A report last week from human rights advocates Amnesty International brought to light a macOS variant of a cross-platform spyware suite known as FinSpy, developed and marketed by German-based outfit FinFisher. The FinSpy tool was written with multiple capabilities in mind, with everything from keylogger, audio recording, camera and screenshot tools to a remote access shell, file enumeration and exfiltration functions. In this post, we look at how to detect the macOS variant and list some previously unpublished IoCs.

What is FinFisher Spyware?
According to FinFisher’s own website and marketing material, the company produces tools for “tactical intelligence gathering”, “strategic intelligence gathering”, and “deployment methods and exploitation”. The company states that it only partners with “Law Enforcement and Intelligence Agencies” and has a “worldwide presence”.
Amnesty International and other civil rights organizations (e.g., the Citizen Lab), however, have noted FinSpy being used in campaigns targeting “activists, journalists and dissidents” in Egypt, Ethiopia, and the United Arab Emirates (UAE) among others. What ties these various campaigns together, aside from the use of FinFisher products, is that the targets are very frequently “human rights defenders”.
Although elements of the toolkit targeting macOS users have been known for some while to malware researchers, and some components of the macOS suite do not appear to be functional on the latest iterations of Apple’s desktop platform, our tests confirmed the malware samples shared by Amnesty will still launch and infect a macOS Catalina install, and that some of the dropped malware is not well-known to reputation services like VirusTotal.
How Does FinSpy for macOS Work?
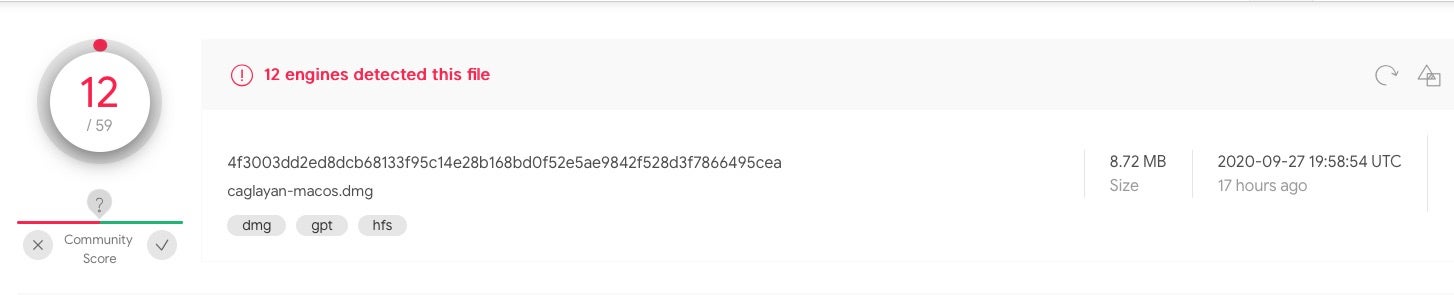
In their report, Amnesty provided the following hash for this sample on VirusTotal which we used for our analysis:
4f3003dd2ed8dcb68133f95c14e28b168bd0f52e5ae9842f528d3f7866495cea
Although some engines on VT have caught up with this sample, the majority still do not recognize it as malware at the time of writing, with only 12/59 detections.
As the sample is not Notarized, the user will need to be socially engineered to override the Notarization check on macOS Catalina, something that commodity malware authors at least have become very successful at achieving.
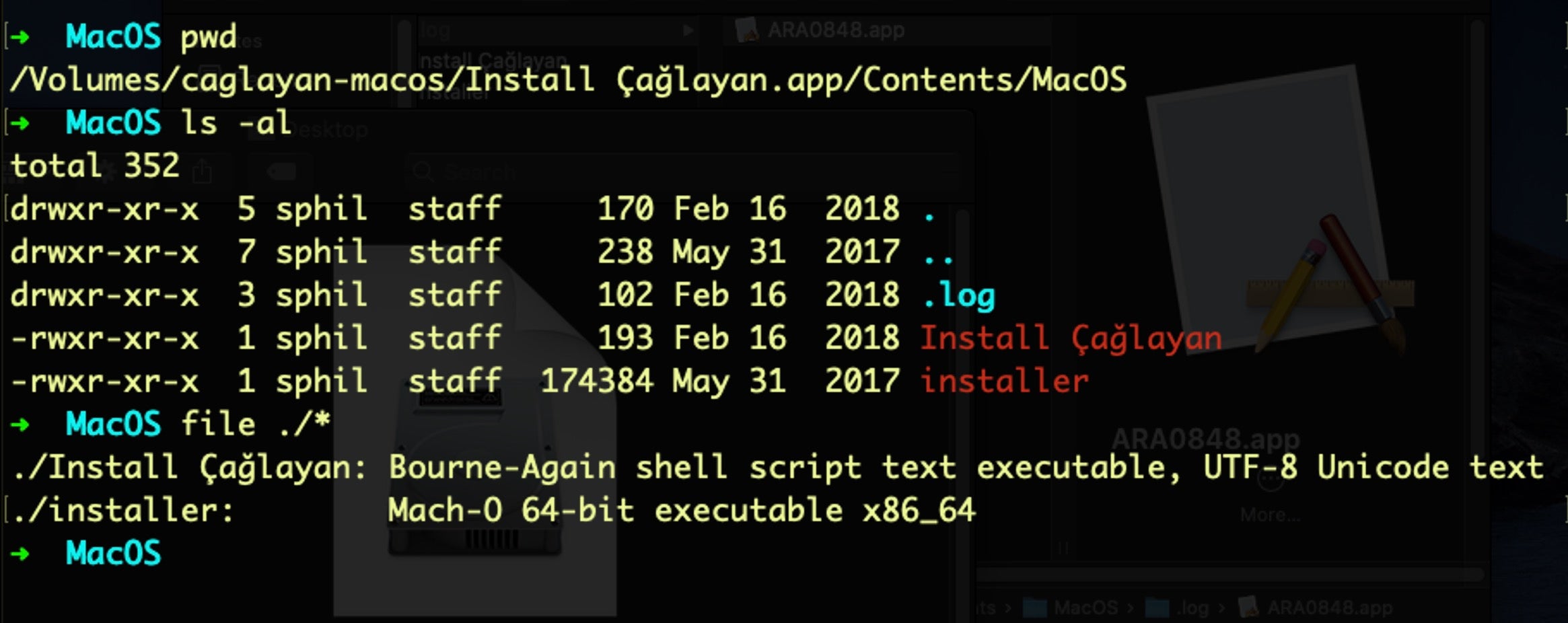
The trojan installer’s MacOS folder contains two executable files and a directory.
