Executive Summary
- A suspected zero-day exploit was used to deliver REvil ransomware to thousands of corporate endpoints.
- Attackers targeted Kaseya VSA servers commonly used by Managed Security Service Providers and IT management firms in order to reach the breadth of their respective customers.
- The attackers abused a variety of benign components, such as certutil.exe, Microsoft Defender, and stolen digital certificates as part of their execution chain.
- At this point, this appears to be the largest mass-scale ransomware incident to date. In an unexpected twist, the attackers are offering a universal decryption tool for all victims at a lump sum of $50 million (originally $70 million).
- In this post, we cover the attack’s execution chain, provide a video showing SentinelOne Singularity’s response against the attack, and provide indicators as well as hunting rules to assist defenders.
What Happened?
On Friday, July 2nd, 2021 a well-orchestrated, mass-scale, ransomware campaign was discovered targeting customers of Kaseya’s managed services software and delivering REvil ransomware. It was initially considered a supply chain attack, a safe assumption at that scale, but with time it became apparent that the attackers were instead leveraging a zero-day exploit against internet-facing Kaseya VSA servers.

Kaseya’s initial advisory underscored the severity of the situation as the company instructed customers to shut down VSA servers until further notice.
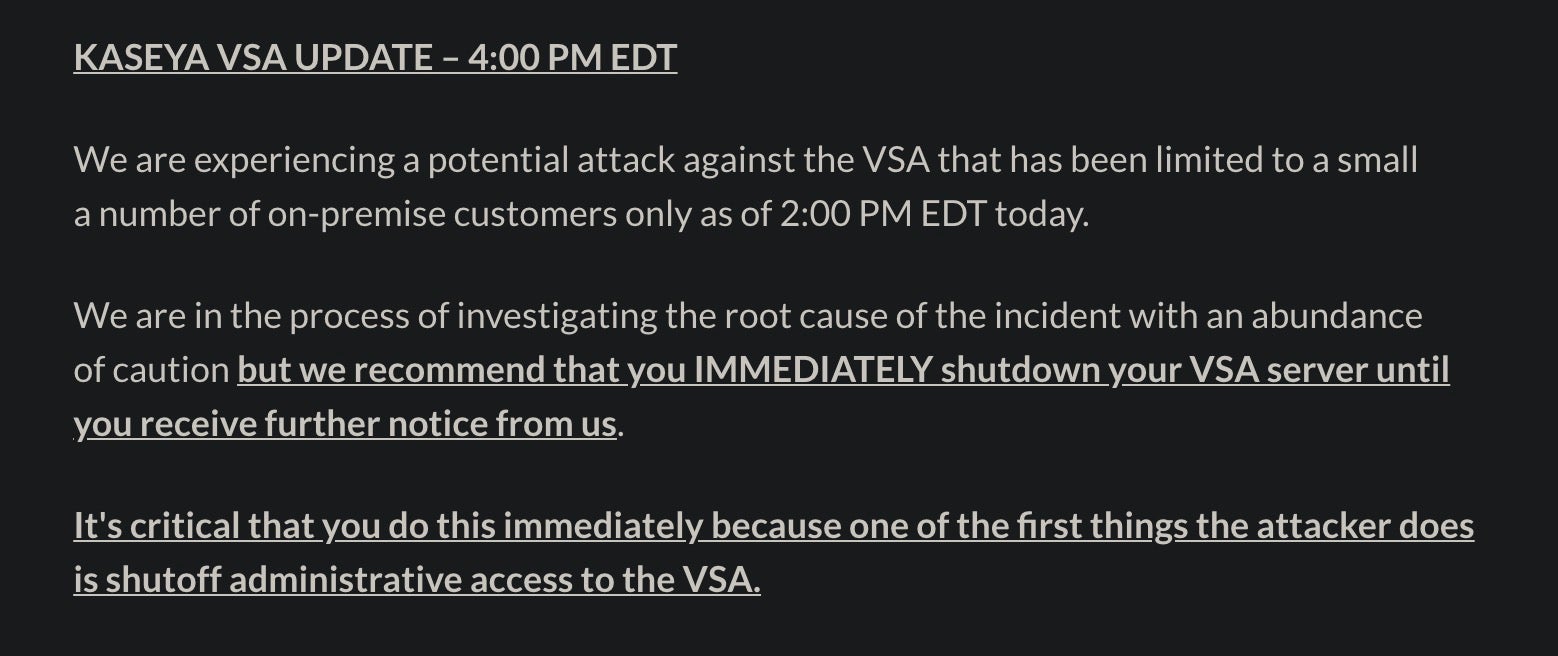
Since then, Kaseya has engaged the security community and triaged the root cause of this incident. This post seeks to unravel the infection chain, highlight relevant indicators, and clarify protections for our customers.
