Artificial intelligence (AI) is such a hot topic right now with everyone clamoring to say how their company is leveraging AI in all the new, flashy ways. Here at SentinelOne, we don’t do hype or hyperbole and AI is nothing new. We were founded in 2013 on the premise that AI could fundamentally transform cybersecurity and achieve real-time defenses against machine-speed attacks. Our cloud workload protection platform (CWPP), Singularity Cloud Workload Security, uses AI to deliver real-time detection and response to runtime threats. Our CWPP agent uses five engines onboard:
- Static AI Engine
- Behavioral AI Engine
- App Control Engine
- Cloud Intelligence Engine
- STAR Rules Engine
Some of the engines use AI while others are rules-based. Each works in concert with the other to defend business applications (aka workloads) running on your infrastructure whether in public or private cloud, on servers, VMs, or containers. To better understand the role of AI in achieving this objective, this blog post focuses on our Static AI Engine and is the first of a five-part series exploring each of our detection engines.

Static AI Engine 101
Much like cloud security, AI itself is a broad field and machine learning (ML) is a subset of this field. ML is exactly as the name suggests: machines learning to perform a task with high accuracy. ML models can be trained for any number of uses, from the academic (e.g., to differentiate between photographs of dalmatian puppies or chocolate chip ice cream) to the highly practical, such as differentiating between benign files and malware.
At the highest level of abstraction, our Static AI Engine consists of supervised machine learning algorithms which analyze files before they execute, examining the file structure and searching for historical patterns synonymous with malicious intent. Digging in a little deeper, the Static AI Engine is a classifier engine, categorizing the files being scanned in a number of classes, such as benign, suspicious, malicious, and so on. Ultimately, the decision tree algorithm delivers a predictive confidence level for a file’s maliciousness. For ML models to perform well, they must be trained over a large data set. SentinelOne’s classifier algorithms have been trained across nearly a billion samples over the past decade, and our threat researchers are continuously improving the models against the latest threats.
Where Static Detection Shines
Static detection of malicious files has several pronounced advantages. Most notably, examining a potentially malicious file before it executes means, quite simply, your endpoint and cloud workloads are protected from malware before it has the opportunity to transact evil. Additionally, static file analysis is computationally inexpensive relative to behavioral analysis. The latter embeds more behavioral signals across the operating system (OS), requiring certain techniques to observe OS-level processes as the file executes. This relative computational efficiency is especially important on cloud infrastructure-as-a-service (IaaS), because every bit of CPU usage shows up on the monthly bill from your cloud service provider (CSP). Therefore, being a good steward of CPU resources is especially important for the CWPP agent, all the more so at scale.
Static analysis is an excellent way to detect malware, but it can’t solve every use case. For example, fileless attacks that launch processes directly from memory without ever creating a file on disk cannot be detected via static analysis. Such memory injection attacks require different detection capabilities. Security teams need not worry as the behavioral analysis in SentinelOne’s CWPP agent’s Behavioral AI Engine can detect memory injection attacks. We’ll dive deeper into Behavioral AI in part two of this blog series.
Case Study | Static Detection vs. Trojan Malware
Recently, the SentinelOne CWPP agent detected Linux malware targeting a customer’s public cloud infrastructure. In this example, the Static AI Engine detected that an originating process called ‘busybox’ wrote a suspicious ELF file to storage associated with a customer’s Amazon EC2 instance. Upon subsequent analysis by SentinelOne, we believe this ELF file to be a Trojan. As the name would suggest, a Trojan is a type of malware that is disguised as a real, reputable program. The supervised ML models in the Static AI Engine are trained in SentinelOne’s labs to recognize features of Trojan malware and more, such as communication modules back to command and control (C2) infrastructure owned by threat actors.
Once the ELF file was written, it was then set to executable, which then called back to a malicious IP address. This C2 infrastructure was a cloud compute instance controlled by the threat actor and operated from another cloud service provider in Europe. Cloud infrastructure is especially attractive to threat actors for use as C2 infrastructure, because they can change IP addresses, locations, and domain names in an attempt to cover their tracks. Our CWPP agent collected all the precise details, which we intentionally redacted from this example to protect our client’s identity.