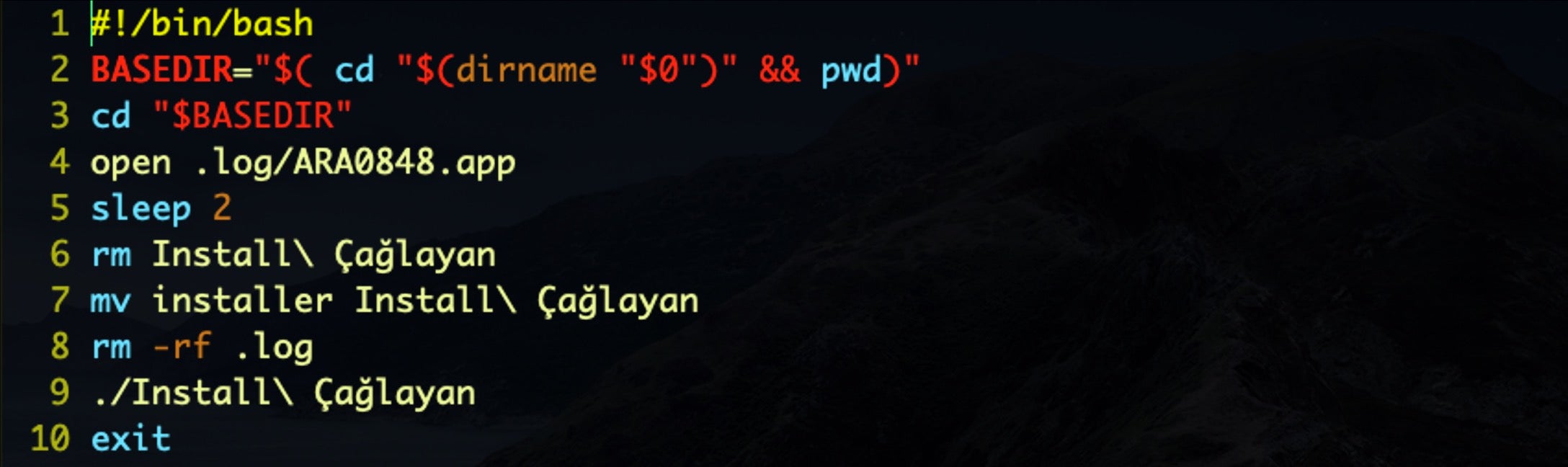
The Bash script, Install Çağlayan, contains the logic for executing the malicious application bundle in the hidden .log folder:
The ARA0848.app’s Mach-O executable contains logic to detect execution in a Virtual Machine environment as a means to thwart macOS malware researchers using any one of Parallels, VMWare or VirtualBox virtualization software:
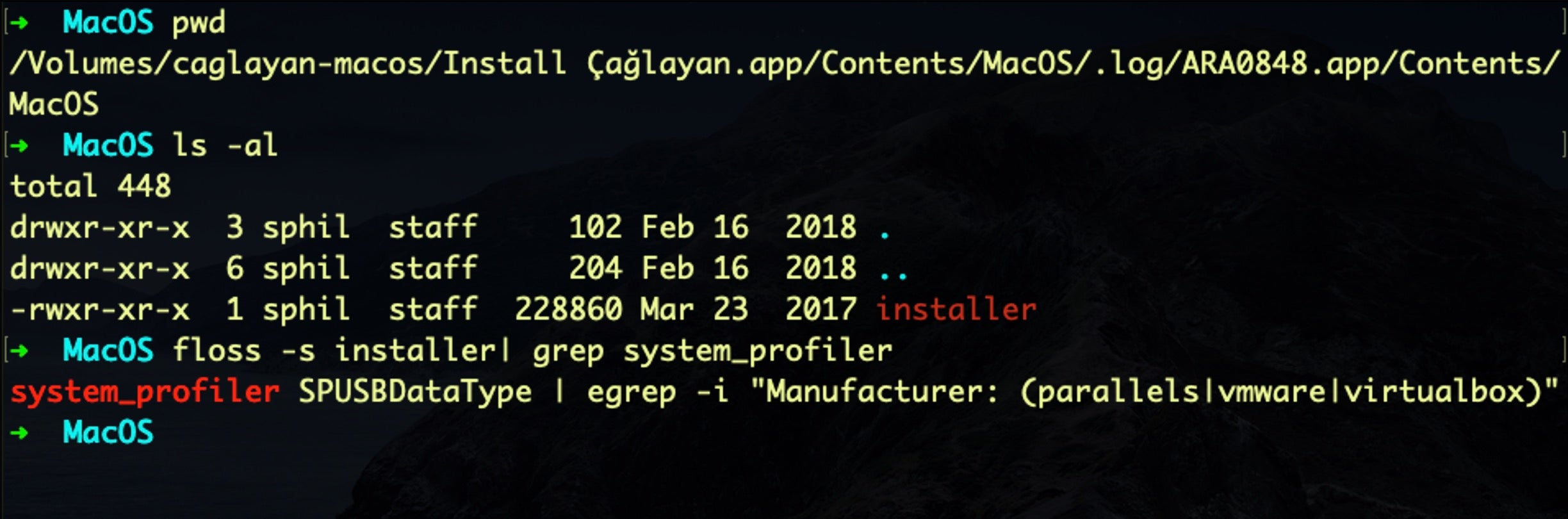
Since it is always wise to reverse macOS malware in an isolated test environment, we had to alter the sample slightly in order to beat its built-in anti-analysis detection routine. In our case, we are using an isolated Parallels Virtual Machine for this lab, so some light binary patching should take care of the VM detection.
