Threat actors are individuals or groups that carry out cyber attacks. This guide explores the different types of threat actors, their motivations, and tactics.
Learn about the importance of understanding threat actors in developing effective cybersecurity strategies. Understanding threat actors is crucial for organizations to anticipate and mitigate risks.

This article will review what threat actors are, threat actor targets, types of threat actors, and how to prevent their attacks.
What is a Threat Actor?
A cyber threat actor is any individual or group that poses a threat to cybersecurity. Threat actors are the perpetrators behind cyberattacks, and are often categorized by a variety of factors, including motive, type of attack, and targeted sector.
Today, the cyber threat environment is arguably more dynamic than ever before and threat actors are becoming more sophisticated.
Understanding threat actors and their motives can help organizations better protect themselves from the damage these actors cause as they exploit vulnerabilities, compromise user identities with elevated privileges, evade security controls, damage or delete data, or manipulate sensitive information.
Threat Actor Targets
Threat actors primarily target large organizations for monetary gain, data, and sensitive intelligence, or to cause service disruption and reputational harm. However, small and medium-sized businesses (SMBs) have also become frequent targets for threat actors because their relative lack of resources can mean that their security systems are weaker than those of large enterprises.
In today’s threat landscape, most organizations are likely to be targeted by a threat actor, regardless of their size or industry. In fact, businesses faced 50% more cyberattack attempts per week in 2021 compared to 2020. Today, threat actors can and will find a path straight to the crown jewels if the path is unprotected.
Threat Actor Types and Attributes
“Threat actor” is a broad term that encompasses a wide variety of individuals and groups categorized based on their skill set, resources, or motivation for attack.
Here are some of the most common types of threat actors and the motivations typically behind their actions:
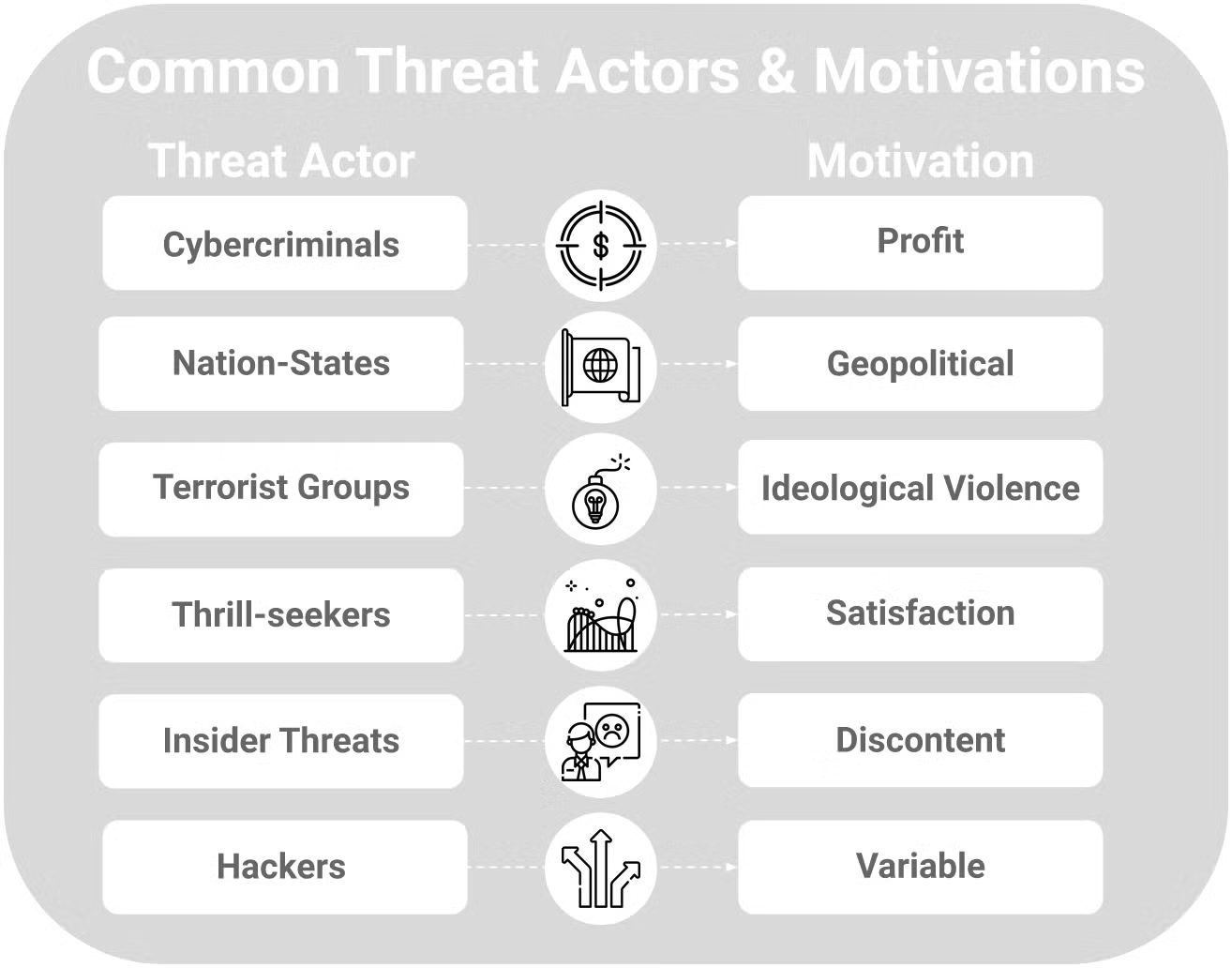
1. Cybercriminals
Cybercriminals are individuals or groups who use digital technology to conduct illegal activity. They’re often motivated by financial gain.
