000 vulnerable instances of the various Ivanti products have been identified as publicly exposed.
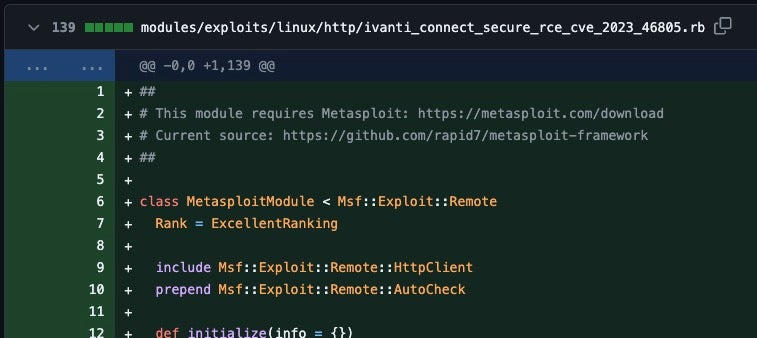
It should be noted that PoC code and MetaSploit modules for these flaws are now available.
Recommendations
These flaws should rank high on the priority list if they have not already been addressed. Defenders are encouraged to review guidance provided by Ivanti and CISA. The CISA guidance also provides explicit requirements for Federal Agencies (per current Federal cybersecurity directives).
Ransomware Updates
This month we saw a number of interesting developments in the ransomware ecosystem. An alleged prior affiliate of the now-defunct Zeppelin RaaS advertised the sale of the associated builder and support files on an underground market. The seller, known as “RET”, offered the package for 500.00 USD. This same seller has a history of selling “AV/EDR-killer” style tools as well.
This sale lowers the previous barrier to entry for Zeppelin-derived RaaS offerings. Prior to this leak (hosted on the well-established RAMP forum), Zeppelin ransomware builders were offered at a fee starting at at least 2000.00 USD. Malicious actors looking to get a discounted form of a “road tested” builder are highly attracted to these types of offers.
In addition, we saw a similar attempt at marketing of a RaaS with a posting to a well-known forum offering BlackCat/ALPHV source code for sale. The posting was accompanied with screenshots of what appears to be affiliate tools for delivery and management of BlackCat payloads.
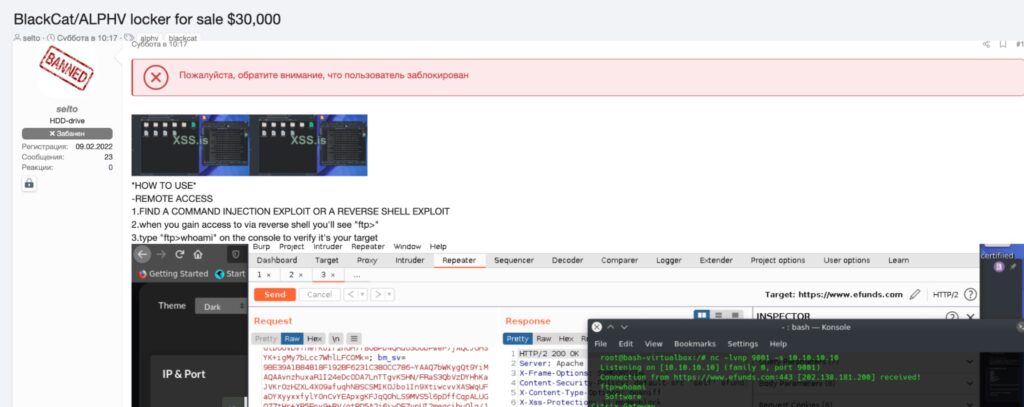
It will take time before the full reach and repercussions of these particular leaks are understood. Any lowering-of-the-bar around these tool sets inevitably attracts more enterprising criminals for whom these tools may have been out of reach prior.
Elsewhere, a portal for the creatively named “Going Insane Ransomware” emerged this month. For those that recall the late 1990s, “Going Insane” appears to embrace the GeoCities aesthetic with a decidedly ‘90’s’ take on the layout of their site.
