From ransomware operators like LockBit and BlackBasta to APTs striking for or against Russian or Chinese interests, threat actors of various stripes all need one thing to get their operations off the ground: initial access to an organization’s network.
Such access can be bought on a variety of trading forums from cyber criminals who specialize in running low-risk phishing campaigns and credential theft operations, or in scanning enterprise networks for known remote code execution (RCE) software vulnerabilities.
Because of the ease with which initial access can now be obtained thanks to poor patch management and lax controls over identity and user credentials, there exists a market where supply is outstripping demand, and vendors involved in selling initial access are lowering their prices in a race to the bottom, making it easier than ever before for threat actors to compromise organizations of all sizes and kinds.
In this post, we reveal what these marketplaces look like from the inside, exposing the ways these traders advertise and sell unauthorized access to organizations.

What Are Initial Access Brokers?
‘Initial Access Brokers’ or IABs typically do not exploit enterprise networks directly but rather sell the access they have harvested to those that do. As a result, various darknet marketplaces, community forums, Telegram channels and surface net communities are teeming with such brokers, competing in a ferocious bazaar to attract and retain new and existing customers.
We have previously explored how such actors focus on the market for buying and selling access to MSP environments. As attacks like Kaseya, Solarwinds, and Wipro have proven, MSPs are a much-sought after target for both financially-motivated cyber criminals and APTs intent on espionage. Since then, we have seen the range of compromised networks expand to cover almost any kind of business or organization, regardless of size.
Companies At Risk From Compromise By Initial Access Brokers
The range of compromised networks we have seen and give examples of below is a worrying indictment of the state of cyber security today. Across these markets, we’ve seen access being sold to government and police computer systems, high courts, banks and critical infrastructure at one end of the scale to online cinemas, casinos, delivery companies, logistics, ISP providers, and local retailers at the other.
In some cases, IABs have surveyed the environments of the victims they are selling access to and even provide the buyer with information on the AV or EDR security solution being used.
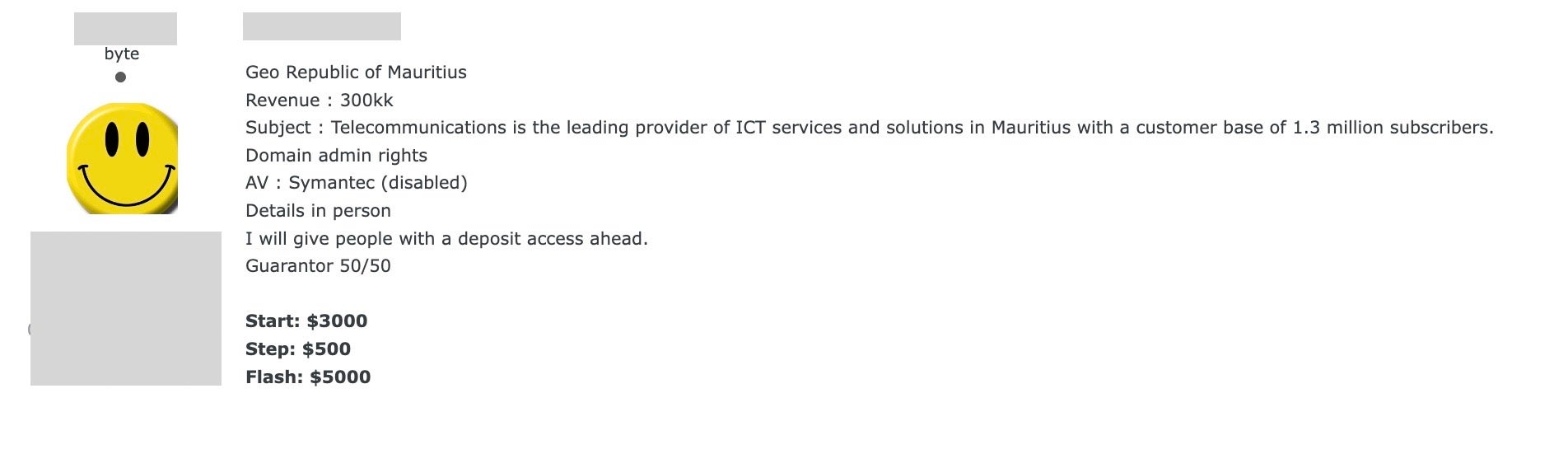
The example above shows a vendor advertising access to a service provider with a customer base of 1.3 million subscribers in the Republic of Mauritius. In an effort to encourage early exploitation, some sales of this nature take on a time-based component in that the seller will raise the price over prescribed intervals, in this case in increments of $500.