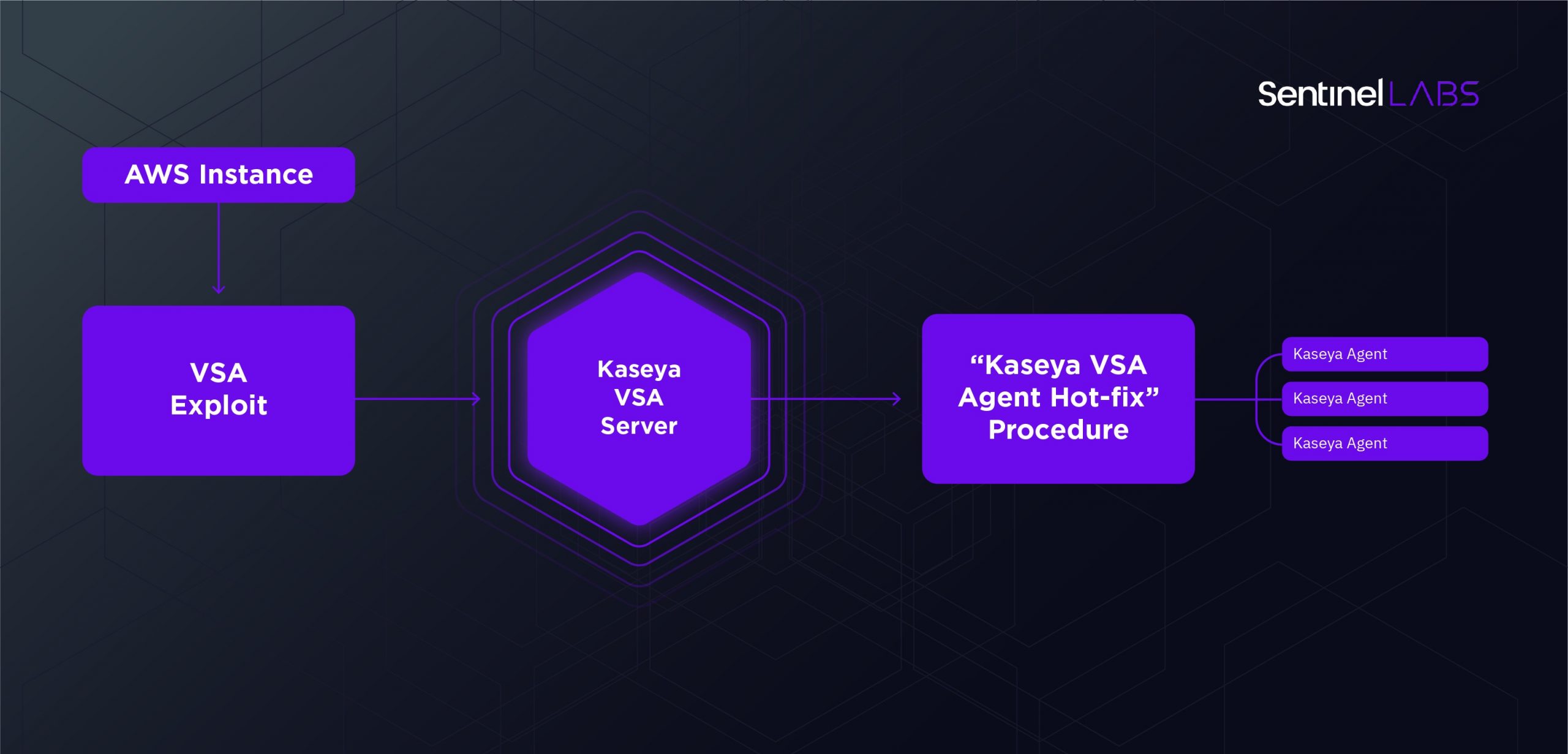
Kaseya VSA Exploit and Infection Chain
Current findings show logic flaws in one of the VSA components (dl.asp) may have led to an authentication bypass. The attackers could then use KUpload.dll to drop multiple files including ‘agent.crt’, a fake certificate that contains the malware dropper. Another dropped artifact, Screenshot.jpg, appears to be a JavaScript file and has only been partially recovered at this time. Specific details regarding the exact nature of the exploit used are still being discovered as the analysis is ongoing.
