From remote code execution and privilege escalation to security bypasses and path traversal, software vulnerabilities are a threat actor’s stock-in-trade for initial access and compromise. In the past 12 months, we’ve seen a number of new flaws, including Log4Shell, ProxyShell, and ProxyLogon, being exploited in attacks against enterprises. These and other known bugs, some revealed as far back as 2017, continue to be routinely abused in environments where organizations have failed to properly inventory and patch. As CISA released its latest update on the most commonly exploited vulnerabilities, we take a look at each of the top 15 most routinely exploited bugs being used against businesses today.

1. Log4Shell (CVE-2021-44228)
Occupying top spot is the notorious flaw in the Apache Java logging library, Log4j, that was first revealed at the close of 2021. This remote code execution vulnerability is widely exploited due to the prevalence of the Log4j library in web applications. It came as a surprise to many organizations and network administrators to even learn that they had this dependency in their software stack.
As details of the vulnerability emerged, responsible organizations scrambled to understand their exposure and apply patches in a timely manner, a process complicated by the fact that several early attempts to patch the bug were soon revealed to be inadequate by researchers. Nevertheless, the presence of Log4Shell at the top of the list of most routinely exploited bugs shows that there are many organizations out there that still haven’t taken appropriate action.
For more details on this vulnerability, see here. For help with mitigation, see here.
2. Zoho ManageEngine ADSelfService Plus (CVE-2021-40539)
Zoho ManageEngine ADSelfService Plus, up to and including version 6113, was found to be vulnerable to a REST API authentication bypass and subsequent remote code execution. The bug, patched in September 2021, allows attackers to use specially-crafted Rest API URLs to bypass authentication due to an error in normalizing the URL before attempting validation. Having bypassed the authentication filter, attackers are able to exploit endpoints and perform attacks such as arbitrary command execution.
The bug is easy to weaponize, and the software is common in the enterprise, with the flaw present in the product’s default configuration. This combination provides high-value for attackers and it’s no surprise that threat actors are actively seeking out and exploiting enterprises with vulnerable versions of this software.