First, we copy the binary off the DMG to local disk, and then open the binary in the vi editor:
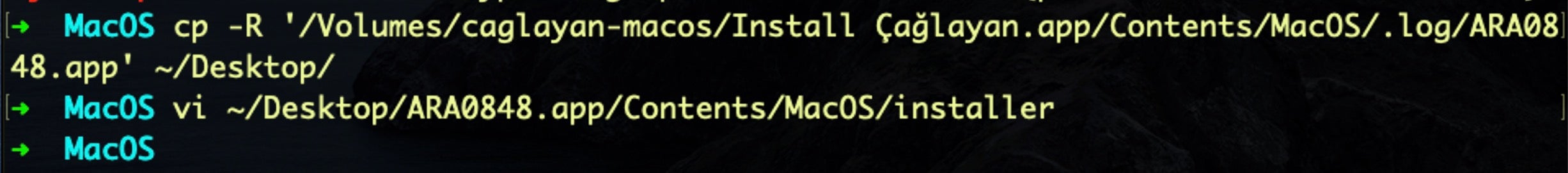
Then we call the xxd utility from vi’s command line:
%!xxd
Next, we search for instances of “parallels”. Fortunately, there are only two:
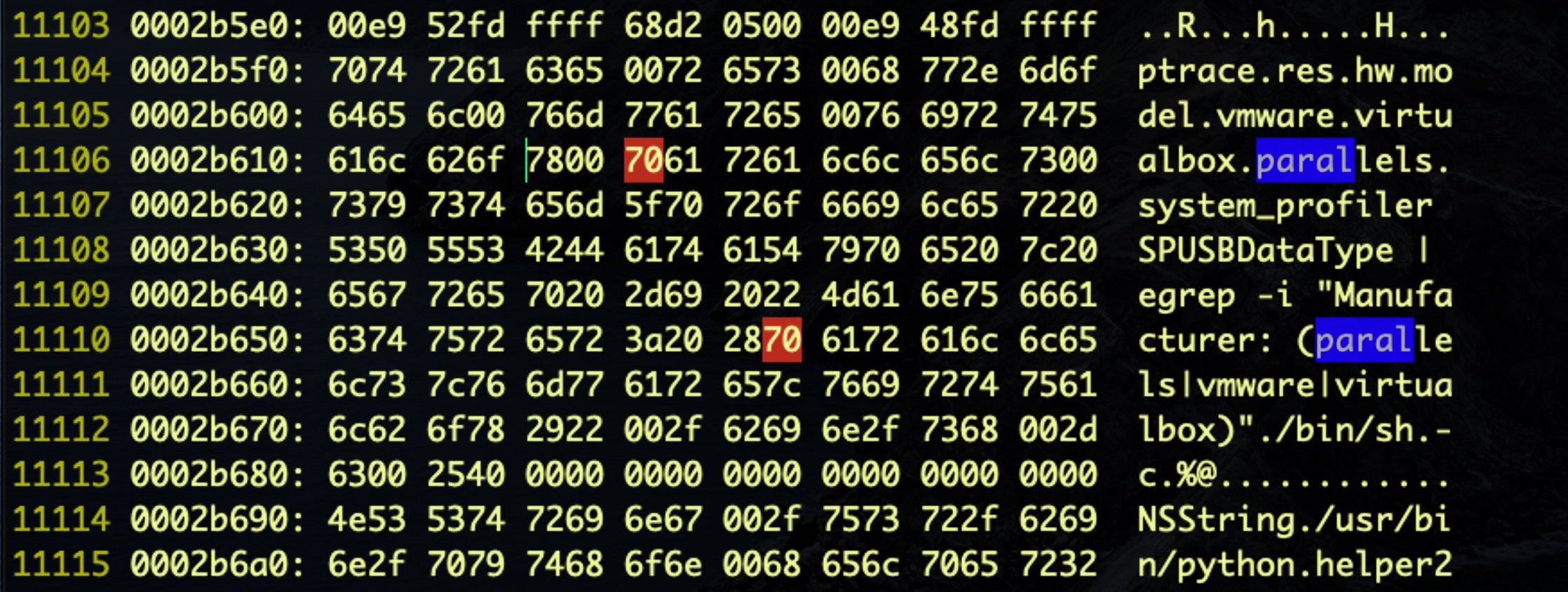
We now edit the first character of each and change it from ‘parallels’ to ‘xarallels’ by substituting the hex 70 (‘p’) for 78 (‘x’). We then use %!xxd -r to reverse the hex back to binary format and save out of vi with the command wq.
