Have you ever had malware on your Mac? The chances are you haven’t, but then again, the same could be said for the majority of the estimated 800 million Windows 10 users out there, too, if you think about it. Similarly, most people haven’t been struck with malaria, but you still wouldn’t risk going for a walk in the jungle without taking anti-malarial precautions, we hope! Enterprises know they can’t risk being “in the jungle” without endpoint protection across their entire Windows fleet, but is the same true for devices running macOS? Just how dangerous is it out there for macOS devices?
The Threat Within
Let’s start from the inside out, as it were. You implicitly trust your users, but bad apples aren’t unknown and protecting the enterprise from insider threats is an important part of your security stance. If you’re familiar with macOS, you’ll know that it has some built-in protections that appear to allow you to control what users can and can’t do. Don’t want them running unauthorised software? No problem, Apple say. Keep your users on Standard accounts to limit their options and rely on Gatekeeper.
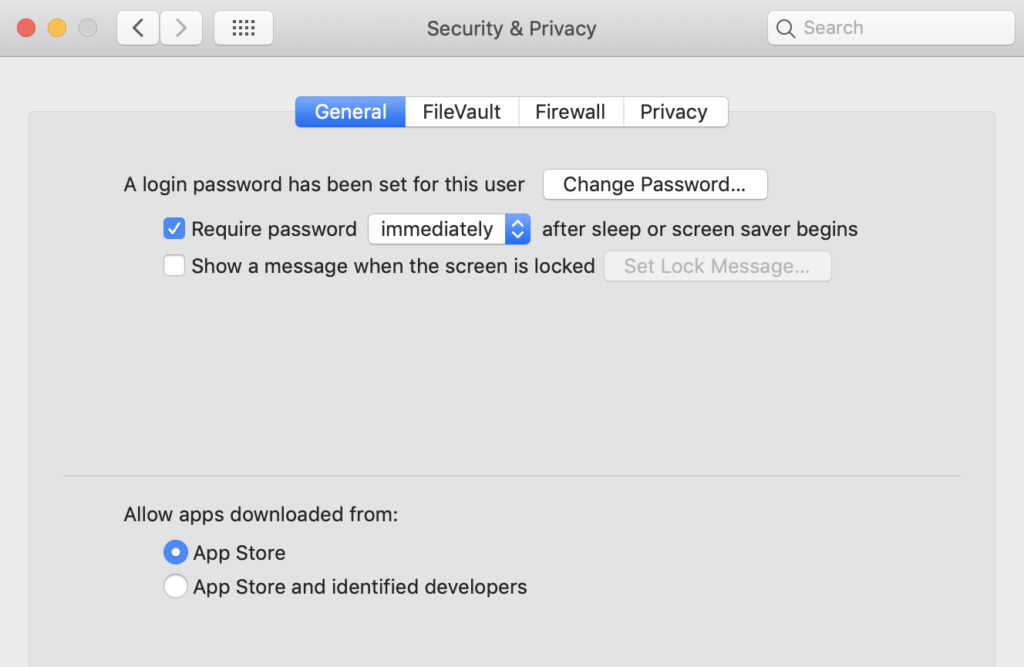
Unfortunately, that won’t protect your device, or your network. Any Standard user can override Gatekeeper settings with a one-liner from the Terminal. It’s no secret, so we’re happy to make sure you know what your users can find out with a simple internet search. A Standard user can override the system-wide policy set up by an Administrator simply by removing the quarantine bit that the browser attaches to downloads. Importantly, this does not require elevated privileges on any currently shipping version of macOS:

But even this isn’t really necessary to bypass Gatekeeper. A user could avoid the inconvenience of removing the quarantine bit simply by downloading an app directly with cURL rather than using a browser. Even with Gatekeeper set to “App Store only” this method will allow a Standard user to run an unsigned app from any source (spoiler: DIE isn’t malware! It’s a file inspection utility that also isn’t code signed!).
curl -s -L -o die.zip https://github.com/horsicq/DIE-engine/releases/download/2.02/die_mac_portable_2.02.zip
If we list the extended attributes on the downloaded file with xattr -l, we’ll see that there is no quarantine bit attached and we can run the application without triggering either Gatekeeper or, for that matter, XProtect. This is because Gatekeeper doesn’t know about apps that come in via the command line, and that includes items from package managers like brew and MacPorts, too. So if your user has access to those without admin rights, they’ll be able to run anything they can find on the internet regardless of your Gatekeeper policy.