For more information and mitigation advice, see here.
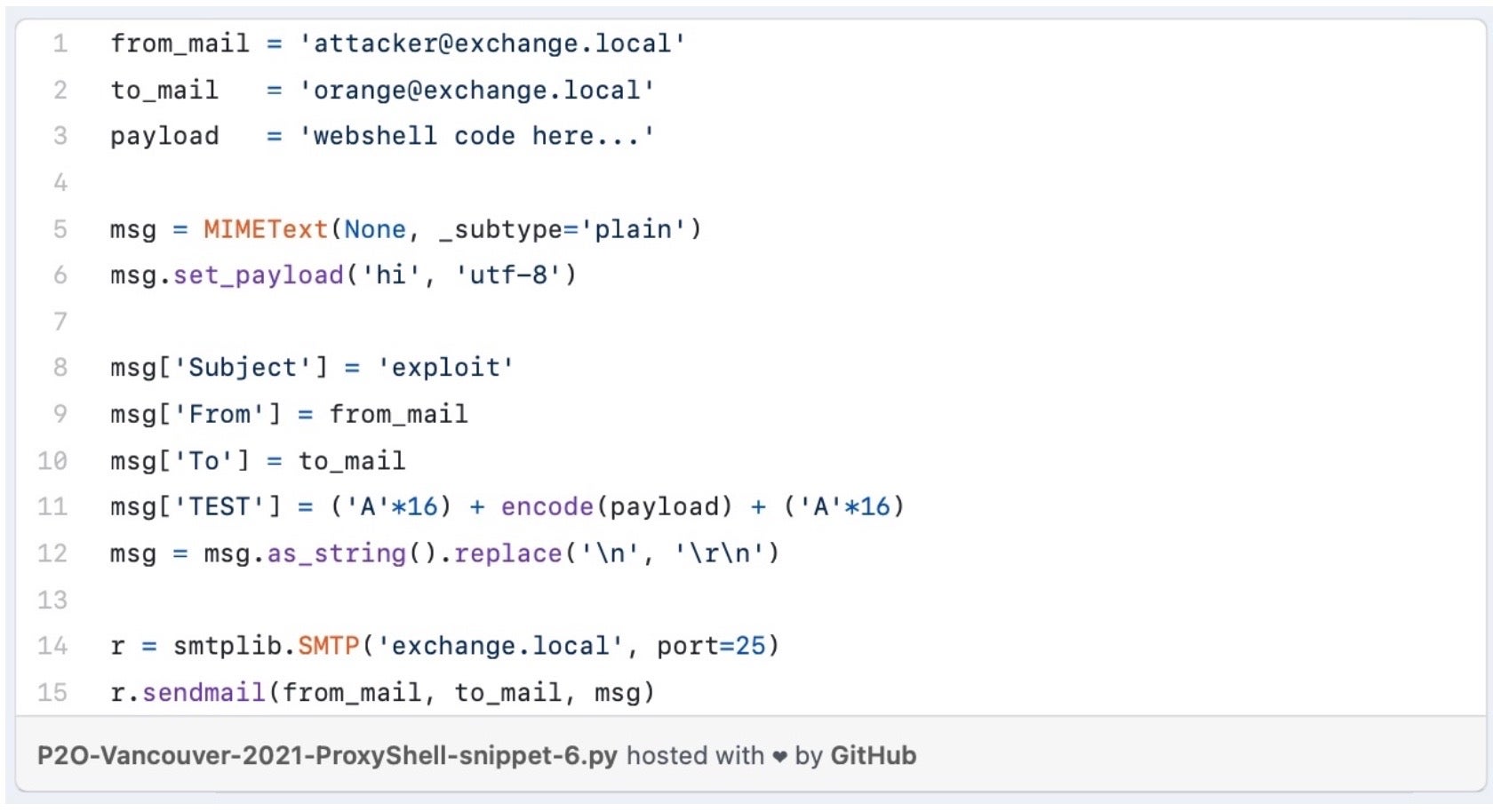
3 – 5. ProxyShell (CVE-2021-31207, CVE-2021-34473, CVE-2021-34523)
ProxyShell consists of three separate flaws in Microsoft Exchange email server, allowing security feature bypass, RCE and elevation of privilege. When chained together in exposed environments, ProxyShell enables an attacker to establish persistence and execute malicious PowerShell commands. Successful exploitation allows threat actors to take full control of vulnerable Microsoft Exchange email servers.
CISA notes that these bugs, first revealed in August 2021, reside within the Microsoft Client Access Service (CAS), a service which typically runs on port 443 in Microsoft Internet Information Services (IIS), and is commonly exposed to the internet so that users can access email from mobile devices and web browsers.
As with many of these CVEs, Proof of Concept code along with documentation is publicly available, making this collection of vulnerabilities highly attractive to attackers.
For more information and mitigation on ProxyShell, see the advisories here, here, and here.
6 – 9. ProxyLogon (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065)
It’s been a tough twelve months or so for organizations running Microsoft Exchange server. Prior to ProxyShell last August came four actively-exploited zero days, collectively known as ProxyLogon in March 2021. These four vulnerabilities occupy the next four positions from 6 to 9 of the 15 most routinely exploited bugs.
ProxyLogon affects Microsoft Exchange 2013, 2016, and 2019. The flaws were initially discovered after being found leveraged in the wild by the HAFNIUM Chinese-based APT, but they have since gone on to be exploited by a wide-range of other threat actors given that the bugs exist in default configurations of widely-deployed enterprise software. Malicious actors are known to use automated tools to actively scan for and identify unpatched servers.
The four CVEs relate to untrusted connections to the Exchange server on port 443 and can be exploited without user interaction. ProxyLogon allows threat actors to bypass authentication, read emails, and deploy malware in enterprise networks. In the initial attacks by the HAFNIUM group, webshells of various types were deployed and additional tools were used to facilitate lateral movement, persistent access, and remote manipulation. Open source tools such as PowerCAT, Nishang, 7zip, WinRAR, and Procdump were also utilized in the HAFNIUM campaigns.