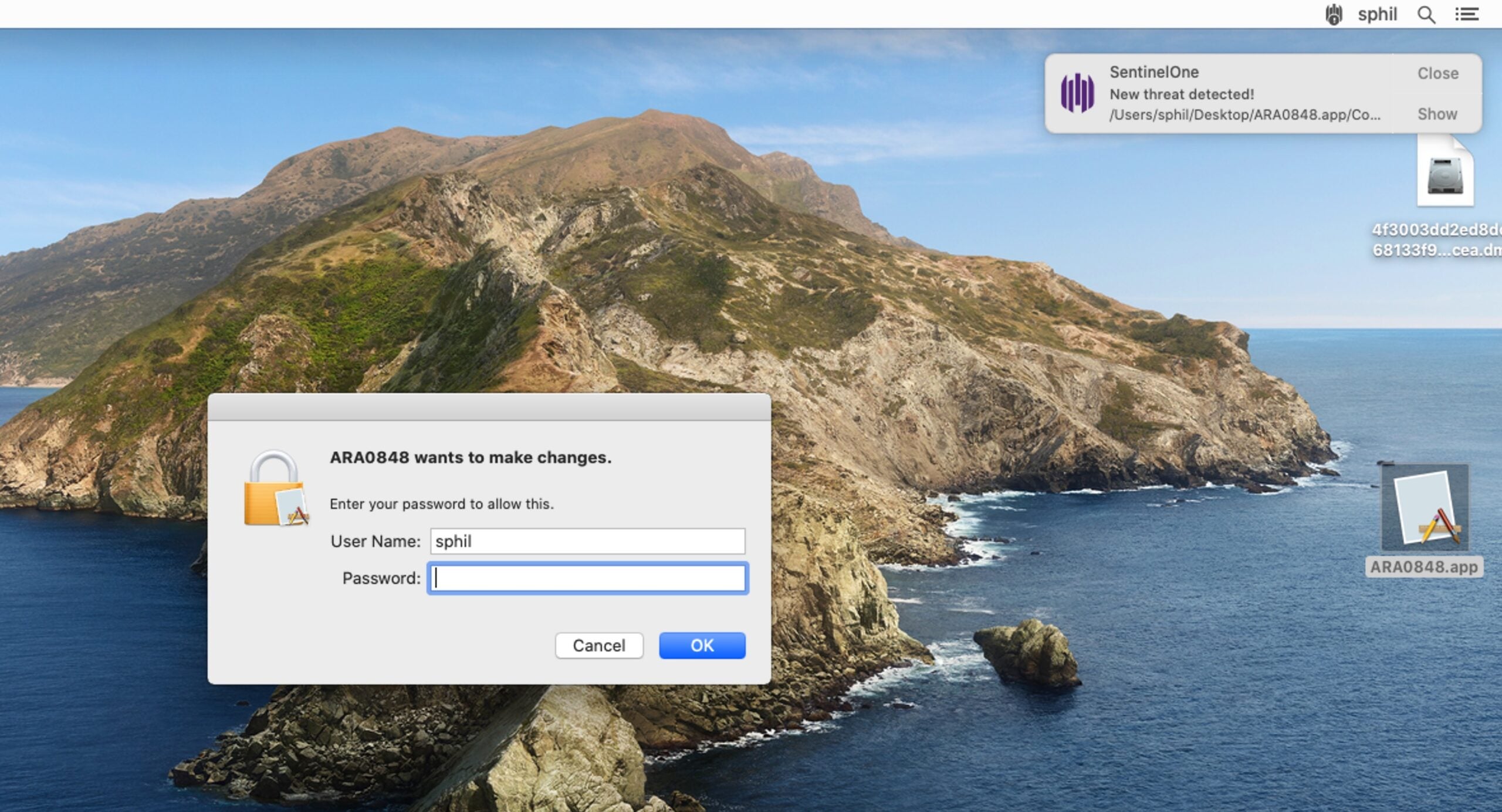
Launching the sample on macOS Catalina requires overriding the Notarization check (more on this below), after which we immediately observe a request from the malware to elevate privileges. After obliging, the malware immediately writes the following files to the user’s Library Caches folder:
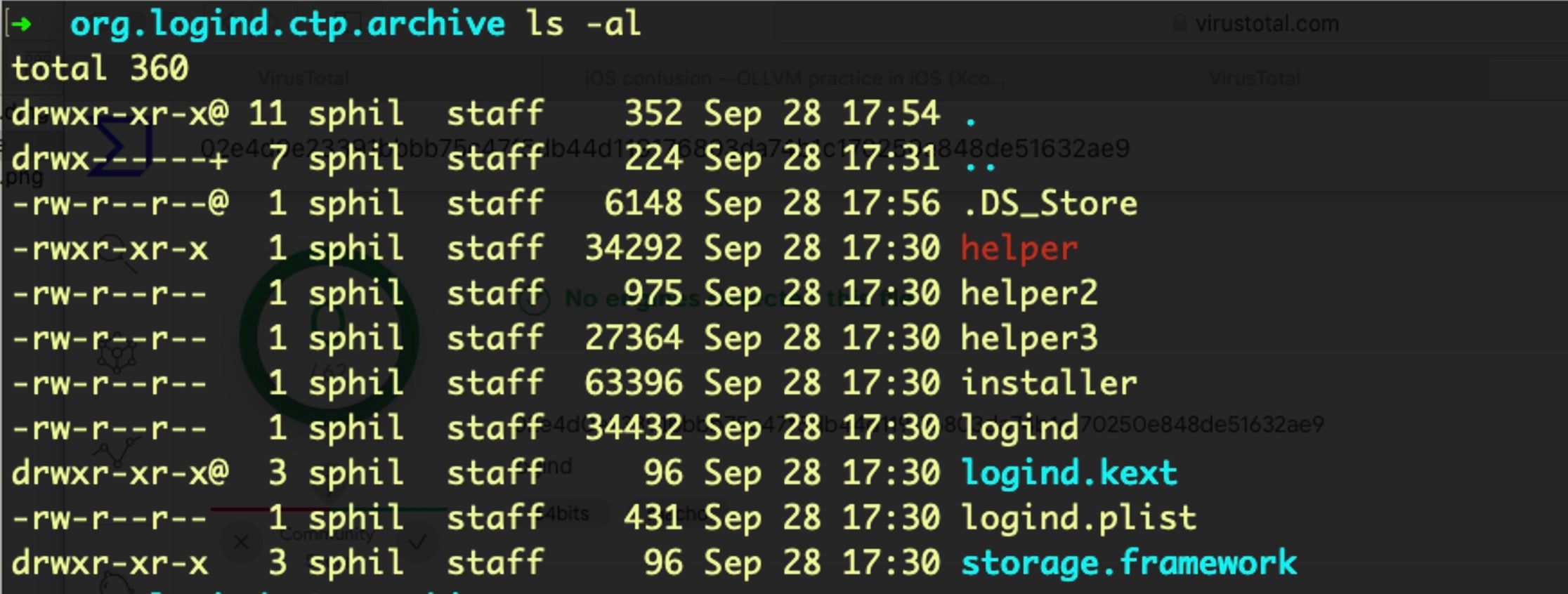
Aside from that, the FinFisher spyware seeks to maintain persistence by writing a domain level LaunchAgent called logind.plist to /Library/LaunchAgents folder.