The suspected exploit chain ends with a SQL injection in userFilterTableRpt.asp in order to queue up a series of VSA procedures that would execute the malware and purge the logs. This activity was seen originating from a hijacked AWS EC2 instance 18.223.199[.]234. Additional activity was observed originating from 161.35.239[.]148 (DigitalOcean), 162.253.124[.]16 (Sapioterra), and 35.226.94[.]113 (Google Cloud).
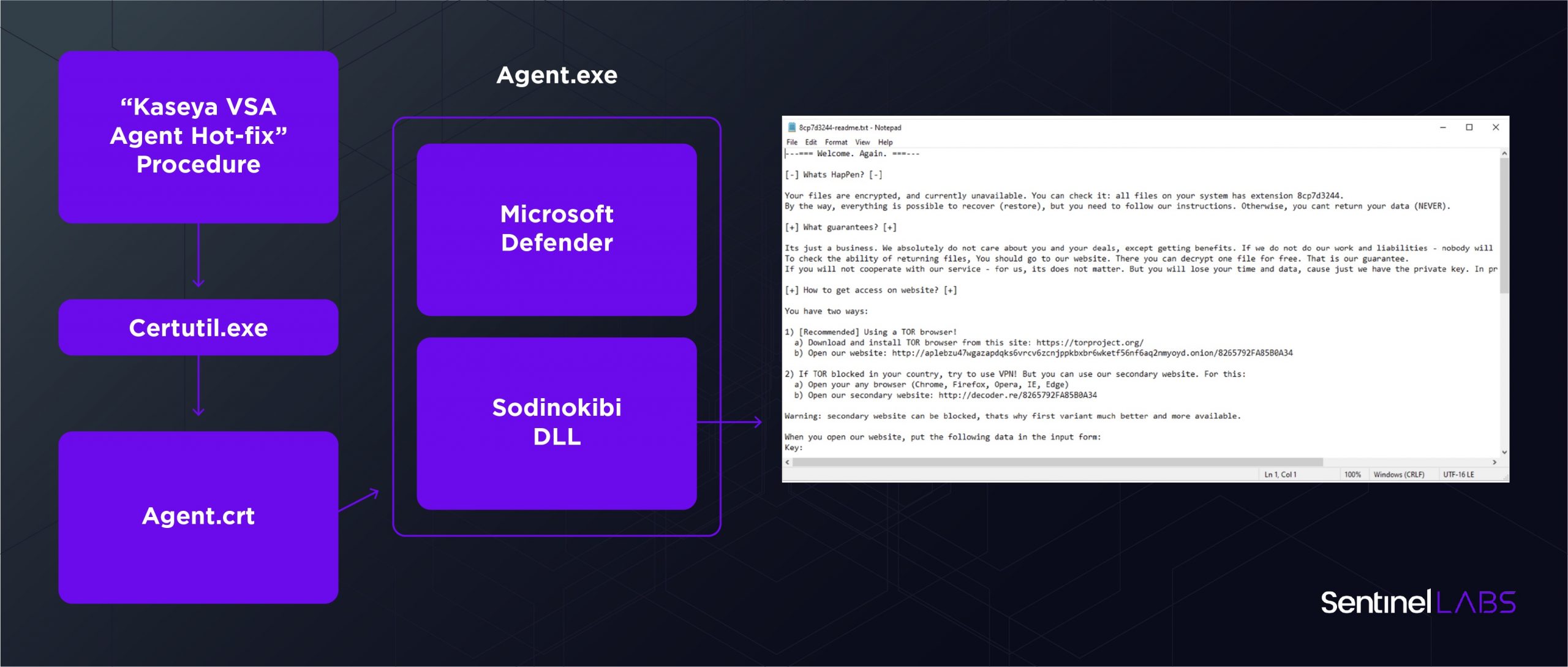
The malicious procedure was labeled ‘Kaseya VSA Agent Hot-fix’. This is a series of commands that check for internet access and use PowerShell to disable a sequence of native Operating System security measures including real-time monitoring, intrusion prevention, network protection, and sample auto-submission. The procedure then invokes the native certutil.exe application commonly used to validate certificates and uses it to decode the contents of ‘agent.crt’ into an executable, agent.exe.
