We are delighted to announce the next step in SentinelOne’s role-based access control (RBAC) capability: supporting fully custom roles. After collecting customer feedback for this new feature, we are now delivering it to the benefit of our global customer base, including but not limited to multi-site enterprises spanning multiple geographies.
Admins now have the flexibility to create unique roles with custom permission settings tuned to the specific needs of their organization, directly from the SentinelOne management console. The six (6) predefined roles – Viewer, C-Level, IT, SOC, IR Team, and Admin – remain unchanged and immediately available, to assist customers with a quick start. Administrators can also create granular API orchestration roles specific to an XDR workflow.

Custom RBAC Roles
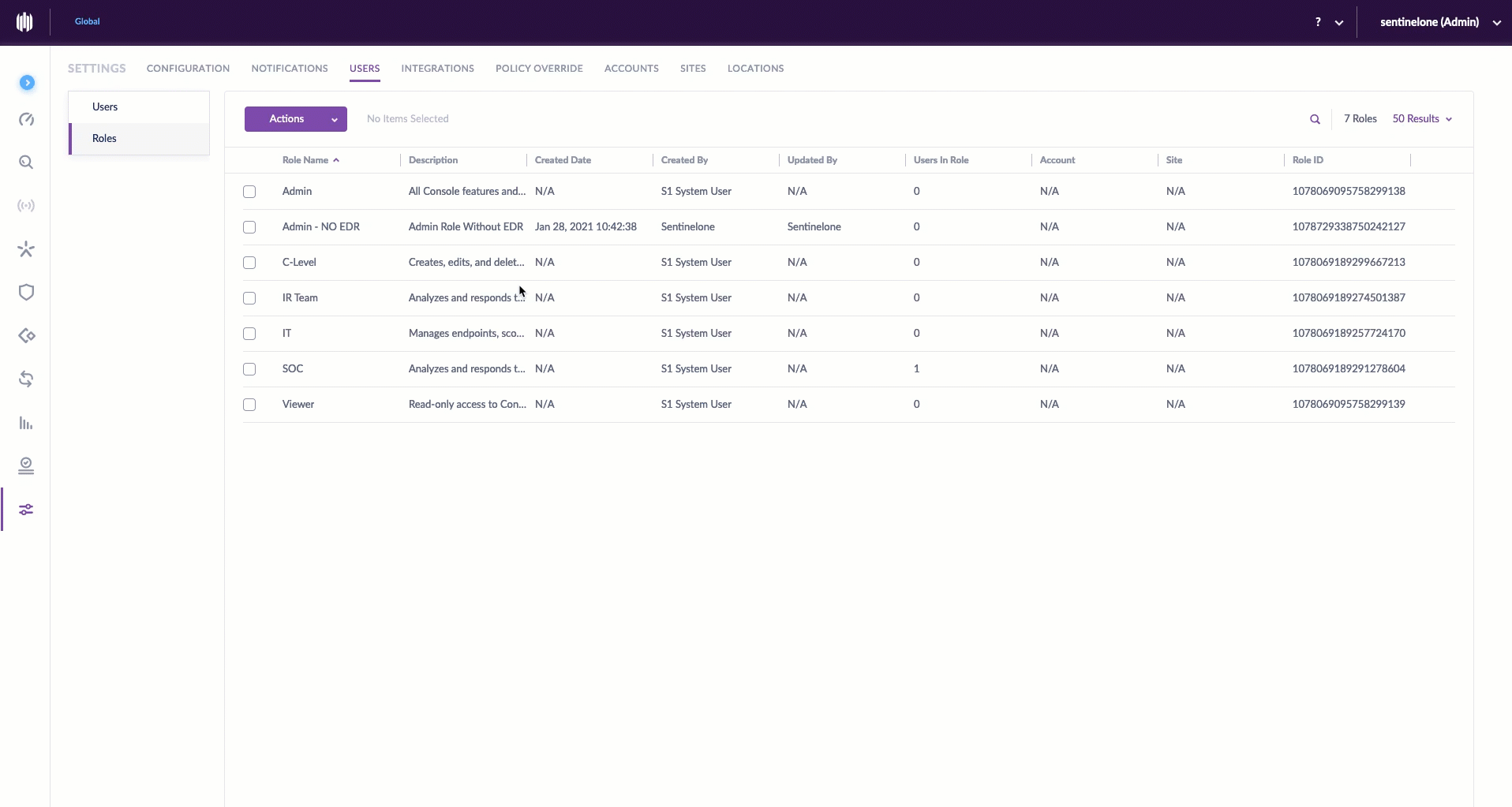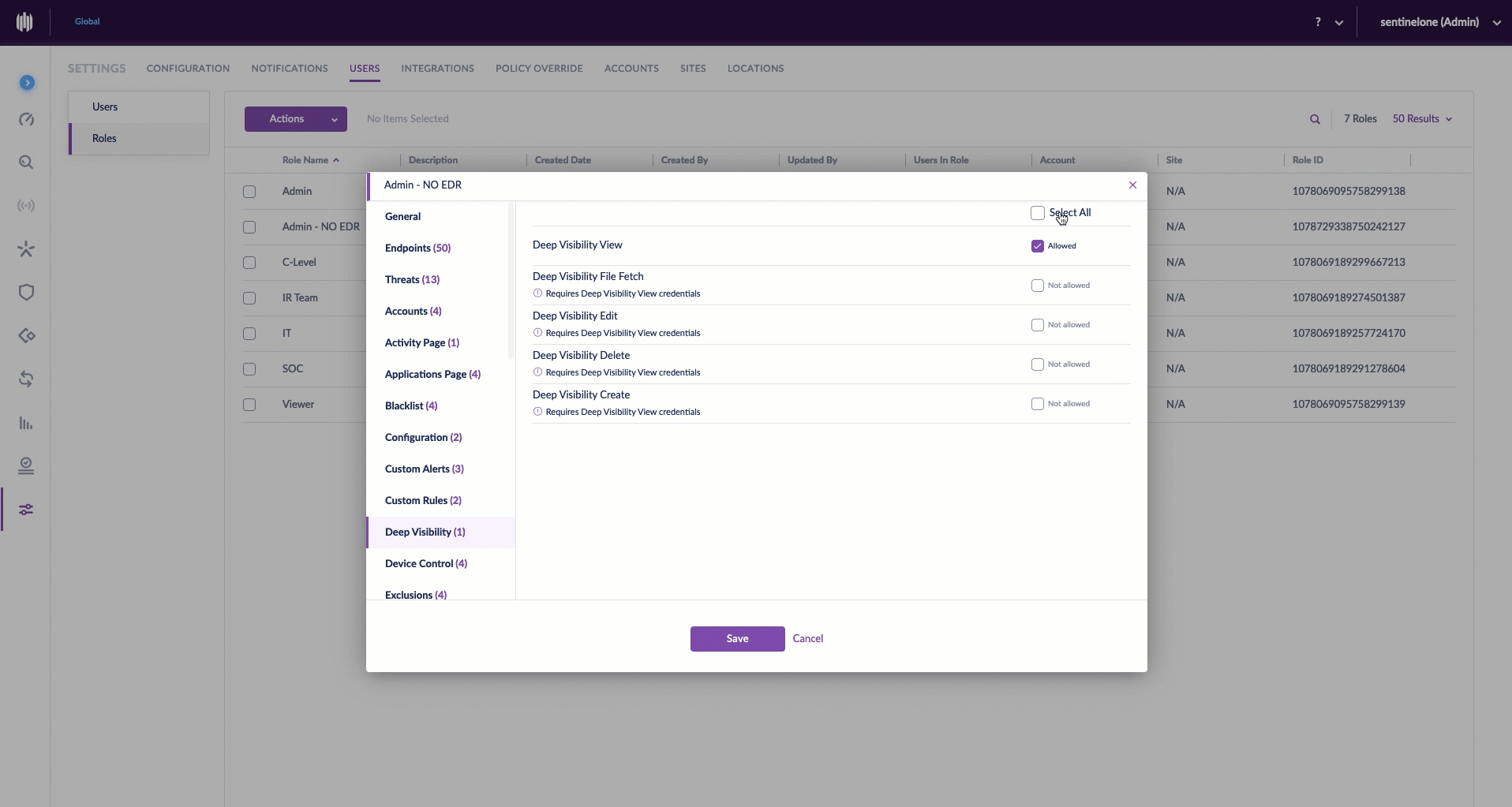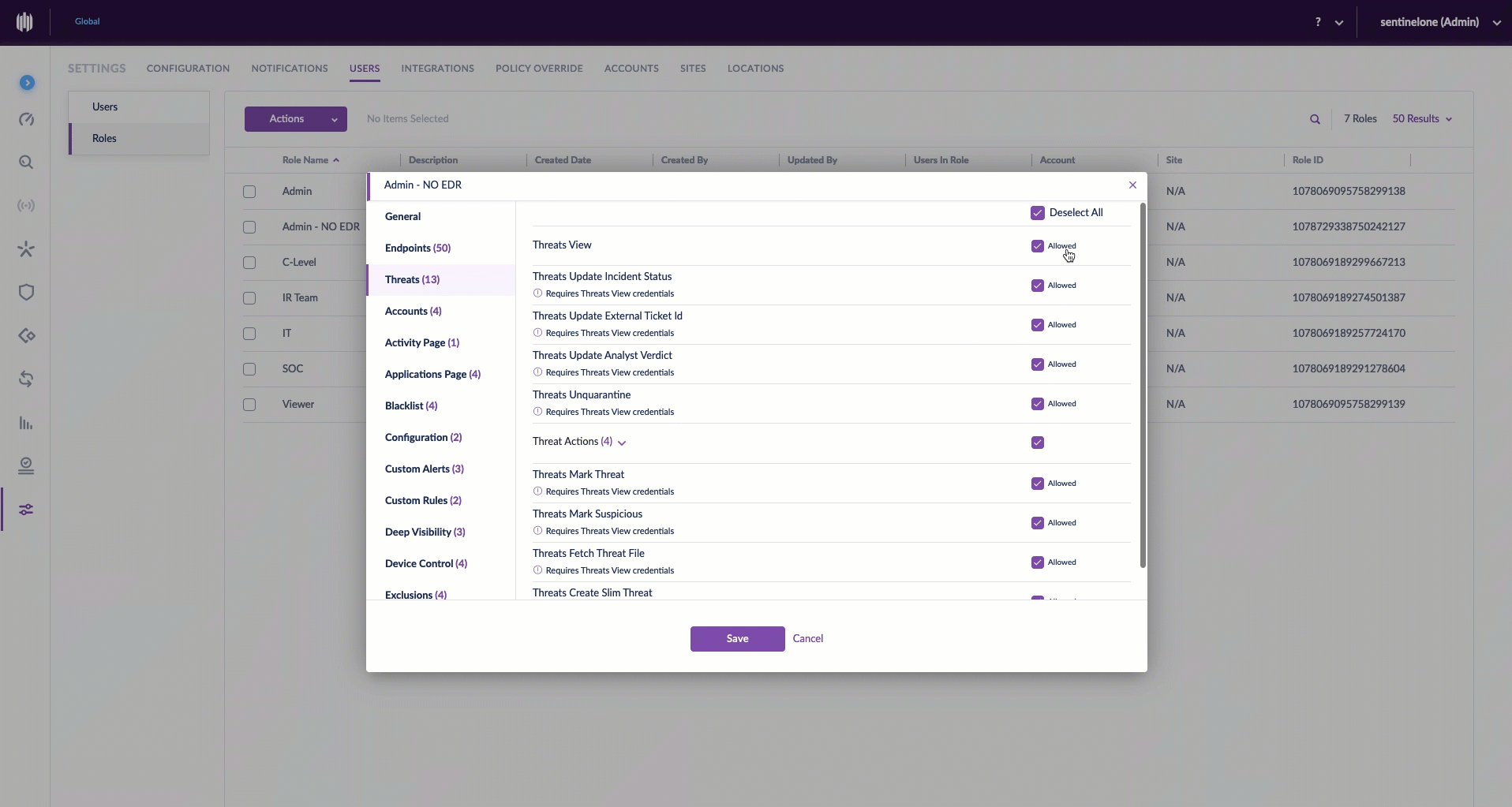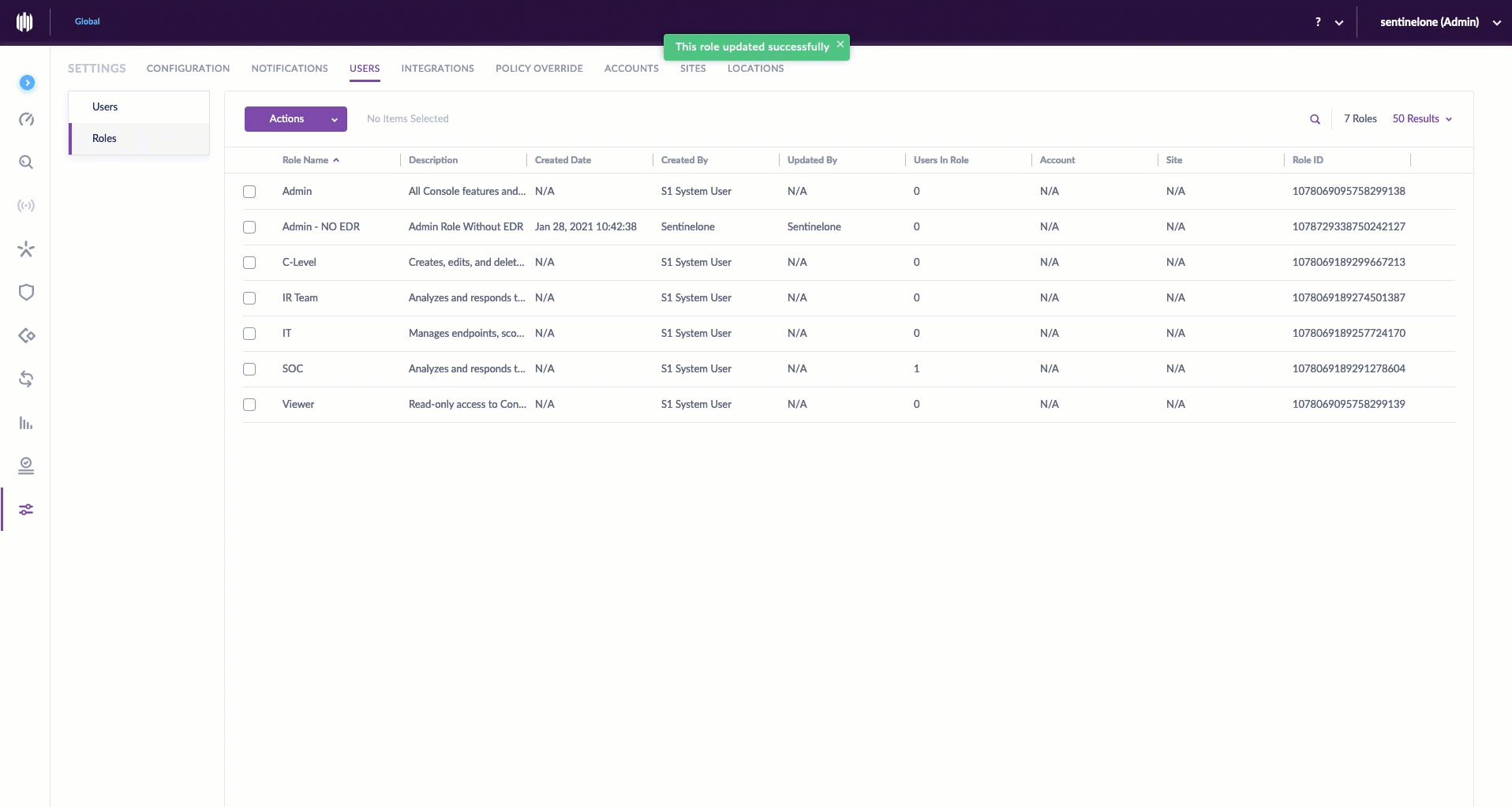
Each SentinelOne customer can now customize permissions so that user experience is optimized for diverse groups of user personas in their organization. Building upon the principle of least privileges, administrators can build and fine-tune the right access level to the minimum set of resources which users need to do their job effectively, striking the right balance between business agility and security. For example, an administrator would not likely grant configuration change privileges for production assets to security analysts, who would instead alert the application owner for follow-up, or perhaps a persona in one site requires different permissions than a similar role at another.
