Mimikatz is a powerful tool used for extracting credentials from Windows systems. This guide explores how Mimikatz operates, its capabilities, and the risks it poses to organizations.
Learn about strategies for detecting and preventing Mimikatz attacks. Understanding Mimikatz is essential for organizations to safeguard their systems against credential theft. In this post, we look at what mimikatz is, how it is used, why it still works, and how to successfully protect endpoints against it.

What is Mimikatz?
Mimikatz is a tool that is commonly used by hackers and security professionals to extract sensitive information, such as passwords and credentials, from a system’s memory. It is typically used to gain unauthorized access to networks, systems, or applications or to perform other malicious activities, such as privilege escalation or lateral movement within a network.
Mimikatz can be used in various ways, depending on the attacker’s goals and objectives. For example, it can be used to:
- Extract passwords and credentials from the system’s memory, allowing the attacker to access networks, systems, or applications.
- Bypass authentication mechanisms, such as multi-factor authentication, by stealing and using stolen credentials.
- Escalate privileges on a system, allowing the attacker to gain access to sensitive data or perform other malicious actions.
- Move laterally within a network, allowing the attacker to access additional systems or networks.
Overall, Mimikatz is a powerful tool that attackers can use to gain unauthorized access to networks, systems, and applications and perform other malicious activities.
The mimikatz tool was first developed in 2007 by Benjamin Delpy. So why are we writing about mimikatz today? Quite simply because it still works. Not only that, but mimikatz has, over the years, become commoditized, expanded and improved upon in several ways.
The official builds are still maintained and hosted on GitHub, with the current version being 2.2.0 20190813 at the time of writing. Aside from those, it is also included in several other popular post-exploitation frameworks and tools such as Metasploit, Cobalt Strike, Empire, PowerSploit, and similar.
These tools greatly simplify the process of obtaining Windows credential sets (and subsequent lateral movement) via RAM, hash dumps, Kerberos exploitation, as well as pass-the-ticket and pass-the-hash techniques.
Mimikatz consists of multiple modules tailored to either core functionality or varied vector of attack. Some of the more prevalent or utilized modules include:
- Crypto
- Manipulation of CryptoAPI functions. Provides token impersonation, patching of legacy CryptoAPI
- Kerberos
- “Golden Ticket” creation via Microsoft Kerberos API
- Lsadump
- Handles manipulation of the SAM (Security Account Managers) database. This can be used against a live system, or “offline” against backup hive copies. The modules allow for access to password via LM Hash or NTLM.
- Process
- lists running processes (can be handy for pivots)
- Sekurlsa
- Handles extraction of data from LSASS (Local Security Authority Subsystem Service). This includes tickets, pin codes, keys, and passwords.
- Standard
- main module of the tool. Handles basic commands and operation
- Token
- context discovery and limited manipulation
Does MimiKatz Still Work on Windows 10?
Yes, it does. Attempts by Microsoft to inhibit the usefulness of the tool have been temporary and unsuccessful. The tool has been continually developed and updated to allow its features to plow through any OS-based band-aid.
Initially, mimikatz was focused on the exploitation of WDigest. Prior to 2013, Windows loaded encrypted passwords into memory, as well as the decryption key for said passwords. Mimikatz simplified the process of extracting these pairs from memory, revealing the credential sets.
Over time Microsoft has made adjustments to the OS, and corrected some of the flaws that allow mimikatz to do what it does, but the tool stays on top of these changes and adjusts accordingly. More recently, mimikatz has fixed modules that were crippled post-Windows 10 1809, such as sekurlsa::logonpasswords.
