Threat actors are increasingly targeting critical infrastructure with ransomware, according to independent reports recently. In February, a natural gas compression facility was attacked by ransomware, forcing it to shut operations for two days. Healthcare companies and research labs have been aggressively targeted since the onset of the COVID-19 pandemic. And now, a new academic project from Temple University in Philadelphia tracking ransomware attacks on critical infrastructure over the last seven years shows that 2019 and 2020 saw a sharp increase, accounting for more than half of all reported incidents over the entire period. In this post, we look at the latest data and explore how such attacks can be prevented.

What is Critical Infrastructure?
According to CISA (the Cybersecurity & Infrastructure Security Agency), “critical infrastructure” is the “assets, systems, and networks” that are vital to the functioning of the economy, public health and national security. Attacks that affect critical infrastructure risk having “debilitating effects” on the country’s ability to function.
CISA says critical infrastructure is spread over 16 sectors, namely: Chemical, Commercial Facilities, Communications, Critical Manufacturing, Defense, Education, Emergency Services, Energy, Financial Services, Food and Agriculture, Government Facilities, Healthcare, Information Technology, Nuclear, Transportation, and Water systems.
That’s a considerable attack surface that is made all the more vulnerable by the fact that organizations in many of those sectors are public-funded and often lack both the budget and the expertise of large, well-resourced private enterprises. The spate of ransomware attacks since 2018 on hospitals, schools and cities like Atlanta, Greenville, Baltimore and Riviera Beach City Council being some of the more high-profile cases in point.