For more details about ProxyLogon see here. For assistance with mitigation, see here.
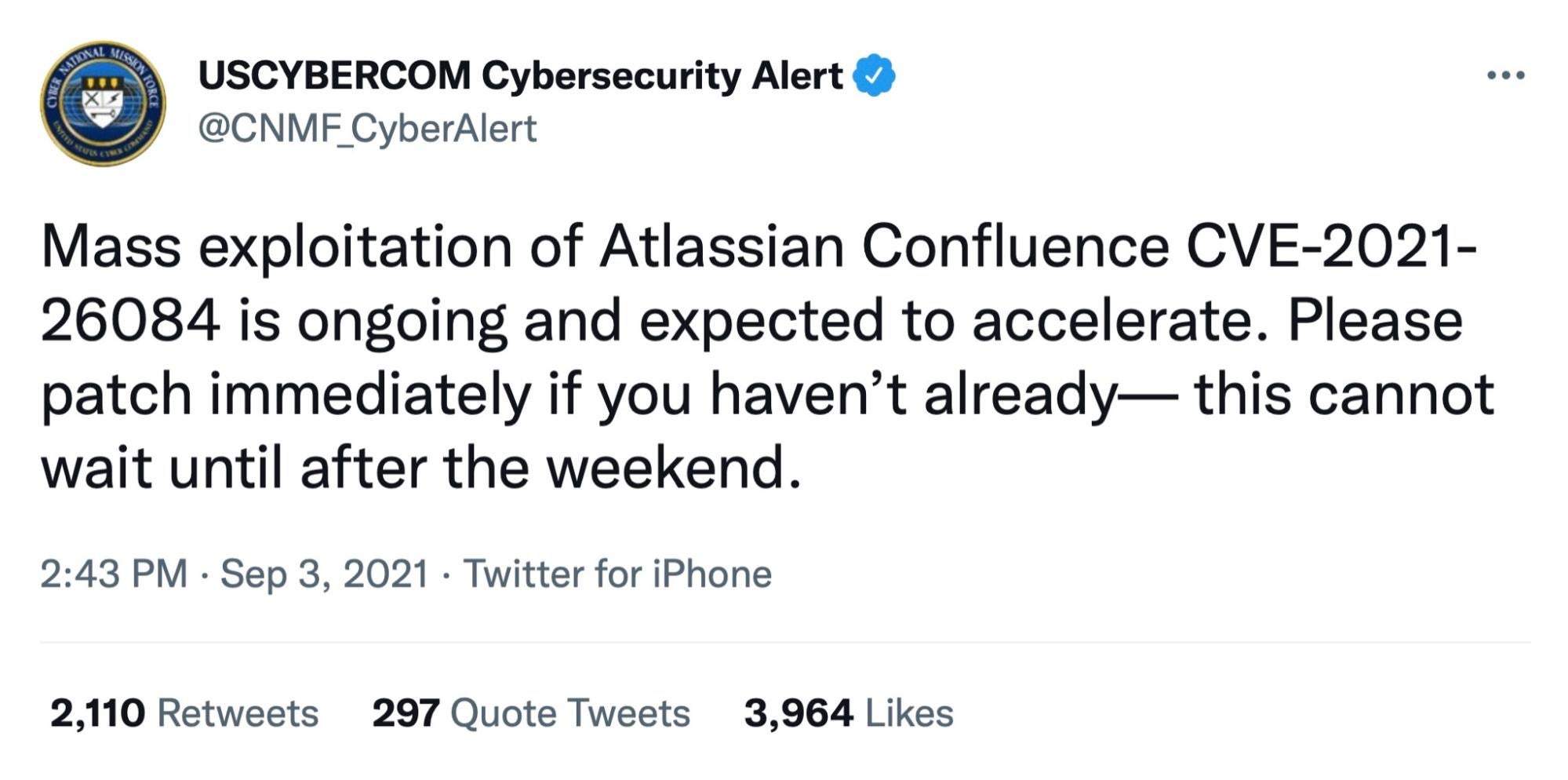
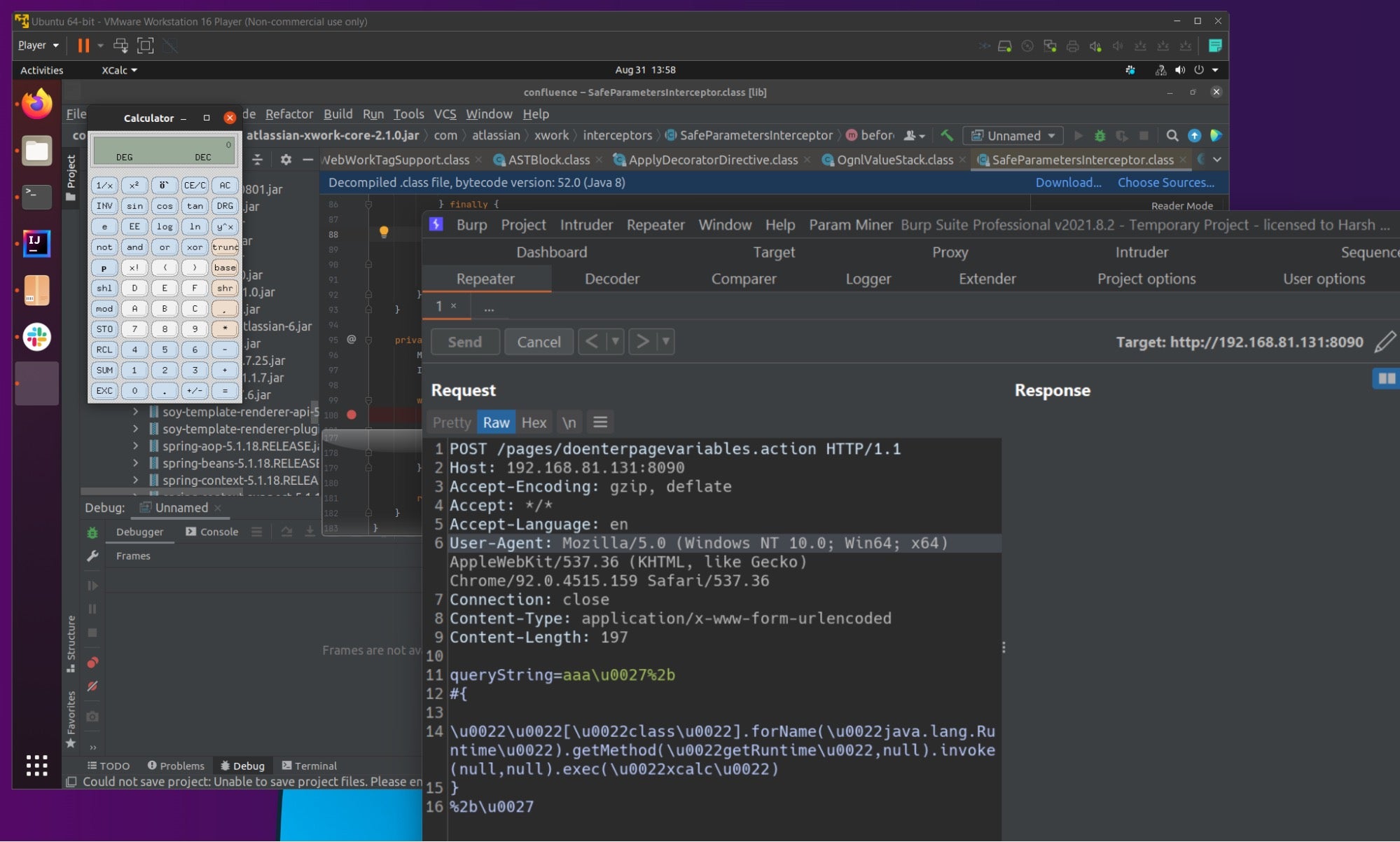
10. Atlassian Confluence Server & Data Center (CVE-2021-26084)
CVE-2021-26084 is a critical severity security vulnerability that allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance. Confluence is a Wiki-style service widely deployed in enterprise environments. Disclosed in August 2021, the vulnerability was, and continues to be, actively exploited in the wild since it is exploitable by unauthenticated users regardless of configuration. Unfortunately, the initial disclosure went unheeded in many enterprises, and by September, USCYBERCOM were warning of ongoing mass exploitation.