This type of threat actor typically employs social engineering tactics such as phishing emails to lure victims into clicking on a malicious link or downloading malicious software (malware). Other examples of cybercrime include stealing data, tricking victims into transferring money, stealing login credentials, and making ransom demands.
2. Nation-States
Nation-states may fund threat actor groups to perform a variety of malicious activities on the networks of other governing entities including espionage or cyberwarfare. Since nation-state funded threat actors tend to be highly resourced, their behavior is often persistent and more difficult to detect.
Targeting their opponents’ networks in stealth, nation-state-funded threat actors typically seek to exfiltrate or corrupt sensitive data and assets, disrupt critical infrastructure, or gather confidential intelligence.
3. Terrorist Groups
As with physical acts of terrorism, the goal of cyber terrorists is typically to cause harm and destruction that furthers their cause. This type of threat actor targets businesses, state machinery, and critical infrastructures or services that will cause the most damage or disruption.
4. Thrill-Seekers
Thrill-seekers are threat actors who attack computer systems or networks for personal enjoyment. Whether they want to see how much data and sensitive information they can steal, or they are interested in how specific networks and computer systems operate, thrill-seekers may not necessarily intend to do much harm to their targets. However, they can interfere with computer systems and networks or exploit vulnerabilities for more sophisticated cyberattacks in the future.
5. Insider Threats
Insider threats are on the rise. These threats can be categorized into the following types:
- Malicious Insiders: Malicious insiders are individuals who have access to the corporate environment and decide to turn against their employers by helping threat actors; usually for monetary gain.
- Incautious Insiders: Incautious insiders are employees who may not have malicious intent but end up causing a data breach due to their carelessness. They might click on a phishing email, install unapproved software, or lose their corporate devices.
6. Hackers
Although the term ‘threat actor’ is often used interchangeably with ‘hackers’, hackers and threat actors are not one and the same. A hacker is someone who uses their computer skills to overcome a challenge or problem, for better or for worse, while threat actors almost always have malicious intent.