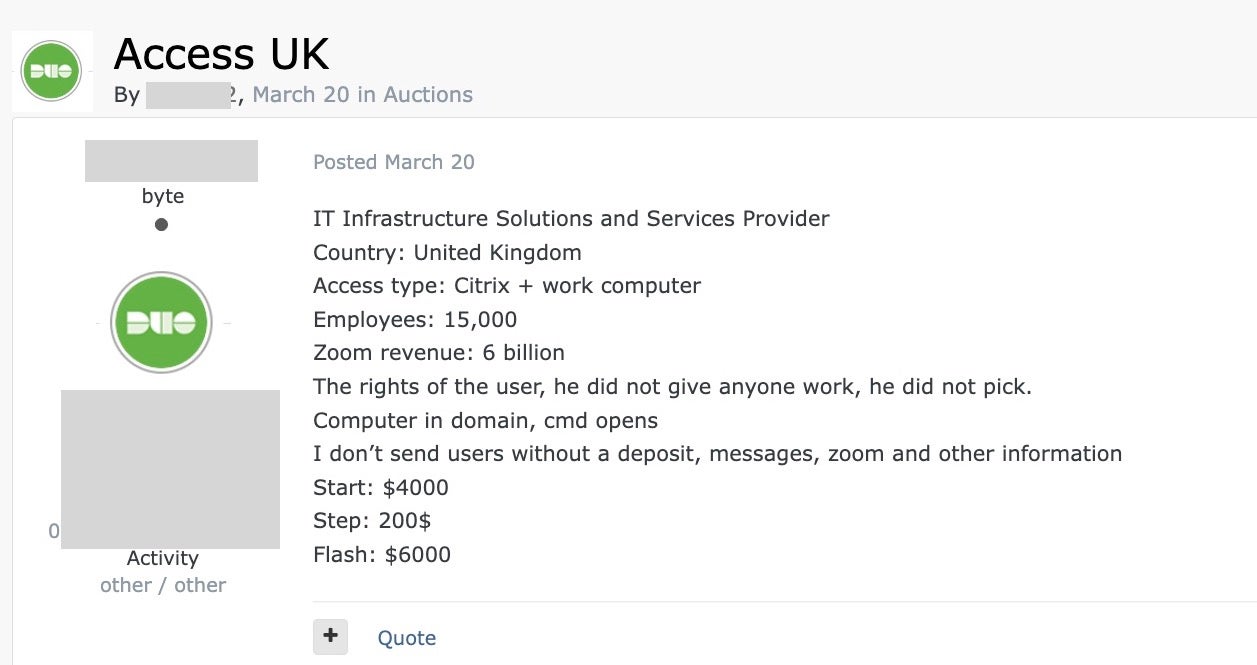
In a different example, a threat actor offers access to a UK IT infrastructure solutions and services provider with 15,000 employees at a starting price of $4000.
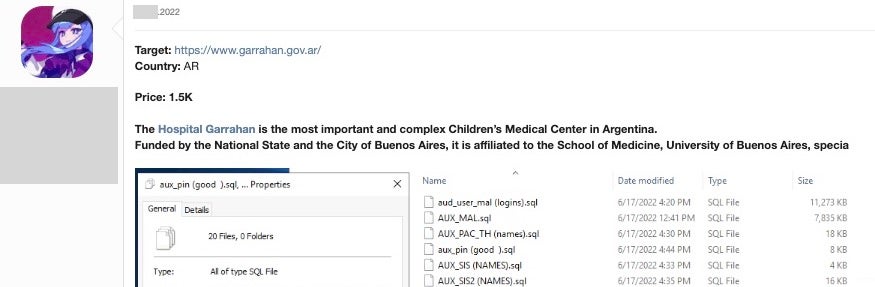
IAB threat actors possess few scruples when it comes to the nature of their targets, even selling unauthorized access to organizations such as hospitals and children’s hospices.