The agent.exe binary was compiled on July 1st, 2021 and acts as a dropper for two embedded executable resources, ‘MODLIS’ and ‘SOFTIS’.
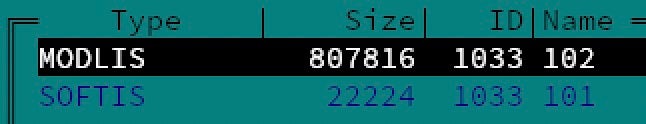
Resource 101, SOFTIS is an outdated legitimate Microsoft Defender executable that is being used to sideload the malicious payload. It’s worth noting that this delivery mechanism of a sideloading dyad (a two-part execution chain) has been used to deliver REvil as early as April 2021.
The payload itself is contained in resource 102, under the resource name ‘MODLIS’.
SHA256 e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2 SHA1 e1d689bf92ff338752b8ae5a2e8d75586ad2b67b MD5 7ea501911850a077cf0f9fe6a7518859 Compilation Timestamp 2021-07-01 12:39:06 Signature Date 2021-07-02 23:15:00 Size 788.88 KB Digital Signature PB03 TRANSPORT LTD.
In order for the malicious payload to be sideloaded by Microsoft Defender, the DLL is dropped at %WinDir%MpSvc.dll and exports the functions ServiceCrtMain, ServiceMain, and SvchostPushServiceGlobals. The file is signed with a stolen digital certificate from a Canadian transport company. It’s one of several stolen certificates recently employed by REvil. The ransomware employs statically-linked OpenSSL to conduct its cryptographic operations. ServiceCRTMain() creates a thread that will deobfuscate the main payload.
While the IOCs directly relevant to the Kaseya incident are a specific subset, we have collected samples for a cluster of similar execution chains including the Microsoft Defender sideloading dyad and still valid stolen digital certificates. We have provided hashes and YARA signatures at the end of this post to help identify additional files signed with these stolen certificates.
During this process, netsh.exe (as we have seen with prior REvil samples) is also called, making the following adjustment to local firewall rules:
netsh.exe netsh advfirewall firewall set rule "group=Network Discovery" new enable=Yes
The following are still valid signers. We have provided YARA signatures at the end of this post to help identify additional files signed with these stolen certificates.
- BUKTBAI, OOO
thumbprint = “282ebc0a99a6328343a7d7706465778c3925adb6” - PB03 TRANSPORT LTD
thumbprint = “11ff68da43f0931e22002f1461136c662e623366” - OOO Saylent
thumbprint = “0d61738e6407c01d5c9f477039fb581a5f81f436”
Encryption and Post Encryption Behavior
The Salsa20 encryption algorithm used by this variant of the REvil ransomware is incredibly fast compared to other common encryption algorithms and is an optimal choice for a ransomware operation of this magnitude. Other highly-prolific ransomware families have employed the same algorithm (e.g., DarkSide & later variations of Petya / GoldenEye).
Once the contents of the machine have been successfully encrypted, ransom notes are dropped alongside encrypted files and the machine’s wallpaper is changed to alert users to their predicament.