Hollywood popularized the term to invoke images of nefarious individuals with malicious intentions, such as causing disruption or breaking the law. However, there are many types of hackers with different capabilities.
Here are some examples of different types of hackers and what they can do:
Black Hat Hackers
Black hat hackers work against organizations or government agencies in an attempt to break into computer networks or systems with malicious intent. Black hat hackers often work alone or with organized crime groups and employ a number of techniques to hack their targets, including social engineering, hacking passwords, infecting devices with malware, logging keystrokes, or creating botnets to execute a Distributed-Denial-of-Services (DDoS) attack.
White Hat Hackers
White hat hackers, also called ethical hackers, work with organizations or government agencies to identify vulnerabilities and protect cyber systems from malicious hackers. Unlike other types of hackers, white hat hackers always have permission from the organization or agency they work with to hack into computer networks or systems.
Grey Hat Hackers
Grey hat hackers fall somewhere in between white hat hackers and black hat hackers. Grey hat hackers hack into computer networks or systems in order to draw the target’s attention to vulnerabilities or potential attack paths and then charge a fee to fix the issues they’ve discovered. Most often, this type of hacker exploits security issues without malicious intent, but it is done without permission and often through illegal tactics.
Green Hat Hackers
Green hat hackers are beginners and often seek out information from more experienced members of the hacking community. Although green hat hackers may not always have the necessary skills or knowledge to launch a coordinated attack, they can still cause serious damage if they don’t have a clear understanding of what they’ve done or how to fix it.
Blue Hat Hackers
Blue hat hackers are most similar to white hat hackers: they’re security professionals working at consulting firms that are hired specifically to test a system prior to its launch. Sometimes, blue hat hackers also target individuals or companies in retaliation for some wrongdoing without putting much thought into the consequences of their actions.
Red Hat Hackers
Red hat hackers are often seen as the “dark horses” of the hacking world, working alone or in private groups to disarm black hat hackers. Unlike white hat hackers who turn black hat hackers into the authorities, red hat hackers often focus on destroying resources and doing harm.
Script Kiddies
Unlike other types of hackers, script kiddies are often motivated by boredom and don’t write their own computer scripts or code. Instead, they insert existing scripts or codes into viruses or applications to hack computer systems belonging to others. In the hacking world, script kiddies are notorious for being relatively unskilled and immature compared to other types of hackers.
Hacktivists
Hacktivists are often considered black hat hackers, but their motivations for hacking are political. Whether they’re concerned with preserving free speech or exposing instances of human rights violations, hacktivists target individuals, organizations, or government agencies.
Most of the time, hacktivists believe they’re trying to enact a positive change in the world. For example, the hacking group Anonymous is well-known for its numerous cyberattacks against several governments and have been called “freedom fighters” by their supporters.
Of the different types of hackers, the term “threat actor” most directly applies to black hat hackers, blue hat hackers, script kiddies, and hacktivists. Whether it’s cybercriminals or insiders, Singularity’s threat intelligence helps track and defend against all types of threat actors.
Related Cybersecurity Concepts to Know
In addition to understanding the essential components of threat actors and their attributes, it’s helpful to review these cybersecurity concepts:
Malware
Malware is a type of malicious software that is designed to damage or disable computers. Malware can be used to steal data, take control of systems, or launch attacks on other computers.
There are many different types of malware, including viruses, worms, Trojans, and ransomware. Malware can be spread through email attachments, infected websites, or compromised software.
Phishing
Phishing is a type of cyberattack that uses emails or websites that appear to be from legitimate sources in order to trick users into disclosing sensitive information or clicking on malicious links.
Phishing attacks can be very difficult to detect because they often use spoofed email addresses and websites that look similar to legitimate ones. Attackers will also target specific individuals or organizations in order to increase their chances of success.
Denial-of-Service Attack
A Denial-of-Service attack (DoS attack) is a type of cyberattack that attempts to make a system or network unavailable to users. DoS attacks target websites or online services and can be used to take down entire systems.
