Due to the current Coronavirus pandemic and the large-scale shift to teleworking, we’ve recently posted on how to prepare yourself and your staff for ‘work from home’ (WFH) and warned of common mistakes that can lead to compromise of endpoints and company networks. In this post, we take a look at some popular teleworking software and highlight some of the privacy and security concerns to be aware of.

Securing Slack and MS Teams Against Malicious Actors
There are likely more than 60 million daily users of workplace chat apps like Slack and Microsoft Teams, and both platforms have seen increased growth as the Coronavirus pandemic has forced most businesses to move to remote work wherever possible. Such apps are vital in today’s digital, distributed workplace, but CISOs and security teams need to be aware of the security implications of using such software.
It is relatively trivial for an attacker on a compromised machine to exfiltrate all of a user’s entire Slack workspaces, chat messages, files and history. Worse, attackers can gain current access to the workspace by stealing the stored session cookies on the user’s machine. As researchers noted earlier this month, all an attacker has to do on a Mac is copy off the entire directory at ~/Library/Application Support/Slack (or alternatively, ~/Library/Containers/com.tinyspeck.slackmacgap/Data/Library/Application Support/Slack if using the sandboxed, App Store version). On Windows, the same data can be found at %AppData%RoamingSlack.
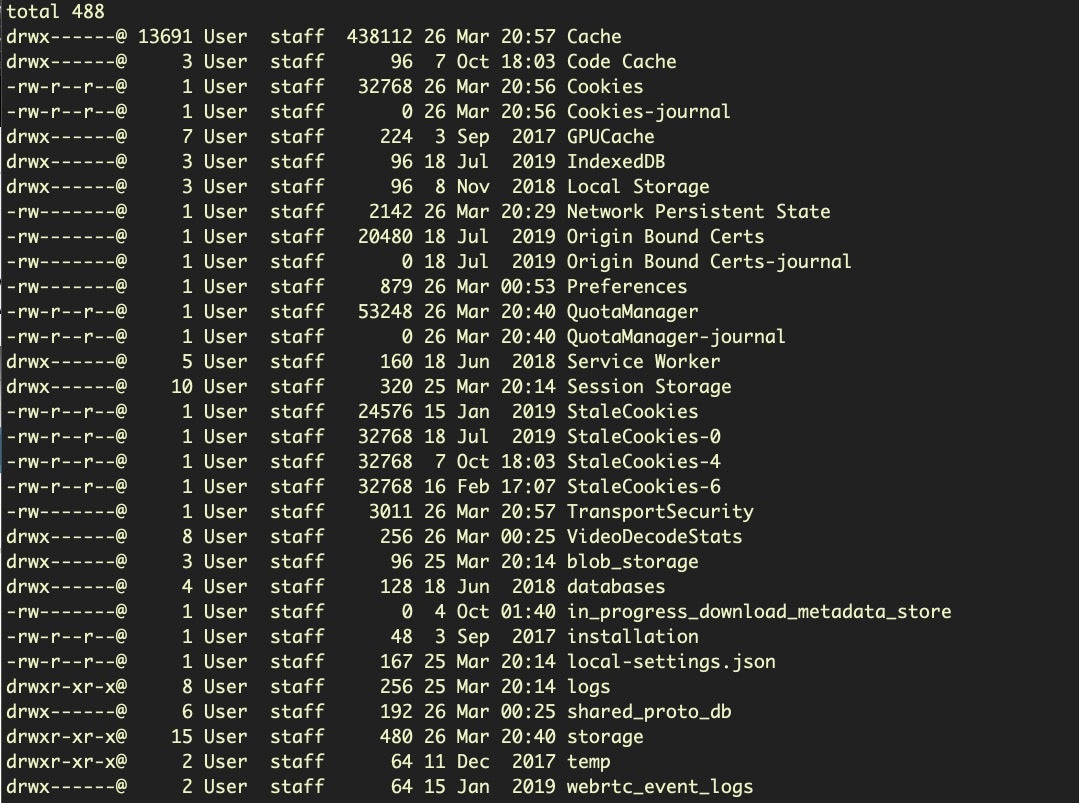
Having acquired the data, the attacker can then start up a virtual machine instance, install the Slack app, and copy the stolen data to the same location on the VM from where it came (the user name need not be the same). Launching Slack will then log the attacker into the user’s workspaces and give them full, live access. Although this activity will be recorded in the workspace Access Logs on the server-side, it will not be obvious to the user unless the attacker actively tries to impersonate the user in the workspace.