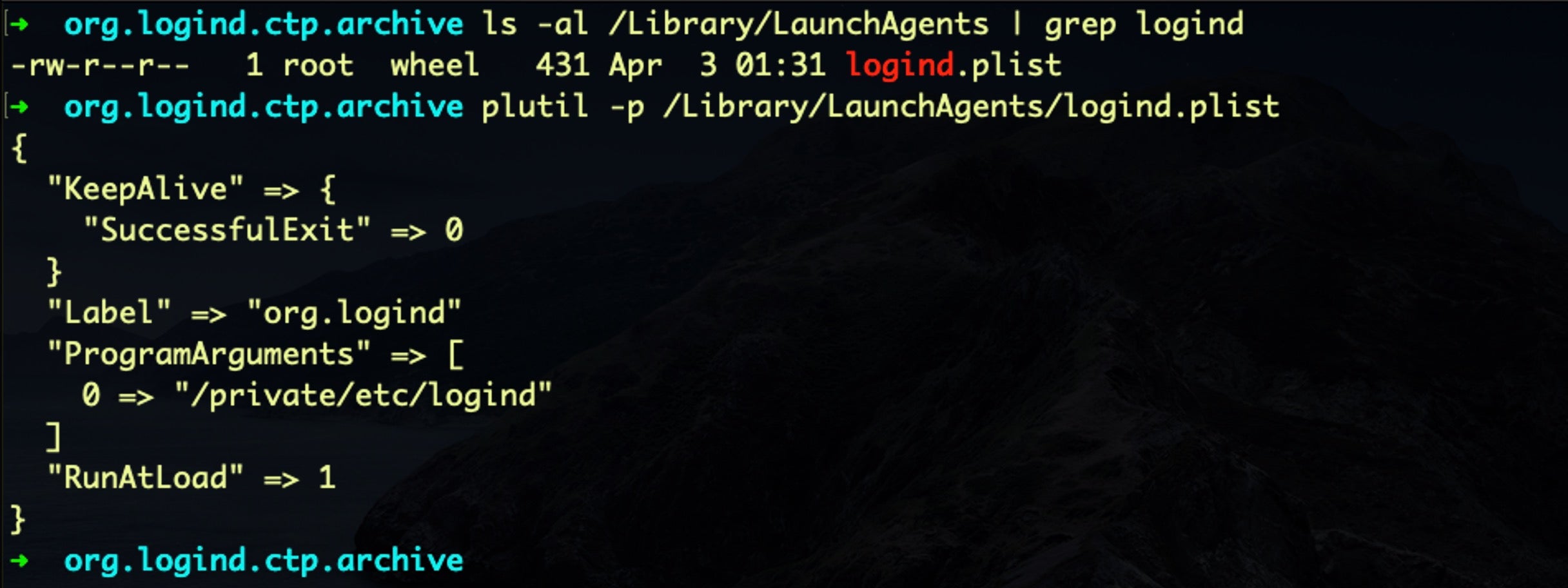
The program argument targets /private/etc/logind, where we find the following setuid, setgid file:
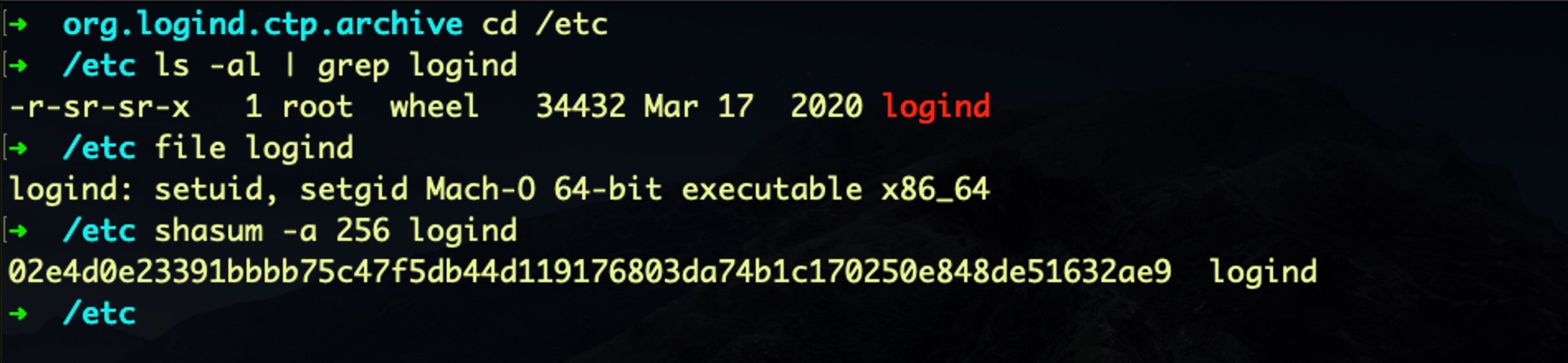
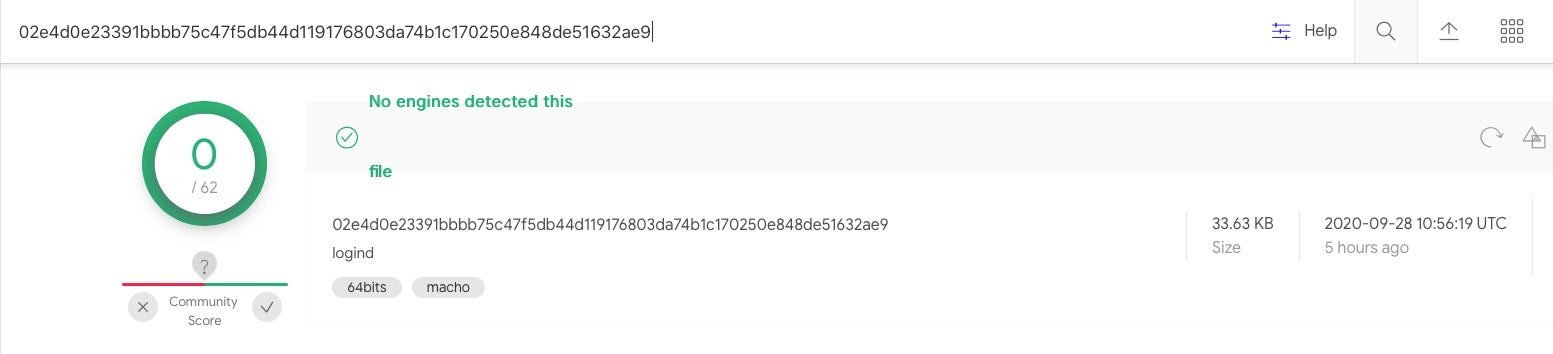
While the path at /etc/logind (or /private/etc/logind) is well-known for this malware (see the next section), the executable dropped in our test is currently unknown on VirusTotal and, to our knowledge, has not been shared before:
02e4d0e23391bbbb75c47f5db44d119176803da74b1c170250e848de51632ae9
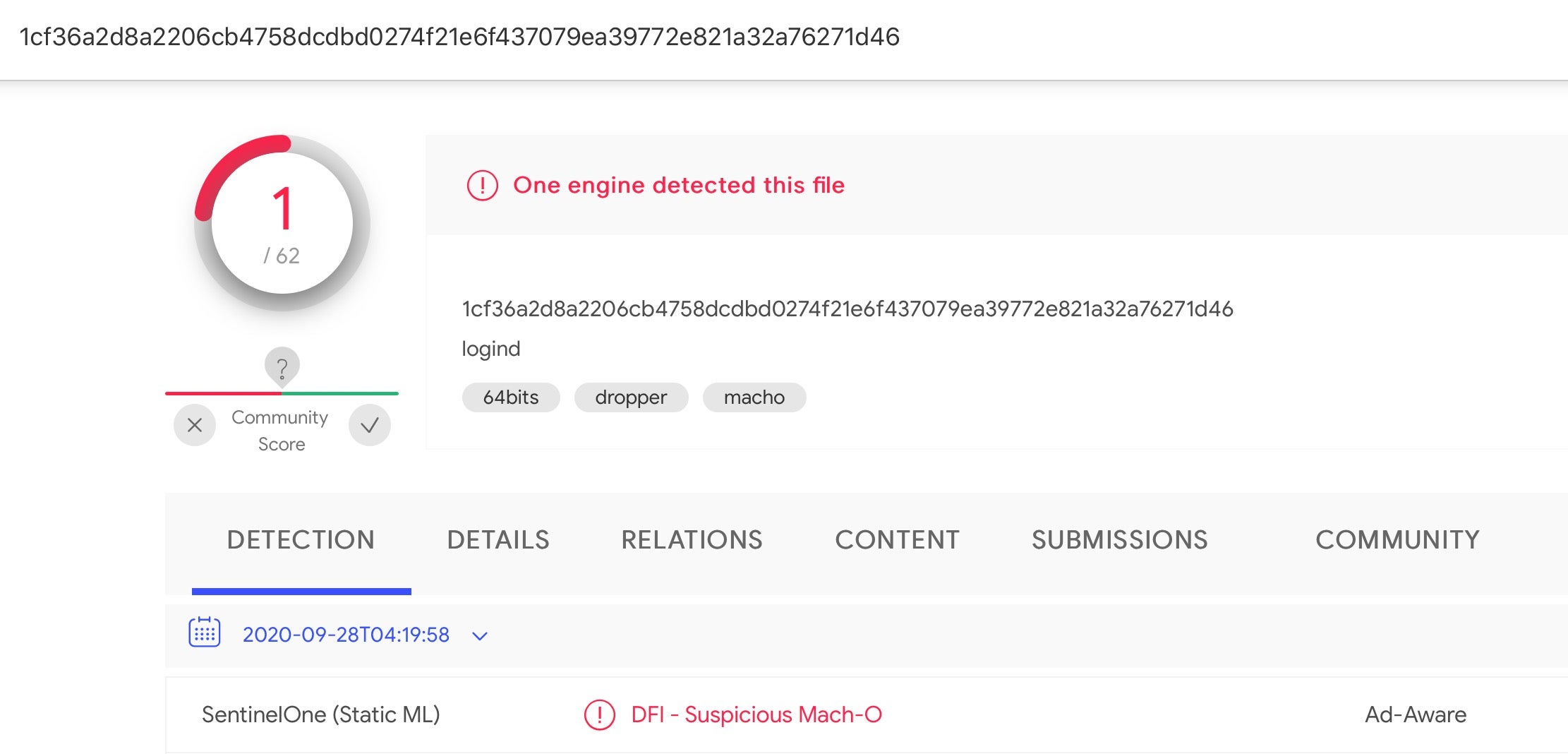
A different file with the same name, but also apparently virtually unknown on VT, appears at
/Library/Frameworks/Storage.framework/Contents/MacOS/logind
1cf36a2d8a2206cb4758dcdbd0274f21e6f437079ea39772e821a32a76271d46
Is FinSpy A New Kind of Fully Undetectable Malware?
Malware authors and resellers are always keen to paint their products as ‘undetectable’ or ‘fully undetectable’ (FUD) to attract customers, and we are sure those who market tools to “Law Enforcement and Intelligence Agencies” are just as concerned to make the same claims. If you’re in the market for buying malware, particularly spyware, then being undetectable is pretty much the first feature on your shopping list.
Despite such claims, very little malware is truly “fully undetectable”, simply because it needs to behave in certain, predictable ways in order to fulfil its objectives (for example, log keystrokes, communicate with a C2 and so on), and in this regard FinSpy is no different.
