On Tuesday, March 2nd, Microsoft released an out-of-band security update addressing a total of 7 CVEs, four of which are associated with ongoing, targeted attacks. The update was in response to an active campaign that was seen on Microsoft clients compromising Exchange servers by bypassing authentication and allowing attackers to read emails and potentially penetrate enterprise networks without the need to authenticate.
The SentinelLabs team has been closely tracking HAFNIUM and Exchange Server impacts. Customers with the Deep Visibility threat hunting module (STAR) may also automate responses (alerts, network quarantine, kill, quarantine) should these IoCs be seen in the future. Our customers can stay ahead of this emerging threat with our protection capabilities and real-time alerts.

Executive Summary
- The attack is relevant for Microsoft Exchange servers (on-prem only). The SentinelOne agent supports protecting Exchange servers and is widely deployed on Exchange servers.
- The SentinelOne agent includes dedicated logic to protect from password scraping, including LSASS dumping and Mimikatz attempts on the agent.
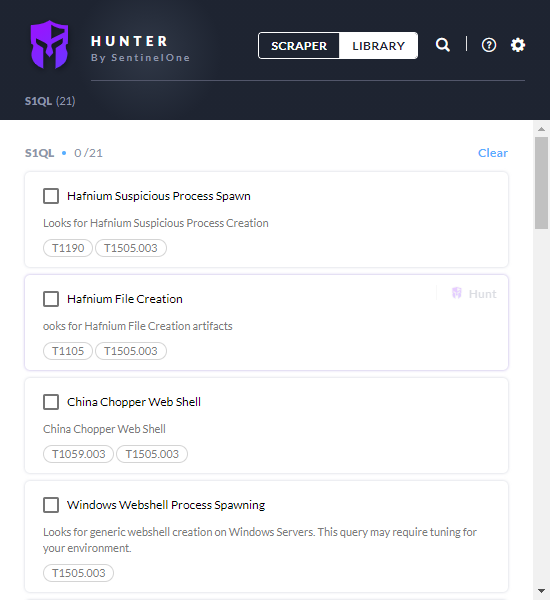
- The SentinelOne Singularity platform supports Deep Visibility hunting queries, allowing customers to do retrospective hunting to identify if there were any HAFNIUM artifacts in their environments.
- All SentinelOne Vigilance clients have already been proactively reviewed for any HAFNIUM attempts and will be closely monitored.
- SentinelLabs and the WatchTower threat hunting teams continue to monitor our existing customers’ infrastructure for any evidence of HAFNIUM, its payloads, and other TTPs. If identified, customers will be notified by our Vigilance service and provided with a course of recommended actions to follow.
- Query packs for SentinelOne customers are available here.
Technical Review
Microsoft update addresses a total of 7 CVEs, 4 of which are associated with ongoing and targeted attacks.
The associated flaws affect Microsoft Exchange 2013, 2016, and 2019. These flaws have been leveraged by an attack group dubbed HAFNIUM, and represent a portion of a more broad attack chain. Additional tools associated with this campaign include:
- Nishang
- PowerCAT
- Procdump
In the days following the disclosure of these flaws, we have observed a significant increase in the amount of scanning and subsequent exploit attempts of these vulnerabilities. The targeting of these flaws is not exclusive to the HAFNIUM group, and we are starting to see separate campaigns which attempt to distribute additional malware families.
It is also critical to note that we are also observing the proliferation of public PoC code for CVE-2021-27065.
Exploited Vulnerabilities
CVE-2021-26855 – Remote Code Execution flaw, via untrusted connections to the Exchange server on port 443. Does not require user interaction
CVE-2021-26857 – Remote Code Execution flaw, via untrusted connections to the Exchange server on port 443
CVE-2021-26858 – Remote Code Execution flaw, via untrusted connections to the Exchange server on port 443
CVE-2021-27065 – Remote Code Execution flaw, via untrusted connections to the Exchange server on port 443
Three additional CVEs are included in the fix, but these are not known to be part of the observed attacks. These are CVE-2021-26412, CVE-2021-26854, CVE-27078
It should be noted that all but CVE-2021-26855 require user interaction. In addition, the relevant CVEs affect on-prem installs of Exchange Server only. Exchange Online is not directly affected, though hybrid environments will have at least one Exchange server requiring patching.
Further Details
The exploitation of these vulnerabilities allowed the attackers to gain their initial foothold in the environment. Once the target had been breached, webshells of various types were deployed to allow for further management and exfiltration from compromised hosts. Where needed, additional tools were used to facilitate lateral movement, persistent access, and remote manipulation. Open source tools such as PowerCAT, Nishang, 7zip, WinRAR, and Procdump were utilized to do just that.
HAFNIUM, as a group, has been linked to attacks against the defense industry, government and policy-related entities, law firms, and medical and educational institutions. Current intelligence indicates that the group operates out of China. The group is considered highly-sophisticated. Their arsenal of tools includes 0-days along with customized malware, COTS/Open-source tools, and LOTL techniques. This includes heavy use of PowerShell and other common native OS features.
Mitigation
In addition to releasing an out-of-band update, Microsoft has also provided detailed guidance and hunting queries (primarily Exchange log-based). We recommend prioritizing Microsoft’s update, along with the additional guidance made available.
Microsoft KB5000871 – Security update for Microsoft Exchange Server 2019, 2016, and 2013.
Microsoft KB5000978 – Security update for Microsoft Exchange Server 2010 Service Pack 3.
Microsoft MSRC Blog Post – Multiple Security Updates Released for Exchange Server.
Microsoft Blog – New nation-state cyberattacks.
SentinelOne Hunting Packs
SentinelOne query packs are available on Hunter here.
IOCs
Associated Threats: Webshells
SHA256
b75f163ca9b9240bf4b37ad92bc7556b40a17e27c2b8ed5c8991385fe07d17d0
097549cf7d0f76f0d99edf8b2d91c60977fd6a96e4b8c3c94b0b1733dc026d3e
2b6f1ebb2208e93ade4a6424555d6a8341fd6d9f60c25e44afe11008f5c1aad1
65149e036fff06026d80ac9ad4d156332822dc93142cf1a122b1841ec8de34b5
511df0e2df9bfa5521b588cc4bb5f8c5a321801b803394ebc493db1ef3c78fa1
4edc7770464a14f54d17f36dc9d0fe854f68b346b27b35a6f5839adf1f13f8ea
811157f9c7003ba8d17b45eb3cf09bef2cecd2701cedb675274949296a6a183d
1631a90eb5395c4e19c7dbcbf611bbe6444ff312eb7937e286e4637cb9e72944
Attacker Infrastructure
(Note: A majority of the hosts below are VPS/VPN/Cloud service providers. The ‘maliciousness’ of these hosts has a limited shelf-life and may result in false positives if limited to this activity.)
103.77.192.219
104.140.114.110
104.250.191.110
108.61.246.56
149.28.14.163
157.230.221.198
167.99.168.251
185.250.151.72
192.81.208.169
203.160.69.66
211.56.98.146
5.254.43.18
80.92.205.81
MITRE ATT&CK
- T1003.003 – OS Credential Dumping: NTDS
- T1021.002 – Remote Services: SMB/Windows Admin Shares
- TA0010 – Exfiltration
- T1105 – Ingress Tool Transfer
- T1003.001 – OS Credential Dumping: LSASS Memory
- T1059.001 – Command and Scripting Interpreter: PowerShell
- T1114.001 – Email Collection: Local Email Collection
- T1136 – Create Account
- S0020 – China Chopper
- T1027 – Obfuscated Files or Information


