As security professionals, one of our primary challenges and responsibilities is understanding how to protect, detect, and respond to cyber attacks across all the operating systems within our enterprise environment. Most organizations today have mixed fleets running various flavors of Windows, macOS, and Linux. The operational reality is that in many cases a sizable portion of some or all of these endpoints will not be on the latest release of their respective operating system version.
Pause and think about your own environment: What is the percentage of endpoints running Windows 10 20H2? What is the primary operating system version for your servers? Are they really all on Windows Server 2019, or are they predominantly on Windows Server 2012 R2? If you are in the Pharmaceuticals or Manufacturing industry, what is the operating system that runs the production line?
In this post, we discuss why it is essential for security professionals to understand the complexities of different operating systems and endpoint types in their enterprise environment when choosing security products.

Attackers Always Look for the Weakest Link
Attackers do not care where the target is located, which operating system they are targeting, or if this endpoint is a known or unknown device. The chances are very high that during an attack, as they are jumping between endpoints, they are targeting different types of operating systems, and some of these endpoints might be in a blind spot for the security team. In the end, as an attacker, they want to reach their end goal by any means necessary.
Working in IT Security means understanding how to harden the environment and protect, detect, respond, and recover against cyber attacks. When choosing the technology you need to achieve these goals, it is critical to deeply understand operating system differences, their respective attack surfaces, and what capabilities your chosen tools have to perform tasks like Digital Forensics Incident Response (DFIR).
For example, the last thing you want when responding to an incident is to realize that your ability to open a remote shell is only available on 10% of your fleet because your tool only supports that feature on Windows 10 1809 or higher. Faced with such a roadblock at such a critical juncture, you would be forced to collect each endpoint physically before being able to perform some vital forensics tasks. By then, it may be too late.
Understanding Threats in Context is Vital