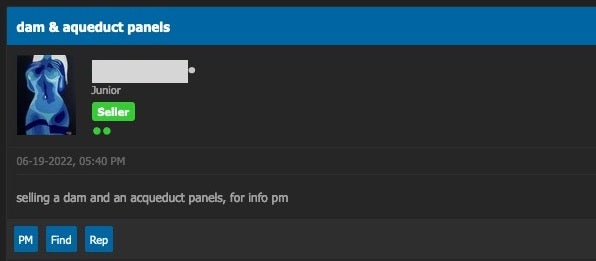
In other cases, vendors are quite happy to sell access to critical infrastructure, such as in this advertisement offering administrative panel-level access to “dam and aqueduct panels”.
Initial Access via Known Vulnerabilities at Rock Bottom Prices
A common form of advertisement in these markets involves a list of many different organizations offered by the vendor that have been collated by scanning for targets that have not patched against various known remote code execution vulnerabilities.
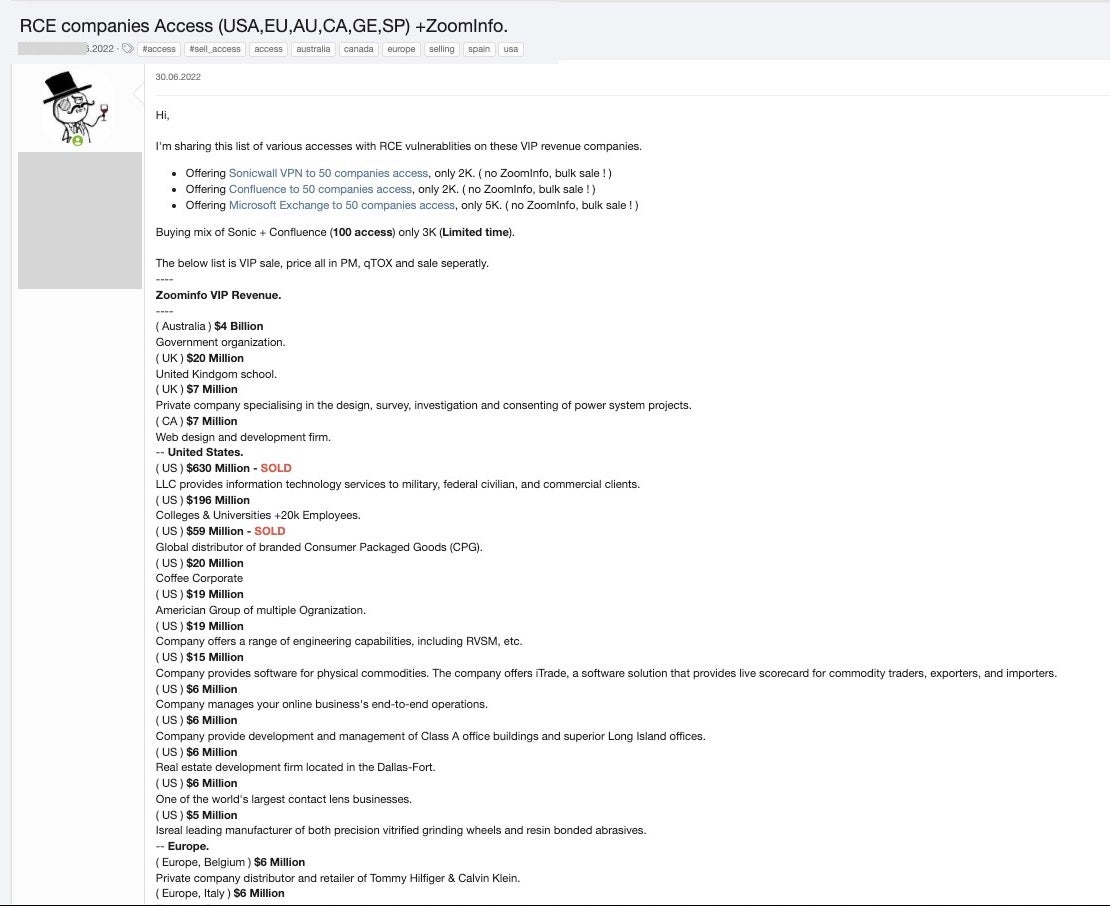
Some of the vulnerabilities most routinely exploited to gain access to organizations and enterprises are:
- CVE-2022-26134 – Confluence
- CVE-2021-26855 (aka ProxyLogon)
- CVE-2021-31207, CVE-2021-34523, CVE-2021-34473 – Microsoft Exchange
- CVE-2021-20038 – SonicWall SMA RCE
In other cases, vendors list a range of organizations with individual prices. The means of initial access is not clear, but given the vast range of different organizations, mass phishing campaigns and credential theft are also likely vectors.