How Frequent Are Ransomware Attacks on Critical Infrastructure?
Ransomware attacks on critical infrastructure have risen dramatically in the last two years, and all the indications are that this is a trend that will continue as ransomware tools and RaaS offerings become increasingly available and lower the bar to entry for cyber criminals without technical skills of their own.
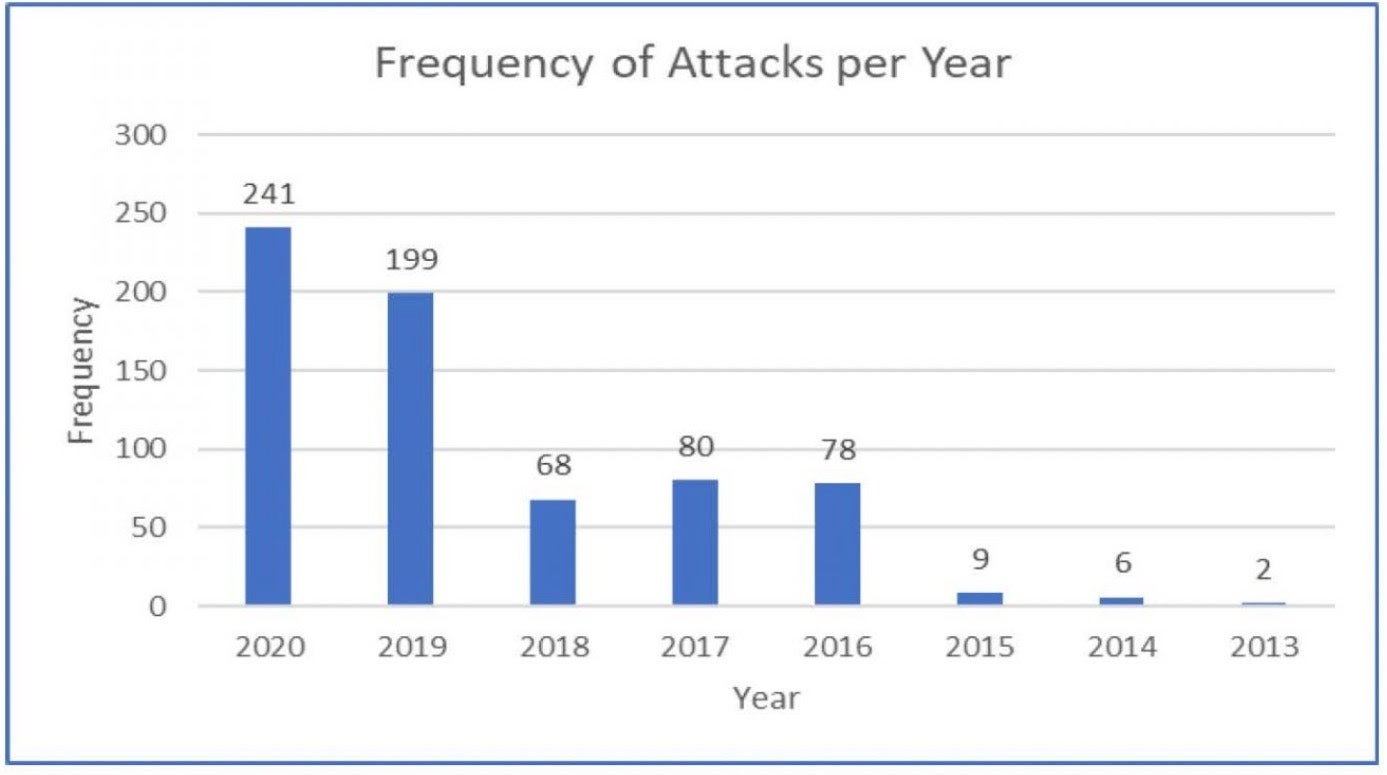
Over the last 7 years, the public data collated by Temple University shows that there have been almost 700 ransomware attacks on critical infrastructure; that’s an average of just under 100 per year, but in fact over half of those have occurred since 2019. 440 attacks in less than two years (we’ve still around four months more of data to collect for 2020) presently equates to around 5 critical infrastructure ransomware attacks every week.
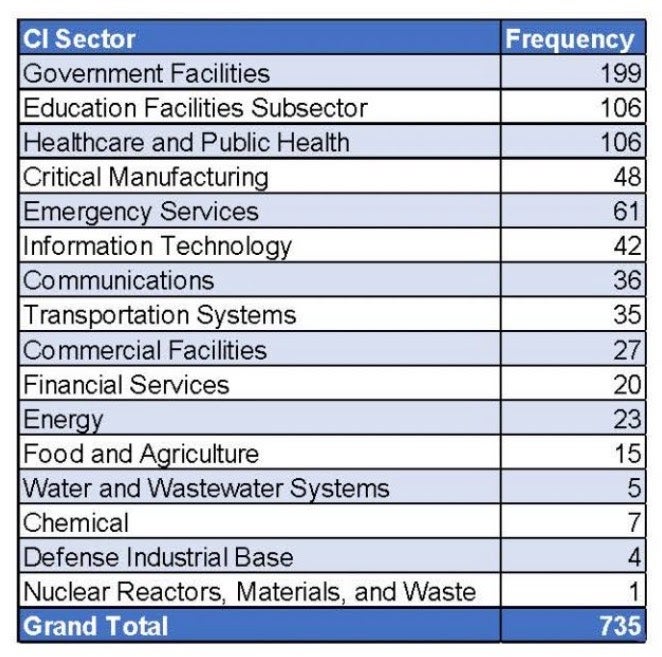
The attacks cut across all CI sectors, from food and agriculture to manufacturing, public health and even education. The defense sector has also been targeted, and so too, worryingly in one case, has the nuclear industry.
By far most ransomware attacks on critical infrastructure in recent years have targeted government-run facilities, with 199 reporting ransomware attacks. Education is not far behind that with 106 reports, followed by 61 reported ransomware incidents targeting Emergency Services.
Who Is Responsible for Attacks on Critical Infrastructure?