Creating a Custom Role
Creating a custom role is simple. Before starting, make sure you have the appropriate scope selected. Then, from the Settings Panel, select the Users tab. Click Roles, and under Actions, New Role. Give it a unique name and description, then click to select/deselect the various permissions for this role. Once saved, you can assign users to the new role. It’s even easier than it sounds.
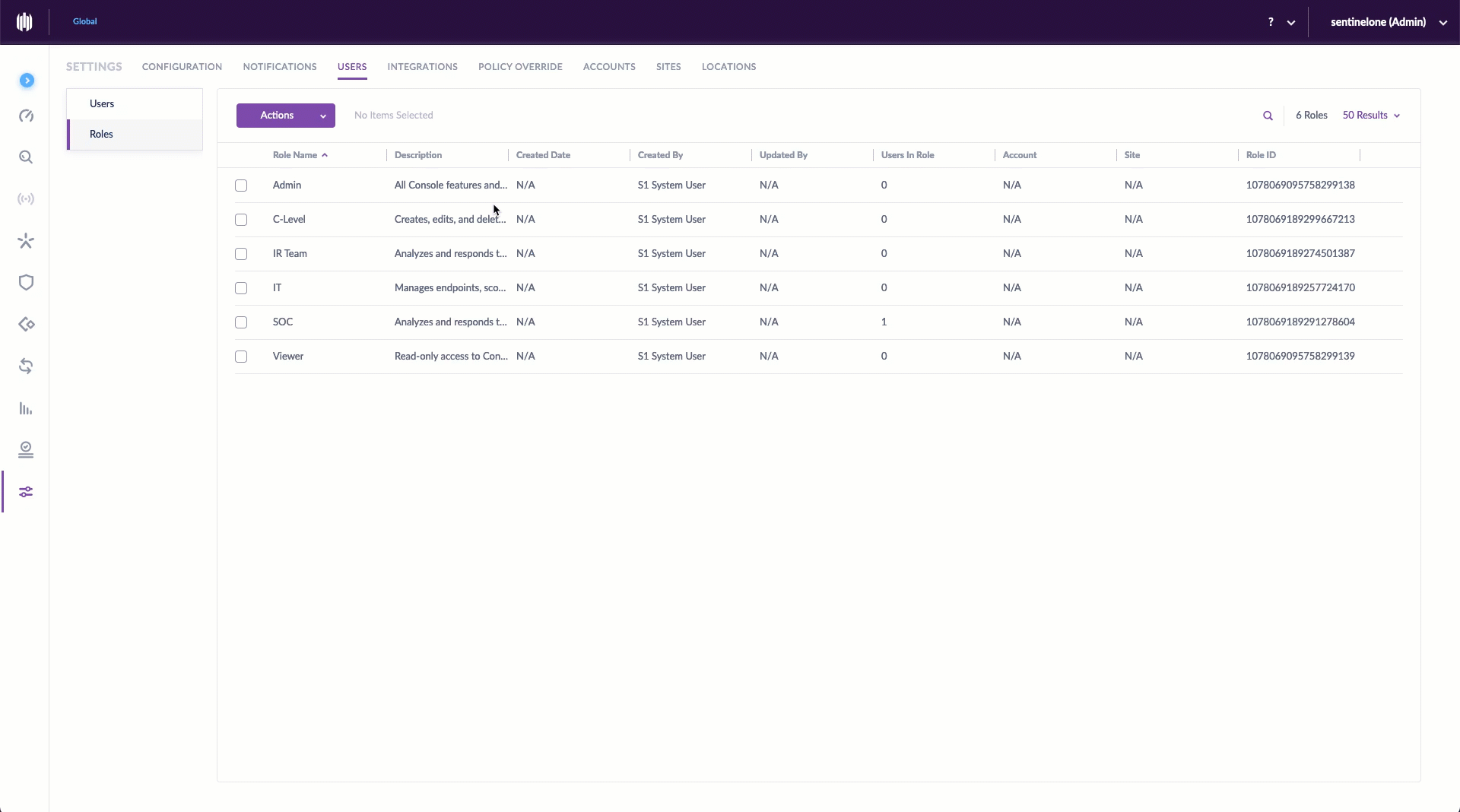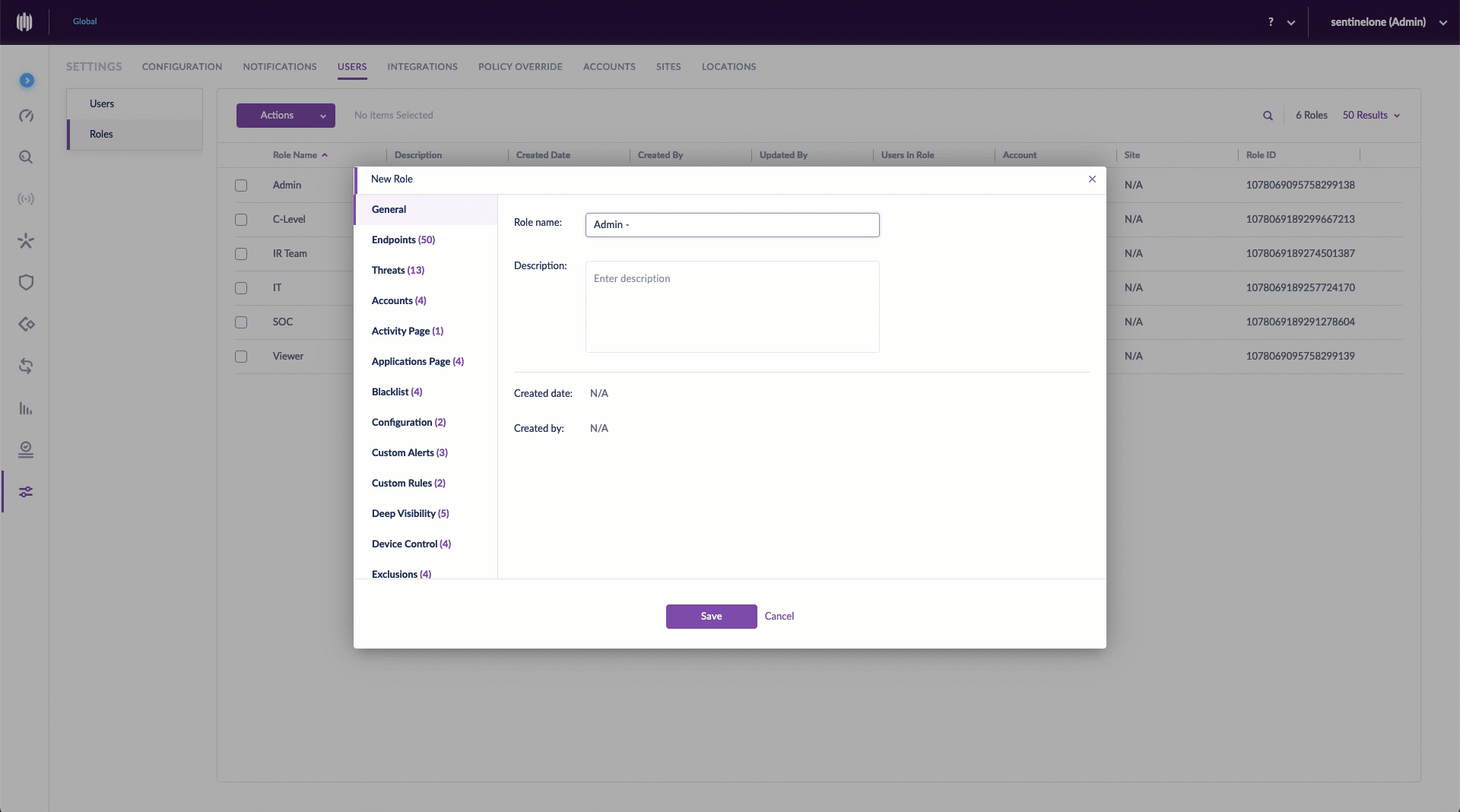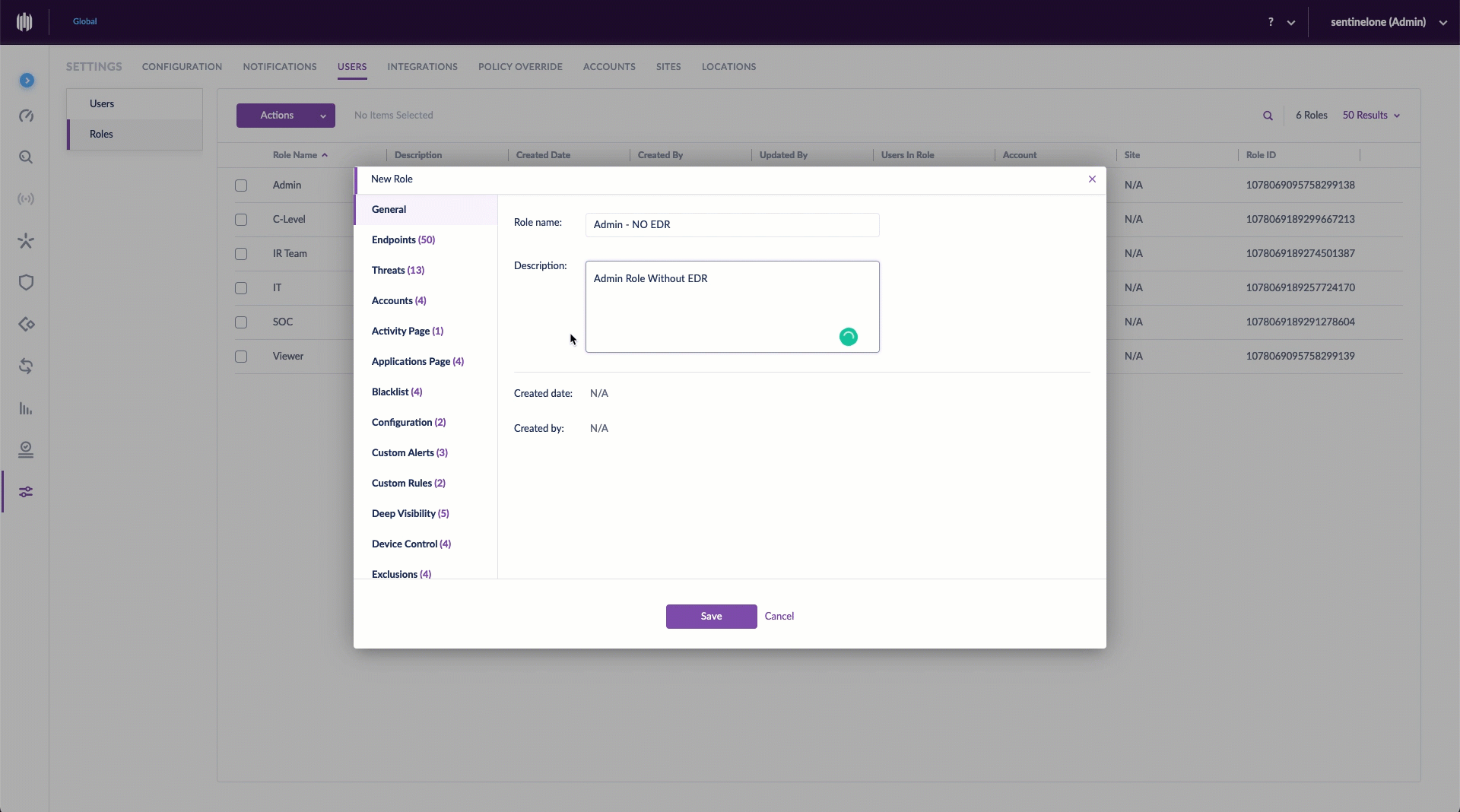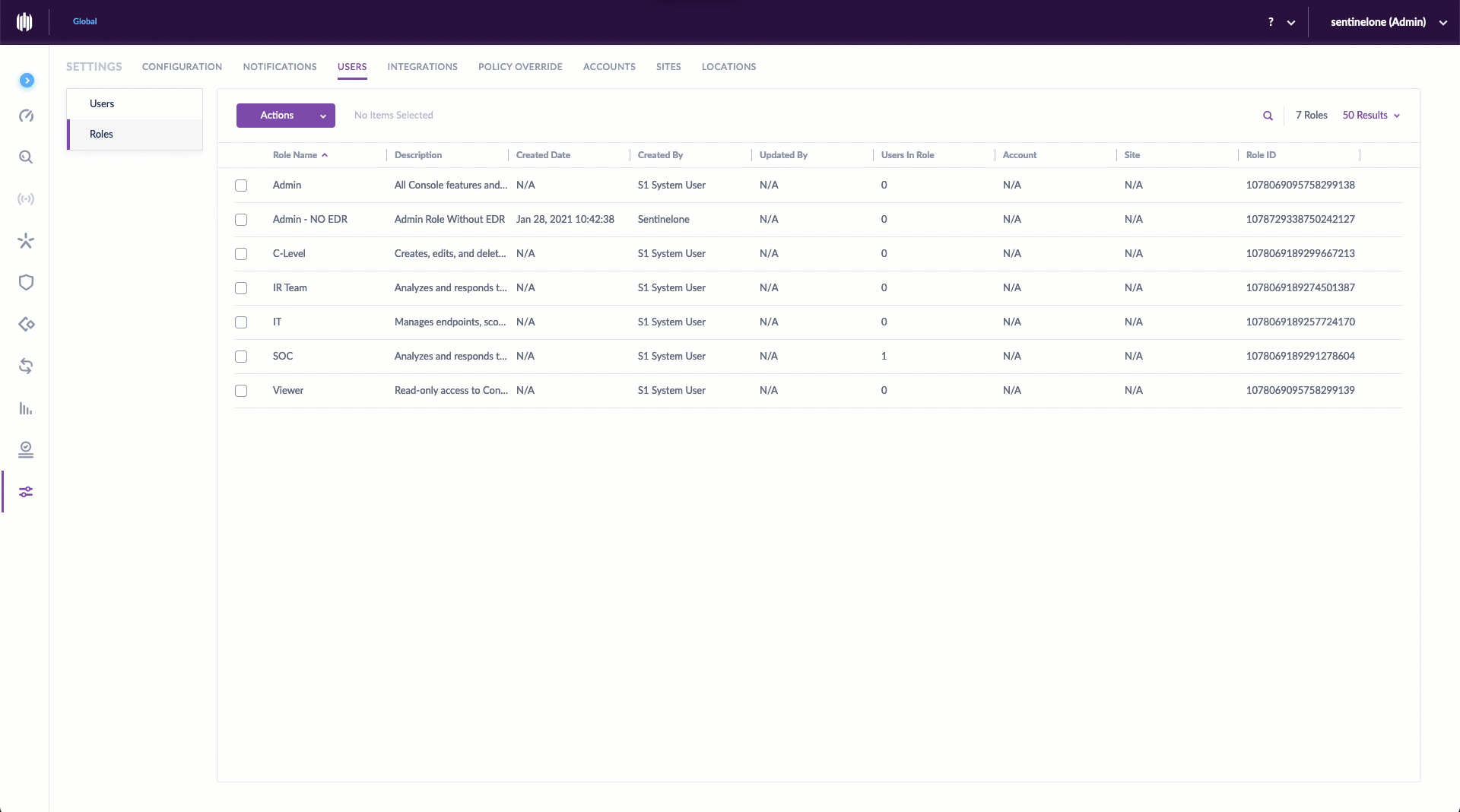
Editing a Custom Role
Perhaps you had an oversight or need to make a change. No problem. Modifying a role is equally straightforward. Click on a role name from the list, make the change, and save.