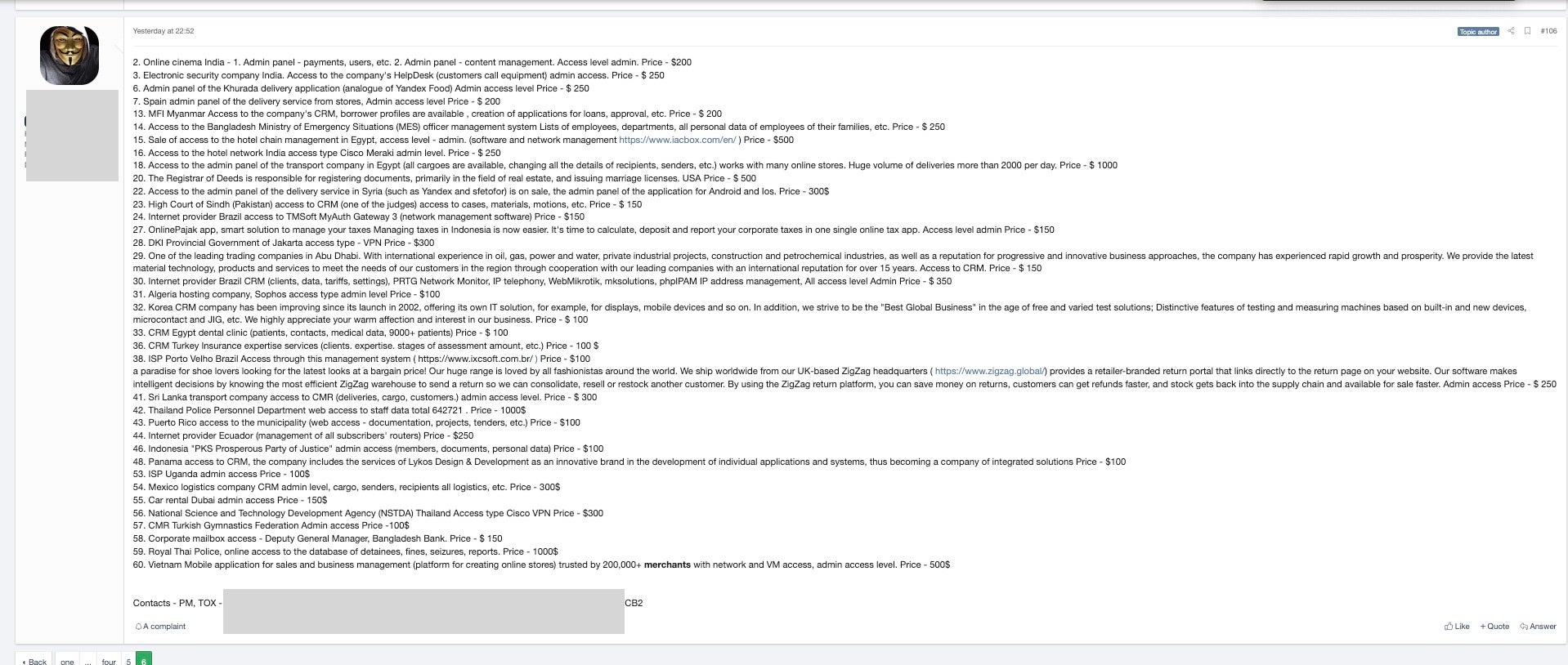
On the one hand, the vendor above is selling access to relatively low-interest compromises at rock-bottom prices, like
- Algeria hosting company; [AV:] Sophos; access type:admin level. Price: $100
On the other, there is potentially devastating data being offered in access for sale to orgnaizations such as
- Royal Thai Police; online access to the database of detainees, fines, seizures and reports. Price $1000
- Thailand Police Personnel Department; web access to staff data total 642721. Price $1000
For a mere $250, the same actor offers interested APTs or enterprising cyber criminals access to the Bangladesh Ministry of Emergency Situations management system, which lists “employees, departments, all personal data of employees [and] of their families”.
