As we usher in the New Year, it’s as good a time as any to think about password security. Is it time to refresh those stale and potentially leaked passwords you’ve been hanging on to for so long? Possibly. December 2018 saw yet another huge data breach, this time at question-and-answer site Quora, with over 100 million user passwords said to have been leaked. If you haven’t already followed our advice for beating holiday season cybercriminals, let us offer you another opportunity to push yourself in the right direction!
How Criminals Get Your Password
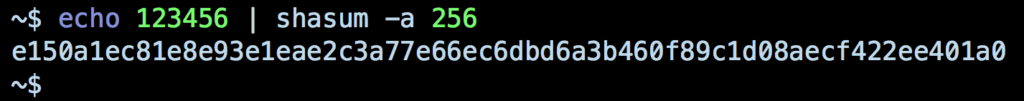
Password theft can occur in multiple ways, from phishing attacks and keylogging to shoulder surfing and mass data breaches like the Quora one mentioned above. In the case of a data breach, plain text password dumps are the dream ticket for cybercriminals, but even hashed passwords dumps like the Quora breach are of great value. A hash of a password isn’t directly reversible — there’s no way to take the hash and decode it — but hashes are determinate. That means the hash for any given string like a password will always produce the same hash. If this wasn’t so, hashes wouldn’t be much good for security purposes. Thus, the sha256 for “hello world” will always produce
a948904f2f0f479b8f8197694b30184b0d2ed1c1cd2a1ec0fb85d299a192a447
Given that determinacy, password crackers can build hash tables of common words and known passwords and then check those against the hashes revealed in data dumps.
If criminals find the hash for say, 123456 in the data dump, then they can easily search their tables for that hash and find it belongs to the most popular password used for the last 6 years in a row! That password hash, and millions of others generated from plain-text dumps and password cracking utilities, is sure to be in every cracker’s look-up tables.
Signs of a Weak Password
There’s a bunch of tell-tale signs that you’re using a password that can easily be cracked, but beware of online services that claim to test your password strength. They’re not all entirely reliable. For example, a study in 2017 found that
the password
password$1is deemed “Very Weak” by Dropbox, “Weak” by Apple, “Fair” by Google and “Very Strong” by Yahoo!
Earlier work concluded much the same thing, with Twitter and FedEx serving up very different conclusions to Dropbox and Google about password strength of the same password string:
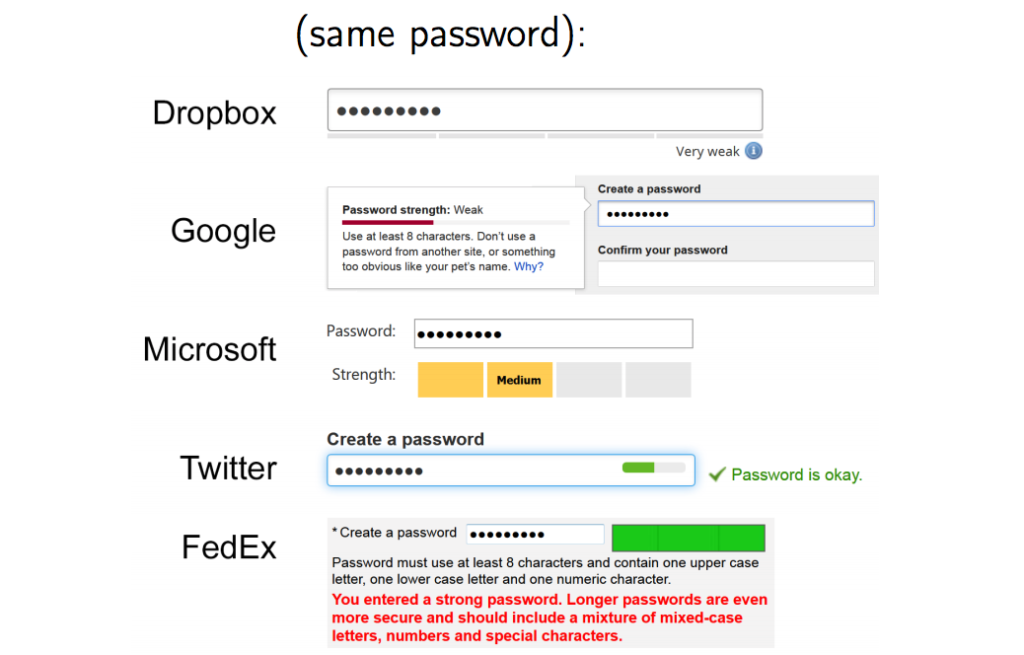
The explanation for these differences revolves around two competing demands on good password choice: security versus usability. Password strength meters typically try to make a compromise between what makes something difficult to crack with what makes something memorable enough to be usable. Studies have shown that when employers try to enforce uncrackable passwords on staff, it can have a negative impact on productivity. As a result, many employees try to circumvent restrictive workplace password policies. Also:
For e-commerce sites like eBay, portals like Yahoo! and order accepting sites like Kaspersky, usability is very crucial because every login event is a revenue opportunity. Anything that undermines user experience impairs the success of the business. So they tend to have less restrictive password policies.
