The Good
Europol has been busy this week rounding up 26 fraudsters belonging to two separate SIM swapping gangs in Spain and Romania in ‘Operation Quinientos Dusim’ and ‘Operation Smart Cash’. SIM swapping involves socially engineering the staff of major phone carriers using personal data obtained in breaches, through phishing and by using OSINT techniques. SIM swappers impersonate their intended victim and convince the phone carrier to transfer the target’s cell services to a SIM card belonging to the attackers. Famously, Twitter CEO Jack Dorsey was caught in a SIM swap attack last year. Typically, fraudsters use the stolen services to gain access to the victim’s online banking and to bypass 2FA and one-time password controls on online accounts. The gangs caught in this week’s report are believed to have snatched funds from over 100 victims’ bank accounts before being nabbed by Europol with the help of the Spanish and Romanian police.

If you’re an Adobe user, and let’s face it most of us are, then you’ll be pleased to hear that Adobe fixed 41 security flaws this week. In a massive security update across both Windows and macOS versions, Adobe plugged vulnerabilities in six major products, including ubiquitous favorites Adobe Acrobat, Adobe Reader and Photoshop. If you haven’t already, update those apps before the hackers reverse and exploit the multiple arbitrary code execution vulnerabilities just fixed.
The Bad
We’re all only too aware of what the big, bad news is this week and likely to be for many weeks ahead: the COVID-19/Coronavirus outbreak that’s wreaking havoc on people’s health, livelihoods and lifestyles across the globe. SentinelOne, like a number of other vendors, is offering free platform access to help secure enterprises and remote workers during this unprecedented crisis. Meanwhile, the bad guys are, of course, taking every opportunity they can to milk the FUD for all it’s worth with malware campaigns, phishing kits and good old fashioned snake oil frauds becoming almost too numerous to count.
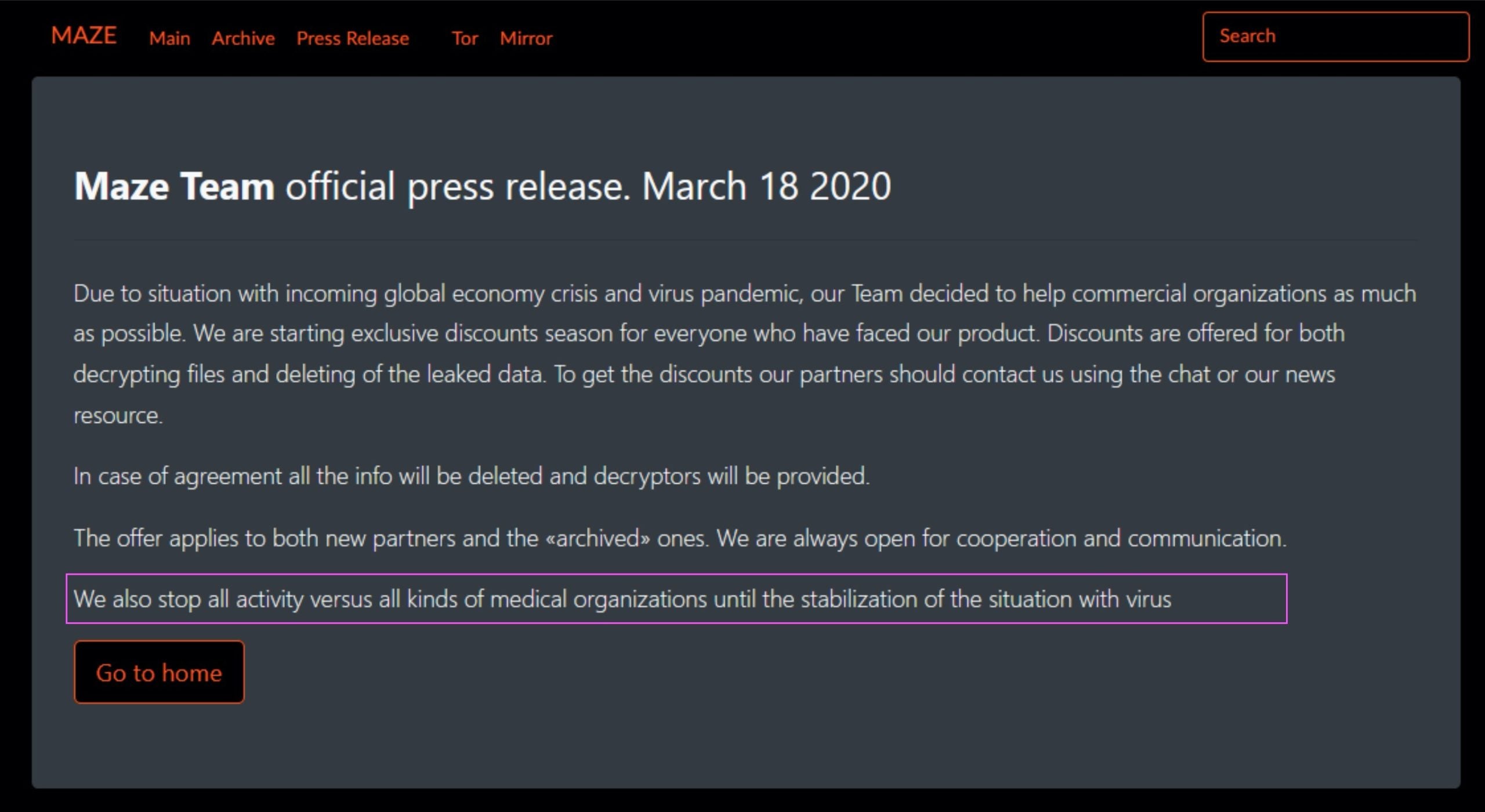
In a sign of the upside-down times that we’re living in, our bad news this week comes with an oddly welcome twist. For the time being anyway, some ransomware operators, namely DoppelPaymer and Maze, have claimed they will avoid deliberately targeting medical services and even offer free decryptors to those that do get hit. Of course, criminals like anyone else may need access to healthcare services before we see the back of the COVID-19 crisis, so we don’t think they’ll be winning any “service to the community” awards just yet.
On a different note, in other bad news this week, it seems TrickBot developers have been busy retooling in order to target US and Hong Kong-based telecoms organizations through a brute-force RDP attack leveraging a malicious DLL file called rdpScanDll. Researchers say very specific IPs have been targeted and that the purpose appears to be espionage. We already know that TrickBot is being leveraged by some APTs, and this looks like it could well be more of the same. More intel on this as soon as we have it.
The Ugly
This week a security researcher found an unsecured database containing over 5 billion records that appear to have been stockpiled since at least 2012. The database appears to have been collected from other previously known sources and compiled into a well-structured format with hash types, leak data, email, password and other information.
Such a massive and organized collection would undoubtedly be a prize asset for fraudsters to get their hands on. Upon discovery, the researcher informed the company he believed to be the owner, and although he received no response, the database was removed within the hour.
It has since been confirmed that the company contacted by the researcher had not suffered a breach and nor did the database contain data from its own customers.
As bad actors routinely probe for such insecure databases in the same way as the researchers who found this one, it’s anyone’s guess at this point whether the treasure trove is already in the hands of spammers, fraudsters and criminals intent on phishing attacks.