Because the Slack data on the user’s machine is exposed to any unsandboxed process running as the logged in user, it’s possible for a malicious app to exfiltrate this data without the victim’s awareness.
While Slack’s developers have acknowledged the issue, their official response is that this is not an urgent issue for them at this time, so security teams are going to need to take their own steps to ensure that the organization’s workspace is secure. These include, in the first instance, ensuring all company devices have a good EDR solution to prevent malware from infecting the system to start with. Secondly, educate users and IT admins about the need to regularly sign out of other devices. This may or may not require a password depending on your workspace settings.
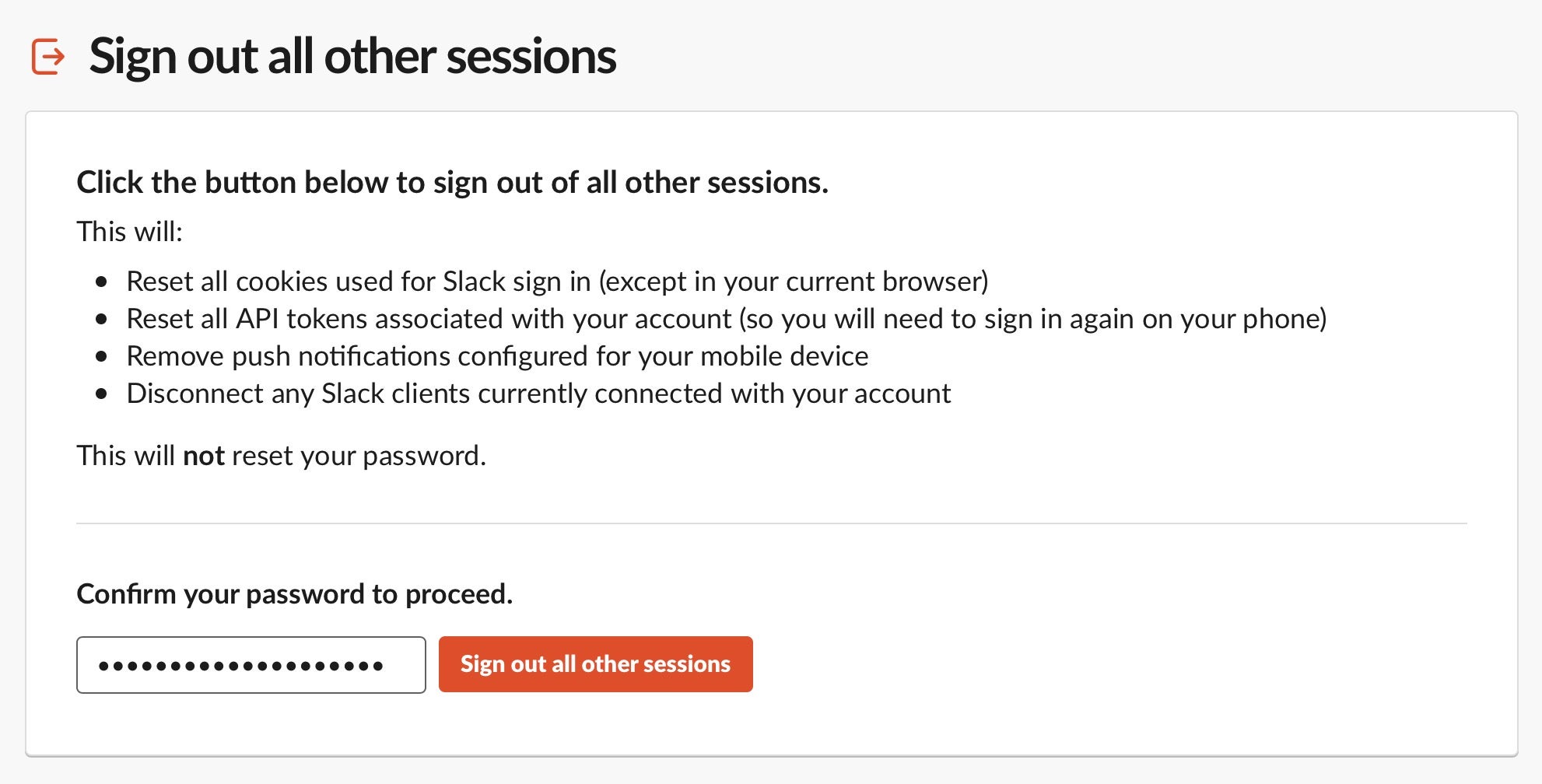
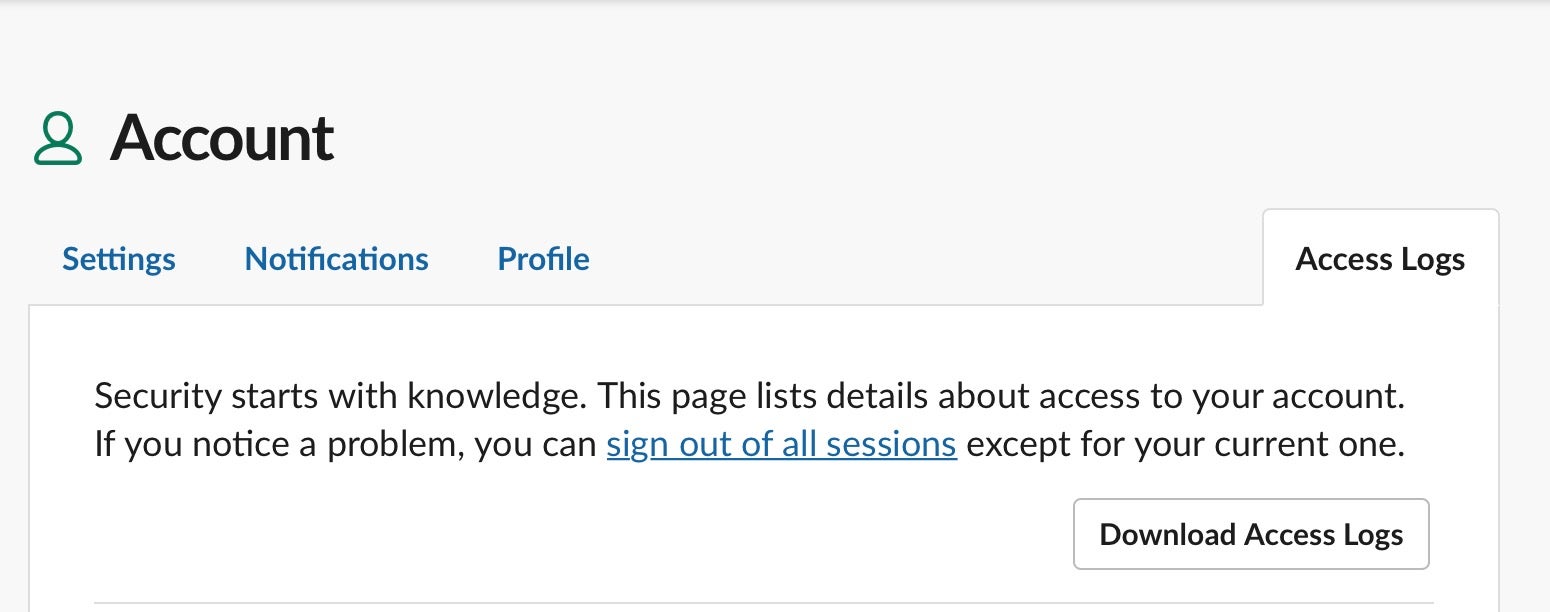
Thirdly, as with all password protected accounts, remind users to change passwords on a regular basis and to set up 2FA for Slack. With workspace platforms like Slack, changing passwords can be easily overlooked. Workspace owners and users can review access logs to check whether any unknown devices have been logged into the account.
The Microsoft Teams’ app, Slack’s major competitor, has also faced security issues in the last 9 or 10 months. Last June, the Teams’ Windows Desktop app was found to be vulnerable to a bug in a dependency, the Squirrel framework, that could allow arbitrary code execution, malicious downloads and privilege escalation. In September of last year, researchers discovered the Teams app was vulnerable to Cross-Site Scripting (XSS) and a Client Side Template Injection. These vulnerabilities have been addressed in recent Teams.app updates, so it is vital that IT admins ensure users are updating these applications in a timely manner.
Regardless of what platform you use, make sure for critical meetings you have a backup plan in place. MS Teams had a 3hr outage back in February when Microsoft incredibly forgot to renew a critical security certificate. Our online digital world may be more susceptible to disruption now more than ever before as people practice social distancing and bandwidth comes under increasing pressure. Regular communication channels from email to telephone may need to be pressed into service in the event of service unavailability. Those, particularly email, have their own security challenges, of course, including phishing and SIM swapping.