While password strength meters may at least provide one indication of password vulnerability – a sign that a password is weak shouldn’t be ignored – there’s also a number of things you can check to help avoid creating a weak password. Here’s 7 signs of a weak password:
1. Your password is widely used by others
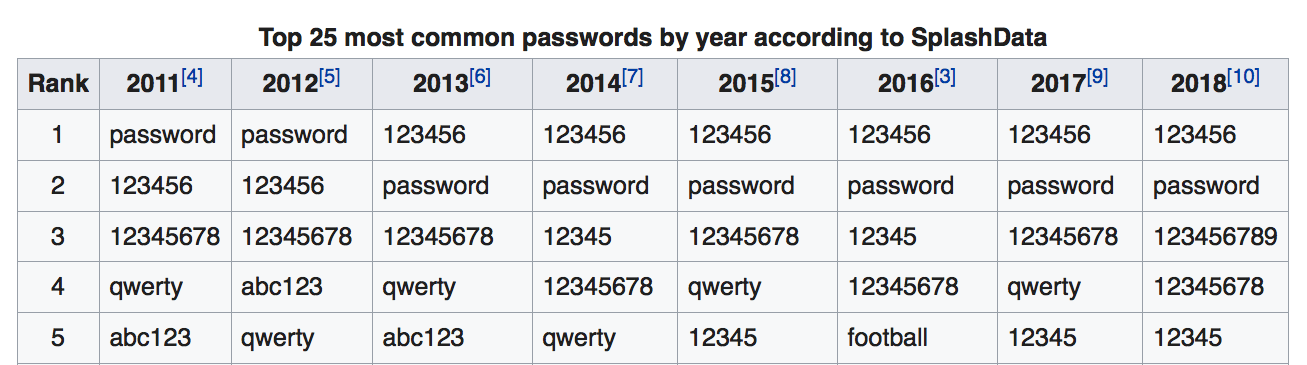
Every year SplashData compile a list of the worst (i.e., most common) passwords. Here’s their top 25 for 2018; make sure yours isn’t in it!
1 123456 (Rank unchanged from last year)
2 password (Unchanged)
3 123456789 (Up 3)
4 12345678 (Down 1)
5 12345 (Unchanged)
6 111111 (New)
7 1234567 (Up 1)
8 sunshine (New)
9 qwerty (Down 5)
10 iloveyou (Unchanged)
11 princess (New)
12 admin (Down 1)
13 welcome (Down 1)
14 666666 (New)
15 abc123 (Unchanged)
16 football (Down 7)
17 123123 (Unchanged)
18 monkey (Down 5)
19 654321 (New)
20 !@#$%^&* (New)
21 charlie (New)
22 aa123456 (New)
23 donald (New)
24 password1 (New)
25 qwerty123 (New)
2. Your password is a superhero, plus a number
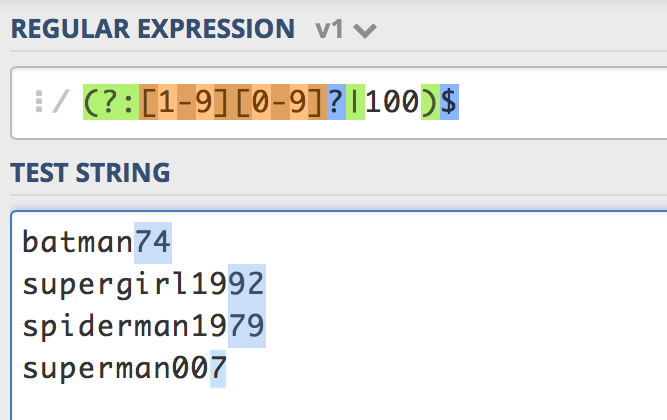
Batman, Spiderman, Supergirl and friends may be cool in some contexts, but not in passwords. Think of every superhero in popular culture, add some iconic movie characters like Neo and Trinity from the Matrix, Mr Spock and Captain Kirk from Star Trek, and you’ve still only got a couple of thousand words for hackers to add to their hash tables.
Ah, of course, but you added a number to it for extra security, right? In an analysis of over 10 million leaked passwords, nearly half a million were found to end with a number between 0 and 99.
a decent password cracker can very easily append a number, or several thousand, to its dictionary of words or brute-force approach
Regex to test for this and similar patterns are simple for hackers to construct and take only seconds to crack.