DoS attacks are usually carried out by flooding the target with traffic or requests until it can no longer handle the load and becomes unavailable. They can also be used to disable systems or networks by corrupting data, taking advantage of vulnerabilities, or overloading resources.
Ransomware
Ransomware is a type of malware that encrypts files or locks systems, making them inaccessible to users. It can be spread through email attachments, infected websites, or compromised software. This type of malware blocks access or encrypts assets, often forcing the user to pay a ransom to regain access to their device, files, or system.
Thinking of ransomware as simple encryption of randomly stolen data is no longer an accurate representation of the plethora of today’s data extortion strategies. Ransomware actors have recently turned toward data theft instead of time-expensive encryption. Trends indicate that full encryption of victim data is often too arduous and slow for many threat actors, and increases the risk of detection.
What’s emerged is a spectrum of threat actors who are moving past traditional, time-consuming encryption and focused on destroying all stolen data. Now, actors are seen prioritizing faster attacks either through data extortion where the data is more or less preserved, or only partial corruption allowing them to move quickly and demand increasingly larger ransom demands.
Drive-by Download
A drive-by download is a type of cyberattack that involves infecting a system with malware without the user’s knowledge or consent. Drive-by downloads usually happen when a user visits an infected website or clicks on a malicious link.
This form of attack can be used to install all types of malware, including viruses, Trojans, and ransomware.
Threat Actor Examples
Some threat actors may be lone attackers while others may be part of a larger, organized crime ring or cyber threat organization.
Reviewing some recent examples of cyberattacks can help organizations better anticipate what type of threat actor might target their networks or systems and prepare for similar incidents in the future.
MeteorExpress
In July of 2021, a wiper attack – an attack using malware designed to erase the hard drive of the computer it infects – crippled the Iranian national railway system. Once successfully hacked, the displays instructed railway passengers to direct any complaints to the phone number of the Iranian Supreme Leader Khamenei’s office.
Dubbed “MeteorExpress,” this campaign demonstrates the ways in which a threat actor can use technical skills to gain access to an information system and exploit it for a political purpose. Today, the threat actor behind this attack is still a mystery.
8220 Gang
A crimeware group known as 8220 Gang targets cloud infrastructure services including AWS, Microsoft Azure, Google Cloud, Aliyun and Qcloud, to deploy illicit cryptocurrency miners at their victims’ expense. Although the group has operated for years, by mid 2021, new campaigns using long-running sets of infrastructure brought botnet numbers from roughly 2,000 infected hosts up to today’s figure of around 30,000.
Threat actors such as 8220 Gang often spend years slowly evolving their campaigns until they become too massive to dismantle.
REvil Ransomware
REvil ransomware was successfully delivered to thousands of corporate endpoints through a zero-day attack targeting Kaseya VSA servers commonly used by Managed Security Service Providers (MSSPs) and IT management firms. This attack appears to be one of the largest ransomware incidents to date with attackers offering a universal decryption tool for all its victims at a lump sum of $50 million (originally $70 million).
Although initially considered a supply chain attack, this well-orchestrated, mass-scale ransomware campaign reveals how lucrative cyberattacks can be for threat actors, and how important a modern endpoint detection and response (EDR) tool is for organizations.
Aoqin Dragon
Named and tracked as “Aoqin Dragon” by SentinelLabs researchers, this nation-state funded threat actor group is responsible for a cluster of malicious activity dating back to 2013 targeting government, education, and telecommunications organizations across Southeast Asia and Australia. Although the exact motives are unknown, it is likely that this Chinese-linked advanced persistent threat (APT) group’s main focus is espionage.
This example illustrates how threat actors can quietly conduct long-lasting campaigns to stay under the radar while conducting espionage operations and continuing to advance their tradeoff.
