Duqu2, Mosquito backdoor and Shamoon-2 are advanced persistent threats with a common trait: they all leveraged Meterpreter, the flagship payload of Metasploit.
What is Meterpreter?
Meterpreter allows an attacker to control a victim’s computer by running an invisible shell and establishing a communication channel back to the attacking machine. Its power and versatility have made it a favorite among pentesters, and clearly these qualities have made it equally attractive to bad actors.
Meterpreter has all the “basic” features one would expect from a penetration testing tool. These include access to a command shell, running executables, sending and receiving files and profiling the network. But it can do much more than that. Taking screenshots, keylogging, port forwarding and privilege escalation are only a few of its capabilities. Moreover, it can load various in-memory modules such as Mimikatz for dumping hashes and plaintext passwords. Meterpreter itself resides entirely in memory, writes nothing to disk, and creates no new processes. Instead, it injects itself into compromised processes and can also migrate from one to another as necessary. These features make it an attractive payload for APTs that prioritize staying under the radar.
Meterpreter can be loaded into memory in various ways. Numerous stagers are available within the Metasploit framework such as Powershell, VBScript, and document macros. The framework offers a large number of exploits which can also be used to inject Meterpreter directly into memory. Advanced users can even write their own loader or exploit and use those with their custom evasion techniques as well.
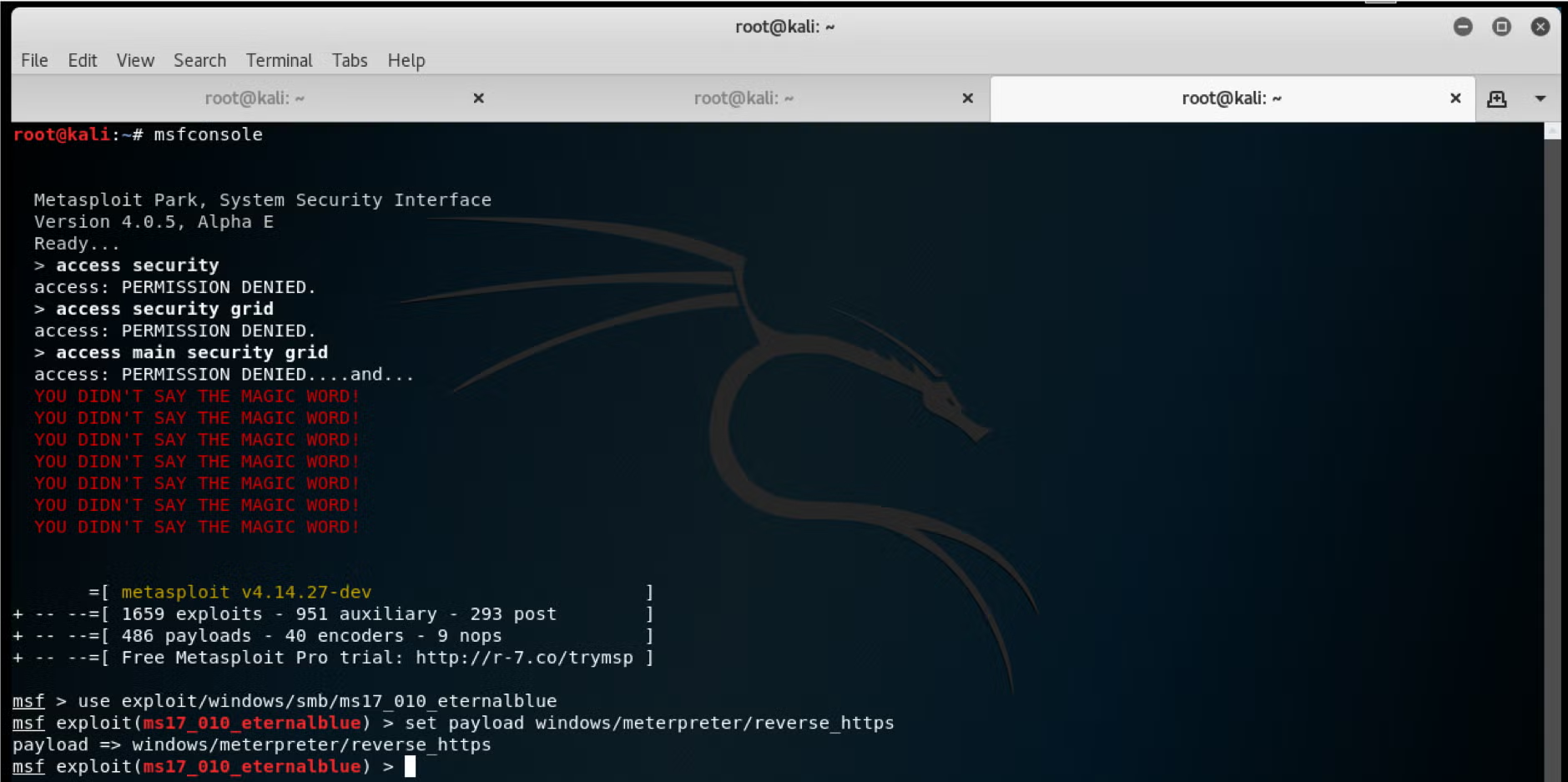
Here is a screenshot taken from the Metasploit framework console, in which the reverse_http Meterpreter payload is set.
Metasploit and Meterpreter are constantly evolving, too. Not so long ago, it was common to drop Meterpreter stagers on the disk and use as many packers as possible to bypass static scanners and evade sandboxes. There are many built-in and easy-to-use encoders in Metasploit for that, and AV companies struggle to keep up with detecting them. Metasploit and Meterpreter have likewise been updated with a number of fileless techniques. For example, injecting the payload into a system process after exploitation and leveraging winAPI in order to query the registry instead of using reg.exe.
However, since Meterpreter’s behavioral footprint is indicative of malware, the SentinelOne Behavioral AI engine will detect it, even if it uses fileless techniques and is loaded directly into memory.
Demo
The following video shows how SentinelOne detects a Meterpreter-based attack.