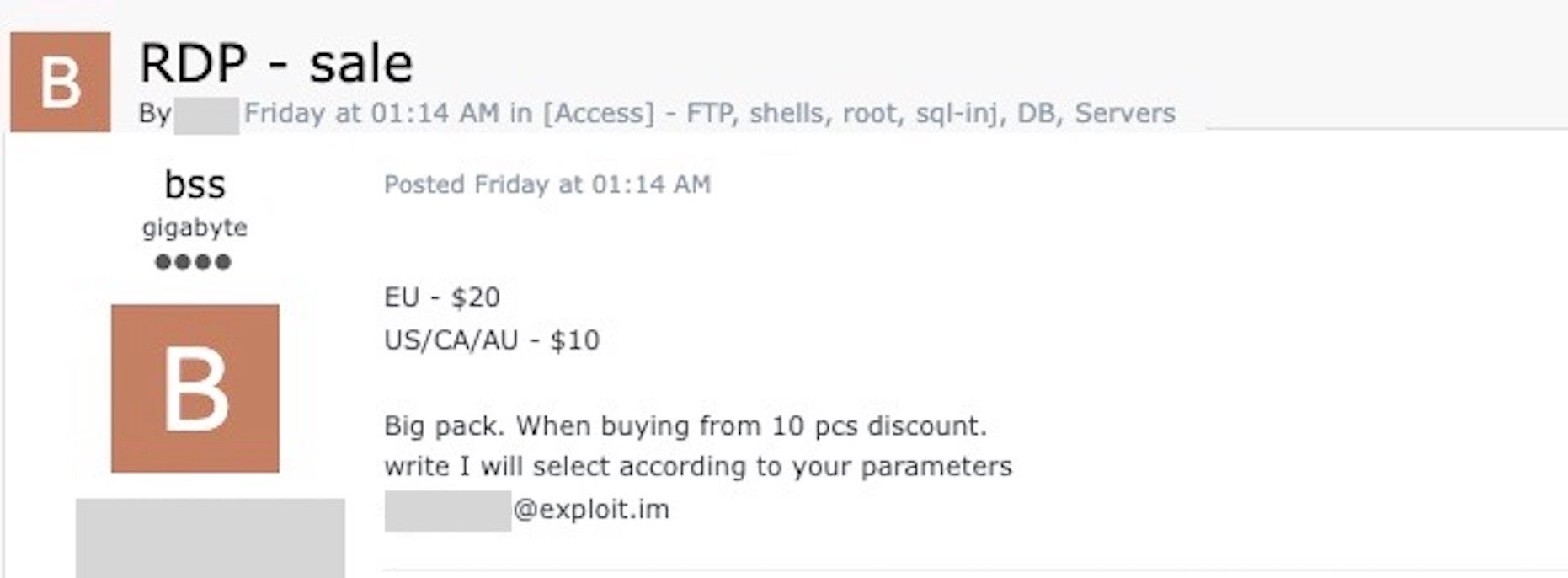
Others offer discounts for bulk buys, selling access to RDP, cPanels, SSH, and Webmail among other things for as little as $10 per item.
