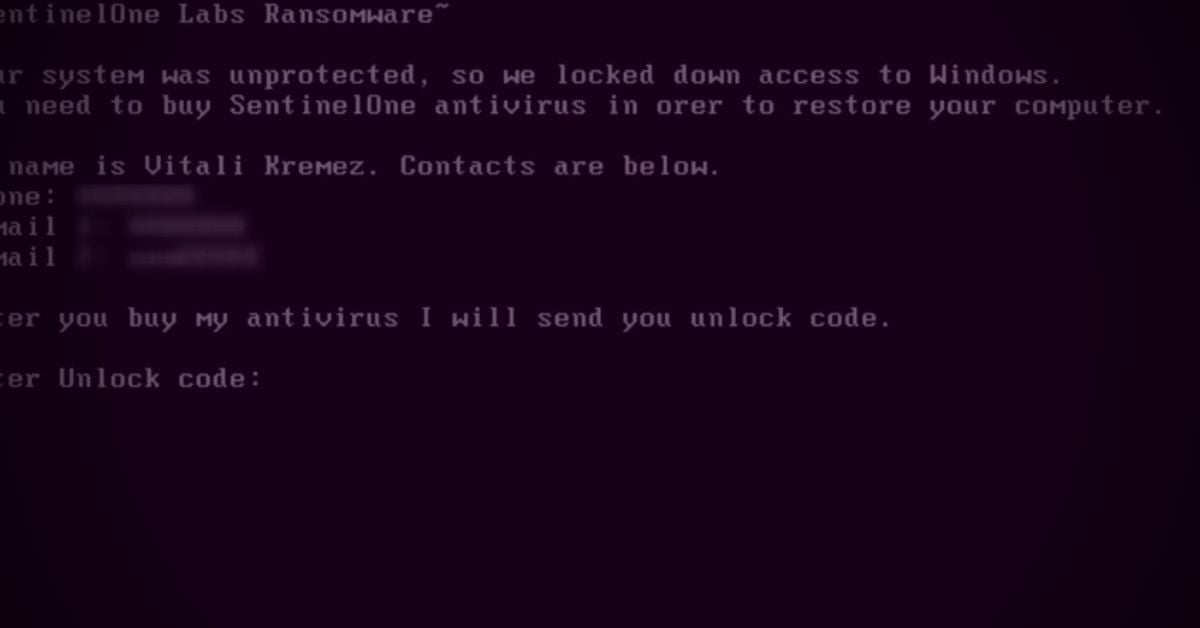
Earlier this month a steady stream of new MBRLocker malware variants began to appear, locking victims out of their devices. While many of these seem to be pranks rather than serious attempts at extortion like typical ransomware, the effect is no less disruptive and potentially just as damaging. This week, some attention-seeking pranksters decided to troll our own Vitali Kremez by releasing an MBRLocker variant using his name and revealing his personal contact details. While we wouldn’t ordinarily comment on such stunts, the issue has already been widely reported in the media.

Why Are Security Researchers Targeted by Malware Authors?
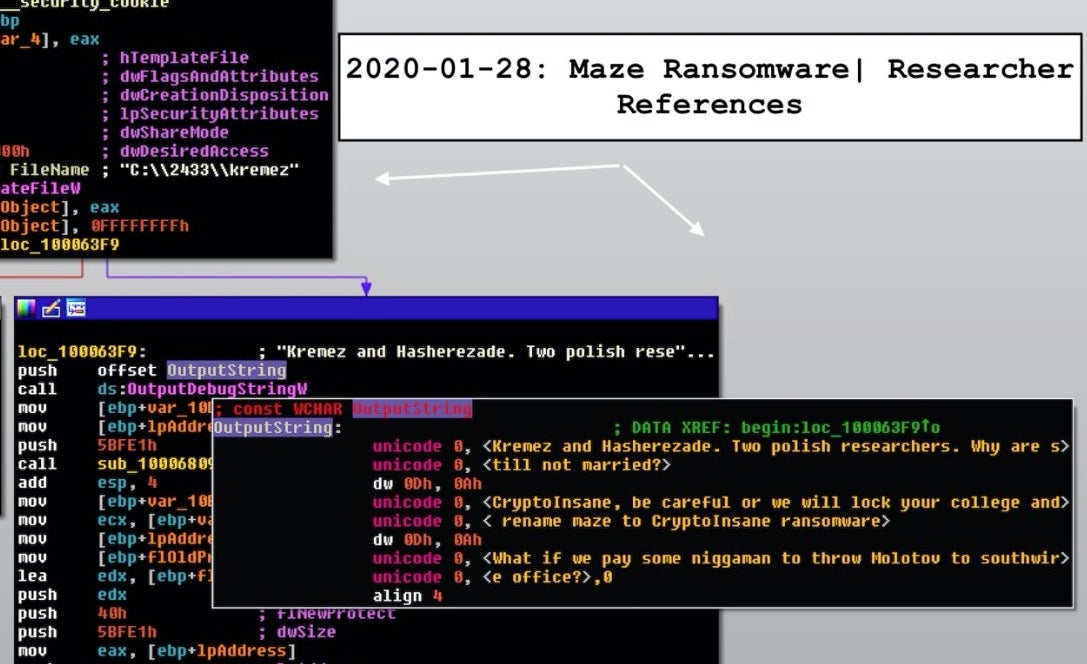
It’s not uncommon for malware authors to bait prominent security researchers and other cybercrime fighters. For example, a malspam campaign trolled AVIRA CEO, Travis Witteveen in 2016, while a ransomware campaign the same year dubbed ‘Black Shades’ included strings taunting researchers. Other ransomware like GandCrab has been known to call out researchers by name in code strings, and earlier this year Maze ransomware singled out Vitali Kremez, Hasherezade and CryptoInsane for special mention in their code.
However, it rarely gets as personal as this latest incident, in which the malware authors impersonated Vitali Kremez, and also included his personal contact details, falsely claimed to be promoting SentinelOne, and also called out security researchers @MalwareHunterTeam. Needless to say, neither SentinelOne nor any of the named researchers are in any way associated with this destructive prank.