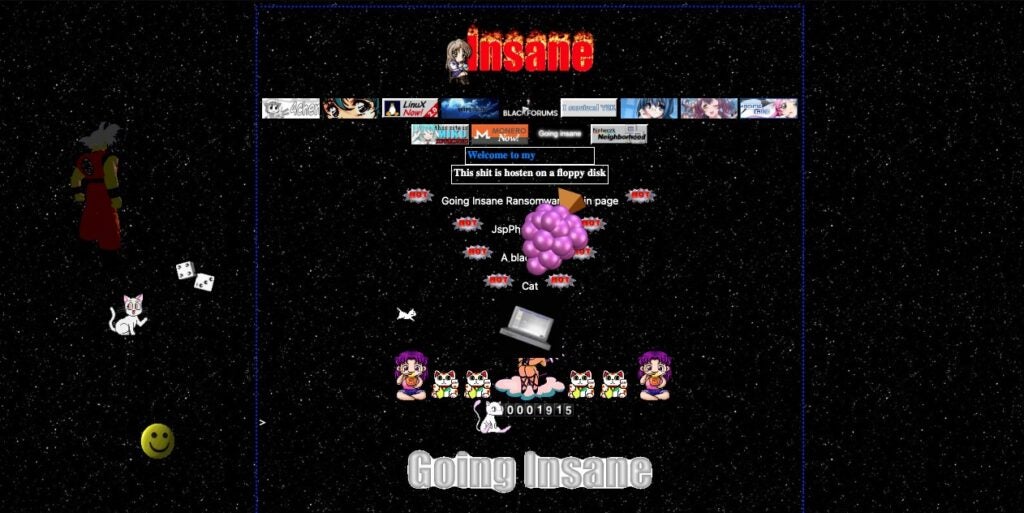
The group is actively recruiting and advertises its affiliate program (RaaS) with the following feature set (quoted):
- Military-grade AES encryption
- Encrypts All Files, Every single one, under lock and key.”
- Spreads in network, Infects every device in the network.”
- Wallet Stealer
- Browser Stealer
- System Info Stealer
- Auto Parsed Cookies
- Fully Undetected, bypasses all AVs
- FUD (0 detects) forever ig
Recommendations
SentinelOne Singularity™ Endpoint detects and prevents attacks associated with known Zeppelin/Buran, ALPHV and Insane RaaS. Defenders and threat hunters may find the following additional indicators useful for GIR ransomware.
nv5lbsrr4rxmewzmpe25nnalowe4ga7ki6yfvit3wlpu7dfc36pyh4ad[.]onion gfksiwpsqudibondm6o2ipxymaonehq3l26qpgqr3nh4jvcyayvogcid[.]onion r2ad4ayrgpf7og673lhrw5oqyvqg4em2fpialk7l7gxkasvqkqow4qad[.]onion insane[@]cock[.]lu
Drainers and Accounts Takeovers
Recently, a swath of account takeover attacks has swept through Twitter/X, leading to the compromise of several high-profile accounts. These accounts have been manipulated to disseminate content centered on cryptocurrency scams, orchestrated by groups known as crypto-drainers, or Drainers as a Service (DaaS).
Victims of these attacks include prominent entities such as CertiK, the SEC and cybersecurity vendor Mandiant.
The methods used to compromise accounts vary, ranging from brute-forcing credentials in cases without Multi-Factor Authentication (MFA) to SIM-swapping where MFA is enabled.
While the concept of Drainers and DaaS is not new, the recent high-profile breaches have cast a renewed spotlight on these malicious activities. The attackers are evidently motivated to target high-traffic accounts, aiming to redirect more users to their malevolent sites, as indicated by the increased click-through rates on the fraudulent posts linked to these hijacked accounts.