High Value Targets Come at Premium Prices
While there is a bustling market for low-priced access, it remains true in the IAB marketplace as any other that you get what you pay for. The takeaway difference between ‘bottom of the barrel’ bulk sales and the more expensive access is precision.
Bulk sellers offer large quantities of accounts with far less control over what environments the accounts belong to or how effectively they can be monetized. Some buyers want to know exactly what they are getting and are willing to pay a premium for it.
In the next example, the seller is offering access to a high-value target where much of the preliminary work needed for successful exploitation has been done. Accordingly, the vendor is asking for a premium price.
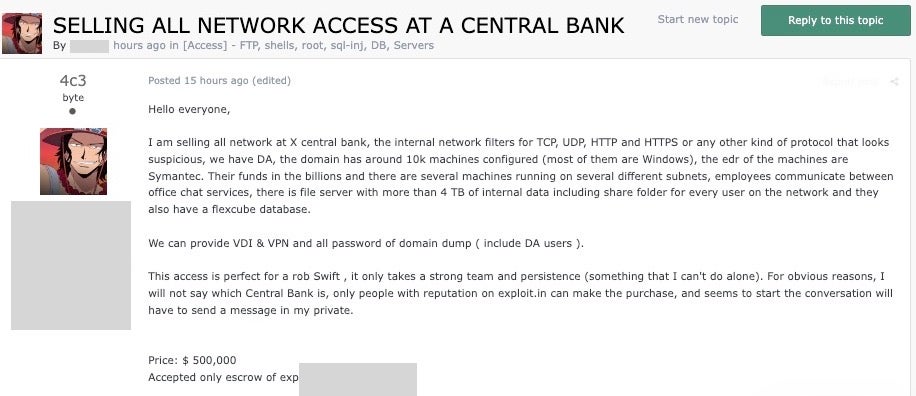
For the right criminal buyer, this provides most of the key information needed. On offer is “Full” network access to a large “central” bank. The vendor claims to have Domain Admin (DA) access with reach to over 10,000 hosts. The seller even makes note of the EDR in use (Symantec, in this case). The price tag, at the time of writing, was a hefty $500,000.
Evil Markets | There’s Something For Everyone
IAB markets are not new, and some vendors and marketplaces have been around long enough to have a surprisingly polished presence.
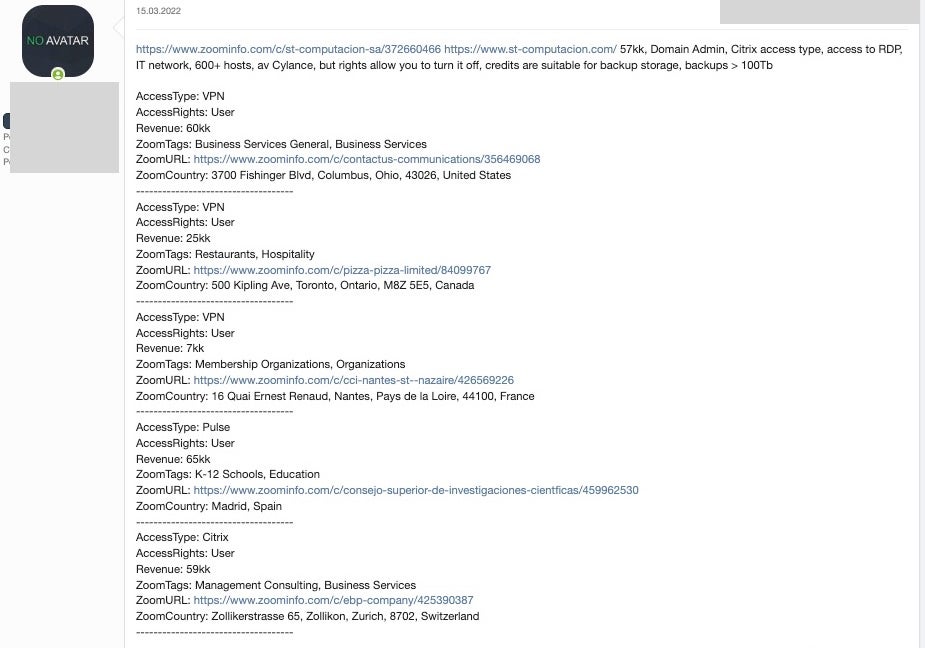
This vendor aims to make life as easy as possible for potential buyers. Along with each entry, the seller provides access type, user level/context, revenue numbers, and links to Zoominfo. If known, the installed AV/EDR is listed along with helpful hints or potential ways to bypass it, such as “AV Cylance, but rights allow you to turn it off”.