In fact, elements of FinSpy have been known to security researchers and static search engines for some time. In particular, a user path used by FinFisher for the persistence agent:
~/Library/LaunchAgents/logind
has been known since at least 2017. Other path elements can be seen added to Apple’s MRT.app in stages over recent months, with new detection paths added in v1.52 and v1.64:
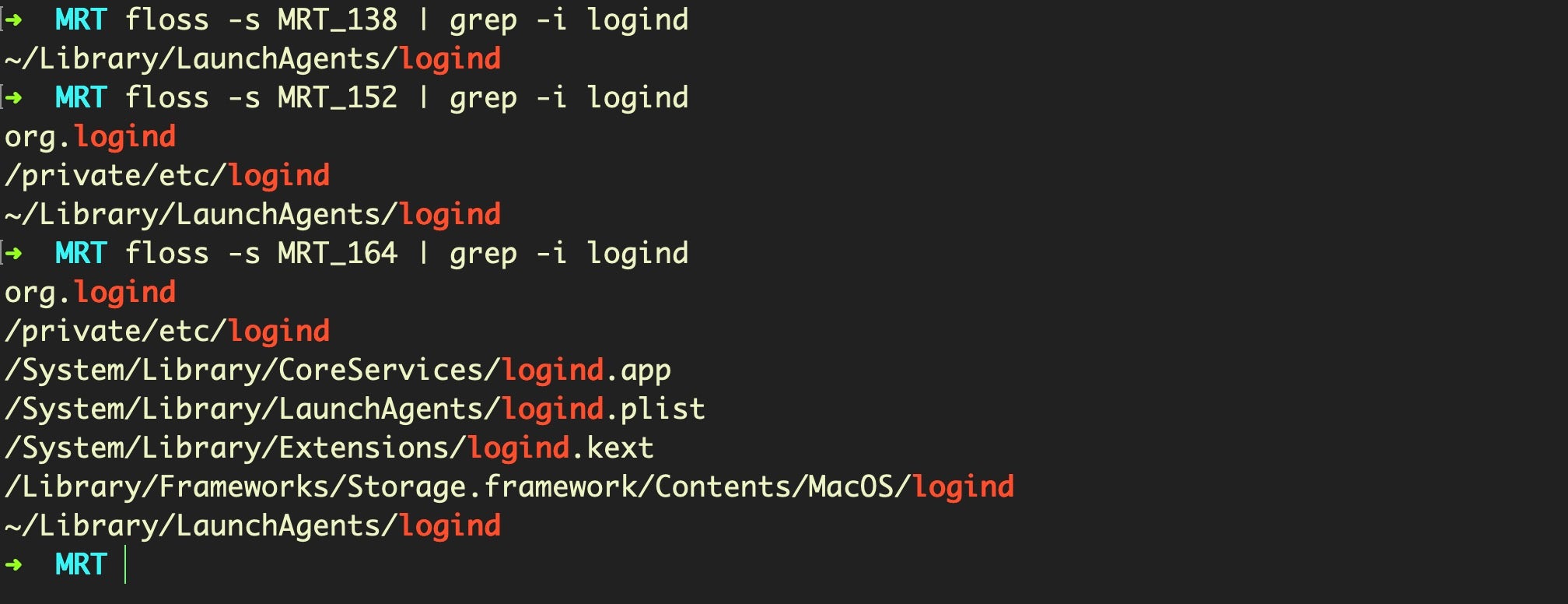
Despite that, even the current MRT.app, v1.66, still doesn’t search for the LaunchAgent at the domain level.
More importantly, however, is that MRT.app’s detections don’t prevent Mac users from becoming victims of FinSpy. Apple’s MRT.app is a post-infection tool that runs at periodic intervals: primarily, when the user boots the Mac or logs in to a user account, as well as when the tool is silently updated by Apple in the background.
In order to actually try and prevent launch and execution of malicious code, Apple uses a number of different technologies: namely, Gatekeeper, Notarization and XProtect. While useful, the first two suffer from the weakness that they are overridable by the user, meaning that the malware can be installed either by socially engineering the victim or by a malicious user with temporary access to the victim’s computer.
On macOS 10.15 Catalina, XProtect has become far more robust and resistant to user bypassing, but XProtect is only as useful as the signatures it contains. Since in our test we were able to execute both the FinSpy trojan installer and the hidden malicious application bundle it includes on a macOS Catalina 10.15.7 installation, we surmise that XProtect has yet to catch up with the latest FinSpy samples.
Does SentinelOne Protect Against FinSpy / FinFisher Malware?
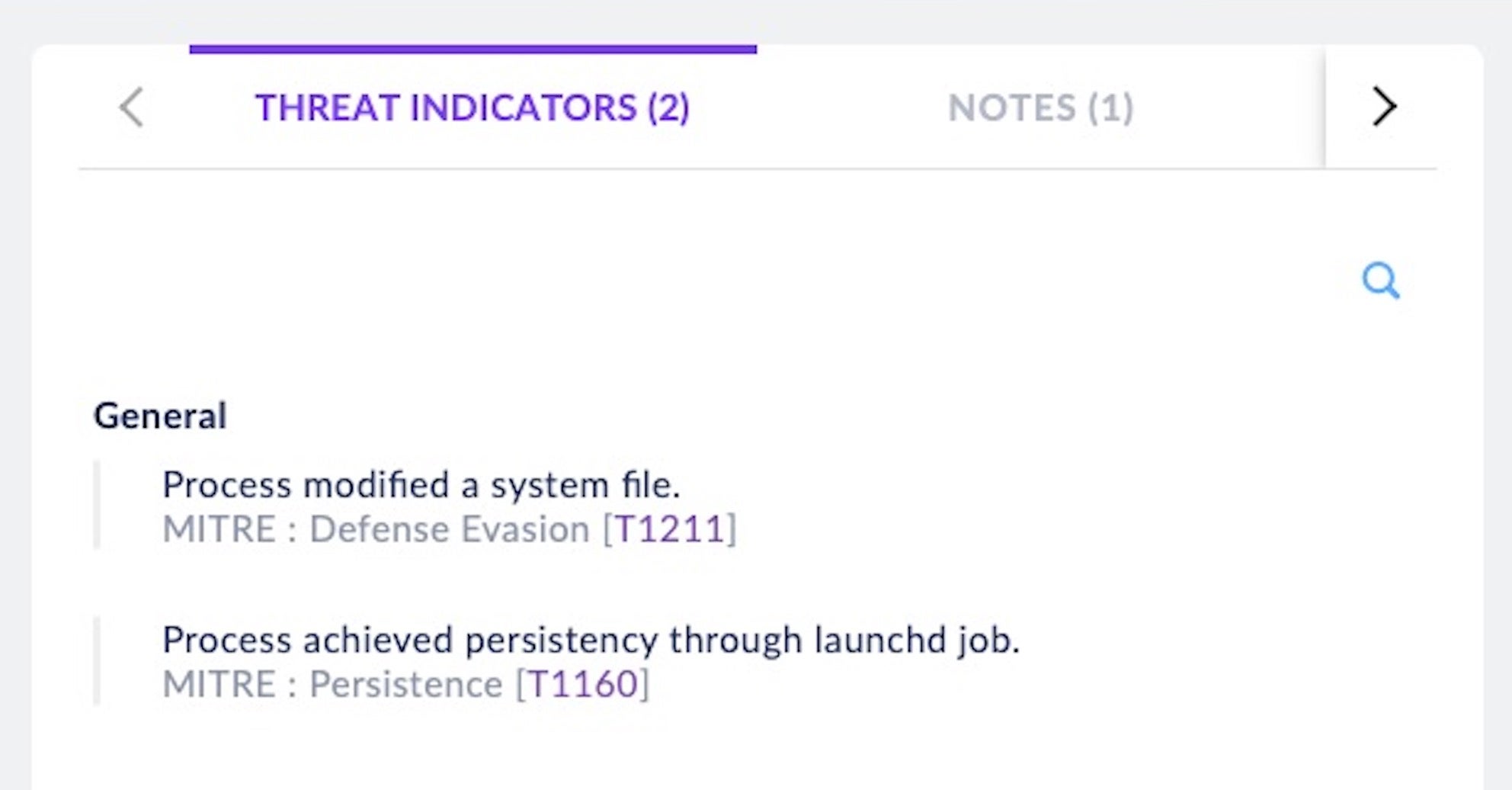
Our test of the above samples shows that the SentinelOne agent correctly detects and blocks FinFisher/ FinSpy for macOS malware.
