Traditional antivirus software is designed to block file-based malware. It works by scanning files on the hard-drive and quarantining any malicious executables it finds. This solution was fine in the early days of security software, but attacks have evolved to bypass this kind of protection in a number of ways. In this post, we look at the five most common cybersecurity threats that can bypass traditional AV solutions.

1. Polymorphic Malware – Same Same, But Different
Take a look at any public malware database like VirusTotal and you’ll see the same old threats being uploaded on a daily basis. A lot of common malware is re-generated – sometimes as often as every few hours – with a completely different file hash. Some malware changes its content based on local device parameters, resulting in a fresh hash every time they run.
What’s a hash? Let’s take a quick-dive into how this works. With a known malicious file, defenders can generate a unique checksum that will identify a copy of that file, regardless of its name or location, on any system using common utilities like sha and md5:
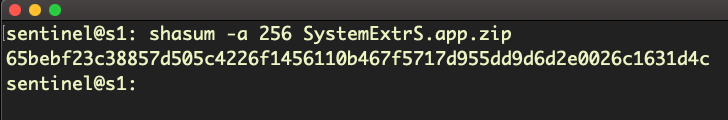
It used to be a great idea, but the rapid recycling of old samples into what legacy AV would see as a “new” threat has reached such epic proportions that it’s impossible for hash-based solutions to keep up.
This is easy for attackers to do: a single byte added to a file will change the resulting hash. The purpose of such tinkering is to defeat signature-based AV tools that rely on checking a file’s hash against a known database of malware hashes.
2. Advanced Threats – If It Ain’t Known, It Ain’t Shown!
Many AV tools have recognized the inadequacy of just checking for signatures, and have moved to using a rule-based scanning system as well, typically the YARA tool invented by Victor Alvarez. YARA offers an improvement over simple file-hashing because it allows a scanner to conduct several tests on a file’s contents. For example, a rule could be created that looks not only for certain fixed strings in the malware but also searches for regex patterns:
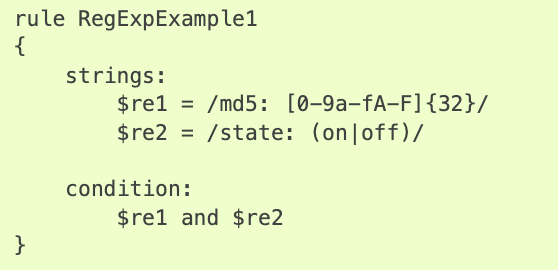
YARA rules were a great step-forward and are deployed by many AV solutions, but there’s two problems that make it easy for malware to avoid detection by such rules.
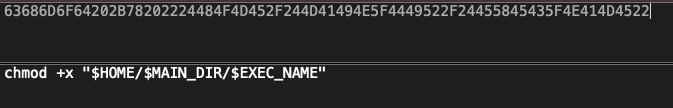
First, as with file hashes, malware authors can figure out which strings a given engine is using to detect their malware and change the strings to avoid detection. Here’s what a real YARA rule looks like:
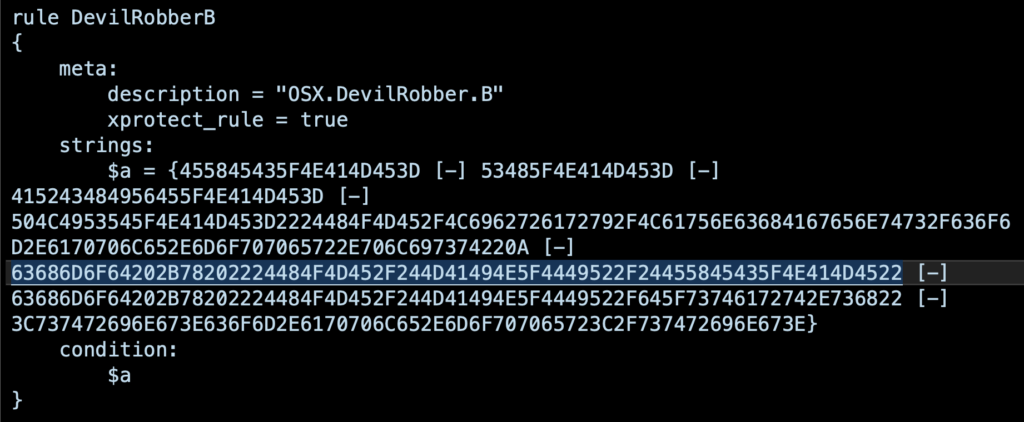
In the above example, which might look quite obscure to the untrained eye, the rules are just plain text strings written in hexadecimal. We – and attackers, of course – can easily convert them back to see what strings are actually being detected. For instance, the highlighted line in the image above is:
Second, and more problematic, is that this technique relies on the engine having already seen the malware at least once in order to analyze it and develop a rule for its detection. That means the defender is always one-step behind the attacker, and sometimes a window of a few days is enough for attackers to get in and out of their targets without detection.