The bug allows a threat actor to execute commands with the same permissions as the user running the service. While it was initially thought that the flaw was only exploitable by a user with a valid account on the system, it subsequently turned out that any unauthenticated user could trigger the vulnerability. Public exploit code exists and is actively being used by threat actors against vulnerable instances.
For more details and mitigation advice, see the advisory here.
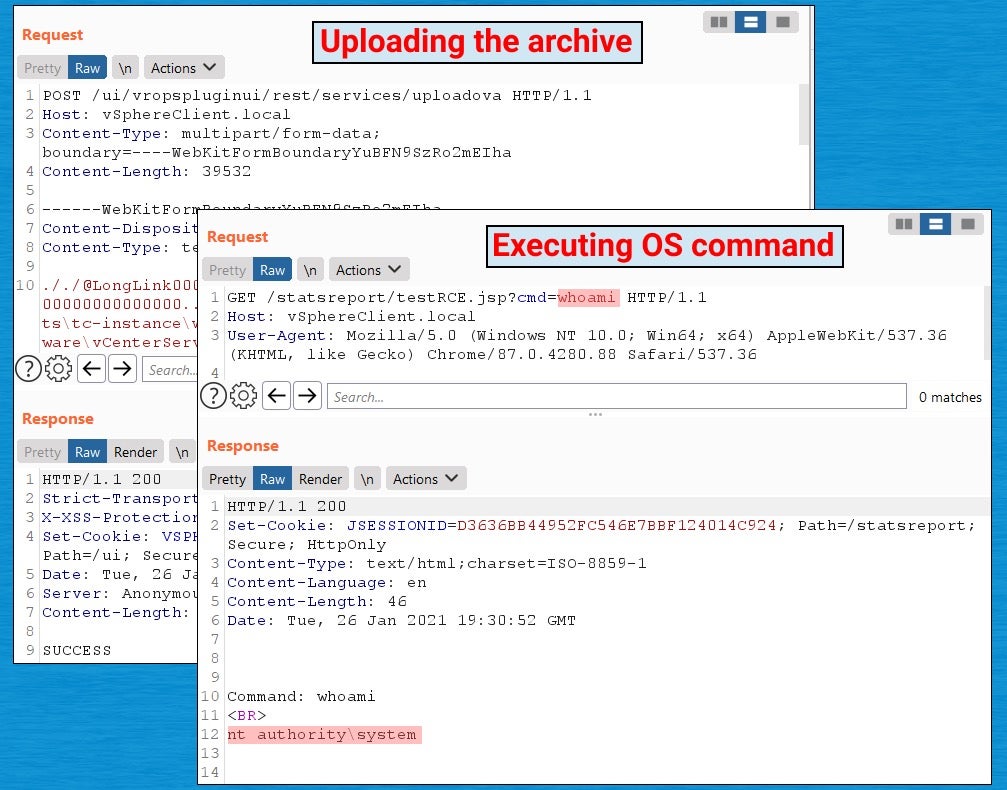
11. VMware vSphere Client (CVE-2021-21972)
In February 2021, VMware disclosed that the vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin, rating the vulnerability as Critical with a severity rating of 9.8.
VMware vSphere is a suite of server virtualization products for corporate infrastructure and includes ESXi hypervisor and vCenter management software. The software is commonly located on internal networks. Exploiting CVE-2021-21972 allows a malicious actor with network access to port 443 to execute commands with unrestricted privileges on the host operating system.
Mass scanning targeting vulnerable VMware vCenter servers was soon reported, and Proof of Concept code to exploit the vulnerability has been published online.
For more information and mitigation help, see the advisory here.