Dealing with commodity malware should be trivial. Today, SOC analysts shouldn’t need to spend time investigating commodity malware that even a legacy Antivirus solution should be able to just prevent. Instead, SOC analysts should spend most of their time defending against more sophisticated attacks; for that, it is critical to understand the correlations between a chain of activities.
To aid with that, the SentinelOne platform provides ActiveEDR powered by Storyline – a powerful capability that provides real-time actionable correlation and context, allowing SOC analysts to understand the whole storyline of the attack as it’s happening.
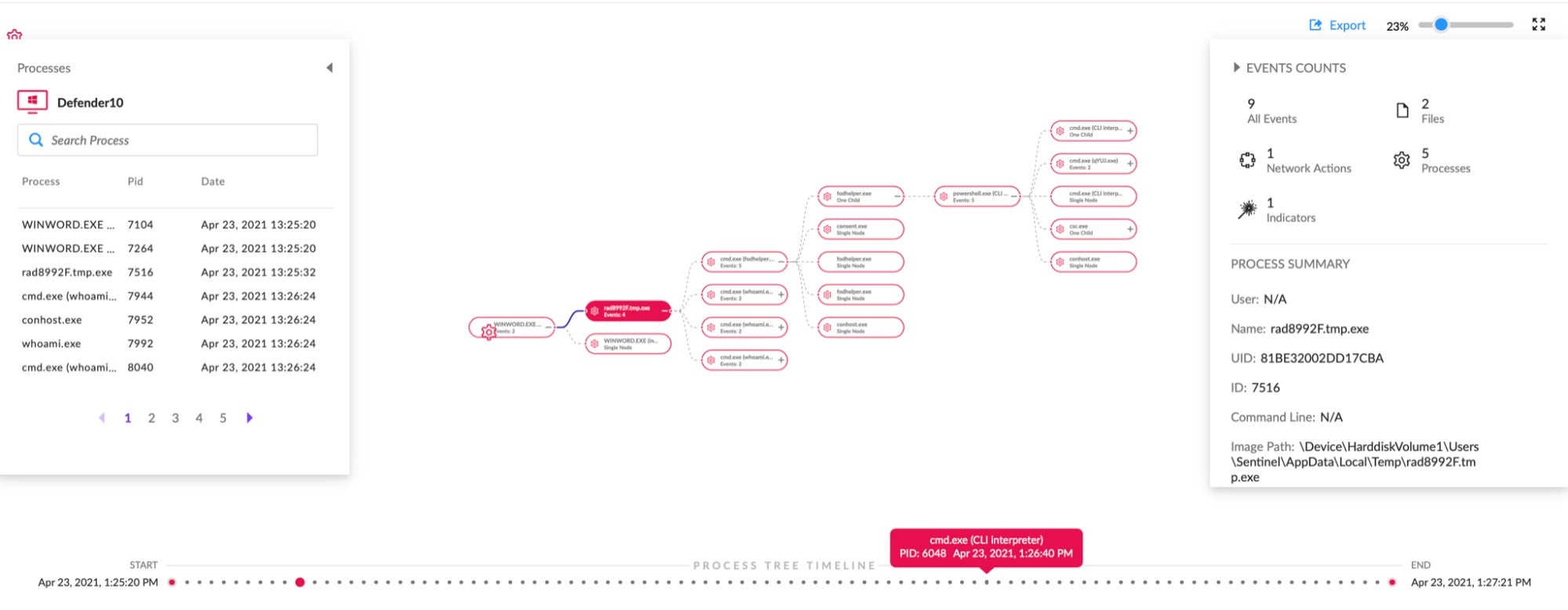
Visibility Is Crucial for Effective Threat Hunting
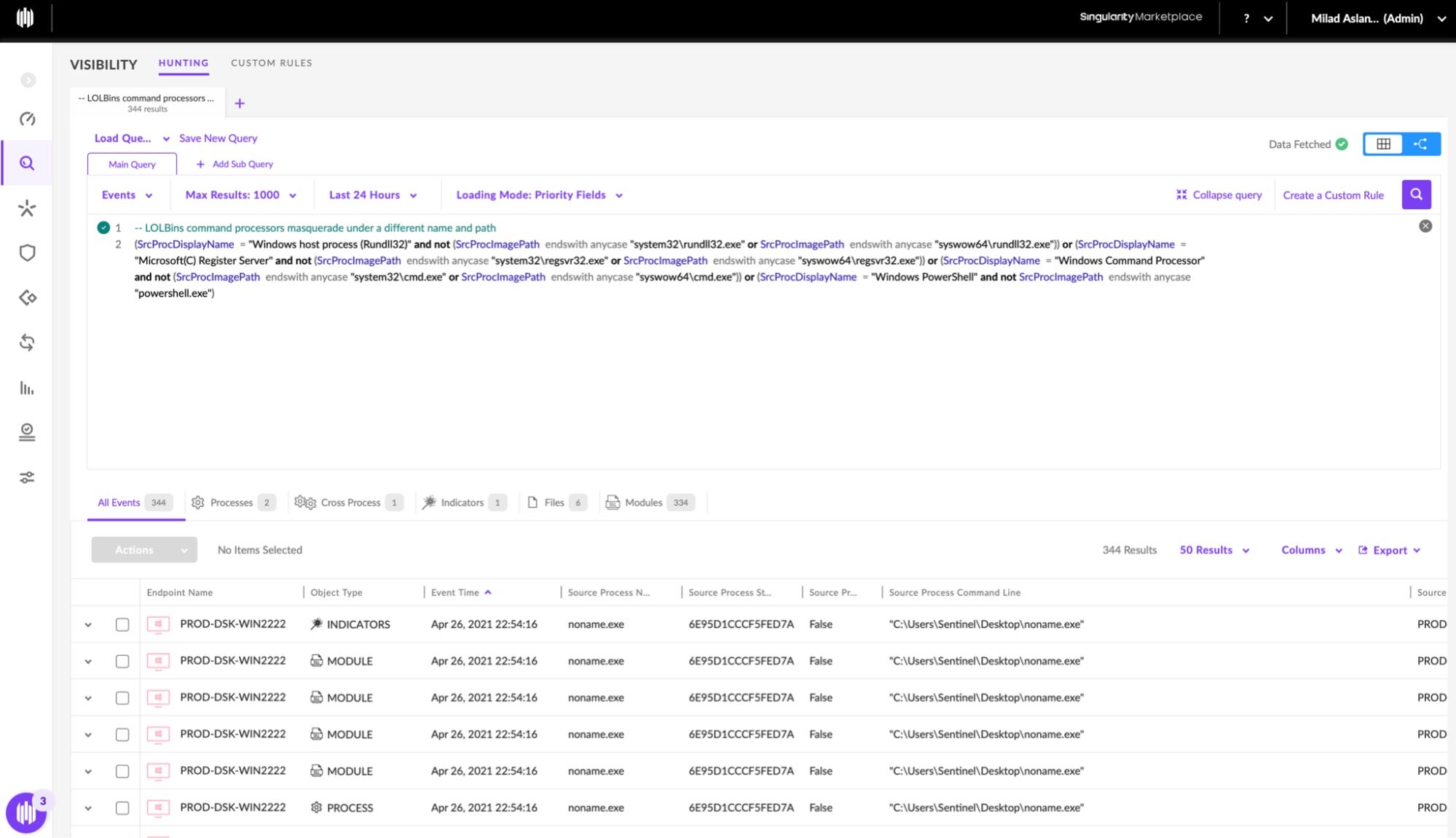
Sometimes, just preventing or detecting threats isn’t enough and we need to unleash the threat hunter in us. Consider the situation when you receive new threat intelligence and decide to sweep the environment for a specific Indicator of Compromise (IOC) or Indicator of Attack (IOA). For that, you can’t just rely on the prevention or detection logs from your security solution. Because when your CISO or Head of Security Operations asks “are we impacted by XYZ?” the response can’t be “Not sure, but our tools didn’t alert on it.” They expect you to know, so you must be able to sweep the environment. That’s the time when you need to be able to access contextualized telemetry data in order to hunt for the unknown.