3. Malicious Documents – When Is A Doc Not A Doc?
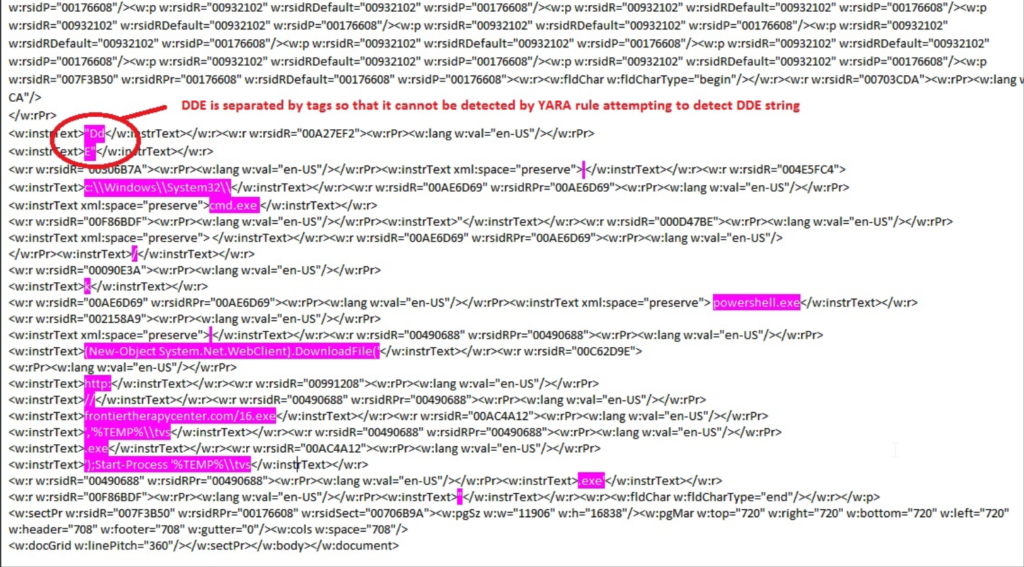
We tend to think of documents as harmless collections of formatted data, a very different species of file from executables or binaries, which are able to run code on our machines. This distinction, though, is blurred when documents contain dynamic elements like JavaScript in PDF files or code execution functionalities like macros and DDE in MS Office document types. Simply opening a file that contains these functionalities can lead to a compromise as they are executed as soon as the document is loaded.
Sometimes a maliciously-formatted document is used to exploit vulnerabilities in the opening application to achieve code execution, rather than relying on functions like macros. Such documents depend on coding errors in the application that can lead to a buffer overflow or heap spraying, a technique whereby embedded shellcode is written to multiple memory locations in the hope that one or more will allow execution of the attacker’s code. Adobe Reader and Microsoft Office are popular targets for these kind of malicious documents both because of their ubiquity, and – at least, in the former’s case – a history of repeated vulnerabilities.