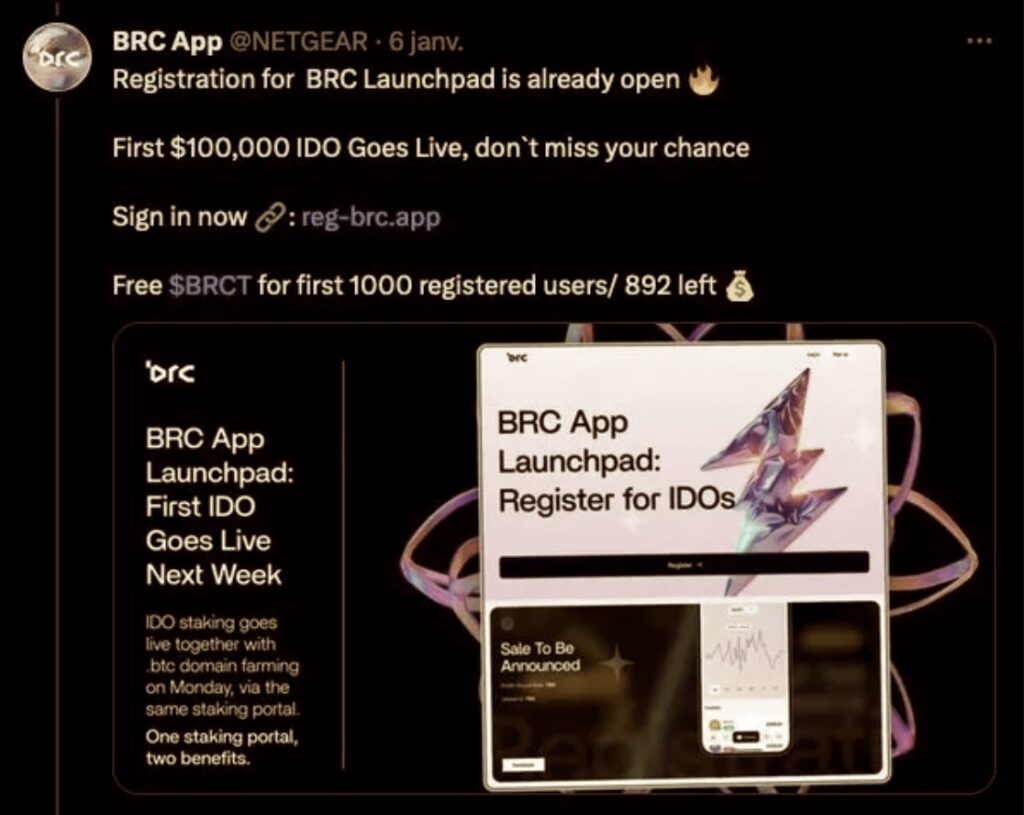
The initial vector for these attacks is typically via phishing followed by device takeovers through techniques such as SIM swapping.
Ultimately these attacks have a far reaching effect beyond just the financial loss of those that fall victim to the scam. Reputable brands that have accounts taken over by these criminals are at risk of reputational harm which could in turn have a financial impact.
Access Brokering and Tools
We continue to see the market for corporate and enterprise-level access flourish, to the point where buyers are soliciting for an opportunity to purchase from the plentiful well of providers. Buyers are currently trying to outbid each other for access either by offering greater fees or taking lower percentages.
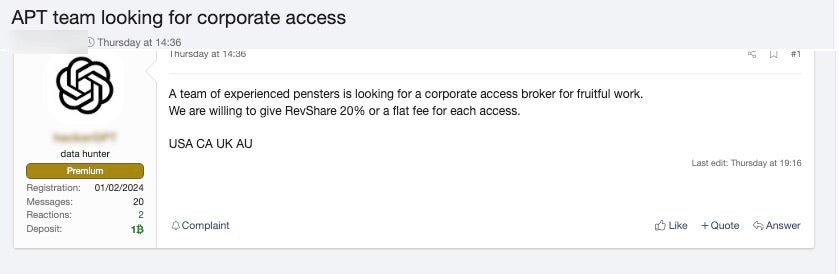
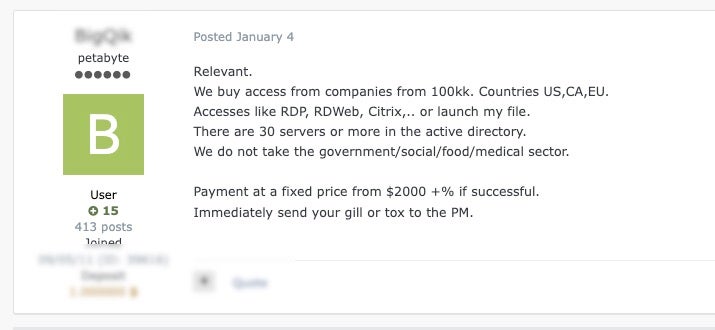
Those that are selling such access are profiting from targeting unprotected services such as IAM and reaping great rewards. It truly is a seller’s market out there at the moment, which is a worrying sign for defenders.