Moshen Dragon
Dubbed “Moshen Dragon,” this Chinese-aligned threat actor has been attributed with hijacking legacy security products including Symantec, TrendMicro, McAfee, BitDefender, and Kaspersky to conduct attacks. In addition to the five different malware triads Moshen Dragon deployed, they also used a variety of other tools including an LSA notification package and a passive backdoor known as GUNTERS.
Threat actors are often likely to use multiple tactics, techniques, and tools to breach computer systems and networks. Once threat actors establish a foothold, they will often proceed with lateral movement within the network, place a passive backdoor into the environment, harvest as many credentials as possible, and then focus on data exfiltration.
How to Prevent & Stop Threat Actor Cyber Attacks
The best advice for defenders is to always act under the assumption that their networks already host threat actors. The best way to prevent threat actors is to have a comprehensive security solution in place. The ideal security solution should include the following capabilities:
1. Endpoint Protection, Detection, and Response (EDR)
To protect organizations against threat actors, security teams use comprehensive endpoint security solutions like Singularity™ Endpoint with detection and response capabilities.
“Endpoint protection” refers to the technology and processes used to defend network endpoints, such as laptops, servers, and mobile devices, from malware and other threats. EDR tools are different from other security solutions in that they do not only focus on identifying and quarantining specific malware or officially declared incidents. Instead, EDR tools look for anomalous activities and provide alerts to security teams for further investigation.
According to Gartner, EDR solutions:
Record and store endpoint-system-level behaviors, use various data analytics techniques to detect suspicious system behavior, provide contextual information, block malicious activity, and provide remediation suggestions to restore affected solutions.
2. Zero Trust Security
A zero trust security model is an approach to cybersecurity that doesn’t rely on predefined trust levels. Instead, it treats all users, devices, and networks as untrusted until they are verified through continuous authentication and authorization checks.
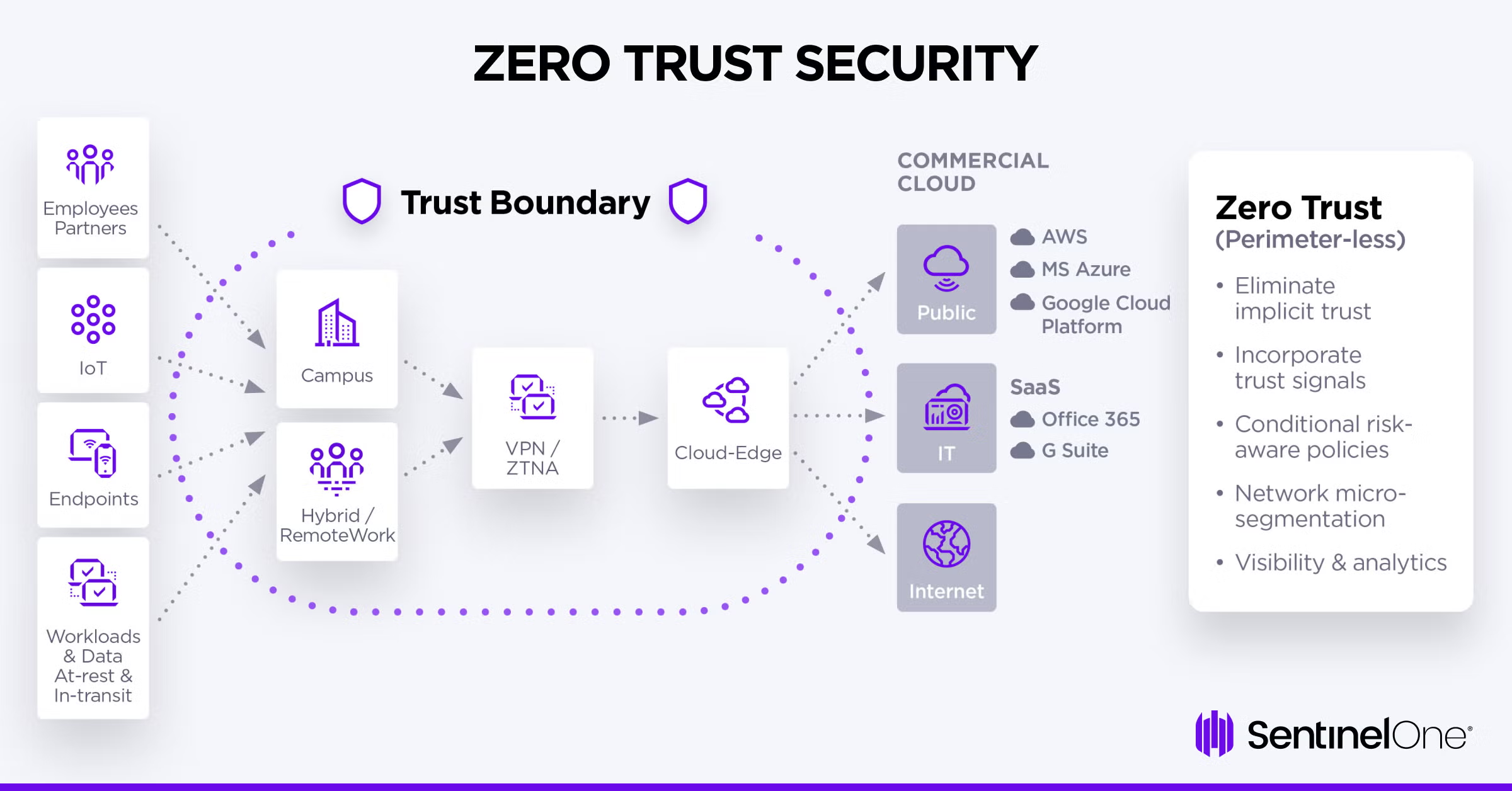
Zero trust architecture can help prevent threat actors from gaining access to computer systems or networks because it does not provide automatic access to sensitive data. Every single user, including employees and contractors, must go through the verification process each time they want to access something.
3. Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more pieces of evidence, or factors, before they can access sensitive data. For example, a user may be required to enter their password and then confirm their identity with a fingerprint or code sent to their mobile phone.
MFA is effective against threat actors because it makes it more difficult for unauthorized users to access sensitive data. Even if they have a valid password, they would also need to have the other factor, such as a physical token or smartphone, to gain access to systems or networks.
4. Defense Against Advanced Persistent Threats (APTs)
An advanced persistent threat is a cyberattack where criminals work together to steal data or infiltrate systems that often go undetected over an extended period of time. In most cases, these attacks are performed by nation-states seeking to undermine another government.
Whereas other cyberattacks such as malware and phishing schemes work in a matter of days, an APT can take place over months or even years.
Some of the most common methods used by APTs include:
- Spear phishing: Sending targeted emails that appear to be from legitimate sources in order to trick users into clicking on malicious links or opening infected attachments.
- Social engineering: Tricking users into disclosing sensitive information or compromising their systems by using deception tactics such as fake websites or phone calls.
- Watering hole attacks: Infecting websites that are commonly visited by a target organization’s employees in order to infect their systems when they visit the website.
APTs are more difficult to defend against because they are usually carried out by well-funded and sophisticated organizations. However, with the right preparation and security measures in place, it can be much harder for them to succeed. Effective defense against threat actors requires an integrated solution like Singularity XDR, which provides real-time detection and response.
 Enhance Your Threat Intelligence
Enhance Your Threat Intelligence
See how the SentinelOne threat-hunting service WatchTower can surface greater insights and help you outpace attacks.
Learn MoreStop Threat Actors with SentinelOne
Threat actors are constantly changing their tactics, making it essential to have a security solution that adapts as quickly as they do. The world’s leading next-generation endpoint security platform, SentinelOne, is purpose-built to stop threats at every stage of an attack lifecycle.