This raises another question that the built-in tools like Gatekeeper and XProtect can’t address. Suppose that a user does circumvent your company policy in one of the ways mentioned, how would you even know, before it was too late? Like Windows, and Linux, there’s no built-in visibility tools on macOS that let you see what’s happening or that can generate alerts according to your own criteria. That’s a large reason why EDR software was invented in the first place.
The Wild, Wild Web
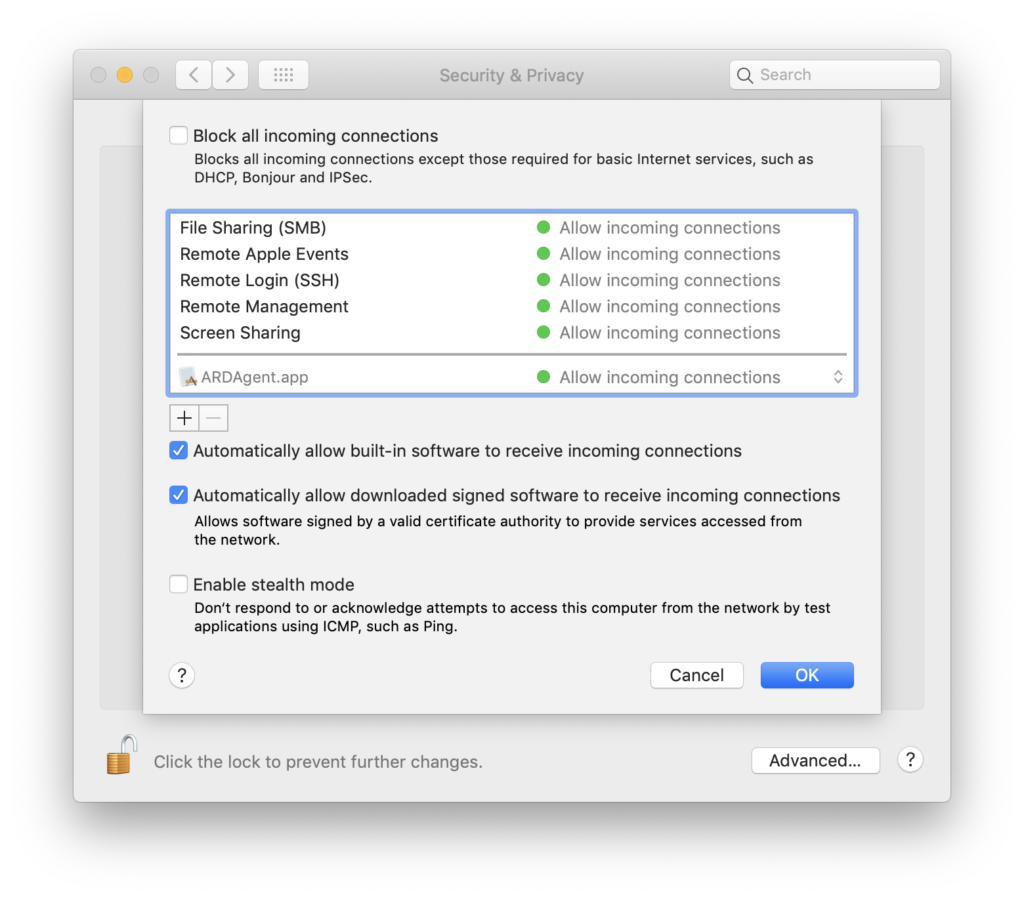
It’s not just a matter of trust. We can all click on something we didn’t intend to or get phished by a targeted attack. How well does macOS stand up to threats that are known? We’ve explained before how easy it is to bypass XProtect. You may also know that macOS has a built-in Application Firewall (OK, you might not know because it’s turned off by default), but what exactly does that do? Surprisingly, not much. Unlike a true firewall, the built-in macOS Firewall can only block incoming connections, so any malware that gets onto your system can punch straight through it and connect to the attackers Command & Control server without raising any alerts from macOS.