The purpose of such stunts is usually attention-seeking, one of the trademarks of the ‘script kiddie’ class of threat actors; professionals generally avoid such behavior, as history shows such attention-seeking is one of the primary opsec failures that lead to the capture of cyber criminals by law enforcement. And while we wouldn’t ordinarily “feed the troll”, the widespread attention this has received in the mainstream cyber media as well as the confusion on behalf of some victims of this recent spate of MBRLocker variants justifies a clarification.
What is an MBRLocker?
MBR stands for “Master Boot Record”, which is a small sector on a disk drive that holds information needed by the operating system in order to boot. Once a machine boots, it will read the MBR first and only then will start the operating system. As such, manipulating the MBR will cause a failure to start the operating system, and from the average user standpoint, they will face a situation where, instead of the operating system being loaded and the user presented with a login screen or desktop view, they will get a command line view of a taunting message from the attacker splashed across the screen.
From a technical point of view, malware that ‘locks’ the MBR typically copies the original MBR to another part of the drive and overwrites the original MBR with the malware author’s code. When the user attempts to boot or restart a device after the malware has done its work, the computer will load whatever code the malicious prankster has placed in the custom MBR. Instead of loading the operating system, the malware displays the attacker’s taunting or threatening message.
MBRLockers have been around for a long time and are relatively unsophisticated malware. The tools to create these have been around since 2011 or so, and are widely available.