Concurrently, we continue to observe the marketing and use of customized “AV/EDR-killer” style tools. Tools like auKill and BackStab are frequently found amongst the artifacts left behind after a long-term ransomware attack or even an ATP campaign.
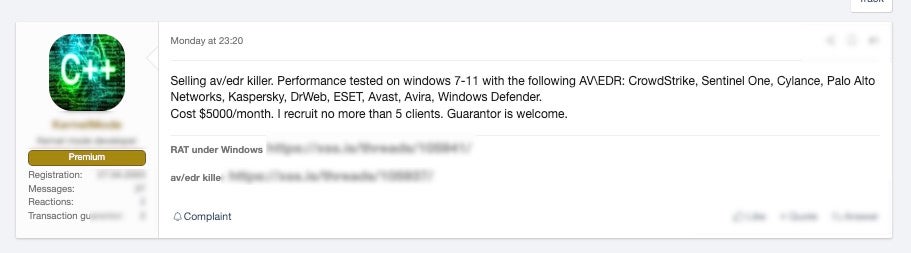
Recommendations
So-called AV/EDR “killer” tools typically rely on BYOD (Bring your own driver) functionality and additional components such as Process Explorer, Zemana and others. This makes them highly visible to well tuned platforms like SentinelOne Singularity™. Ensuring that the organization has good visibility into endpoint processes along with anomaly detection can provide additional safeguards against such tools.
For more information on Drainers and DaaS, defenders are encouraged to review The Rise of Drainer-as-a-Service | Understanding DaaS.
Law Enforcement and Disruption
It’s not all doom and gloom! Fortunately, there have been some important disruptions in the cybercrime landscape over late December and throughout January.
The main figurehead of the ShinyHunters threat group, Sebastien Raoult, was sentenced to 3 years in prison, along with having to pay requisite restitution. The group has an extended history of compromising developer repositories to steal API keys and other credentials. Raoult (alias “Sezyo Kaizen’) was found guilty of selling or facilitating the sale of breached company data across multiple platforms and markets. This includes well-known markets such as Alpha and Empire as well as forums like XSS and RaidForums.
Also this past month, a new decryption tool for the Tortilla variant of Babuk (aka Babuk Tortilla) has been released. The tool is the result of a collaboration between Cisco Talos, the Dutch Police and Avast. Following the apprehension of the actor associated with this particular variant of Babuk, Talos was able to work with Avast to expand the existing decryptor to accommodate the newly gained insight into other Babuk variants.
The Babuk Tortilla decryptor tool is available for download via the NoMoreRansom project.
Conclusion
The first month of 2024 has seen a continuation of the trends we’ve been highlighting across the last quarter of 2023. The increasing availability of tools that lower the barrier to entry for cybercriminals continues to fuel a crimeware ecosystem in which relatively unskilled threat actors can carry out low-risk/high-reward attacks on unprepared organizations.
The uptick in ‘Drainer-as-a-Service’ offerings and attacks is an extension of the service model popularized by ‘Ransomware-as-a-Service’ to target the widespread use and popularity of cryptocurrency, a model that seeks to steal from individuals but harnesses corporate assets to reach a large audience through social media account takeovers. As we often note, where there is money, an enterprising criminal will look for a way.
Organizations can improve their security posture, protect their assets, and avoid being the next victim on the list through awareness, training and suitable security technology. To stay informed and receive our next update, follow us on social media. To see how SentinelOne can help secure your business, contact us or request a free demo.


