SentinelOne is delighted to release its third, comprehensive Mac-focused ebook for enterprise security teams, the Complete Guide to Understanding Apple Mac Security for Enterprise.
Following on from How To Reverse macOS malware and A Guide to macOS Threat Hunting & Incident Response, our latest macOS ebook is an all encompassing guide to the native security technologies built-in to macOS: how they work, where they fail, what they protect against, and what they don’t.

Who is the macOS Security Ebook For?
The SentinelOne Complete Guide to Understanding Apple Mac Security for Enterprise is an essential reference for anyone needing to understand the strengths and weaknesses of the security controls built into Apple Macs and the macOS platform.
The guide covers macOS right up to and including the latest release of macOS 12 Monterey and answers many common questions asked by system administrators and security teams managing Mac devices, including:
- How secure are Macs by design?
- Are third-party AV security controls required on macOS?
- What kind of security software works best on macOS?
- Which approaches to macOS security are the most effective?
- What sort of threats do businesses with macOS fleets face in 2021?
What Will You Learn from the macOS Security Ebook?
In the guide, you’ll find detailed sections on areas such as:
- Architecture & Codesigning: Does the new M1 architecture provide increased security over Intel machines? Is it still possible to run unsigned malicious code on macOS Monterey on both of these architectures?
- Gatekeeper: How easy is it for malware or malicious insiders to circumvent Gatekeeper’s controls? Are these bypasses used by in-the-wild malware?
- Notarization & OCSP: What do these technologies achieve, and what are their limitations? How does malware circumvent these checks?
- XProtect and MRT: How do these technologies work on modern versions of macOS, how can you test if they are protecting against specific kinds of malware, and how effective are they?
- TCC Privacy controls: How well does TCC protect sensitive data on a Mac, and in what situations does TCC fail to work?
What Kind of Malware Threats Target macOS?
Throughout, the guide discusses the Mac’s built-in security technologies with references to real, in-the-wild malware such as XCSSET, Shlayer, Bundlore, Adload and others, describing exactly how security breaches can occur on systems that remain unprotected by additional security controls.