3. Your password contains your birthdate
Birthdates are one of the things many naive users will instantly think of when creating a password, as it’s the simplest thing for almost everybody to remember. Unfortunately, it’s also information that is easily discovered by bad actors. Many social media sites will require or encourage users to input their birthdate, and who doesn’t like getting lots of birthday cheers on Facebook?
Hackers, of course, know this and they know how to find this data. [See our article on OSINT (Open Source Intelligence) for more information on this]. It’s also a trend that seems common among younger users, so a guess of the present year minus anything between 13 and 30 years is another easy pattern for password crackers to test.
4. You’re too cool to care!
In 2018, “whatever”, “blahblah” and “trustno1” were the 91st, 66th and 79th most popular passwords, respectively. Being original is incredibly hard, and password attackers are ready for society’s disenchanted!
5. Your password is a word backwards
This, too, isn’t as original as many people naively suppose. Reversing a word doesn’t improve the security of a bad password in the slightest, since it’s the easiest thing for a hacker to do in one line of code in almost every scripting and programming language ever invented.
6. Your password is a keyboard pattern
What do the following random-looking passwords have in common, aside from being easily crackable?
- 1q2w3e
- 1qaz2wsx
- zxcvbnm
- !@#$%^&*
Well, two things, actually. First, they are all in the top 100 most commonly used passwords for 2018; secondly, they are all based on keyboard patterns.

7. Your password is too short
What’s a good password length that will be both secure and memorable? Anything less than 10 characters is easy to crack. A 6-character password drawn from a 74-character characterset (upper & lower case, numerals and special characters) can be cracked in 0.16 seconds:
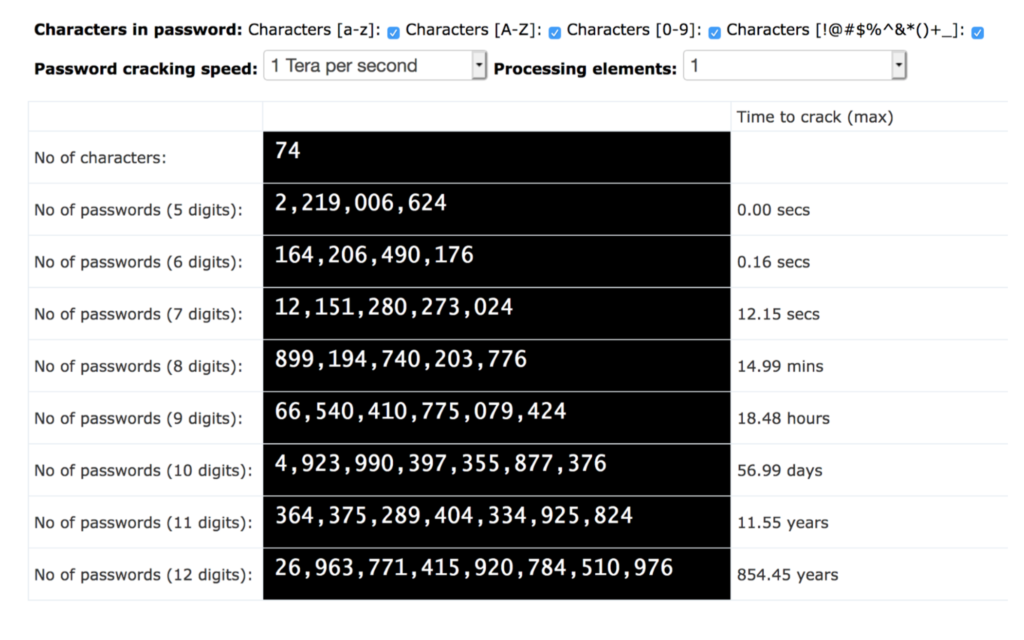
And surprisingly, shorter isn’t necessarily more memorable. There are ways to remember even the longest passwords. Compare this difficult-to-remember 12 character string:
l7aHPQ9-*=[9)(
with this lengthy passphrase, which contains all the same special characters:
NotInA(1)Month=[31-Days]Of*Sundays*
A passphrase of 35 characters is far less likely to get brute-forced in anyone-round-here’s lifetime!
Passwords The Right Way
Avoiding these common pitfalls will help reduce your chances of having your passwords cracked if they are hoovered up in some mass data breach during 2019 or later. However, user-created passwords are always going to be prone to predictability, and hackers have the best tool for parsing predictable human-created data: computers that can run automated scripts!
The only sure way to defeat cracking attempts is to have a password with maximum entropy that is unique to each site. Our advice is use a good password manager to both create and manage passwords and, wherever available, turn on 2FA or similar authenticator protocols.
On top of that, don’t forget to change your passwords on a regular basis. With passwords responsible for protecting some of your most vital assets, what could be a better resolution to start New Year 2019?