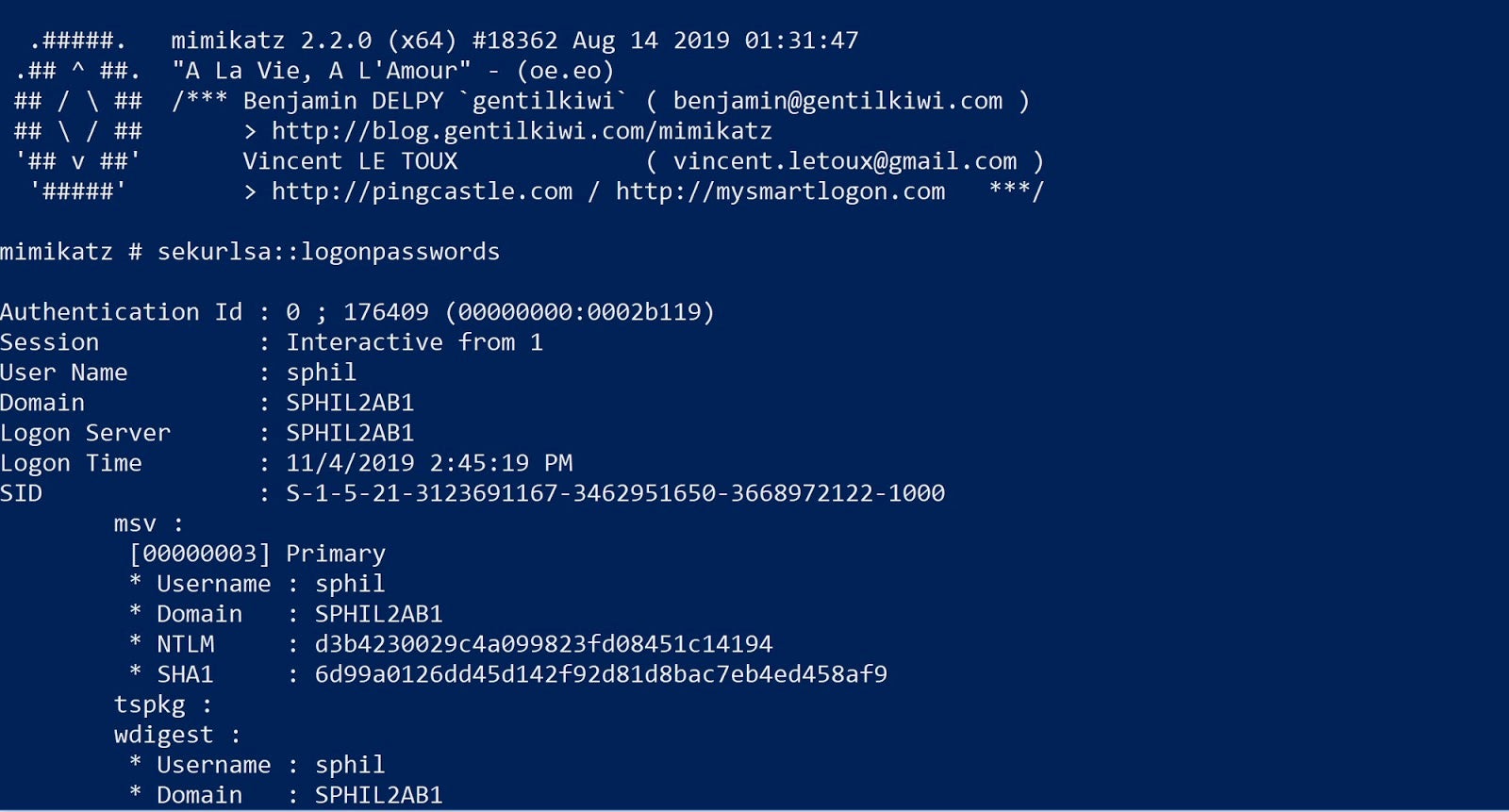
Mimikatz supports both 64-bit x64 and 32-bit x86 architectures with separate builds. One of the reasons mimikatz is so dangerous is its ability to load the mimikatz DLL reflexively into memory. When combined with PowerShell (e.g., Invoke-Mimikatz) or similar methods, the attack can be carried out without anything being written to disk.
Learn how our Singularity™ Platform detects and prevents attacks like Mimikatz.
