Despite determined efforts to neutralize it, GandCrab ransomware has continued to evolve and spread throughout 2018. We took it for a ride.
GandCrab is an aggressive piece of malware that has struck nearly half a million victims since it was first detected in January 2018. It uses a variety of infection vectors to compromise endpoints including email campaigns, websites and exploit kits such as Rig and GrandSoft.
The first stage of the infection collects data such as the computer name, OS version, and whether any legacy AV software is installed. It also checks whether the target machine has a Russian keyboard and, if not, proceeds to the next stage. This involves terminating applications and processes that the victim may be using for content creation such as text editors and email clients. The malware infects every connected drive, except for CD-ROM media, and also ensures that any backup or Shadow copies of the user data are deleted:
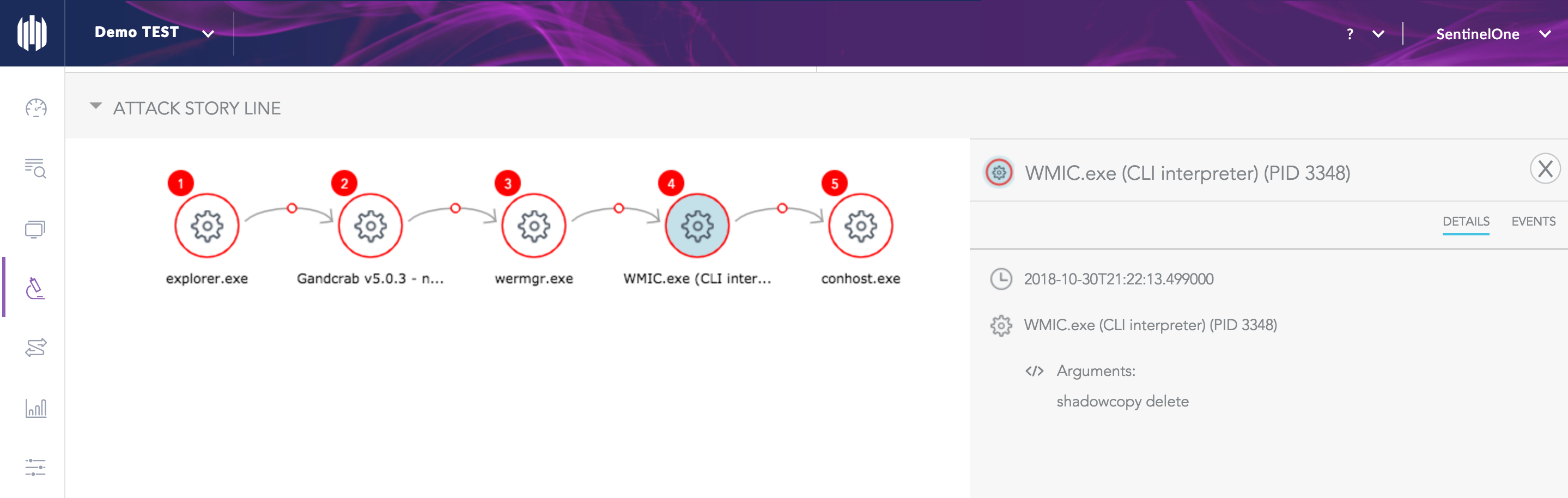
The malware may then attempt to elevate privileges before checking in with its C&C server, at which point the server receives an encrypted key containing a unique ID for the victim.
GandCrab is “smart” enough to ignore system and program files, which of course may be needed by the victim to make payment to the attackers, and focuses on user data files. It encrypts each file with a unique AES-256 key.
On successfully encrypting a target device, GandCrab delivers a ransom note instructing the victim to make payment in Bitcoin or Dash, demanding anything between $300 to $6000 USD.
There have been several attempts to defeat GandCrab. In February, a first decryption tool was made available on No More Ransom by the Romanian Police, with the support of the Europol. A second version of the GandCrab ransomware was subsequently released by the criminals with improved coding and even comments directed at law enforcement, security companies and No More Ransom. A third version followed a day later. Now in its fifth version, this file-locking malware continues to be updated at an aggressive pace. Each version appears with new, more sophisticated techniques to bypass cybersecurity vendors’ countermeasures.
As shown in the demonstration video, SentinelOne can prevent execution of GandCrab and, as a final safety measure, even decrypt the user’s encoded .crab files through rollback.