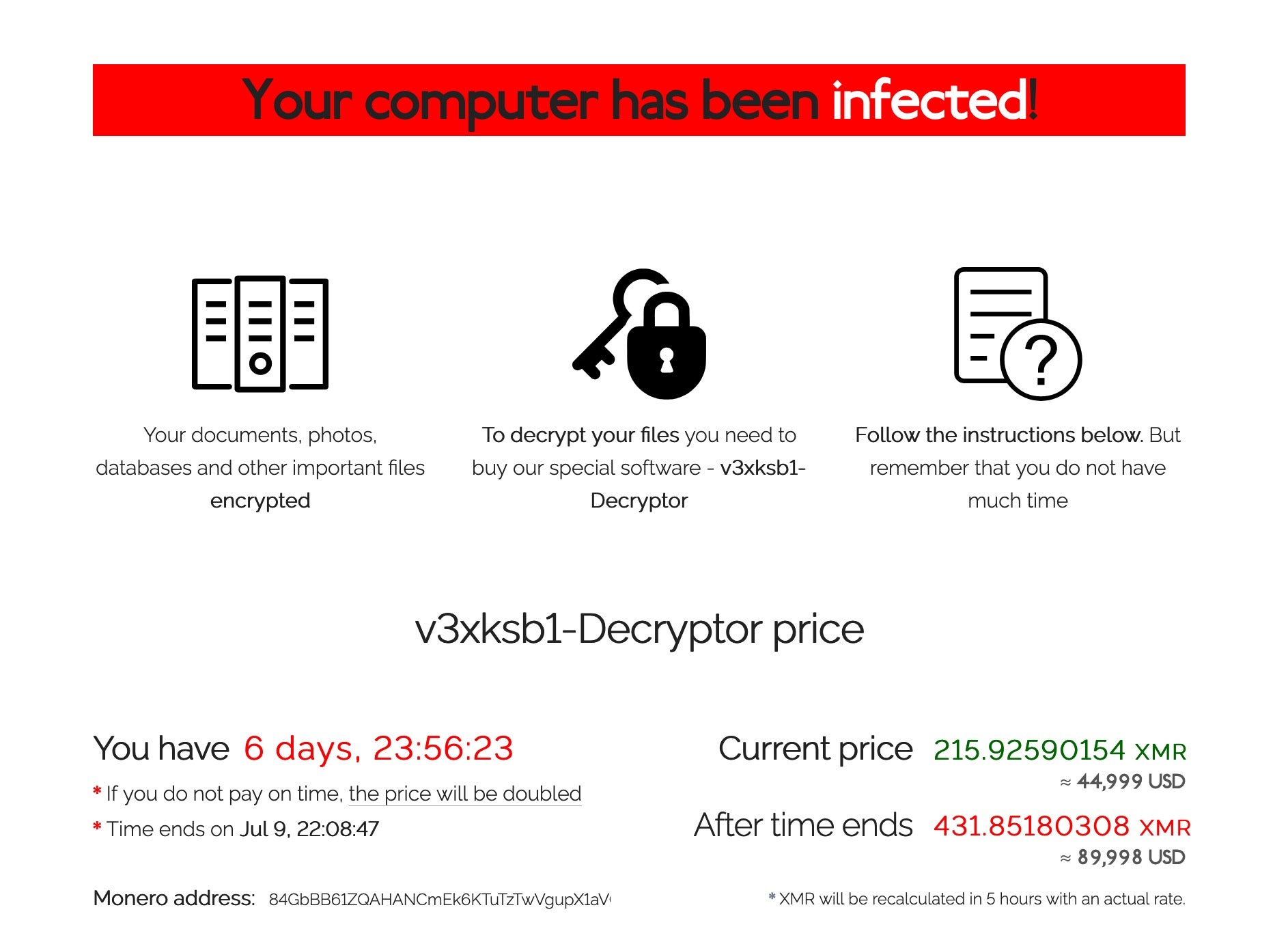
The ransom note directs users to an .onion site and an alternative for those that don’t have access to TOR. The site asks for the key appended to the ransom note before providing a ransom amount for that specific endpoint, along with a timer that indicates how long the victim has to pay before the ransom demand increases. The standard demand for a non-corporate domain machine is the equivalent of $44,999 in Monero (XMR) or Bitcoin (BTC). Taking a broader view, the REvil gang has reportedly offered a universal decrypter for the eye-watering lump sum of $70 million (later amended to $50 million).
