Executive Summary
- Some endpoint vendors have been claiming this 10/10 severity CVE is a network security issue. SentinelOne today shows that this is inaccurate and that exploitation of Zerologon can be detected on the endpoint.
- SentinelOne is the only known vendor able to accurately detect the exploitation attempt on targeted hosts. The SentinelOne platform is also capable of linking post-exploitation events together with our Storyline technology.
- This critical detection ability is available starting 4.2 SP4 and is available for existing SentinelOne customers.
- Watch the demo below to see SentinelOne autonomously detect this critical server vulnerability. Innovation and a vector-agnostic technology matters in keeping our customers one step ahead of the threat landscape.

The Zerologon Vulnerability Explained
CVE-2020-1472, more popularly known as “Zerologon”, is a critical vulnerability in all versions of Microsoft Windows Server that are currently supported (Windows 2008 R2, 2012, 2016, 2019). This privilege escalation vulnerability leverages a flaw in the Netlogon Remote Protocol (MS-NRPC) and allows an attacker to impersonate a system, including the machine account of the domain controller itself.
The vulnerability, discovered by security expert Tom Tervoort of Secura, allows a remote attacker to forge an authentication token for Netlogon to set the computer password of the domain controller to a known value. After that, an attacker can use the new password to take over the domain controller, alter or add additional authentication credentials, escalate privileges or move laterally to other machines in the domain.
Subsequently, other researchers have discovered more ways to operationalize the Zerologon vulnerability beyond resetting the domain passwords, including demonstrating the capability to extract all domain passwords. This development increases the risk enterprises are exposed to.
For such an attack to be successful, an attacker would first have to gain remote or physical access to a device on the same network as a domain controller. However, valid domain credentials, or domain membership, are not prerequisites for a successful attack.
Since the vulnerability was disclosed, exploit code has been found in the wild and CISA has stated that the vulnerability poses an “unacceptable risk” and requires “immediate and emergency action”.
Although Microsoft have released an initial patch for Zerologon, this is only the beginning of a phased rollout, which the OS vendor expects to take until at least Q1 of 2021 to complete. Meanwhile, Microsoft’s advisory points out that the current update only protects supported Windows devices, leaving legacy versions of Windows and other devices that communicate with domain controllers using the Netlogon MS-NRPC protocol vulnerable to compromise.
Moreover, the initial patch does not prevent an attack exploiting Zerologon. Rather, it adds logging to detect non-secure RPC and a registry setting to disable non-secure RPC if there aren’t any devices using the protocol. The challenge for enterprise security teams is that this may break legacy applications if it is just turned off. Hence, even with the currently available patch, if an organization can’t disable the registry setting they are still vulnerable.
Detecting and Defending Against Abuse of Zerologon
From an endpoint perspective, this attack can be challenging to detect as the attacker is essentially authenticating to the domain in a manner resembling legitimate user/account behavior. In addition, the primary attack vector is at the network level, as opposed to through interaction with a host’s filesystem. As a result, addressing the flaw directly is ‘out-of-scope’ for many traditional endpoint security solutions.
In contrast, SentinelOne researchers have taken a vector agnostic approach that leverages some unique, proprietary, SentinelOne innovations to enable detection of this exploit on the endpoint. Our SentinelLabs research team has been running numerous tests across various available frameworks. During our analysis, we observed that this attack, while successful, will also be highly noticeable on the domain controller as the attack negatively affects communications with the domain controller in numerous ways.
As a result of our research, the SentinelOne platform is able to both detect initial exploitation as well as the post-exploitation attacks on a targeted system. While this attack starts from the network, the endpoint is fully aware of the incoming traffic attempts.
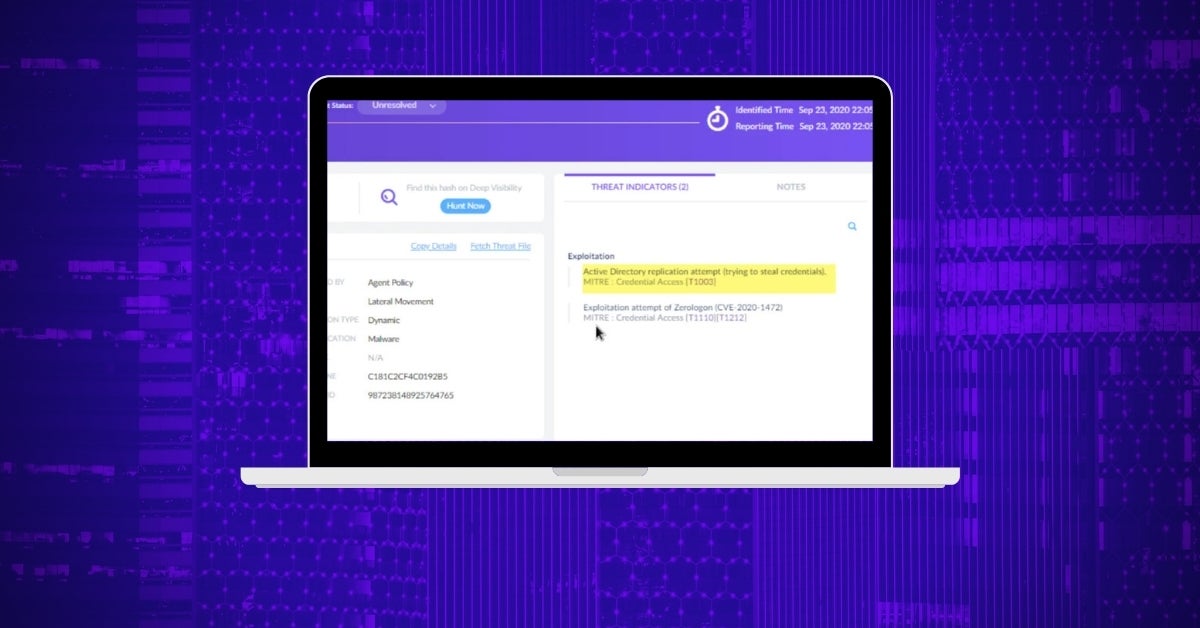
The Netlogon Remote Protocol is used to maintain domain relationships from the members of a domain to the domain controller (DC), among DCs for a domain, and between DCs across domains. By monitoring the authentication attempts made within the system, both locally and remotely, and by passing them through our behavioral AI engine, we are able to distinguish the exploitation attempts from benign authentication attempts.
When a suspicious activity is detected, a threat is raised allowing for an in-context alert to be shown in the management console.
Interested in Protection from Zerologon?
Like any other modifications on the agent, we started deploying this capability to selected customers to ensure stability in various environments. This critical detection is available now to existing customers deploying 4.2 SP4. Versions 4.3 and 4.4 will include this detection capability with the upcoming service pack update. If you are not already a SentinelOne customer, find out more about how to protect your business or request a free demo.