12. ZeroLogon (CVE-2020-1472)
Not all of the 15 most routinely exploited vulnerabilities were discovered last year; others continue to be exploited even though mitigations for them have long been available. Chief among these is the notorious ZeroLogon bug from August 2020. Revealed a month after Microsoft patched it, ZeroLogon is an elevation of privilege bug that revolves around a cryptographic flaw in Microsoft’s Active Directory Netlogon Remote Protocol (MS-NRPC). By exploiting the bug, an unauthenticated attacker can log on to servers that are using NT LAN Manager (NTLM).
The vulnerability lies in the fact that, in attempting to implement a custom encryption algorithm in MS-NRPC, Microsoft made a critical mistake such that the initialization vector (IV) is set to all zeros rather than a random number. Exploiting the vulnerability allows a remote attacker to forge an authentication token for Netlogon and to set the computer password of the domain controller to a known value. Malicious actors can leverage this vulnerability to compromise other devices on the network. Subsequently, researchers discovered other ways to operationalize Zerologon, including extracting all domain passwords.
Zerologon has been observed in the attack chain of ransomware actors such as Ryuk and multiple public POC exploits are available.
For more information on ZeroLogon see here. For help with mitigation, see here.
13. Microsoft Exchange Server (CVE-2020-0688)
Also first revealed in 2020, CVE-2020-0688 is another remote code execution vulnerability in Microsoft Exchange Server that occurs when the server fails to properly create unique keys at install time. According to the CVE, knowledge of the validation key allows an authenticated user with a mailbox to pass arbitrary objects to be deserialized by the web application, which runs as SYSTEM.
In September of 2020, CISA advised that Chinese-affiliated actors were exploiting CVE-2020-0688 for remote code execution to enable email collection of targeted networks. In July 2021 and again in February 2022, CISA further advised that Russian-affiliated threat actors were exploiting CVE-2020-0688 to escalate privileges and gain remote code execution on vulnerable Microsoft Exchange servers.
For more information on CVE-2020-0688 and help with mitigation, see here.
14. Pulse Secure Pulse Connect Secure (CVE-2019-11510)
CVE-2019-11510 is a vulnerability affecting Pulse Secure VPN appliances which allows threat actors to gain access to victim networks. An unauthenticated remote attacker can send a specially crafted URI to perform an arbitrary file reading vulnerability. This flaw has been exploited by both Chinese and Russian actors, and used in extended campaigns targeting COVID-19 research data during the recent pandemic.
Patches were released for this vulnerability in April 2019; however, multiple incidents have occurred where compromised AD credentials were used months after victim organizations patched their VPN appliance. CISA also says that it has responded to numerous incidents at U.S. Government and commercial entities where malicious cyber threat actors have exploited CVE-2019-11510.
15. Fortinet FortiOS and FortiProxy (CVE-2018-13379)
Four years in the wild and still making it into the top 15 most routinely exploited vulnerabilities, CVE-2018-13379 is a path traversal vulnerability in the FortiProxy SSL VPN web portal. On exploitation, the bug may allow a non-authenticated, remote attacker to download FortiProxy system files through specially crafted HTTP resource requests.
As you would expect from a vulnerability that has been exploited for over 4 years, it has a long and storied history and has been used to deploy ransomware as well as steal data. CISA has released several advisories over the years detailing its use by both Russian and Iranian state actors.