Duplicating a Custom Role
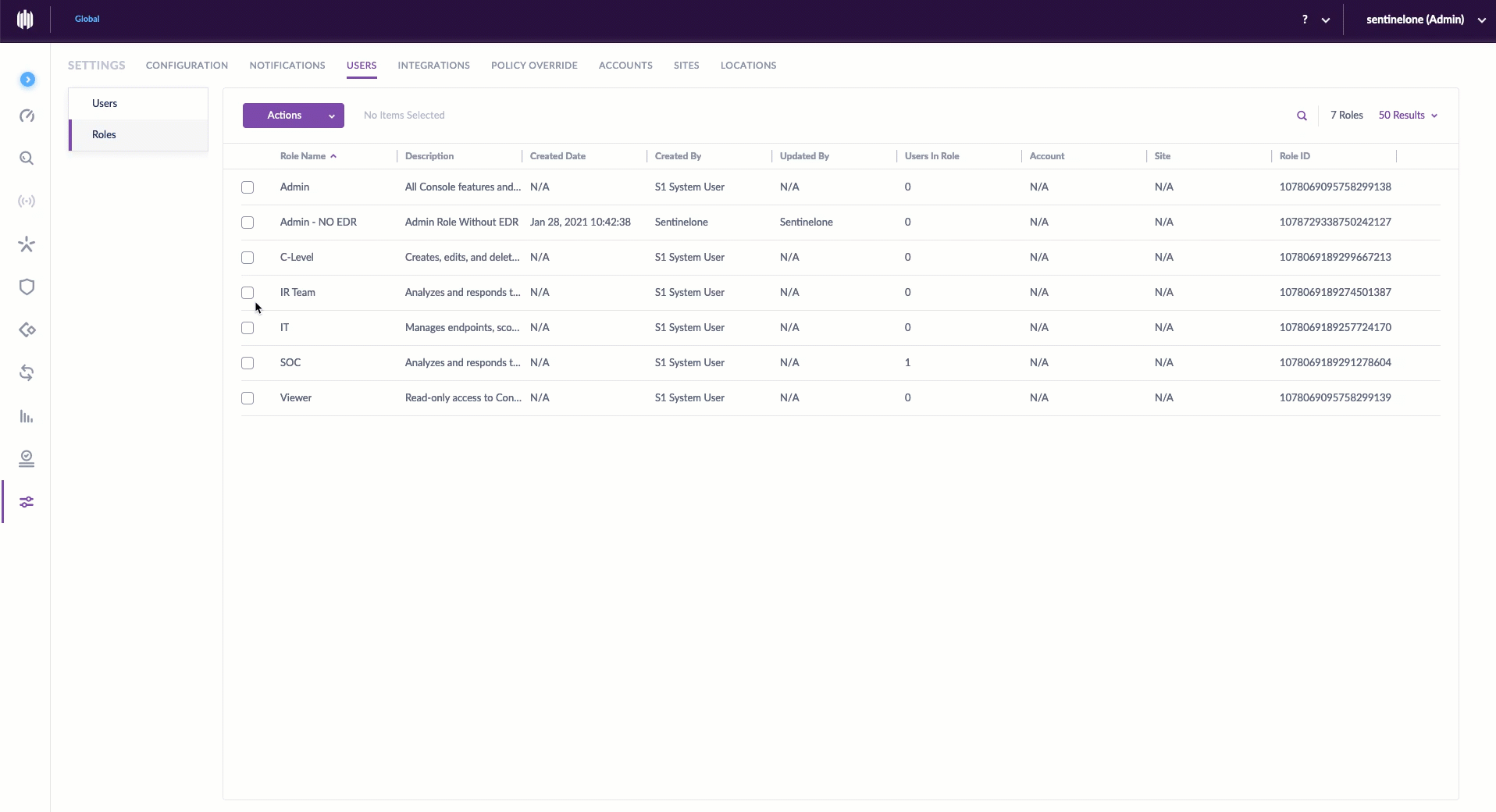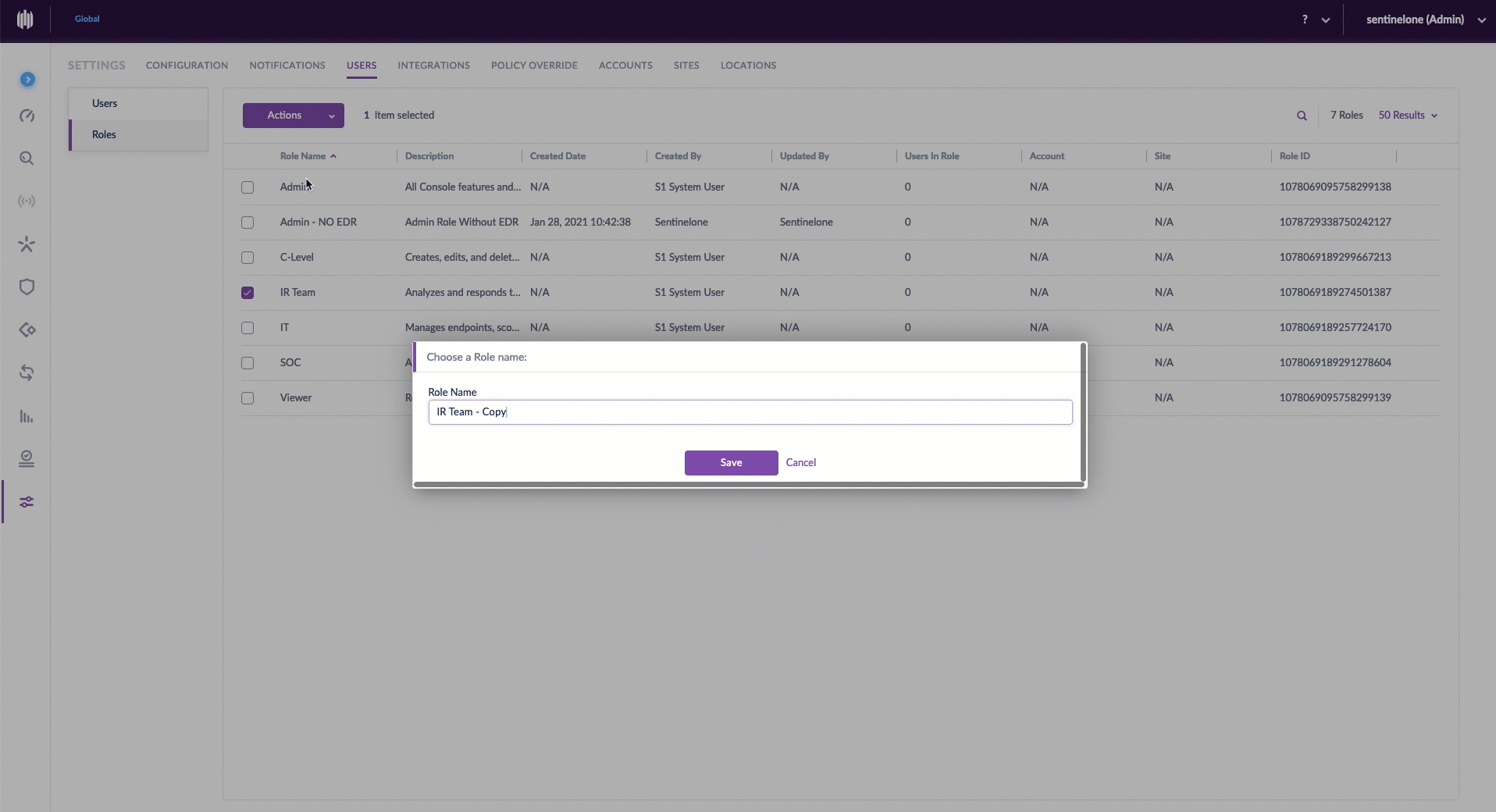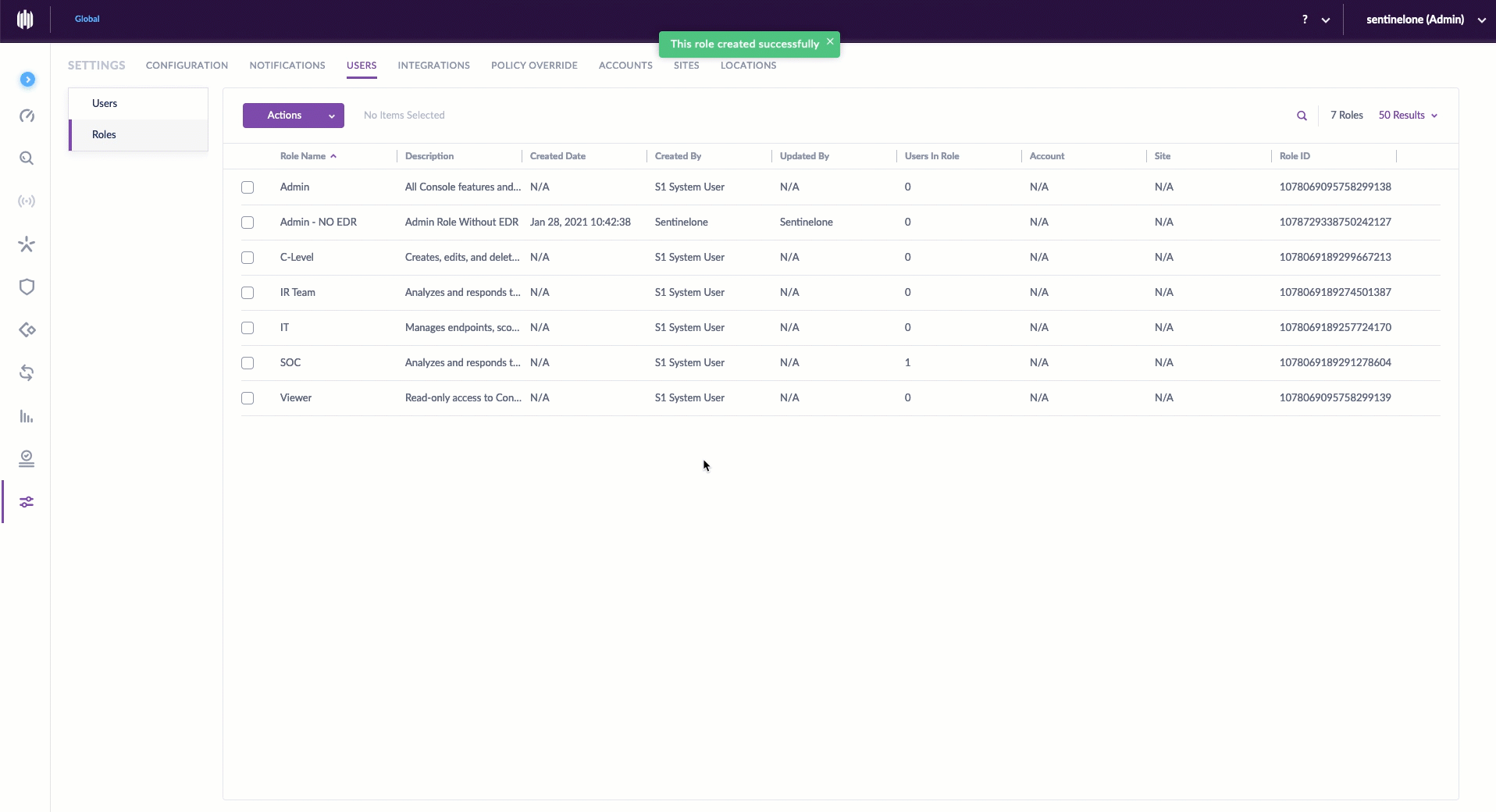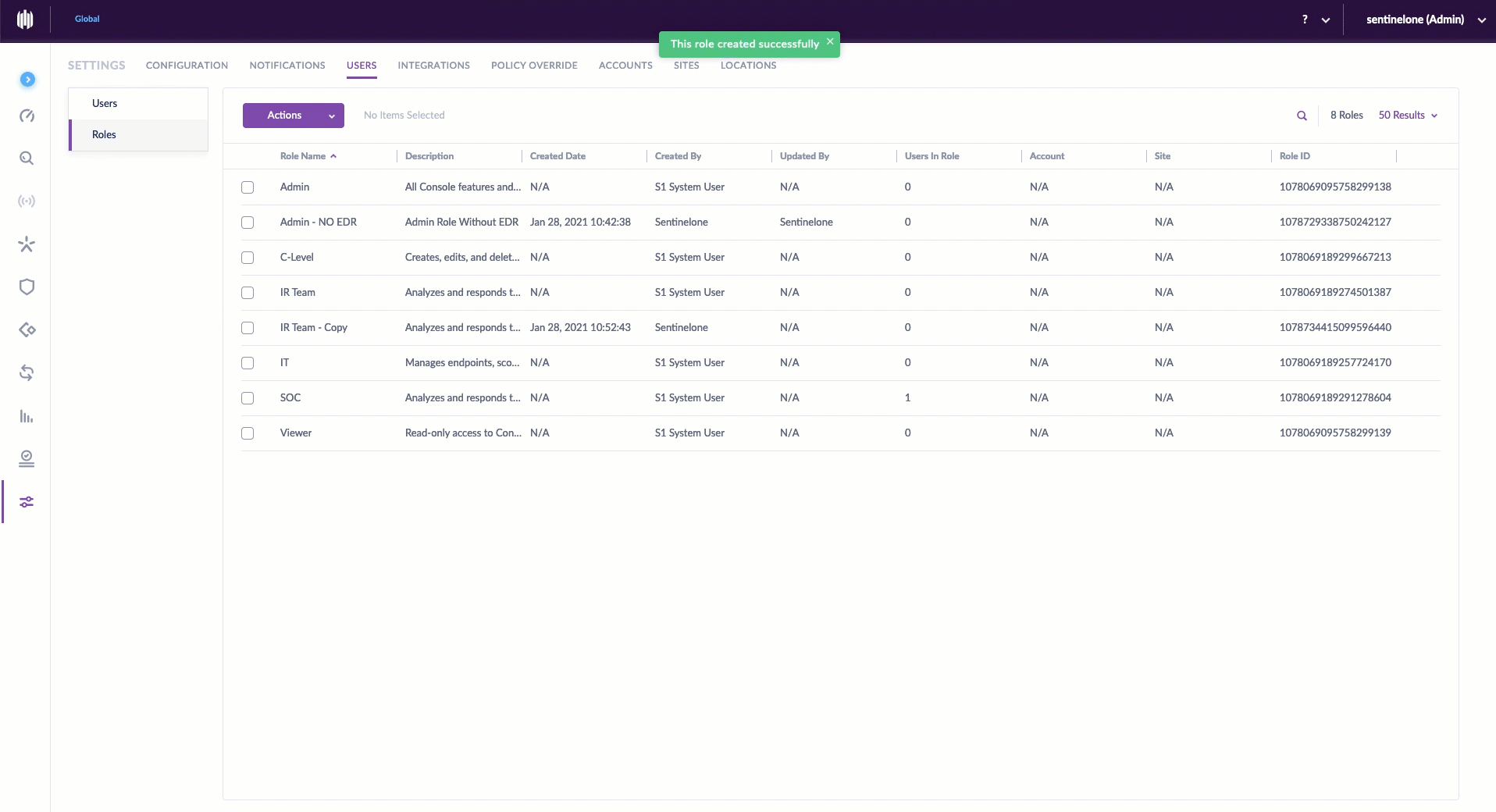
As an extra level of convenience when creating new roles, customers can copy a similar role and make the few permissions changes necessary. This helps admins move forward quickly.