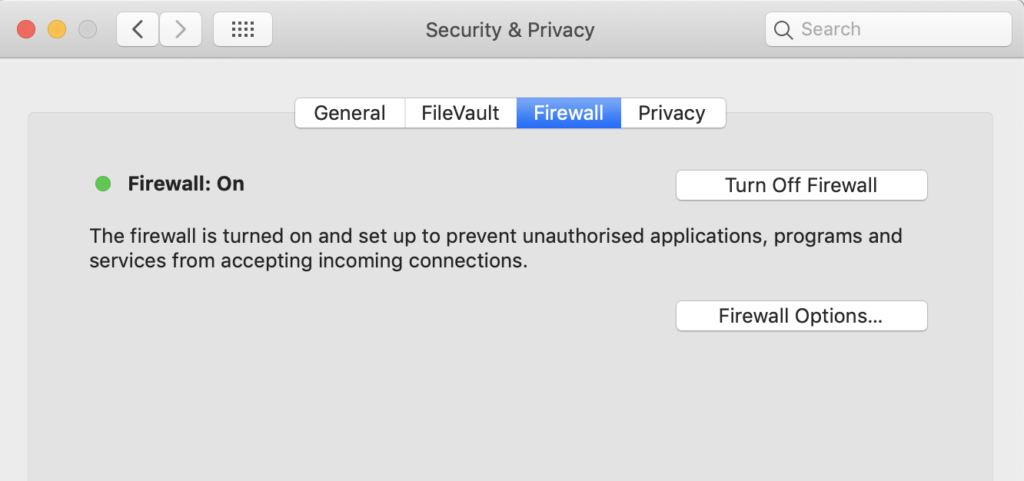
What’s more, since the Firewall’s default settings basically whitelist pretty much everything, including SSH, just flipping the switch to “On” isn’t going to block any software that’s signed from receiving connections from the internet either.
But signed software is safe, right? Well, it might be if it isn’t a trojan for something else, compromised in a supply chain attack or signed by a malicious actor. Do malware authors really have access to developer signatures? Of course! At $99 per signature, it’s a cheap buy-in for malware authors and AppleIDs are traded openly on the dark web and even the regular internet.
Data That Won’t Rest
Apple are rightly proud of the security provided by FileVault (also known as FileVault 2), which provides unbreakable encryption to protect your data when your Mac is at rest – sleeping, or better still, powered off. What Apple are less vocal about is the increased danger that the current implementation of FileVault presents when your macOS-powered endpoint is in use.
FileVault does not encrypt data per user; it only encrypts and decrypts the entire disk all at once, meaning that once some user is logged in, every users’ data is equally unencrypted.
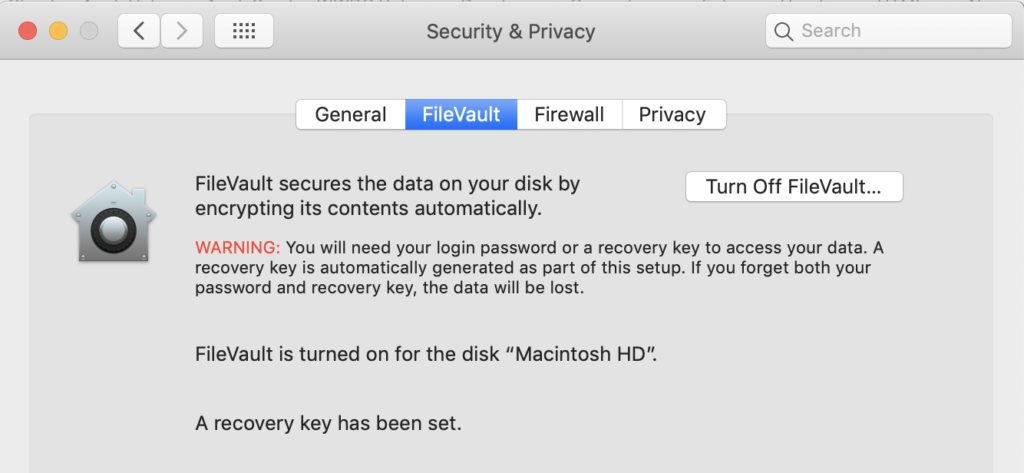
It’s a common business case to have more than one user account on a single Mac, and we all understand that users need to be protected from each other. If you’re an Admin user with other users on the same Mac, you don’t want anyone logging into those accounts to have the opportunity to steal unencrypted data from your account, but that scenario isn’t prevented by the current implementation of FileVault. This is a regression from the older, and original version of FileVault that was implemented on OSX up until 2010, which encrypted each user’s data individually.