Our behavioral detection reveals that the FinSpy malware attempts Defense Evasion and Persistence, which we map to MITRE ATT&CK TTPs T1211 and T1160, respectively.
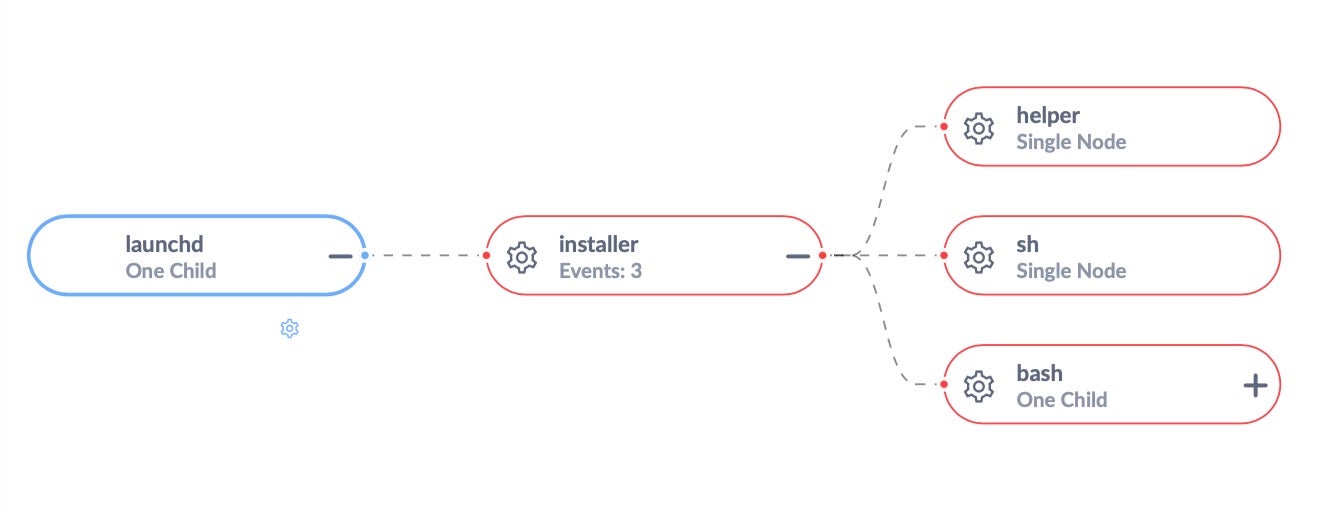
The SentinelOne management console Process Tree accurately maps the execution of malicious processes, correctly convicting those that belong to the malware (in red):
Conclusion
FinFisher’s FinSpy malware for macOS is a commercially produced and distributed product aimed at infecting Mac users for the purposes of spying, stealing data and remotely controlling the target machine. While we pass no judgement on whether this spyware is being ‘legitimately’ used by law enforcement or intelligence agencies around the world, we remain committed to ensuring that SentinelOne customers are fully protected from infection by this or any other unauthorized software on their endpoints. If you would like to see how SentinelOne can help protect your business, contact us today or request a free demo. For more insight into macOS malware threats, see here.
Indicators of Compromise
/Volumes/caglayan-macos/Install Çağlayan.app/Contents/MacOS/.log/ARA0848.app/Contents/MacOS/installer (Mach-O)
SHA256: 651bc82076659431e06327aeb3aacef2c30bf3cfd43ae4f9bc6b4222f15bb673
SHA1: 2584f1119c65ffd0936e2916b285389404b942c9
/private/etc/logind (Mach-O)
SHA256: 02e4d0e23391bbbb75c47f5db44d119176803da74b1c170250e848de51632ae9
SHA1: 62e5dc40bfabaa712cd9e32ac755384db07f0dab
/Library/Frameworks/Storage.framework/Contents/MacOS/logind (Mach-O)
SHA256: 1cf36a2d8a2206cb4758dcdbd0274f21e6f437079ea39772e821a32a76271d46
SHA1:d3dab40d51e1b4ff332b6be1c993c916c3d58481
~/Library/Caches/org.logind.ctp.archive/helper (Mach-O)
SHA256: 562c420921f5146273b513d17b9f470a99bd676e574c155376c3eb19c37baa09
SHA1: 72cb14bc737a9d77c040affa60521686ffa80b84
~/Library/Caches/org.logind.ctp.archive/helper2 (Python Script)
SHA256: af4ad3b8bf81a877a47ded430ac27fdcb3ddd33d3ace52395f76cbdde46dbfe0
SHA1: 9a0ede8fad59e7252502881554be0c21972238c9
~/Library/Caches/org.logind.ctp.archive/helper3 (Mach-O)
SHA256: 6ab836d19bc4b69dfe733beef295809e15ace232be0740bc326f58f9d31d8197
SHA1: 427a1c1daf9030069f0c771ce172c104513a7722
~/Library/Caches/org.logind.ctp.archive/installer (Mach-O)
SHA256: ac414a14464bf38a59b8acdfcdf1c76451c2d79da0b3f2e53c07ed1c94aeddcd
SHA1: a65965b960b3d322bbae467f51bf215d574b00cc