As in any area of commerce, more sophisticated vendors understand the importance of presentation and some marketplaces like Odin offer slick interfaces to facilitate trade.
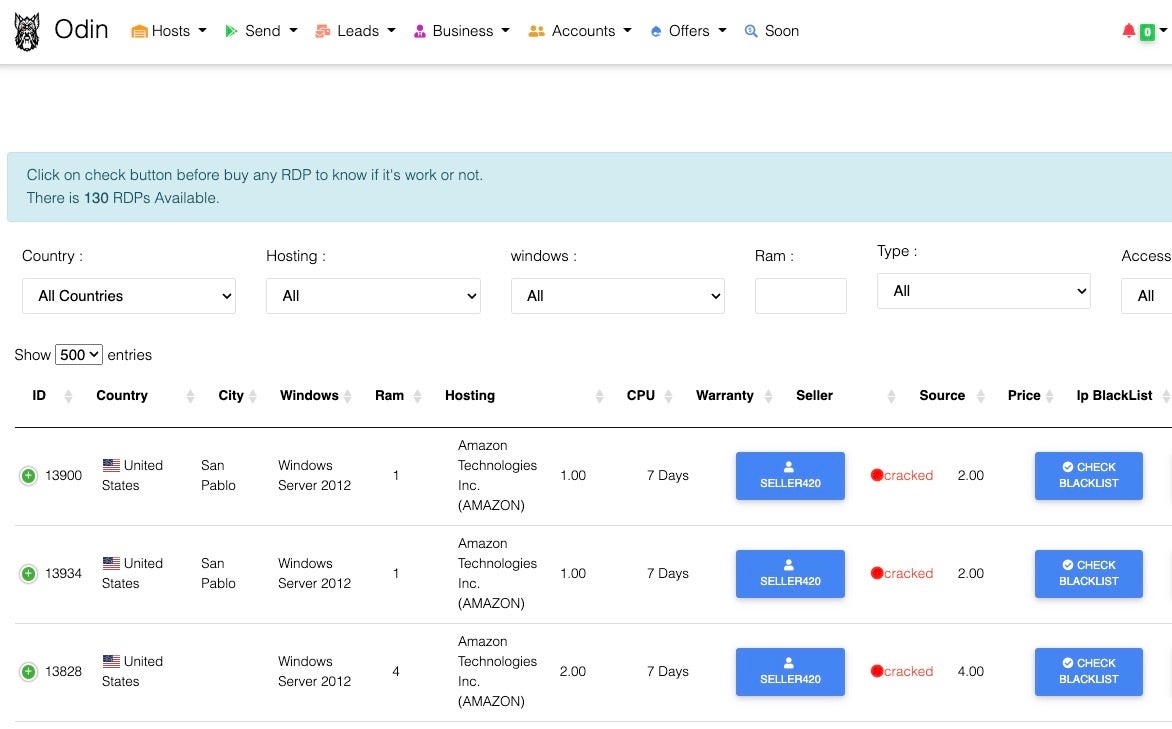
From simple forum listings to polished web applications offering filtering and sorting options, there’s an evil market trader out there to suit every type of buyer looking for access to compromised organizations.
Does Access For Sale Translate Into Real-World Breaches?
It is not difficult to correlate the items we see for sale in IAB marketplaces and the compromises listed on ransomware operators’ leak sites.