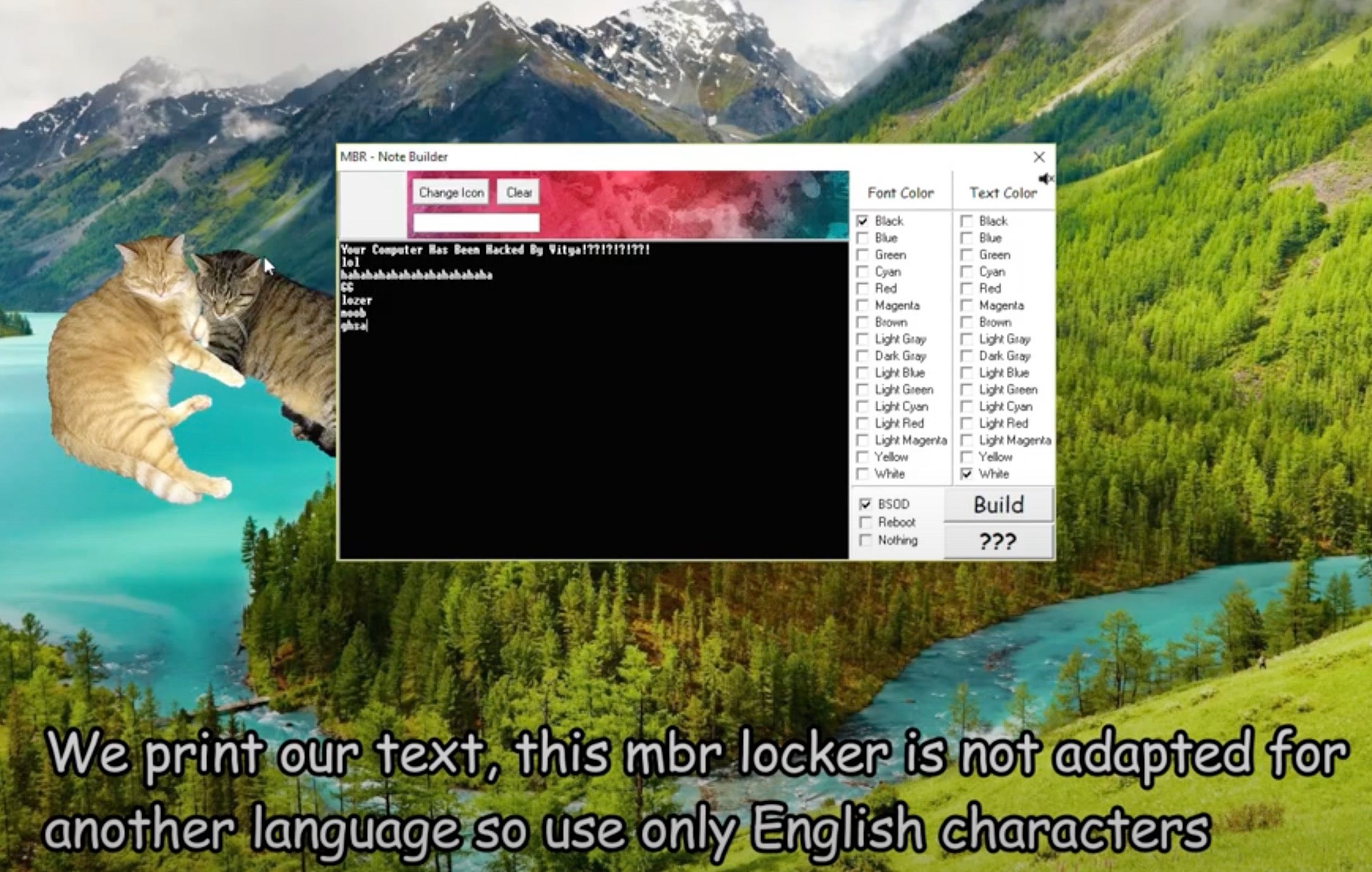
Over the last year we have seen something of a resurgence in the use of MBRLockers, resulting from some ‘aggressive’ advertising through Youtube, Discord, and similar social media platforms. Recently there have been multiple attacks observed leveraging this tool, outside of the ‘SentinelOne Labs’ focused example. Most are far more generic in nature, prompting victims to communicate with the attackers, via email, to receive the “unlock code”. Some of these are scams, others are genuine ransomware attempts, and still others are just purely destructive.
Often, an MBRLocker is not as fatal as it may seem. In some cases, victims have found that they can escape the custom MBR and restore the original by using the keychord “CTL+ALT+ESC”. However, this does not work on all variants, including the one released this week that has caused so much attention.
If you have been affected by this recent MBRLocker on an unprotected machine, the primary mitigation is to restore from a known-good backup. As MBRLockers are typically spread through download sites offering cracked versions of commercial software, be sure that your users are avoiding such sites and ensure your devices are protected by a trusted security solution.
Does SentinelOne Protect Against MBRLocker?
Yes, it does. As demonstrated in the video below, the SentinelOne platform protects customers from all variants of MBRLocker.
Conclusion
Defenders are used to dealing with cybercriminals that are motivated by profit, whether that comes from ransomware, adware, business email compromise, cryptomining, data theft or any one of the other myriad scams they come up with. Crude wiper malware like the one we’ve seen this week is just a destructive prank that yields only two things for the perpetrators: thrills and publicity. For victims without the protection of a modern security solution, it’s nothing but misery. Therein lies the one thing that such pranksters do have in common with professional cybercriminals: a lack of concern for the damage they do.