How Widely Used Is Mimikatz Today?
Many prominent threats bundle mimikatz directly or leverage their implementations to pull credentials or simply spread via the discovered credential sets. NotPetya and BadRabbit are two huge examples, but more recently, Trickbot contains its own implementation for basic credential theft and lateral movement.
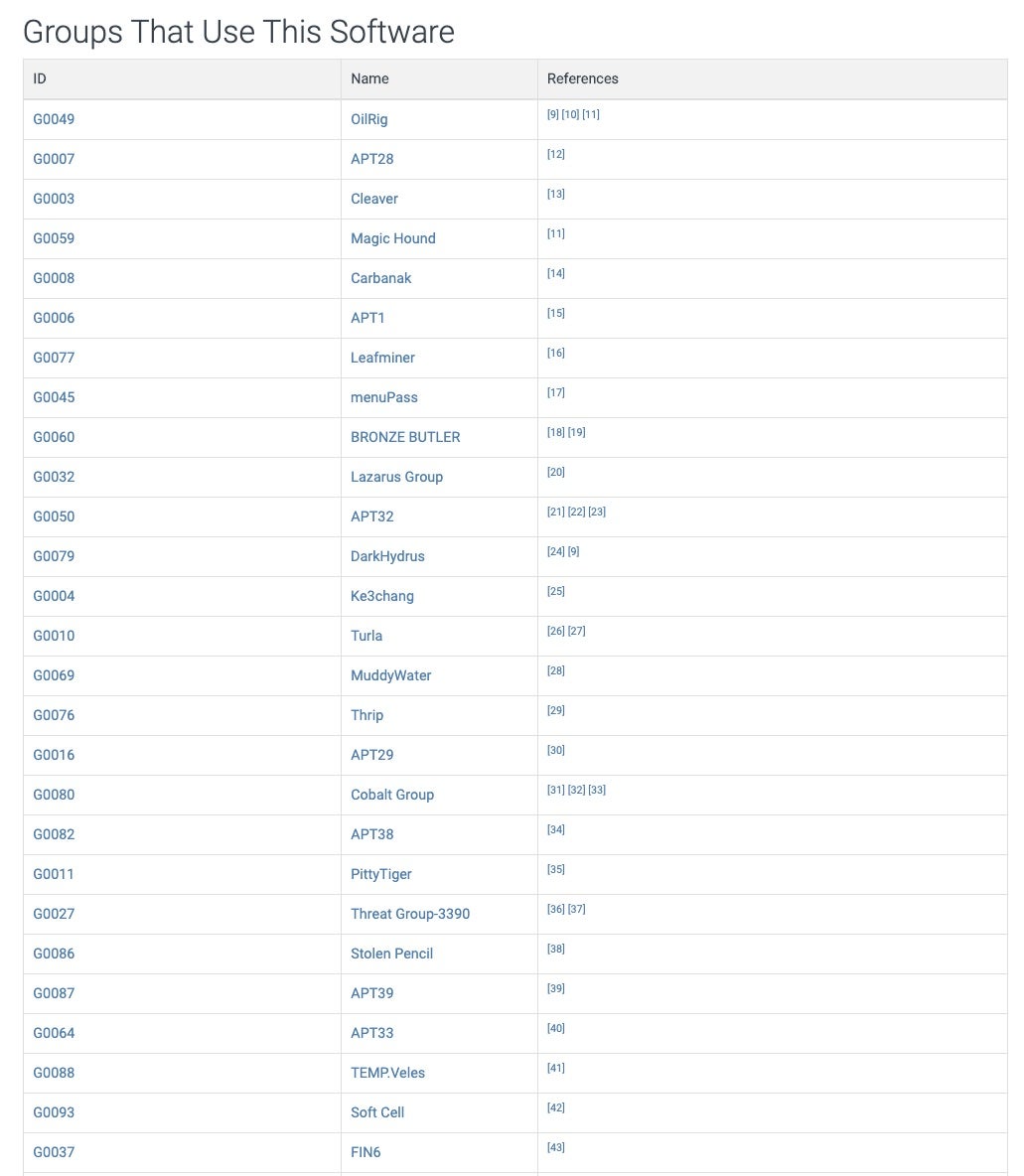
To get another idea of how prevalent the use of mimikatz is in real-world attacks one need only look as far as MITRE. While this list is not complete, it gives a good idea of how many sophisticated attackers (aka APT groups) are using this tool. This list is a true “Who’s Who” of scary threat actors involved in advanced targeted attacks: Oilrig, APT28, Lazarus, Cobalt Group, Turla, Carbanak, FIN6 & APT21 just to name a few.