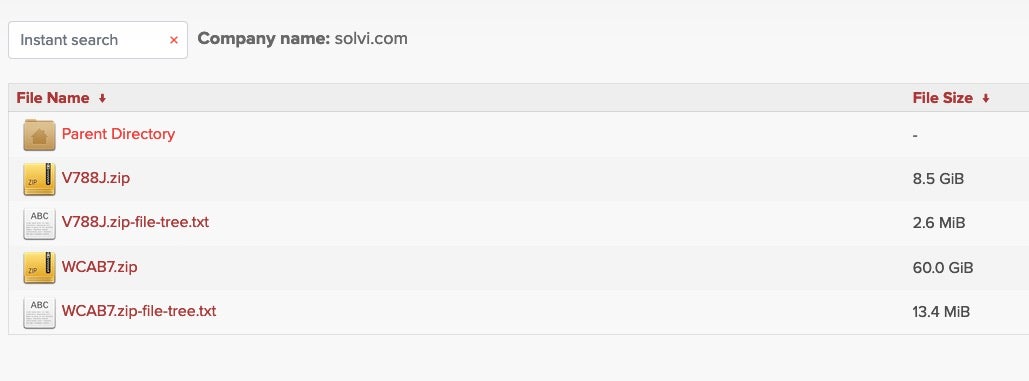
For example, the following victim, a Brazilian company in São Paulo, was listed on an IAB marketplace in March 2022.
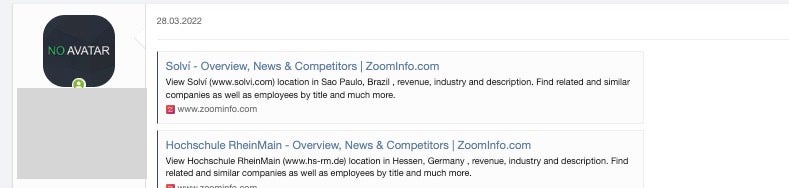
Searching the LockBit 3.0 ransomware group’s index in August shows the company’s data has been exfiltrated for ransom, sale or public leaking.
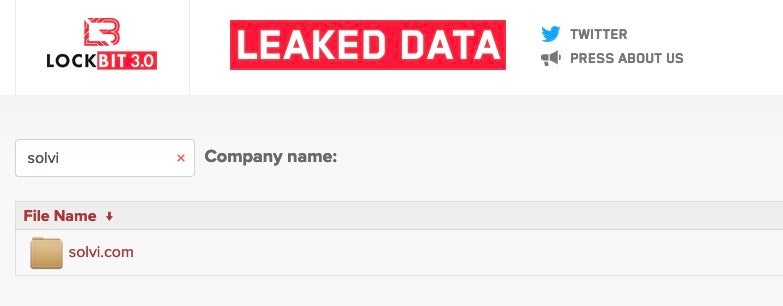
The stolen data amounts to around 68 gigabytes in two zip archives, along with file tree indexes for each.
Conclusion
The trade in access to compromised networks has been around for some time and is not going away anytime soon, and the nature and existence of these markets hold several important takeaways for organizations and security teams.
First, neither location nor size offer protection from cyber criminals. The geographical range of compromised organizations spans pretty much the entire world, and every type and size of business and organization is represented.
Second, protection against initial compromise isn’t optional or ‘nice-to-have’. Organizations that find themselves being traded on these markets are at high risk of finding themselves appearing on ransomware leak sites or suffering breaches with potentially serious financial and reputational harm.
Third, the bar to entry has never been lower. Criminals are happy to sell this access at prices that are little more than pocket change to most threat actors. These low prices mean new players can experiment at low cost, fuelling the cybercrime economy and expanding the number of attackers out there. For security teams, understanding where the barrier of entry is for such threat actors in the organization’s network can go a long way towards structuring effective defenses.
For organizations, it is imperative to ensure that access to networks is protected by a trusted identity solution that can prevent credential misuse, identify vulnerabilities, and trap both remote and insider threat actors through deception technologies. To learn more about how to protect your organization, please visit Singularity™ Identity.