So, Do Macs Get Malware?
Let’s get to the really juicy question, then. There was a bit of a Twitter storm this week when a user asked this question:
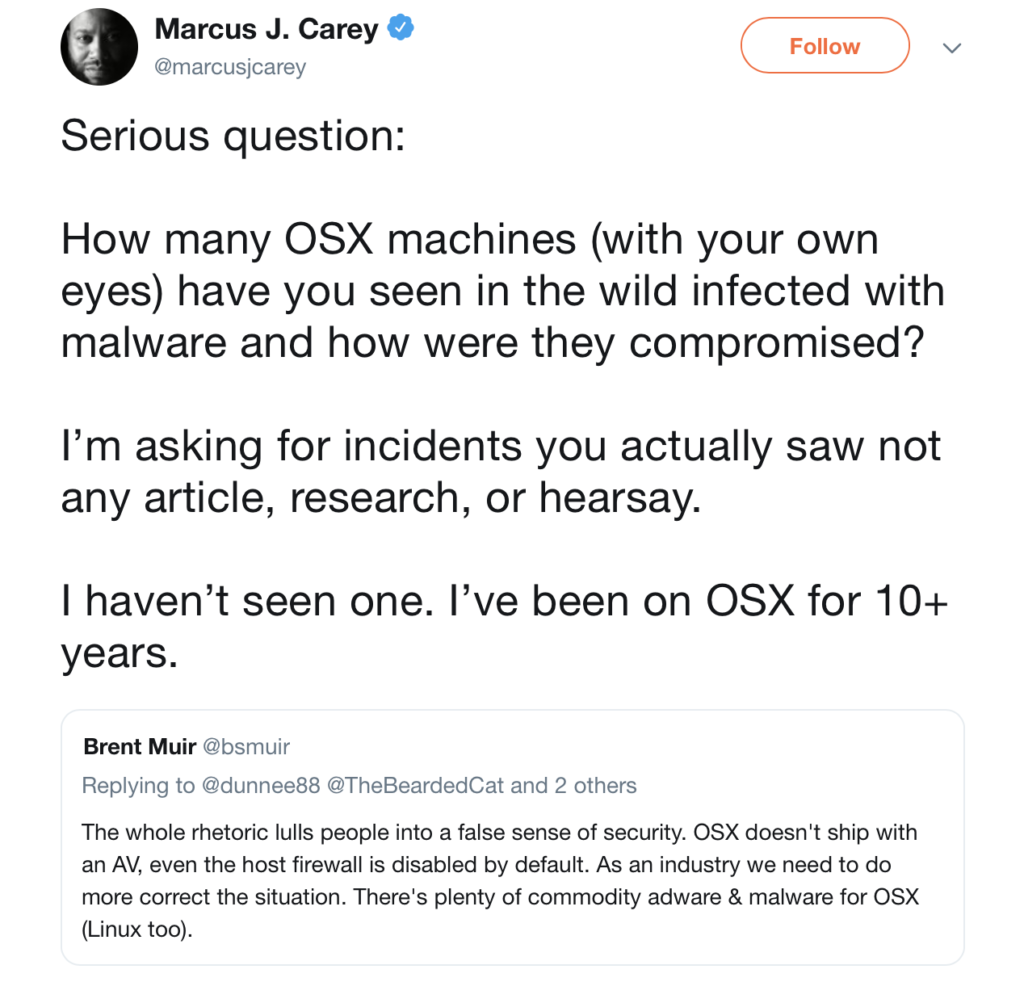
The discussion was picked up in a number of forums and Slack channels where debate continued to rage, so let’s answer that question clearly. The last time I saw an infection on macOS was the very same day that the tweet was posted, and I pretty much see infections on a daily basis on machines unprotected by Next Gen security software. Here’s what that infection looked like from userland:
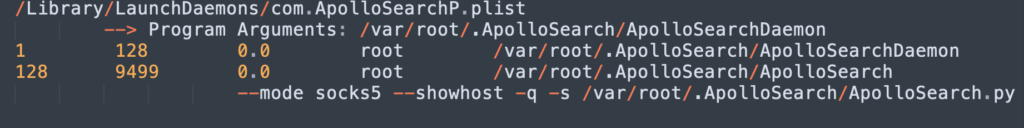
In this case, the user was operating a Mac that was not protected by a Next-Gen security solution. They downloaded a signed installer app that appeared to be an Adobe Flash Player, but was in fact a trojan installer. The installer was signed with a valid Apple Developer ID, so it waltzed by Gatekeeper, and then downloaded a malicious, encrypted zip file, enabling the malware to also stroll past legacy AV solutions that rely on scanning files for strings or hashes when they are written to disk.