All these groups develop their own way to invoke/inject mimikatz so as to ensure the success of the attack and evade the endpoint security controls that may stand in the way.
Cobalt Group, specifically, is a great focus point as they get their name from the use of the Cobalt Strike tool. Cobalt Strike is a collaborative Red Team and Adversary Simulation tool. As mentioned above, mimikatz is included as core functionality. Even more concerning is the ability to invoke mimikatz directly in memory from any context-appropriate process in which the Cobalt Strike beacon payload is injected. Again, this kind of ‘fileless‘ attack avoids any disk reads/writes, but it can also bypass many modern “next-gen” products that are not able to properly monitor very specific OS events/activities.
Can Mimikatz Defeat Endpoint Security Software?
If the OS cannot keep up, can 3rd party security solutions defend against mimikatz attacks? That depends. The mimikatz tool creates a challenge for traditional endpoint security controls, aka legacy AV and some “next-gen” tools. As noted above, if they are not monitoring behavior in memory, or if they are not monitoring specific behaviors and events, they will simply not see or be able to prevent the attack.
It should also be noted that mimikatz requires Administrator or SYSTEM level privileges on target hosts. This requires that attackers inject into a process with appropriate privileged context, or they find a way to elevate privileges that simply bypass some AV software solutions, particularly if those solutions are prone to whitelisting “trusted” OS processes.
Discover how SentinelOne’s Endpoint Security protection blocks credential-stealing tools like Mimikatz in real-time.
How To Successfully Defend Against Mimikatz
As this in-the-wild case study shows, SentinelOne’s static and behavioral AI approach provides robust prevention and protection against the use of mimikatz. Even when injected directly into memory, regardless of origin, SentinelOne is able to observe, intercept, and prevent the behavior. Even more important, however, is that as a result, we also prevent the damage that mimikatz can cause. The loss of critical credentials, data, and ultimately time and money is avoided as mimikatz cannot evade the SentinelOne on-device agent.
SentinelOne stop mimikatz from scraping credentials from protected devices. In addition to other built-in protection, we have added a mechanism that does not allow the reading of passwords, regardless of the policy settings.
 Get Deeper Threat Intelligence
Get Deeper Threat Intelligence
See how the SentinelOne threat-hunting service WatchTower can surface greater insights and help you outpace attacks.
Learn MoreConclusion
The bottom line here is that mimikatz is a near-ubiquitous piece of the modern adversary’s toolset. It is used across all sophistication levels and against the full spectrum of target types and categories. Despite being developed over 12 years ago, the toolset continues to work and improve, and likewise, mimikatz continues to challenge aging and legacy endpoint protection technologies.
SentinelOne offers a best-in-class solution to handle all angles of mimikatz-centric attacks with behavioral AI and Active EDR. There is no substitute for autonomous endpoint detection and response in today’s threat landscape.