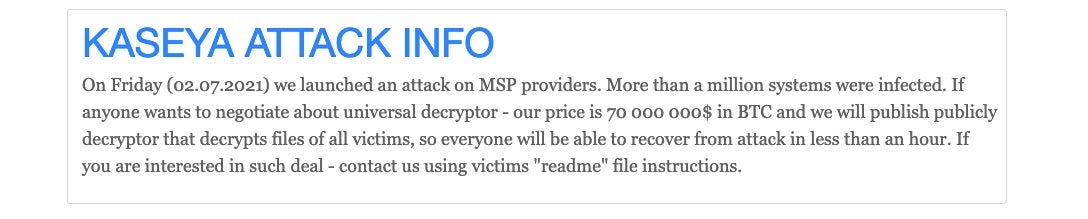
Latest Developments
On Monday, July 5, Kaseya announced they are developing a new patch for on-premise installations in order to assist customers in getting back to service. Kaseya also published a Compromise Detection Tool for customers to check if their on-premise installation had been actually compromised.
Since this outbreak, attackers have been scanning for Kaseya on-premise internet exposed servers using publicly available platforms such as Shodan.io. This time window allows attack groups besides REvil to obtain immediate access over the internet to customer-sensitive networks.
This attack proves again the necessity for a modern EDR solution which defends against improper use of built-in operating system executables (LOLBINs), such as detecting certutil.exe writing executables or usage of signed software such as MsMpEng.exe running from unexpected locations and executing unexpected software.
This threat is detected and mitigated by SentinelOne:
Conclusions
While the full impact of this attack is still unfolding, it’s a further escalation in the sophistication of cybercrime, not only on the technical side but also in how the attack was orchestrated. It’s clear that the perpetrators are well aware of the PR implications and will use widespread disruptions to try to maximize the payouts. This is yet another reminder of why security products need to leverage the power of data, specifically rich behavioral data, and AI. Malware and ransomware are increasingly cunning and novel in their techniques to compromise devices. A data-driven and AI-powered approach creates an autonomous posture to cybersecurity. It’s not enough to use signature-based or human-powered legacy solutions to protect your organization’s attack surfaces as every second counts when defending from advanced attacks like this one.
While we continue to uncover the full ramifications of this attack, our advice to defenders is to always act under the assumption that their networks are already host to malicious actors. The exorbitant profits realized by cyber criminals will only add to the sophistication of the attacks we’ll continue to see, the means and motivations are already there. Ransomware is a reality that every organization must face operating in the digital age. Cybersecurity today has become a critical part of corporate operations: the ability for malicious actors to disrupt and profit has reached new levels of relevance as a possible existential threat to businesses.
Indicators of Compromise
Samples
agent.crt encoded dropper
2093c195b6c1fd6ab9e1110c13096c5fe130b75a84a27748007ae52d9e951643
agent.exe dropper
d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
Payloads
e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2
8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
Additional recent REvil activity including dyad droppers and payloads with still valid stolen digital signatures:
aae6e388e774180bc3eb96dad5d5bfefd63d0eb7124d68b6991701936801f1c7
df2d6ef0450660aaae62c429610b964949812df2da1c57646fc29aa51c3f031e
f6908ef76b666157a13534db47652a845d8f7d985fdf944f7e43a3afd3f3d8c2
d5ce6f36a06b0dc8ce8e7e2c9a53e66094c2adfc93cfac61dd09efe9ac45a75f
d8353cfc5e696d3ae402c7c70565c1e7f31e49bcf74a6e12e5ab044f306b4b20
dc6b0e8c1e9c113f0364e1c8370060dee3fcbe25b667ddeca7623a95cd21411f
cc0cdc6a3d843e22c98170713abf1d6ae06e8b5e34ed06ac3159adafe85e3bd6