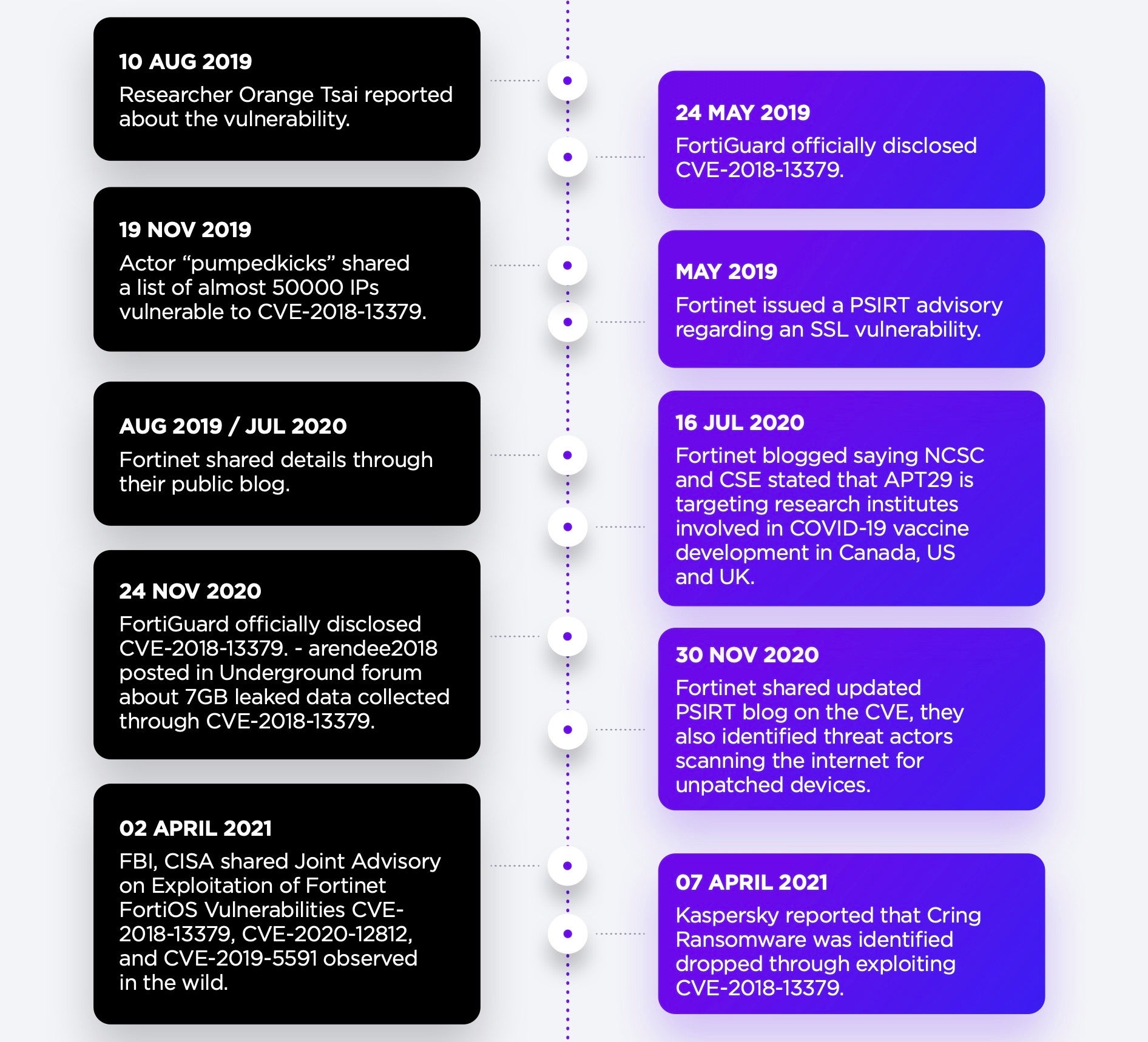
As recently as February 2022, SentinelLabs tracked Iranian-aligned threat actor TunnelVision as making good use of CVE-2018-13379, along with other vulnerabilities mentioned above like Log4Shell and ProxyShell, to target organizations.
For more information and mitigation advice on CVE-2018-13379, see the advisory here.
Conclusion
Successful enterprise security teams understand that old vulnerabilities never go away, and while the focus and the fire drills are often around the latest CVEs to hit the news, CISA’s annual list of most routinely exploited vulnerabilities offers a cautionary tale to us all: find the vulnerabilities in your software stack before threat actors do. It’s important to remember that from an attacker’s point of view, targeting old flaws remains a successful attack vector and is less work than discovering and developing new zero days, particularly when most critical flaws typically have publicly available Proof of Concept exploit code.
We hope that by bringing attention to this list, enterprise security teams will make renewed effort to ensure that they are not the next ones to suffer a compromise from an unpatched software dependency.
If you would like to see how SentinelOne can help your organization to defend against attacks of all kinds, contact us or request a free demo.