SentinelOne proactively resolves threats in real-time, using AI-powered models to identify malware and ransomware binaries before they can attack. It also builds critical context for proactive real-time detection and response that can protect systems from advanced persistent threats.
ActiveEDR, revolutionary technology designed by SentinelOne, identifies malicious acts in real-time, automating the required responses and allowing easy threat hunting. Harnessing the power of machine learning and artificial intelligence, it takes the burden off SOC teams and is able to autonomously mitigate events on the endpoint without relying on cloud resources.
Empowering security teams and IT admins to focus on the alerts that matter, ActiveEDR reduces the time and cost of bringing context to the complicated and overwhelming amount of data needed with other, passive EDR solutions. Instead, it provides comprehensive visibility, protection, and response capabilities in a single agent/console architecture.
Discover how SentinelOne proactively protects organizations from threat actors and schedule a demo today.
Threat Actor FAQs
A threat actor is any individual or group that intentionally causes harm in the cybersecurity world. They exploit vulnerabilities in computers, networks, and systems to carry out attacks on individuals or organizations. Threat actors can be lone hackers, organized criminal groups, nation-state operatives, or even malicious insiders within your own company.
They use various methods like malware, phishing, ransomware, and social engineering to achieve their goals. Their motivations range from financial gain and political activism to espionage and simple disruption.
The five main types are cybercriminals, nation-state actors, hacktivists, insider threats, and script kiddies. Cybercriminals seek financial gain through ransomware, fraud, and data theft. Nation-state actors work for governments to conduct espionage and cyberwarfare. Hacktivists use attacks to promote political or social causes.
Insider threats come from current or former employees who misuse their access. Script kiddies are inexperienced attackers who use existing tools without deep technical knowledge.
Not really. “Hacker” is a broader term that includes both ethical and malicious actors. Hackers can be categorized as white-hat (ethical), black-hat (malicious), or gray-hat (somewhere in between). All threat actors are hackers, but not all hackers are threat actors. White-hat hackers work to improve security through legitimate penetration testing and vulnerability research.
Threat actors specifically refer to malicious hackers who intend to cause harm. The key difference is intent – threat actors always have malicious purposes, while hackers might be trying to help improve security or simply explore systems without harmful intent.
Threat actors start with reconnaissance to gather information about their targets. Then they gain initial access through methods like phishing emails, exploiting vulnerabilities, or social engineering. Once inside, they escalate privileges to gain higher-level access. Next, they conduct discovery to map the network and identify valuable targets.
They move laterally across systems to expand their foothold. After that, they execute their main objective – whether that’s stealing data, deploying ransomware, or establishing long-term persistence.
Yes, they can. Insider threats are among the most dangerous threat actors because they already have authorized access to your systems and data. They can be malicious insiders who intentionally steal information or sabotage systems, negligent insiders who accidentally create vulnerabilities, or compromised insiders whose accounts have been hijacked by external attackers. Malicious insiders often have deep knowledge of security procedures and can bypass many controls.
Defense requires multiple layers of security controls. Start with employee training on phishing and social engineering tactics. Implement multi-factor authentication and strong access controls. Deploy endpoint detection and response tools to catch malicious activity. Monitor network traffic for suspicious patterns and indicators of compromise. Keep systems patched and updated regularly.
Use threat intelligence to stay informed about current attack methods. Conduct regular security assessments and penetration testing. Develop incident response plans and practice them. The key is assuming a breach mentality – you need detection and response capabilities, not just prevention.
Threat intelligence transforms raw data about threats into actionable information you can use to defend your organization. It helps you understand which threat actors are likely to target your industry, their preferred tactics and techniques, and current attack campaigns. You will be able to prioritize your defenses against the most relevant threats. You can use indicators of compromise to detect ongoing attacks and threat actor profiles to predict future attacks.
They also help incident response teams understand what they’re dealing with and how to respond effectively. Its goal is to shift from reactive to proactive security.