For legacy AV solutions that rely on signatures, detecting these kinds of malicious documents can be difficult for two reasons. File hashes can easily be changed just by creating a document with different “normal content”, and even scanning via YARA rules can be defeated with simple code obfuscation as in this example:
4. Fileless Malware – It Doesn’t Have To Be Seen To Be Real
When most people think of malware, they typically think of some kind of malicious file that gets downloaded onto their computer and starts to cause damage or steal personal data. In the last few years, however, attackers have realised that traditional AV solutions have a gaping blindspot: malicious processes can be executed in-memory without dropping telltale files for AV scanners to find.
Fileless malware attacks have become increasingly common over the last few years, with notable examples including Angler, Duqu, Poweliks and WannaCry. The key to the rise of fileless malware has largely been the advent and widespread adoption of PowerShell, although JavaScript and PDF, Macros and DDE (as mentioned above) have also been deployed in fileless attacks.
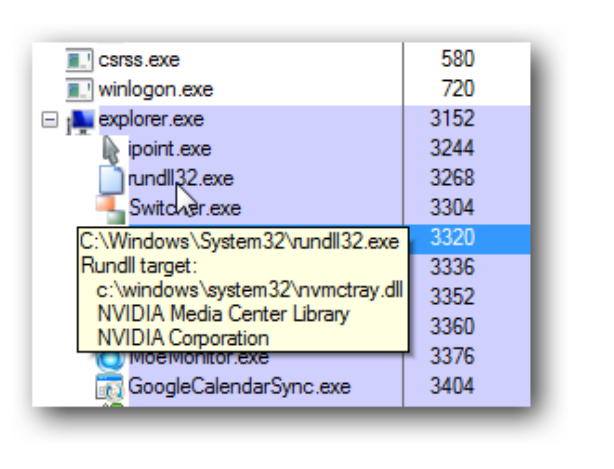
What makes fileless attacks so difficult for traditional antivirus software to spot is the fact that they typically subvert trusted processes, such as PowerShell and rundll32.exe – an essential Windows executable that loads dynamic libraries of shared code for other programs.
5. Encrypted Traffic – Hiding The Threat Pretty Securely
Another blindspot for legacy AV is encrypted traffic, which thanks to pressure from Google and others has now become the norm for most websites. While https and SSL certificates are a great way to help secure your communications with a trusted website, they just as “helpfully” protect attackers’ communications, too.
Malicious actors can hide their activities from inspection by ensuring, just like regular websites, that traffic between the victim and the attacker’s command-and-control (C2) server is protected by end-to-end encryption.
Recent figures also suggest that nearly half of all phishing sites are now using the secure https protocol to mask their activities from both users and much security software.
How SentinelOne Can Help
At SentinelOne, we understand that attackers have not and never will stand still, and they will continue to evolve their techniques. That’s why we have built a product that doesn’t rely on traditional solutions but takes the fight to the attackers by using active EDR that predicts whether a process is malicious regardless of where it comes from. Whether it’s polymorphic or novel malware, a malicious document or fileless attack, our single-agent solution leverages behavioural AI among other engines to detect attacks both pre-execution and on-execution. We also provide deep visibility into encrypted traffic for post-execution threat-hunting. We were the first security product to introduce a ransomware guarantee, as early as 3 years ago, as proof of confidence in our AI technology.
Conclusion
Malware and malware authors haven’t abandoned their old techniques, but they’ve added significant new ones to counter the moves made by traditional AV software some years ago. Once upon a time, signature detections and YARA rules might have provided “good enough” defense, but these days any solution that’s not deploying a behavioural AI engine with machine learning is going to be outwitted by today’s attackers. With phishing, ransomware and cryptomining all on the increase, the modern enterprise needs a modern solution. If you haven’t tried out the SentinelOne offering yet, click the Free Demo button above and see the difference our easy-to-deploy solution can make to the security of your business.