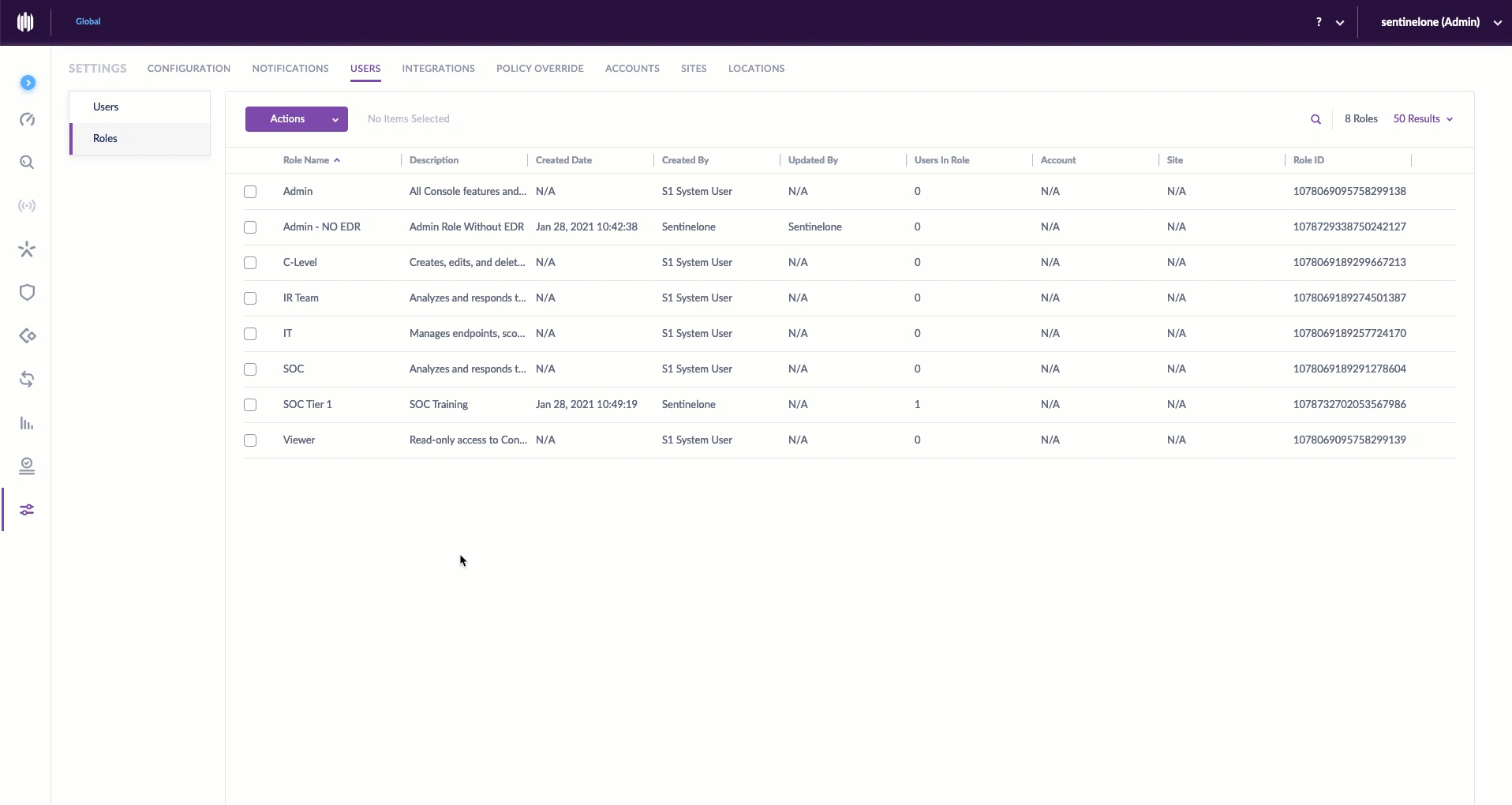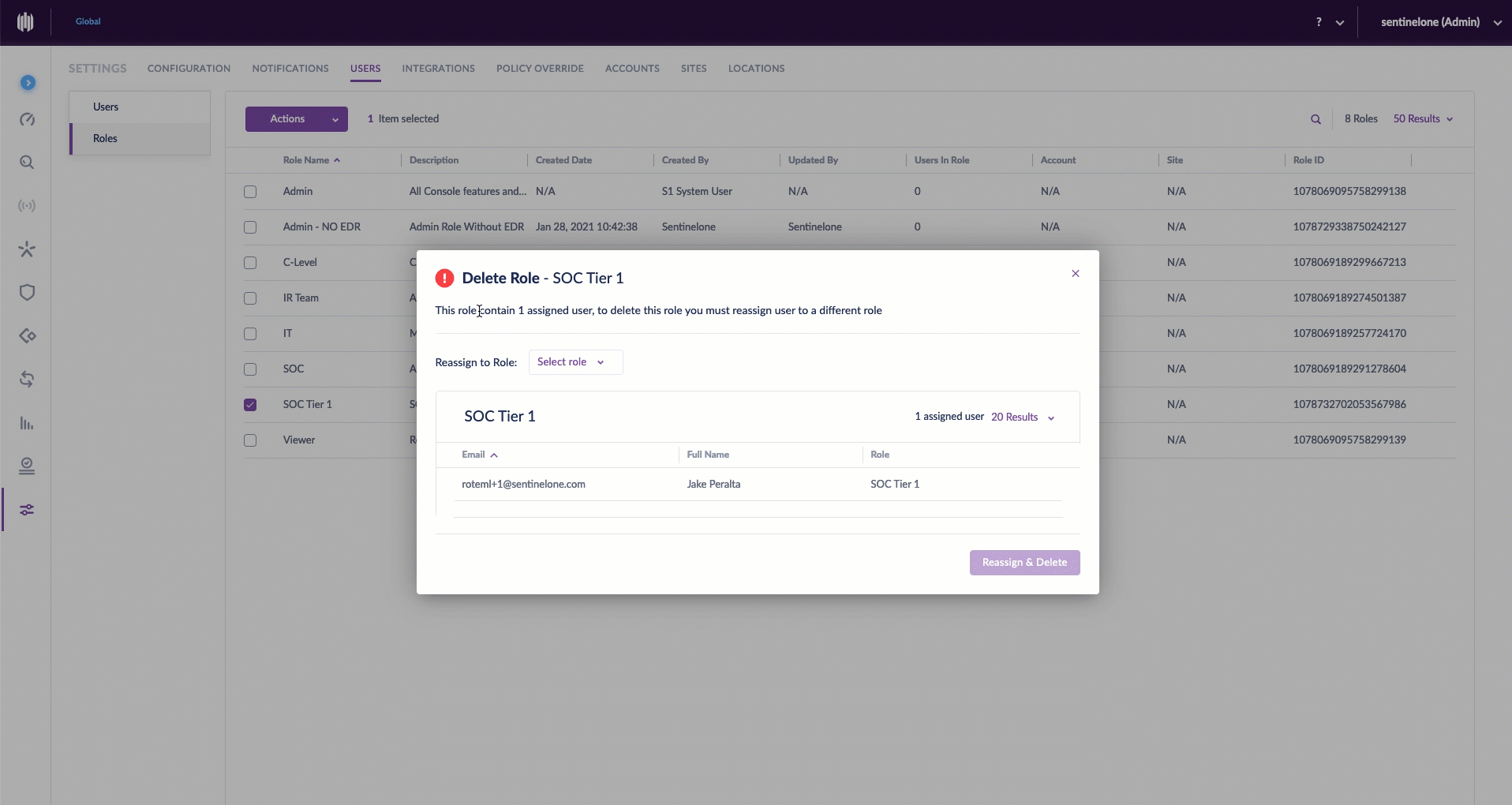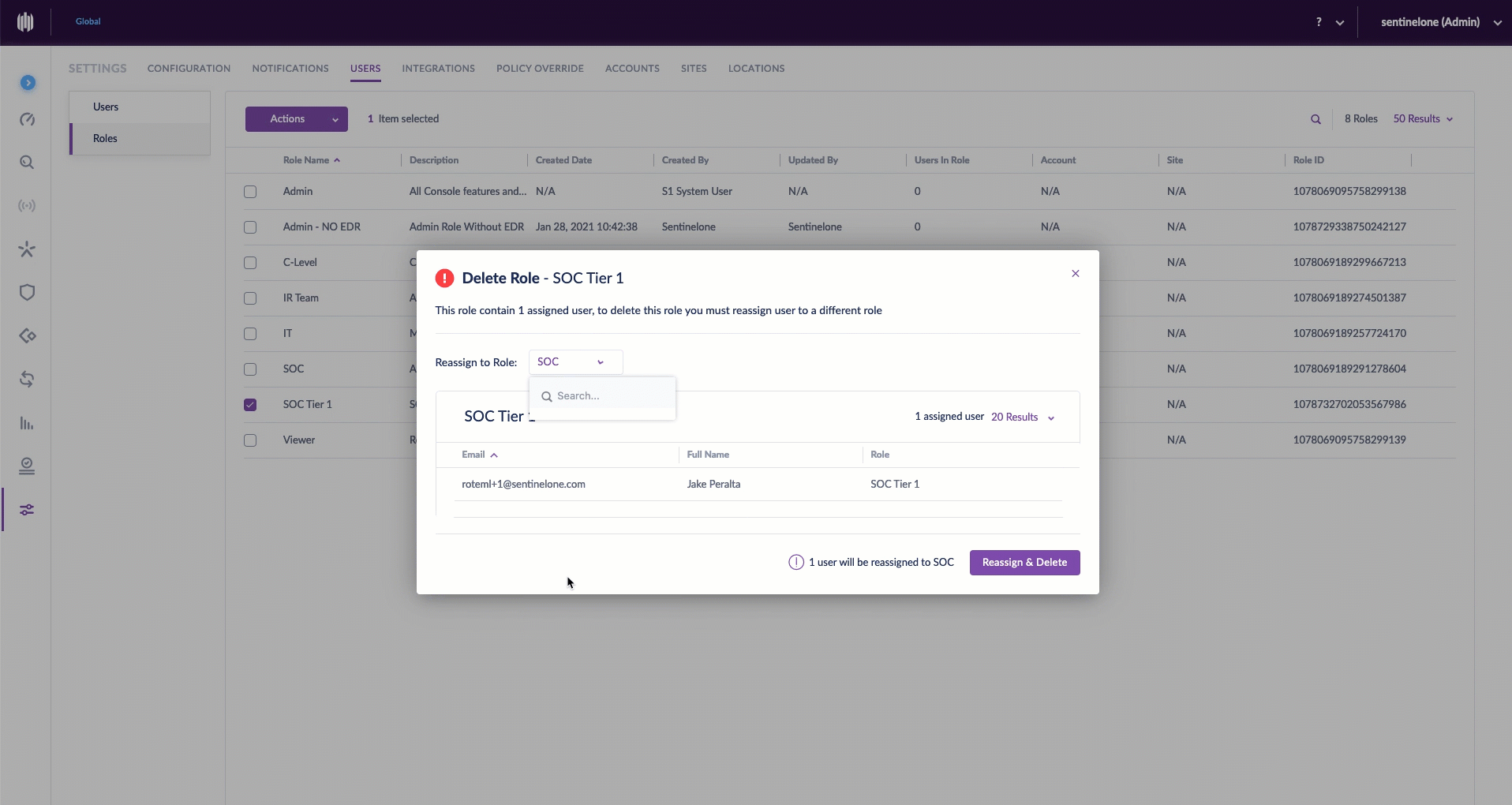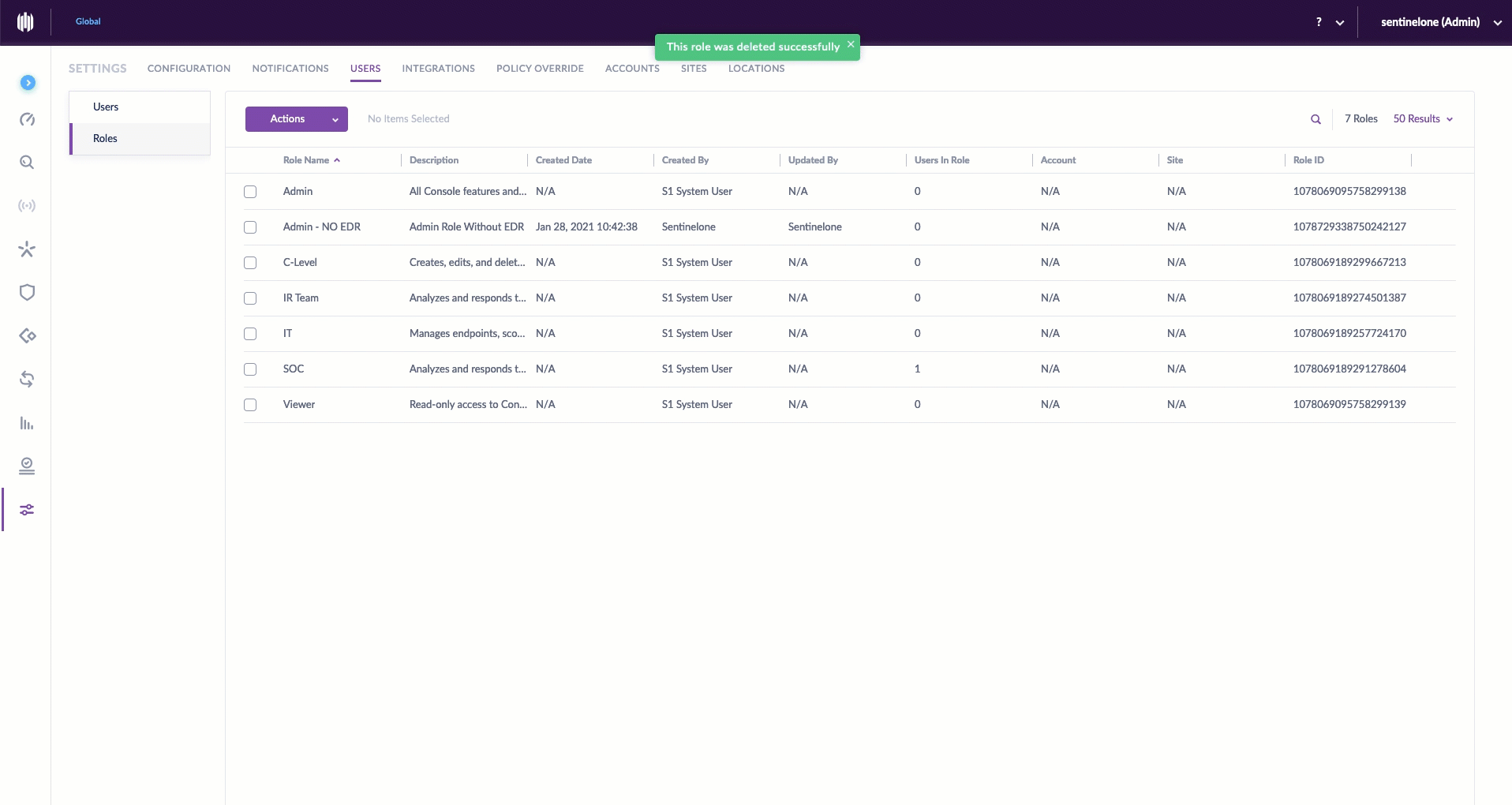
Delete a Custom Role, Reassign Users
Sometimes, a custom role outlives its usefulness. Of course, when deleting a custom role, consideration should be given to the users who have been previously assigned to this role. SentinelOne understands this, so we made it easy for admins to delete a role and reassign users in the same breath.
To delete a role, simply select the role name checkbox, go to Actions > Delete Role. Then select the role to which you wish to reassociate affected users, and click Reassign & Delete. And, for the astute reader: the six aforementioned predefined roles can never be edited or deleted.
Summary
SentinelOne remains fully committed to customer success. Part of that commitment is listening and responding to customer feedback, which we are always grooming within our product innovation backlog. We hope that this fully customizable role capability helps simplify your cybersecurity journey.
To learn more about how SentinelOne has extended autonomous cybersecurity beyond the user endpoint to cloud workloads and IoT devices, feel free to visit our Singularity Cloud and Singularity Ranger pages.