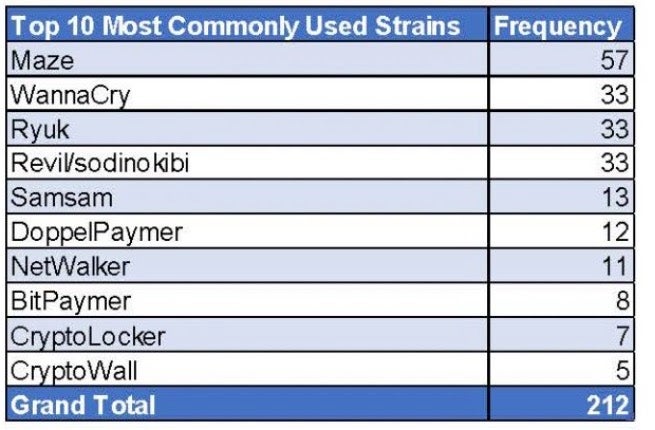
Attacks against critical infrastructure targets have become increasingly frequent with the prevalence of off-the-shelf ransomware tools like Netwalker sold on the darknet. It’s no surprise to see Maze top of the list of ransomware used in such attacks, as Maze has been on something of a rampage over the last 12 months or so, bringing with it the threat not only of encrypting data but also exfiltrating it to use as leverage against victims unwilling to pay.
It’s a tactic that’s been copied by REvil, Snatch, Netwalker, DoppelPaymer, Nemty and other ransomware operators. The general strategy is: don’t rely on your backups or technical solutions to get you out of trouble, because if you do we’ll just sell or publicise your IP and confidential data anyway.
Aside from Maze, which reportedly was used in at least 57 incidents against critical infrastructure, Wannacry’s “15 minutes of fame” led to it accounting for some 33 attacks on businesses in the 16 essential sectors, the same number as each of the more recent and still ubiquitous Ryuk and Revil/Sodinokibi ransomware strains.
Other ransomware strains reportedly involved in critical infrastructure attacks include DoppelPaymer (12), Netwalker (11), BitPaymer (8), CryptoLocker (7) and CryptoWall (5).
How Much Does A Critical Infrastructure Ransomware Attack Cost?
Unlike APTs and nation-state actors who may look for inroads into critical infrastructure for espionage or sabotage, cyber criminals using ransomware are typically interested in one thing: the financial pay off. To that end, the amount of ransom demanded in 13 recorded cases exceeded 5 million dollars, with another 13 recorded as between $1m and $5m. Some 31 ransomware incidents demanded $1m or less, while 66 sought $50,000 or less.
As noted above, the prevalence of ransomware has increased proportionally to its availability to technically low-level, likely “first-time” cyber criminals. This is evidenced by statistics showing that 54 ransomware attacks against critical infrastructure targets demanded $1,000 or less. Possibly, these actors had taken a “shotgun” or “scattergun” approach to infect random targets and were not fully aware of the nature of the organization they had compromised. Also, some RaaS tools set a fairly low ransom limit on first-time buyers and newbies “trying out” the software to entice these actors to pay for “premium services” after getting a taste of success.
How Can We Protect Critical Infrastructure Against Ransomware?
With the nature of modern ransomware attacks now being to exfiltrate data as well as encrypt files, the key to ransomware defense is prevention; in other words, preventing the attackers from getting in where possible, and detecting and blocking them as early as possible in the threat lifecycle where not.
This requires, first and foremost, visibility into your network. What devices are connected and what are they? Discovery and fingerprinting through both active and passive discovery are a prerequisite for defending against intruders. It’s also important to control access, harden configurations and mitigate vulnerabilities through frequent patching. Enforcing VPN connectivity, mandatory disk encryption, and port control will also reduce the attack surface for ransomware.
Email and phishing are still the main entry vector for ransomware, so a good and frequent training program with simulations is important. On top of that, ensure that even if users are compromised, they only have access to services and resources necessary for their work.
These are all good measures that should stop opportunistic attacks, but determined threat actors targeting critical infrastructure will find ways around these. That’s why a proven EDR solution that stops attacks early is essential.
Conclusion
The increase in ransomware attacks on critical infrastructure is a major concern. Once the target solely of nation-state actors that would rarely execute “noisy” attacks which could reveal their presence, businesses and organizations within the 16 sectors of critical infrastructure are now seen as prime targets for ransomware operators. Disrupting and potentially damaging vital equipment, networks, assets and services means cyber criminals have a better chance of getting a payout. With data leakage and regulatory fines also a factor, it’s vital that these attacks are stopped in their tracks. If you would like to see how the autonomous SentinelOne platform can help protect your organization against ransomware attacks, contact us today or request a free demo.