SentinelOne’s Deep Visibility was built with this kind of situation in mind. You can leverage an intuitive, SQL-like query language to quickly search the entire contextualized dataset of your SentinelOne instance.
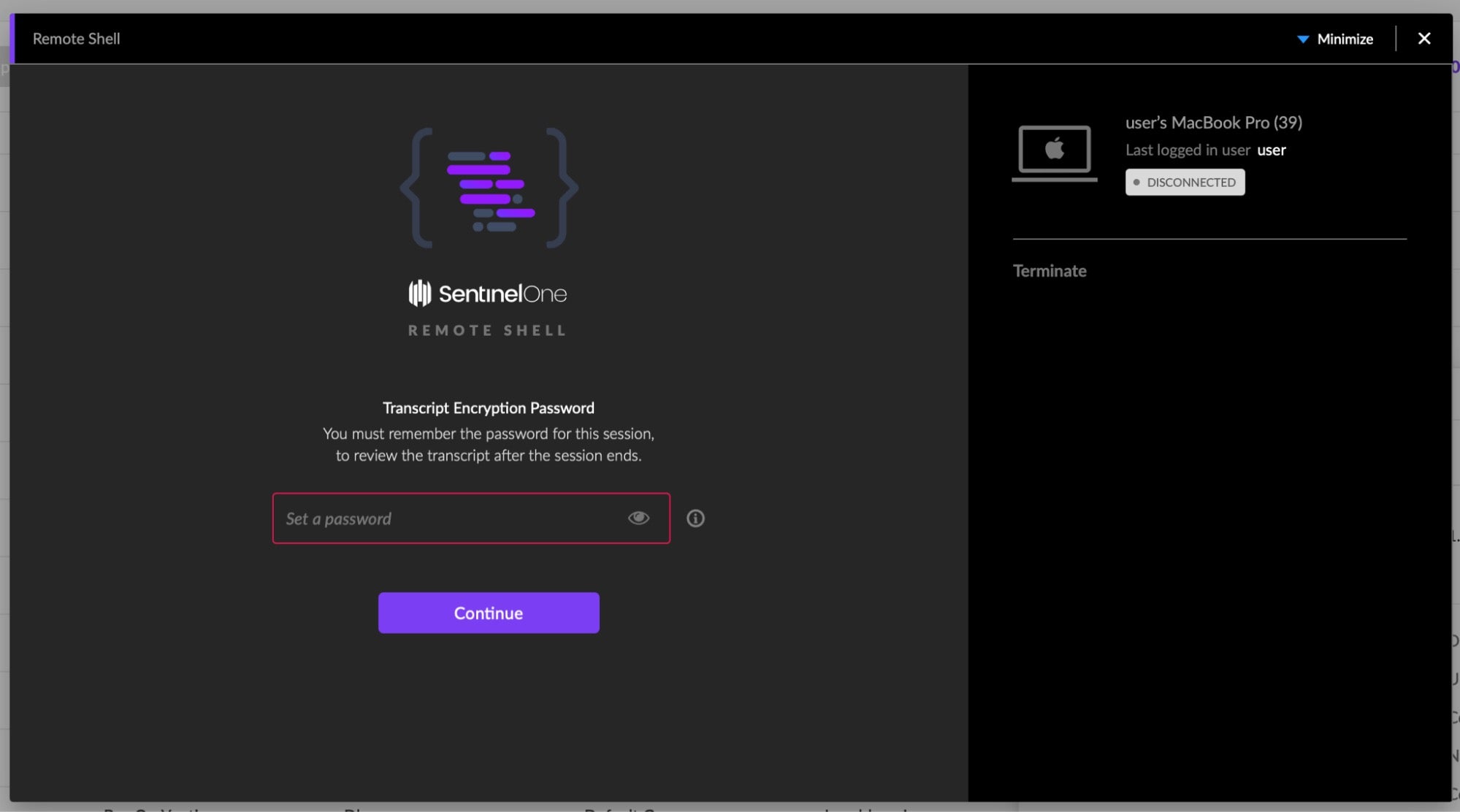
Of course, when we are investigating a threat, it can sometimes be handy or even a necessity to perform more advanced digital forensics activities. For example, you might need to collect hibernation files, memory dumps or list some of the registry hives. To do so, historically we would need to gain physical access to an endpoint. Nowadays, with employees working from home or on remote sites, this has become exponentially more difficult.
The answer is a secure, remote shell capability. With SentinelOne’s Full Remote Shell capability, you can connect directly to the target endpoint to carry out any necessary tasks across all your SentinelOne-protected endpoints, regardless of what OS your endpoints are running.
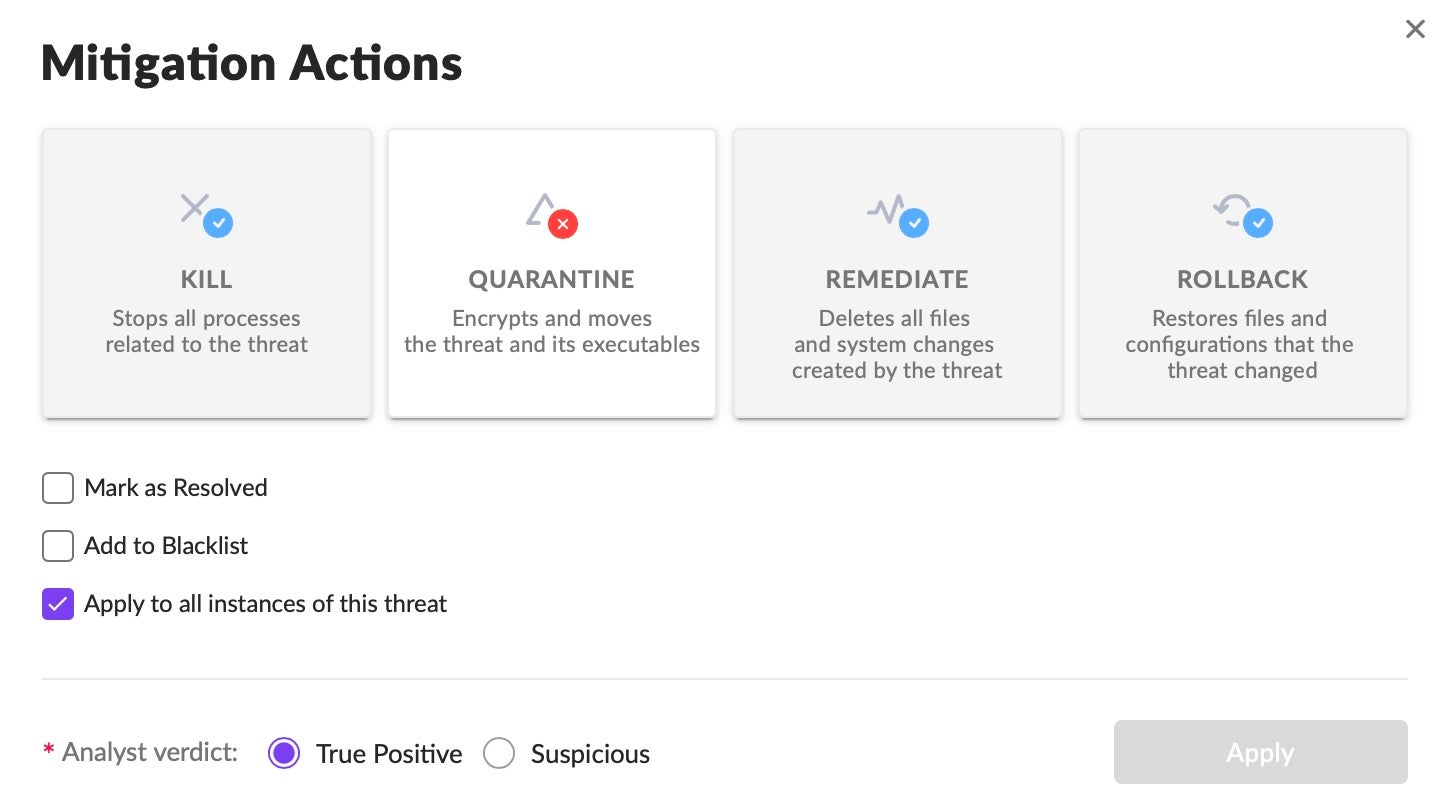
Remediation and Mitigation Needs To Be Simple
