2018 was a great year for the SentinelOne blog, with 335% YOY increase in page views!
During 2018 we covered new malware and ransomware, shared educational pieces about security essentials, dived deep into macOS security, and conducted some Windows internal research. Before starting to work on our next publications, we wanted to stop for a few minutes and see what you, our readers, really liked this year. Ready?
Favorite Topics
According to our traffic logs, in 2018 you wanted to know how SentinelOne technology works, watch how malware and ransomware can compromise devices, and how SentinelOne can seamlessly roll it back. Fileless malware was also popular along with security essentials: signs of weak passwords, what is Phishing, what is Windows PowerShell, and Crypto Jacking. You also loved exploring our integration with Microsoft ATP, reading about our blockbuster ebook: “90 DAYS | A CISO’S JOURNEY TO IMPACT” (chapter 2 is coming), and more.
On the macOS front, we demonstrated how important it is to have a security product on top of Apple’s built-in mechanisms. On the research front, we covered Deep Hooks: Monitoring native execution in WoW64 application and What Really Matters with Machine Learning.
Here are the most popular posts of last year:
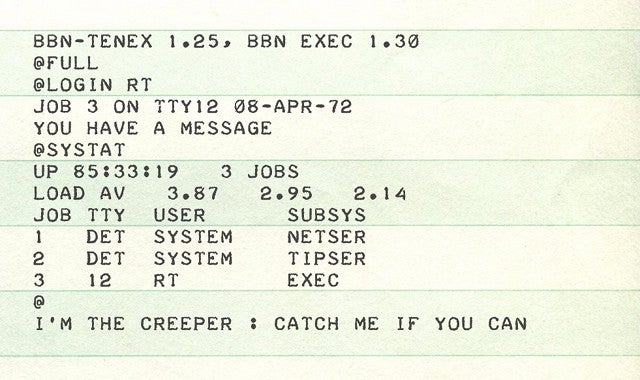
1. THE HISTORY OF CYBER SECURITY — EVERYTHING YOU EVER WANTED TO KNOW
Our winning post covers the history of cybersecurity. It began with a research project. A man named Bob Thomas realized that it was possible for a computer program to move across a network, leaving a small trail wherever it went. He named the program Creeper, and designed it to travel between Tenex terminals on the early ARPANET, printing the message “I’M THE CREEPER: CATCH ME IF YOU CAN.”
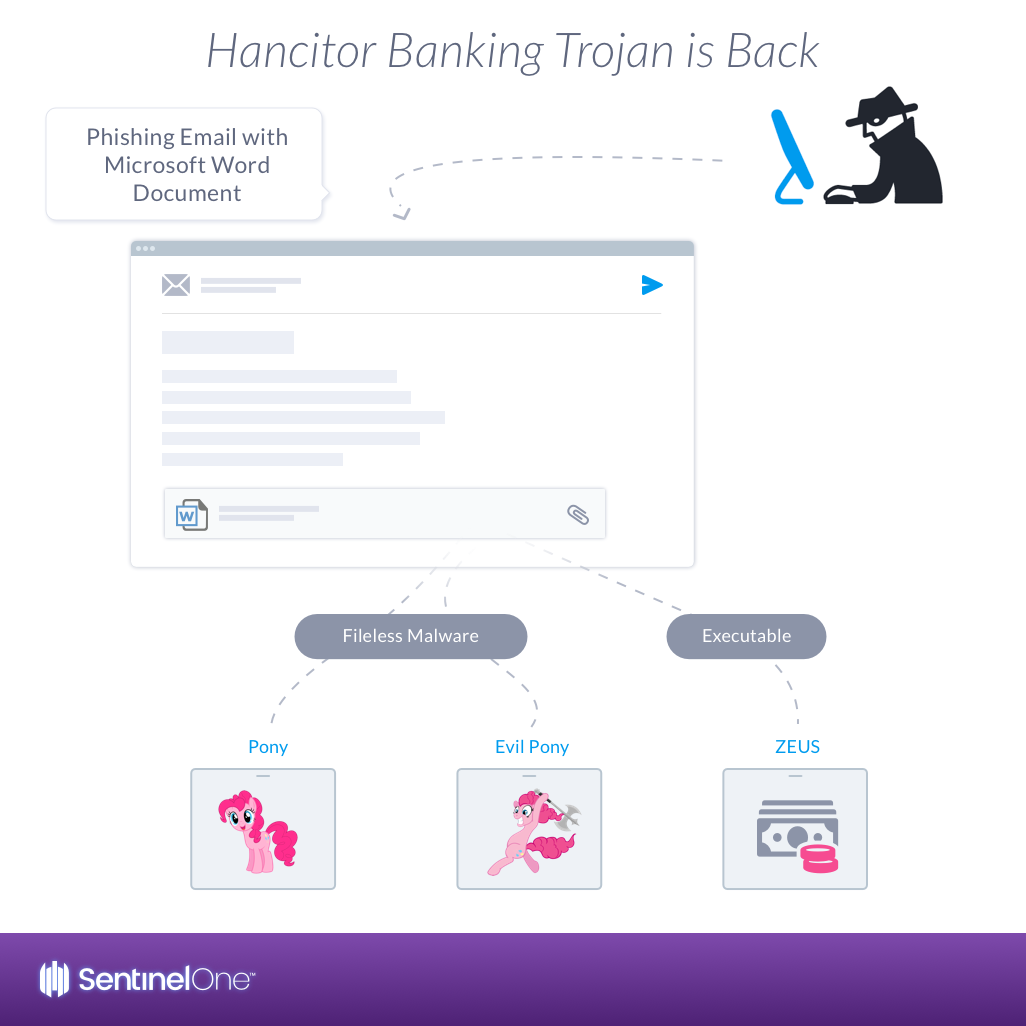
2. HANCITOR BANKING TROJAN IS BACK | USING MALICIOUS WORD ATTACHMENT
The Hancitor trojan, also known as Chanitor, took the 2nd place. Hancitor trojan is a downloader first observed in 2014. Back then, it distributed its payload via a Microsoft Word document email attachment with embedded malicious macros. Over the years, several flavors have been seen in the wild using a variety of infection techniques.
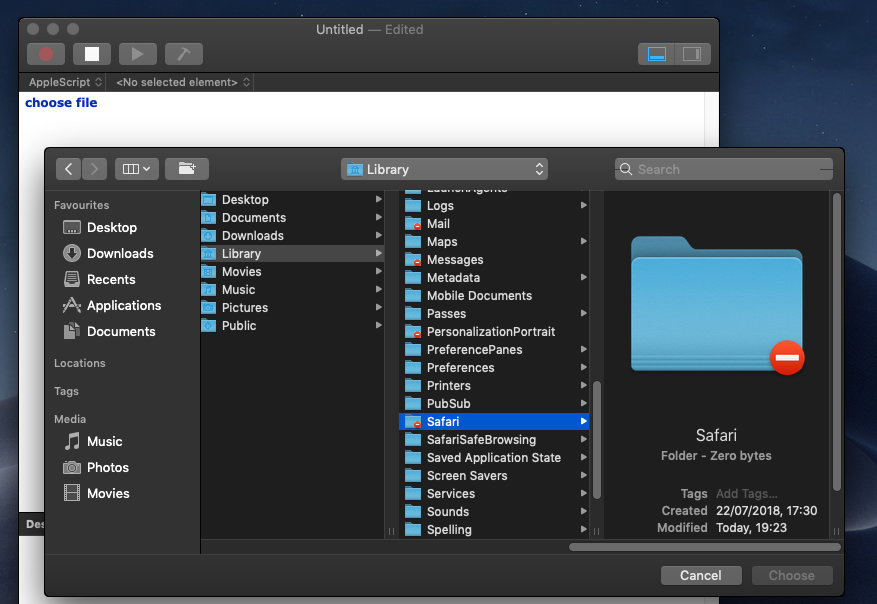
3. MOJAVE’S SECURITY “HARDENING” | USER PROTECTIONS
With Mojave’s security hardening, any local or remote user can bypass Apple’s new Full Disk Access requirement using ssh. Find out how we kept you safe!
Happy new year from SentinelOne marketing team!


