The Good
The United States, Cyprus and Latvia have successfully seized and dismantled a major dark web marketplace dealing in personally identifiable information (PII).
According to a FBI press release this week, law enforcement bodies confirmed the shutdown of the SSNDOB Marketplace, a series of websites that had listed the names, dates of birth, and Social Security Numbers of approximately 24 million individuals based in the United States.

U.S. Attorney Roger Handberg announced the closure, saying “I applaud the extensive work and cooperation by our domestic and international law enforcement partners in bringing a halt to this global scheme. The theft and misuse of personal information is not only criminal but can have a catastrophic impact on individuals for years to come.”
In the press release, the FBI detailed how the administrators used online monikers distinct from their true identities, maintained servers in several countries, and required digital payment or cryptocurrencies to protect anonymity and fly under the radar.
The authorities also laid out the SSNDOB Marketplace’s activities, such as offering customer support functions, advertising their services on criminal forums, and regularly monitoring activities and payments on their websites. While it was active, the Marketplace raked in more than $19 million USD in revenue.
In the U.S., the IRS’ Criminal Investigation Cyber Crimes Unit and Criminal Investigation’s Tampa field office led the investigation alongside the FBI’s Tampa division. They worked closely with the Latvian police, the Cyprus police, and the FBI’s Legal Attaché Offices responsible for Latvia and Cyprus with support from the U.S. Department of Justice’s Office of International Affairs.
When authorities executed seizure orders against the Marketplace’s domain names, the Marketplace was effectively shut down.
While agents in the statement lamented the “devastating impact” identity theft had on victims’ mental and financial health, this closure is a major milestone for international cooperation in shutting down cyber criminal operations, and we hope it is the first step in helping victims of these threat actors find closure.
The Bad
Yet another public school district has fallen victim to a ransomware attack.
On June 8th, 2022, Tenafly Public Schools announced that they would have to cancel final exams as the district worked on restoring its computer systems. This incident comes immediately after an audit that yielded new recommendations to mitigate the district’s cyber risk.
Until remediation is complete, the schools are continuing classes under modified lesson plans, since students cannot access their Google Classroom, Genesis, email accounts and other day-to-day services.
After a ransomware attack, the Tenafly School District in New Jersey canceled all final exams this yearhttps://t.co/ZjoM97uF0P
— Catalin Cimpanu (@campuscodi) June 9, 2022
According to the district, administrators became aware of a breach when several computers in the district network were encrypted. The district’s IT department quickly isolated devices, shut down the district’s computer network and brought in cybersecurity consultants to help with incident response and remediation. Reports also indicate that law enforcement officials are working with the district and its experts to investigate the breach.
Representatives for the district did not comment on the size of the ransom, but they did say that the district has not decided whether they would be paying the ransom. As remediation continues, the Tenafly school district has laid out plans to begin implementing recommended improvements from the audit as their systems come back online. However, representatives did not say when the computer systems would be back up, only stating that they “anticipate that it will just be a few days.”
Incidents like these demonstrate how crucial it is to regularly evaluate your cybersecurity program and ensure that your organization is keeping pace with recommended security measures — you never know when a cyber criminal could threaten your day-to-day operations.
The Ugly
Old and new security threats are coming together to enable lateral movement across networks and launch double extortion attacks.
According to a recent report, researchers have observed the Black Basta ransomware group leveraging Qbot (also known as Qakbot), a 24-year old infostealing trojan to enable lateral movement across infected networks.
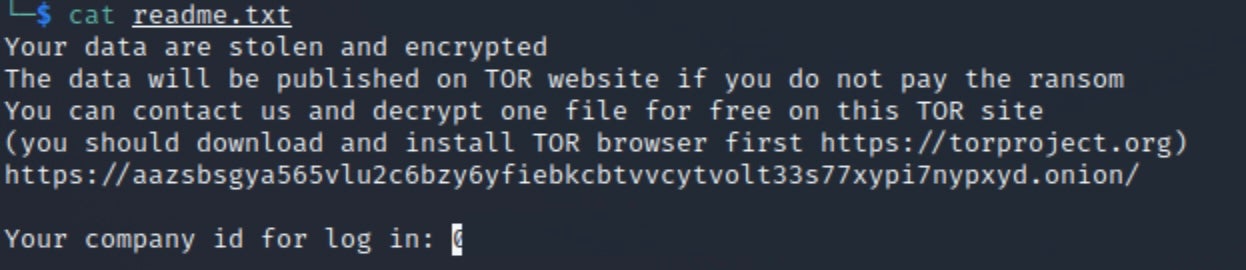
Black Basta first emerged in April 2022, and targets a variety of firms and industries by initially stealing network data before encrypting infected machines. Once the encryption is complete, Black Basta demands a ransom payment for the return of the stolen data. If the victim refuses to pay, the ransomware gang leaks the victim’s data on a dedicated Tor site.
Meanwhile, Qbot was first spotted in 2008. Initially an infostealing trojan targeting Windows users, this malware has constantly evolved over the past 14 years, adopting context-aware delivery tactics, phishing capabilities and other tactics to avoid detection in order to exfiltrate cookies, engage in keylogging, and steal credentials for online banking accounts and other login details.
Although cyber criminals commonly use Qbot to help their ransomware establish a foothold in targeted networks, Black Basta is leveraging the malware with new methods. When Black Basta gains access to a network, it remotely uses Qbot to create a temporary service on a target host.
Once it’s used Qbot to establish a foothold, Black Basta uses RDP and a batch file to enable RDP logons, which allows the group to establish remote desktop sessions on infected machines.
Emerging threats like these are a good reminder to security professionals that older threats can still pose some risk, especially in the hands of inventive cyber criminals.