Once we understand the incident, it’s time to move into the remediation and containment phase. Typically, you are looking for mitigation actions like stopping all processes related to a threat, encrypting and moving the threat and its executables into quarantine, deleting all files and system changes created by a threat and, if required, to restore file configurations that the threat changed.
While SOC analysts often have their hands full resolving incidents, administrators need to manage the security posture of the enterprise environment including such things as managing device control policies, hardening policies, firewall policies and access vulnerability management information.
Historically, this work required both analysts and security administrators to master a variety of different IT systems depending on the operating system, and sometimes even waste time opening an IT help desk ticket to implement a change.
When choosing a modern security solution, look for tools that simplify the security stack and offer a single and simple interface for managing security controls, mitigation, remediation, threat hunting and all other aspects related to security.
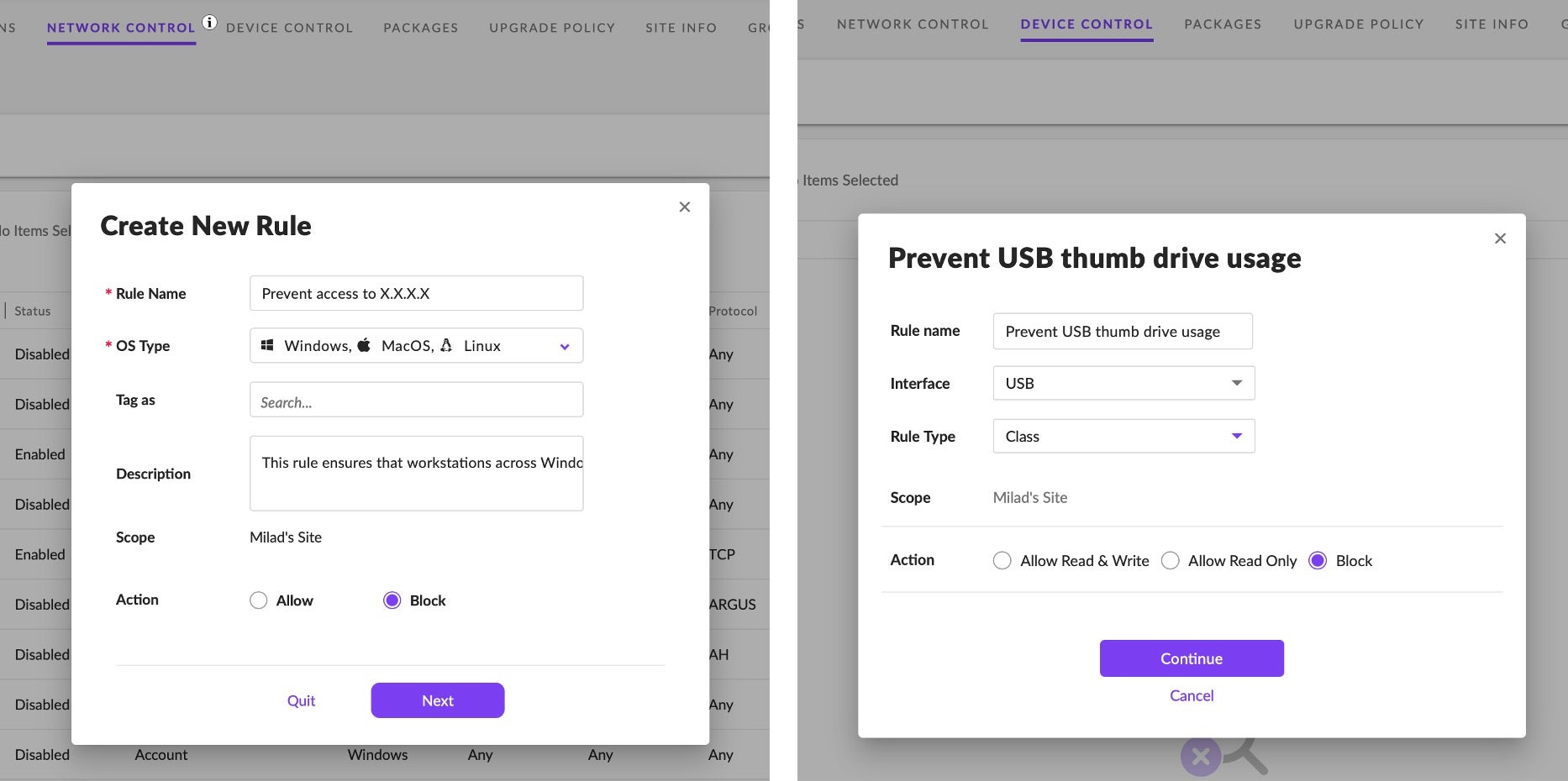
The benefits here include being able to train people faster on a common platform and avoiding baked-in institutional knowledge that revolves around a few specialists who know how to handle obscure and often legacy software. With the right interface, you can reduce the time it takes to deal with threats, which should be simple, intuitive and easy to learn.
With SentinelOne, all these functions are available within one console, empowering everyone dealing with security, from the SOC team to security administrators, to manage whichever functions are appropriate to their work across Windows, macOS, and Linux. Features like customizable Role-based access control ensure that each person and group in your organization only has access to the features they need to do their work effectively.
We Are All In This Together: One Team
As we know cybersecurity is a team sport and not every organization has the resources to staff a dedicated SOC. That’s why SentinelOne offers Vigilance MDR, a Managed Desktop Response (MDR) and Digital Forensics Incident Response (DFIR) service to support your security department. Our analysts are subject matter experts when it comes to detecting and responding to cyber-attacks. They monitor and where needed, react to all suspicious behaviours regardless of which operating system type, version or location of the endpoint.