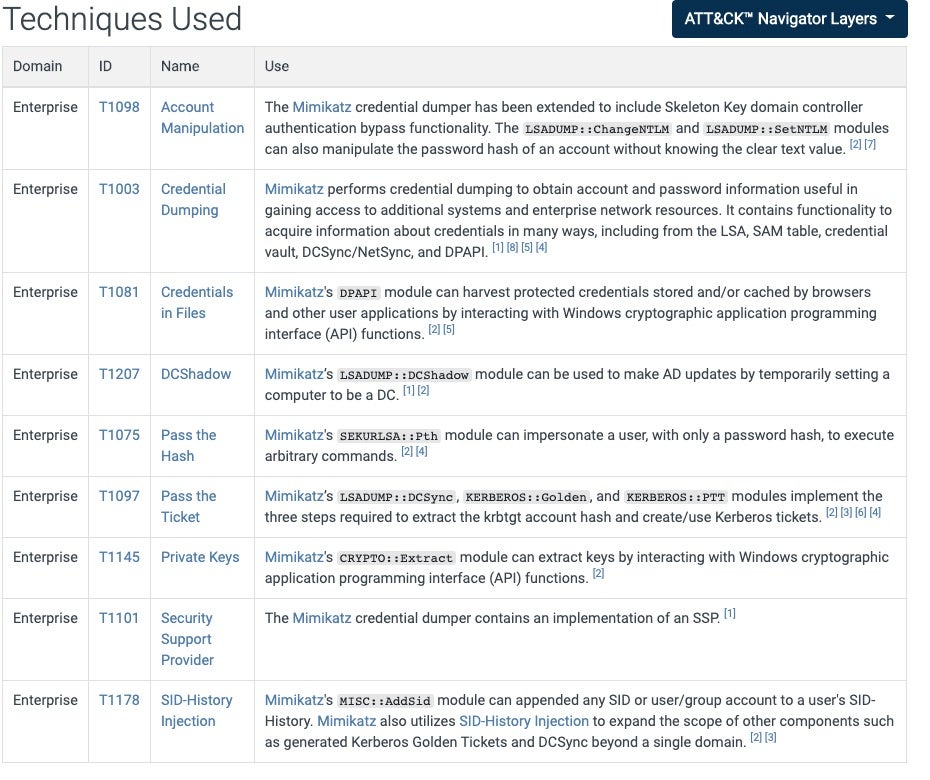
MITRE ATT&CK IOCs
Mimikatz {S0002}
Account Manipulation {T1098}
Credential Dumping {T1003}
Pass The Hash {T1075}
Pass The Ticket {T1097}
Private Keys {T1145}
Security Support Provider {T1101}
Cobalt Strike {S0154}
Mimikatz FAQs
Mimikatz is one of the most widely used and downloaded threat actor tools that was originally created by Benjamin Delpy as a proof of concept. It’s one of the world’s best password stealers and hackers use the tool to infiltrate networks.
You need to run Mimikatz as an administrator in order to use it correctly. There are 2 versions available – 32bit and 64bit. The sekurlsa module in Mimikatz lets users dump passwords from memory. The cryptomodule gives access to the CryptoAPI in Windows and lists and exports certificates and private keys. The Kerberos API can be accessed with Mimikatz’s Kerberos module and it can be used to extract and manipulate Kerberos tickets.
You can detect Mimikatz through PowerShell script block logging by monitoring for specific commands like “mimikatz”, “sekurlsa::pth”, or “kerberos::ptt”. Look for LSASS memory dumps using dbgcore.dll or dbghelp.dll. Monitor for unusual process access to lsass.exe and check for suspicious PowerShell activity. If you have SentinelOne deployed, it can automatically detect and block Mimikatz processes. You should also watch for credential dumping attempts and unusual authentication patterns.
It’s not a virus. However, Mimikatz is an open-source malware program that steals passwords and user credentials. You can also call it a hacktool.
If you’re using Mimikatz for penetration testing and security research, then yes it’s legal. But if you use it to steal passwords without permission is illegal, then that’s criminal by nature. Many organizations have explicit policies regarding its use and require proper authorization before deployment.
Change your admin privileges and caching policies. Turn off debugging privileges and increase local security authority. Configure additional LSA configuration items to reduce your organization’s attack surface. To enable security logging and monitoring, you can use SentinelOne. This will help you catch password stealing attempts and prevent credentials harvesting and theft.