As we can see, the malware installs itself deeply and invisibly at the root level. It sets up a LaunchDaemon for persistence that runs for all users. MacOS doesn’t have any built-in mechanism for monitoring persistence, though savvy users can roll-their-own with something like Folder Actions to monitor some of the common persistence locations. Unfortunately, these are neither convenient nor reliable, and offer no means to monitor what’s happening across your network.
The process spawned by the malware runs a python script that leverages a popular man-in-the-middle github project to intercept and modify web traffic.
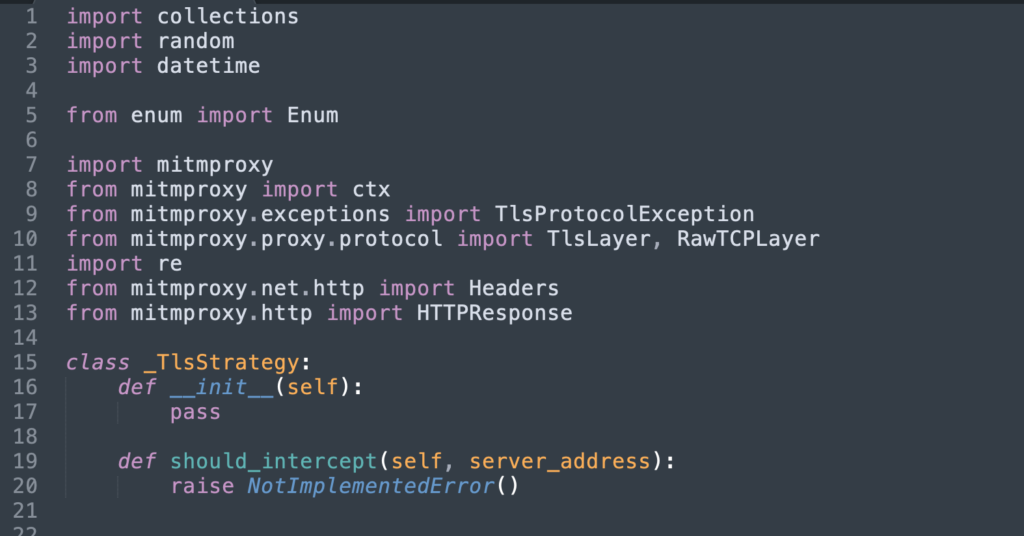
This is just one example of the many I see from users running macOS without endpoint protection. How much malware is there for macOS? We rounded up the threats from last year, noting that the biggest threats to Apple’s operating system outside of targeted APT attacks come from cryptominers and publically available exploit kits like empire that allow anyone to become a malware author without needing to be super hackers or coding gurus. Script kiddies are now more powerful than ever.
Conclusion
Whether you need to add protection to your endpoints isn’t really about the overall percentage of machines that get infected but about whether you can afford to have even one of your machines vulnerable to attack.
As we’ve seen in this post, the collection of user tools that Apple provides under “Security & Privacy” are hardly up to the task of enterprise security. Whether it’s defending against banking trojans, phishing scams or keeping an eye on every kind of device on your network, the only sensible choice is a Next Gen solution like SentinelOne.