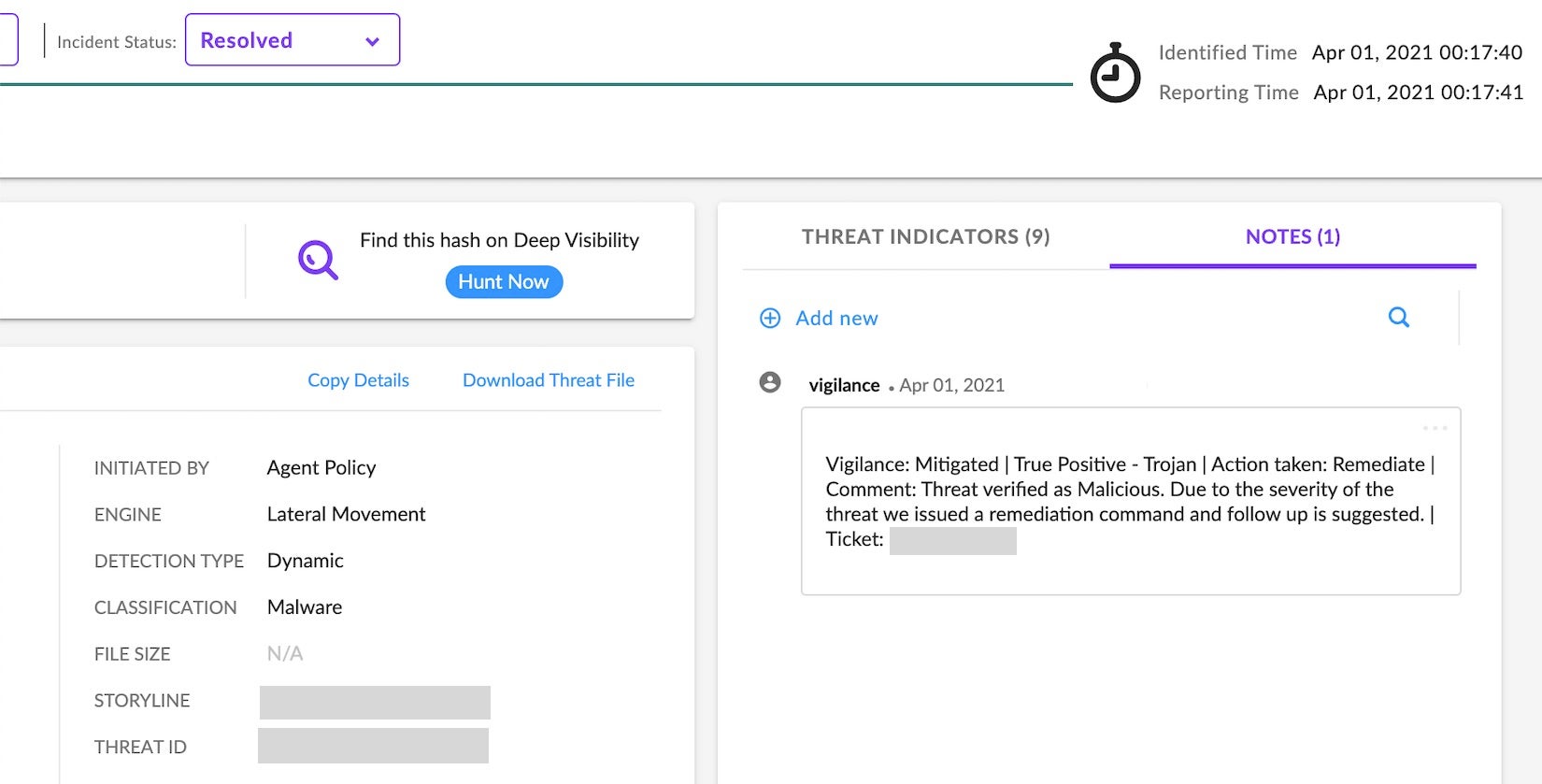
Gain Visibility Into the Unknown
When looking into an enterprise environment today, do we really know what is connected? Or is it more likely that we have a relatively good understanding of what should be connected, and we might just assume that we prevent unauthorized access to the network?