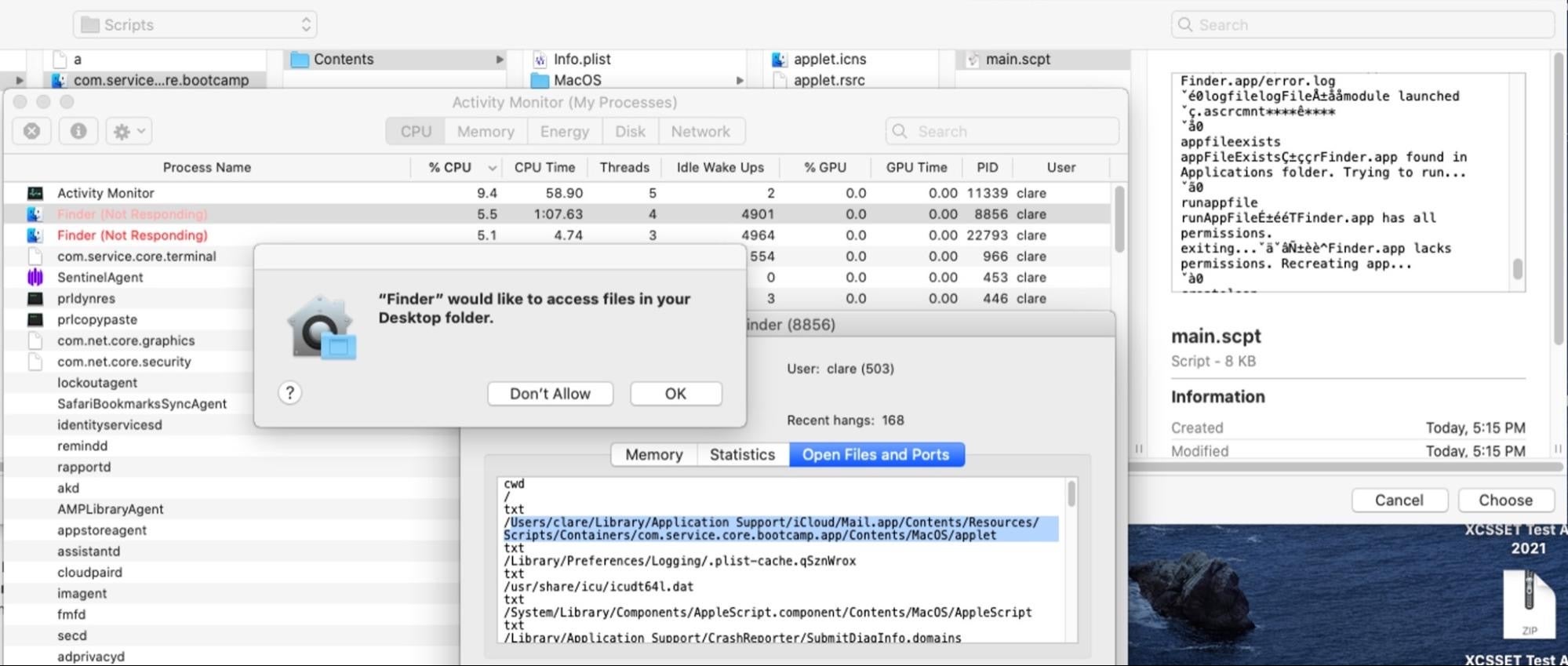
Administrators and security teams charged with protecting macOS endpoints will learn about vulnerabilities in Apple’s platform that can be and are used by threat actors to compromise Mac devices, circumvent code signing requirements, beat Gatekeeper, bypass OCSP and Notarization, and defeat TCC privacy protections.
Learn How to Test Mac AV Software
SentinelOne’s Complete Guide to Understanding Apple Mac Security for Enterprise also includes sections on how to test security products against known malware samples, and what to look out for when evaluating third-party security products for Mac. Learn why, for example, a revoked code signature does not mean your Macs are protected from a particular malware family.
Only last month, we saw how a new targeted threat, macOS.Macma, was able to beat Apple’s on-device security and yet was easily detected by third-party behavioral engines like SentinelOne.
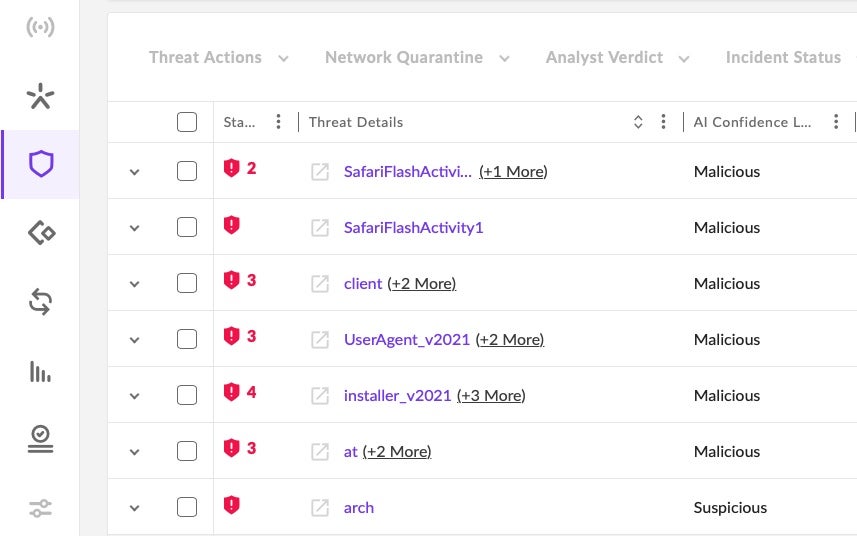
This guide also explains, with examples, how Mac admins can test for themselves whether the Mac’s own AV tools, XProtect and MRT (Malware Removal Tool), have been updated to protect against a particular threat or not. Learn how to test which malware you are protected from, and which you are not.
Why You Should Read the macOS Security Ebook
Apple Mac computers are increasingly common in today’s enterprise. Despite its shared Unix heritage with Linux, Apple’s macOS is idiosyncratic, as are the attack vectors that it is susceptible to, and the security implications of running a fleet of Macs in the enterprise is not widely understood. This is true even more so now that Apple has moved away from Intel architecture to its own implementation of ARM, ‘Apple silicon’.
Throughout this ebook, we illustrate areas where Macs face security risks by referencing real, in-the-wild malware that we have seen emerge or adapt in the last 12 to 18 months,
It’s vital that enterprise security teams managing a fleet of Macs are up-to-date with just how the latest threats can and do target the macOS platform.
This guide will help security teams bridge the gap and understand how best to protect Macs in the enterprise.