Security & Privacy While Using Video Conferencing Software
Zoom and Skype are great ways to hold meetings from small teams to tens of thousands. But these apps also have security and privacy implications.
First, ensure your own physical space is suitable for a meeting. Social media has this last week or two been chock with mildly embarrassing images of people engaged in work from home who didn’t consider their surroundings. From the spouse walking around in his underwear to one employee who inadvertently revealed more than colleagues wanted to see after taking her smartphone to the bathroom while on a conference call, it’s always worth remembering your environment.
A few quick tips for personal comfort: look behind you and check what can be seen by the camera. Make sure family and others who share your living space are aware of when you’re on a work call. Whether it’s barking dogs or a family spat, unwanted background noise can be both disturbing and embarrassing for other meeting participants. In addition, take care when screen sharing. Ensure there are no applications, images or videos visible that might be in the Not Safe For Work (NSFW) category or that might expose personal or confidential business data. Check which tabs are visible in the top bar of your browser and whether you’re accidentally about to reveal sites you’ve recently been visiting.
Second, be aware of the privacy policies and features of the software you’re using. Zoom has some interesting features, like attention tracking and some “should know” policies on data collection and sharing.
As for security, there are a number of issues to be aware of with video conferencing software, and particularly if you’re coming to something like Zoom as a newbie. It’s worth checking out Zoom’s useful guide here for basic tips on how to prevent things like “Zoom pirates” and “Zoom bombing”, where unwanted participants join a call through open or guessed meeting Ids and take over the meeting by sharing images from their screen. As the host, you can manage participants and make sure you don’t lose control of the meeting by properly configuring your account settings. Turning on 2FA and requiring authorized email addresses are basic precautions for any in-house meeting.
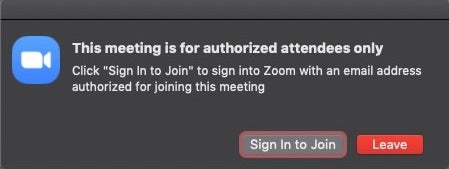
Aside from locking the meeting down to authorized participants, other options are available that can allow you to restrict screen sharing without permission, remove unwanted or disruptive participants from a Zoom meeting, and mute participants or turn off their video. Other teleconferencing software should have similar settings, so check the documentation if necessary and make sure you know how to control unexpected events.
It’s also important to keep the meeting secure from those outside the call. Account managers should ensure that end-to-end encryption is enabled to prevent snooping of traffic, particularly if remote workers are connecting to meetings from outside of the company’s secure VPN network.
Remember that video meetings can be recorded by any participant, and that raises issues of confidentiality and leakage. Recordings are stored locally on the user’s device. With Zoom, for example, they can be found in ~/Documents/Zoom on a Mac, and Users/UsersDocumentsZoom on Windows. If that device is compromised, those recordings are vulnerable to being leaked and leveraged. Extorting and exposing victims is a technique that’s increasingly popular with some attackers, like ransomware developers Maze and DoppelPaymer, for instance.
Earlier this year, researchers found that Zoom had a vulnerability which made it possible to figure out which random numbers were valid Zoom calls. The researchers were then able to use those numbers to eavesdrop on calls. This vulnerability was discovered shortly after Zoom and a number of other video conferencing apps were found to contain a software vulnerability that could lead to remote command execution (RCE) on any macOS device, even if the Zoom app had been uninstalled. In this case, Apple took quick action and updated their own internal security software to remove the vulnerability. Both vulnerabilities are patched in the latest versions of Zoom.
As with workplace chat apps, so with teleconferencing software: ensure that your users are patching as soon as updates are available, and that endpoints are protected by a security platform that can protect against malware, malicious devices and network compromise.
Conclusion
It’s a truism that all software contains bugs. Most are trivial and never noticed by users, some are zero days we never learn of until after they’ve been either patched or exploited in the wild, while others are critical and patched in a timely fashion. There’s another class of issues that fall in between the cracks: developers are informed, but the issue remains unpatched, perhaps because the vendor does not agree as to the severity of the security risk, or doesn’t think it’s their bug to fix, or cannot find a technical solution. On top of that, some security and privacy issues arise not from flaws in programs, but in the way we use those programs, such as not being aware of our environment when teleconferencing. The best way to protect ourselves from such a wide range of issues is to share knowledge, follow best practices and implement security technology where we can to mitigate issues on our behalf.