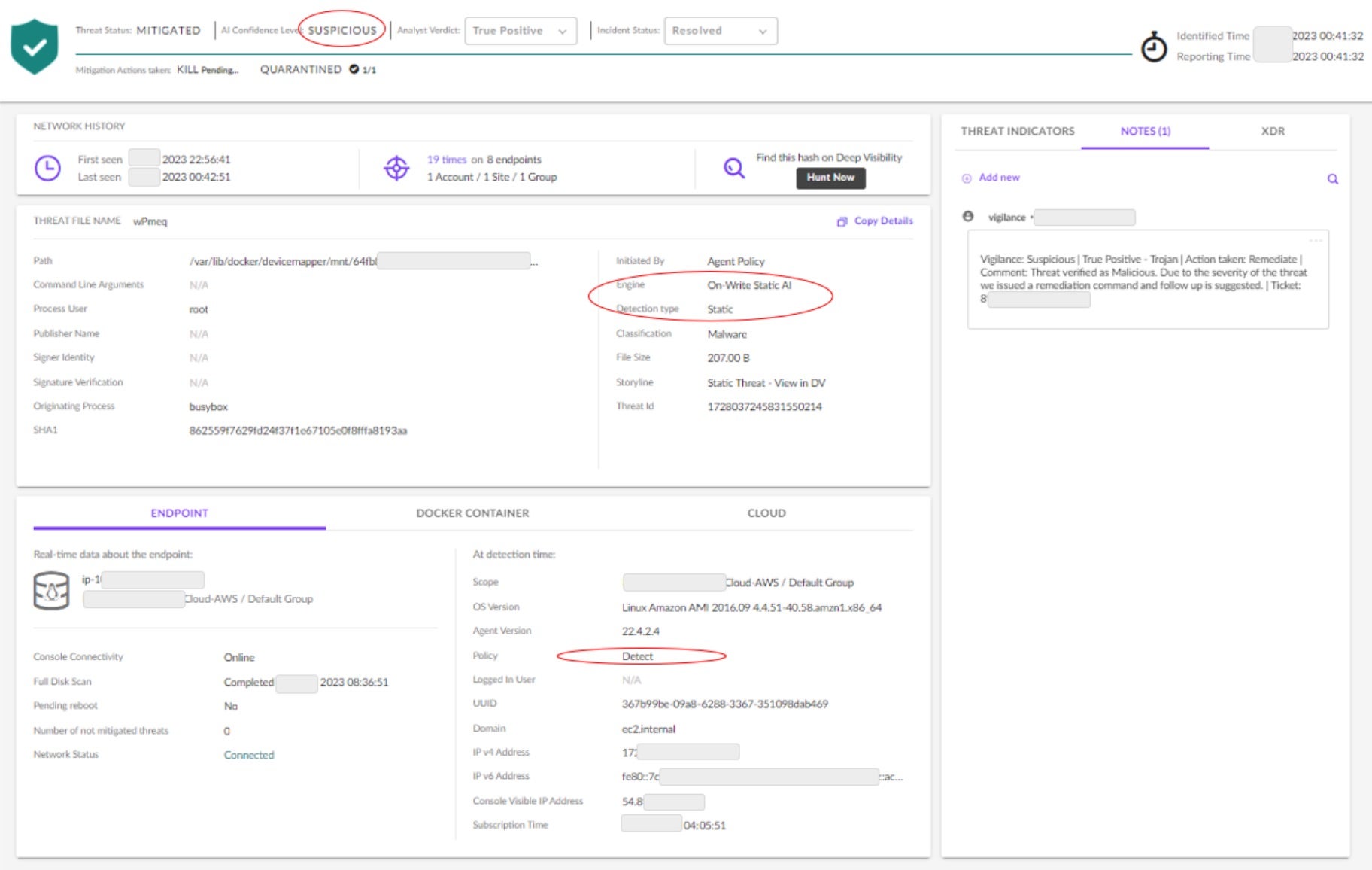
In the SentinelOne management console shown in Figure 1, there are a few things to point out. The engine responsible for making the threat detection is “On-Write Static AI,” meaning that the Static AI Engine made the detection when a suspicious file was written to disk.
Secondly, the AI Confidence Level is shown as “SUSPICIOUS.” There are two confidence levels: SUSPICIOUS and MALICIOUS. Different policies for response action can be set for each confidence level. Finally, the agent policy for this detection confidence level is shown as “Detect.” This means that the agent has issued an alert, but no response action is taken, meaning that it is awaiting disposition from a cybersecurity professional.
In this specific example, the customer is also subscribed to our Vigilance MDR service. As shown in the incident notes section of Figure 1, the SentinelOne Vigilance analyst confirmed the verdict as a true positive, took mitigative actions to quarantine the threat file, and then notified the customer. Since the Threat Status was “Mitigated,” the status symbol in the upper left of the console displays a green shield with a check mark.
It is worth noting that agent policy can just as easily be set to “Protect”. The choice between Detect or Protect Mode is governed by policies which the customer controls. If the policy had been set to Protect for this case study example, the mitigation response action would have been fully automated and executed immediately after the detection, surgically unwinding the effects of the attack while simultaneously preserving a record of all telemetry collected during the incident.
Conclusion
The Static AI Engine truly is the workhorse of our CWPP agent. By training our proprietary ML models over nearly a billion malware samples over the course of nearly a decade, our static file analysis is the first line of defense in our ruthlessly efficient CWPP agent.
To learn more about the value of real-time CWPP in your cloud security stack, head over to the solution homepage. Or see how Singularity Cloud Workload Security works with a 2-minute guided walk-through here. For a personalized demo, connect with one of our cloud security experts today.