81d0c71f8b282076cd93fb6bb5bfd3932422d033109e2c92572fc49e4abc2471
MITRE TTPs Used in Kaseya Attack
T1112 – Modify Registry
T1012 – Query Registry
T1082 – System Information Discovery
T1120 – Peripheral Device Discovery
T1491 – Defacement
T1543.003 – Create or Modify System Process: Windows Service
T1036 – Masquerading
T1036.003 – Masquerading: Rename System Utilities
T1202 – Indirect Command Execution
T1486 – Data Encrypted for Impact
T1106 – Native API
YARA Hunting Rules for REvil/Kaseya Artifacts
import "pe"
import "math"
rule cw_REvil_Kaseya_BUKTBAI_stolenCert
{
meta:
desc = "Stolen digital certificate: BUKTAI"
author = "JAG-S @ SentinelLabs"
last_modified = "07.02.2021"
version = "1.0"
hash = "d8353cfc5e696d3ae402c7c70565c1e7f31e49bcf74a6e12e5ab044f306b4b20"
hash = "d5ce6f36a06b0dc8ce8e7e2c9a53e66094c2adfc93cfac61dd09efe9ac45a75f"
hash = "df2d6ef0450660aaae62c429610b964949812df2da1c57646fc29aa51c3f031e"
hash = "aae6e388e774180bc3eb96dad5d5bfefd63d0eb7124d68b6991701936801f1c7"
condition:
uint16(0) == 0x5a4d
and
for any signer in pe.signatures:
(
signer.subject == "/C=RU/L=Samara/O=BUKTBAI, OOO/CN=BUKTBAI, OOO"
or
signer.serial == "42:c1:64:9a:6b:80:64:0f:ad:7a:fb:b8:3e:29:81:52"
or
signer.thumbprint == "282ebc0a99a6328343a7d7706465778c3925adb6"
)
}
rule cw_REvil_Kaseya_PB03TRANSPORT_stolenCert
{
meta:
desc = "Stolen digital certificate: PB03 TRANSPORT"
author = "JAG-S @ SentinelLabs"
last_modified = "07.02.2021"
version = "1.0"
hash = "8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd"
hash = "e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2"
hash = "d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e"
condition:
uint16(0) == 0x5a4d
and
for any signer in pe.signatures:
(
signer.subject == "/C=CA/ST=Ontario/L=Brampton/O=PB03 TRANSPORT LTD./CN=PB03 TRANSPORT LTD."
or
signer.serial == "11:9a:ce:ad:66:8b:ad:57:a4:8b:4f:42:f2:94:f8:f0"
or
signer.thumbprint == "11ff68da43f0931e22002f1461136c662e623366"
)
}
rule cw_REvil_Kaseya_SAYLENT_stolenCert
{
meta:
desc = "Stolen digital certificate: PB03 TRANSPORT"
author = "JAG-S @ SentinelLabs"
last_modified = "07.02.2021"
version = "1.0"
hash = "cc0cdc6a3d843e22c98170713abf1d6ae06e8b5e34ed06ac3159adafe85e3bd6"
hash = "dc6b0e8c1e9c113f0364e1c8370060dee3fcbe25b667ddeca7623a95cd21411f"
condition:
uint16(0) == 0x5a4d
and
for any signer in pe.signatures:
(
signer.subject == "/C=RU/L=Cherepovetz/O=OOO Saylent/CN=OOO Saylent"
or
signer.serial == "00:bd:df:46:f3:a2:de:7d:2b:fb:f5:16:9a:e9:76:d9:7e"
or
signer.thumbprint == "0d61738e6407c01d5c9f477039fb581a5f81f436"
)
}
rule cw_REvil_Kaseya_Dropper
{
meta:
desc = "Dropper for Microsoft Defender + Sodinokibi DLL Sideload"
author = "JAG-S @ SentinelLabs"
last_modified = "07.02.2021"
version = "1.0"
hash = "df2d6ef0450660aaae62c429610b964949812df2da1c57646fc29aa51c3f031e"
hash = "dc6b0e8c1e9c113f0364e1c8370060dee3fcbe25b667ddeca7623a95cd21411f"
hash = "aae6e388e774180bc3eb96dad5d5bfefd63d0eb7124d68b6991701936801f1c7"
hash = "81d0c71f8b282076cd93fb6bb5bfd3932422d033109e2c92572fc49e4abc2471"
strings:
$drop_ransom = "mpsvc.dll" ascii wide fullword
$drop_defender = "MsMpEng.exe" ascii wide fullword
$drop_path = "C:\Windows\" wide fullword
condition:
uint16(0) == 0x5a4d
and
(
2 of ($drop*)
and
pe.number_of_resources == 2
and
for all rsrc in pe.resources:
(
math.entropy(rsrc.offset, rsrc.length) >= 6.7
)
)
}