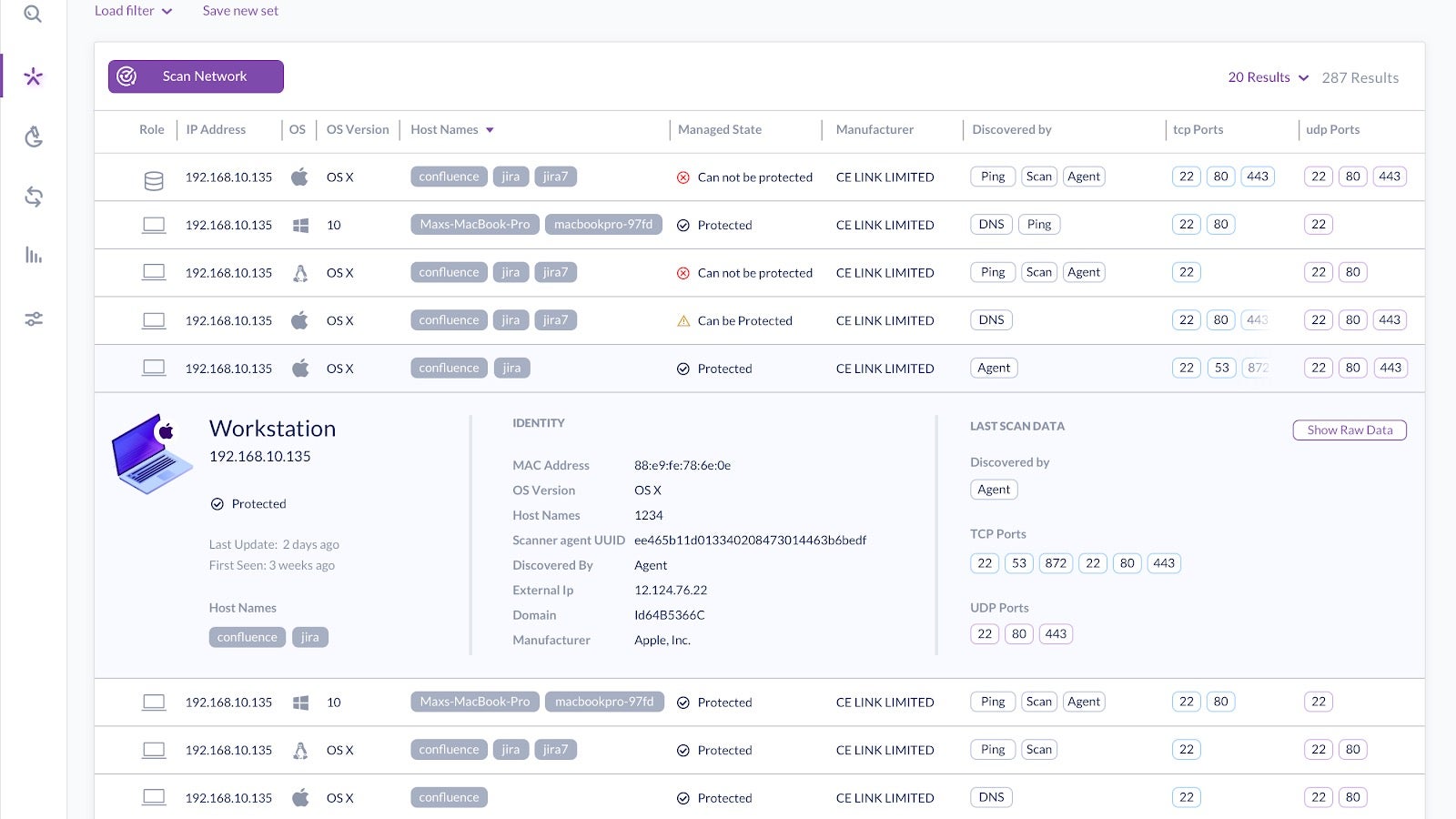
Today, because our networks often contain not only traditional endpoints but a variety of other devices such as IoT and Operational Technology (OT)-type devices, it can be difficult for admins to know exactly what’s on the network.
SentinelOne’s Ranger capability addresses this problem by turning your SentinelOne agents into a distributed sensor network that combines passive and active reconnaissance techniques to build a map of everything in your environment. With that, you gain critical visibility across managed and unmanaged endpoints regardless of their operating system and endpoint type.
Conclusion
As security professionals, every day brings us fresh challenges. Some of us might be working on responding to an incident; others might be working on identifying ways to improve the security posture of the enterprise environment. In the end, our line of work requires us to have a good understanding of the enterprise environment. Only by having the right tools with the right level of visibility will we be successful in protecting, detecting, responding, and recovering in times of need. Therefore, it is crucial to select your endpoint security vendor based on whether they can provide you with the comprehensive capabilities required across your entire digital estate.
At SentinelOne, we understand that enterprises have different operating system types, versions and endpoint types. Therefore, we provide a comprehensive endpoint security platform that supports all major operating systems and offers feature parity for different versions of Windows, macOS, and Linux.
If you would like to learn more about how SentinelOne can help protect your entire organization, contact us for a free demo.


