Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data. Our guide explores the different types of vulnerabilities, their potential impact on organizations, and the importance of vulnerability management.
Learn about common sources of vulnerabilities, including software bugs and misconfigurations, and discover best practices for identifying, assessing, and mitigating these risks. Stay informed about the latest trends in vulnerability management and how to strengthen your organization’s security posture.
 How Enterprises Can Stay Safe from Software Vulnerabilities
How Enterprises Can Stay Safe from Software Vulnerabilities
To stay safe from security vulnerabilities, enterprises should follow best practices for cybersecurity. This may include the following measures:
- Regularly perform security audits and assessments to identify and prioritize vulnerabilities.
- Implement a robust patch management program to ensure that all software and systems are up-to-date with the latest security patches and fixes.
- Use vulnerability scanners and other security tools to quickly identify and remediate vulnerabilities.
- Train employees on identifying and reporting potential vulnerabilities and implement a process for responding to reported vulnerabilities.
- Work with a trusted security partner or a managed security service provider to help identify and mitigate vulnerabilities in your environment.
- Regularly perform penetration testing to simulate real-world attacks and to identify and remediate vulnerabilities in your environment.
- Implement robust access controls and authentication mechanisms to prevent unauthorized access to your systems and data.
What Types of Vulnerabilities are used Against Enterprises?
Some of the most famous vulnerabilities used for security breaches include:
- SQL injection: This vulnerability allows an attacker to inject malicious SQL code into a database to gain access to sensitive data or to manipulate the database.
- Cross-site scripting (XSS): This vulnerability allows an attacker to inject malicious JavaScript code into a website to steal user data or perform other malicious actions.
- Remote code execution (RCE): This vulnerability allows an attacker to execute arbitrary code on a remote system, gain unauthorized access, or perform other malicious actions.
- Unvalidated inputs: This vulnerability allows attackers to provide malicious input to a website or application, bypass security controls, or execute arbitrary code.
- Unsecured credentials: This vulnerability occurs when sensitive data, such as usernames and passwords, are stored unsecured, allowing attackers to easily access them.
- Unsecured networks: This vulnerability occurs when networks are not properly configured or protected by firewalls or other security measures, allowing attackers to easily gain access.
- Unsecured devices: This vulnerability occurs when devices, such as laptops and mobile phones, are not properly secured, allowing attackers to easily access them and steal sensitive data.
Some examples of vulnerable software that was used to compromise enterprises include:
- Adobe Flash: This software was widely used on the internet but was also known to be vulnerable to several security exploits, including buffer overflow and heap overflow attacks.
- Microsoft Windows: This operating system is the most widely used in the world, but it has also been the target of numerous security vulnerabilities, including remote code execution and privilege escalation vulnerabilities.
- Apache Web Server: This web server software is widely used on the internet, but it has also been the target of security vulnerabilities, including cross-site scripting and cross-site request forgery attacks.
- Oracle Database: This database software is widely used by businesses, but it has also been the target of security vulnerabilities, including SQL injection and privilege escalation attacks.
- Adobe Acrobat Reader: This software is widely used for viewing PDF files, but it has also been the target of security vulnerabilities, including remote code execution and heap overflow attacks.
- Java: This programming language is widely used for developing web applications, but it has also been the target of security vulnerabilities, including cross-site scripting and remote code execution attacks.
- PHP: This programming language is widely used for developing web applications, but it has also been the target of security vulnerabilities, including SQL injection and cross-site scripting attacks.
One of the most commonly exploited vulnerabilities in the wild is the CVE-2017-0199, a remote code execution vulnerability in Microsoft Office that allows attackers to execute malicious code on the victim’s system. This vulnerability has been exploited by various ransomware groups, including the Ryuk, Emotet, and Dridex malware families.
Why Patching Vulnerable Software is Important?
As a CISO, it is important to prioritize patching vulnerable software to protect your organization against security breaches, maintain compliance with industry standards, avoid legal liabilities, and improve overall security posture. This may involve implementing a patch management program that regularly checks for and installs security patches for all software used within the organization. It may also involve working with other departments, such as the IT team, to ensure that patches are applied promptly and consistently. Additionally, it may involve monitoring the security landscape and staying up-to-date with the latest threats and vulnerabilities to identify and address potential risks as they arise.
To summarize, patching vulnerable software is important for several reasons:
- To protect against security breaches: By patching vulnerable software, organizations can protect themselves against security breaches, such as data theft, ransomware attacks, and other forms of cybercrime. For example, in 2017, the WannaCry ransomware attack exploited a vulnerability in the Microsoft Windows operating system to encrypt data and demand ransom payments.
- To maintain compliance with industry standards: Many industries have specific compliance standards that require organizations to patch vulnerable software in a timely manner. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires organizations to apply security patches within 30 days of release to protect against security breaches.
- To avoid legal liabilities: If organizations fail to patch vulnerable software, they may be held legally liable for any security breaches that occur as a result. For example, in 2018, a U.S. court ruled that Target was liable for a data breach due to its failure to patch a known vulnerability in its payment card system.
- To improve overall security posture: By patching vulnerable software, organizations can improve their overall security posture by reducing the number of potential attack vectors and reducing the risk of compromise. For example, by patching software such as Adobe Flash, Microsoft Windows, and Apache Web Server, organizations can protect against a wide range of security vulnerabilities, including buffer overflow, heap overflow, and remote code execution attacks.
How Vulnerabilities Can be Prioritized?
The number of Common Vulnerabilities and Exposures (CVEs) submitted each year varies, but it has been increasing in recent years. In 2020, over 24,000 CVEs were submitted, a significant increase from previous years. This trend will likely continue as the number of connected devices, and the amount of sensitive data shared online grows.
The Common Vulnerability Scoring System (CVSS) is a commonly used scale for measuring the severity of vulnerabilities. This scale uses a range of metrics to determine the potential impact of a vulnerability, such as the type of attack, the likelihood of successful exploitation, and the impact on confidentiality, integrity, and availability.
The CVSS scale uses a score from 0 to 10, with 0 being the least severe and 10 being the most severe. For example, a vulnerability with a score of 0.1 would be considered low severity, while a vulnerability with a score of 9.0 would be considered critical severity. The CVSS score can help organizations prioritize patching and risk mitigation efforts based on the potential impact of a vulnerability.
Some examples of CVSS 10 vulnerabilities, which are considered the most severe, include:
- The Heartbleed vulnerability in OpenSSL allows attackers to access sensitive data, such as passwords and private keys, from a vulnerable server.
- The WannaCry ransomware attack exploited a vulnerability in Microsoft Windows to encrypt files and demand a ransom payment.
- The BlueKeep vulnerability in Microsoft Windows allows attackers to remotely execute arbitrary code on a vulnerable system.
- The Shellshock vulnerability in Bash, allows attackers to execute arbitrary code and gain unauthorized access to a system.
- The EternalBlue vulnerability in Microsoft Windows allows attackers to remotely execute arbitrary code and spread malware across a network.
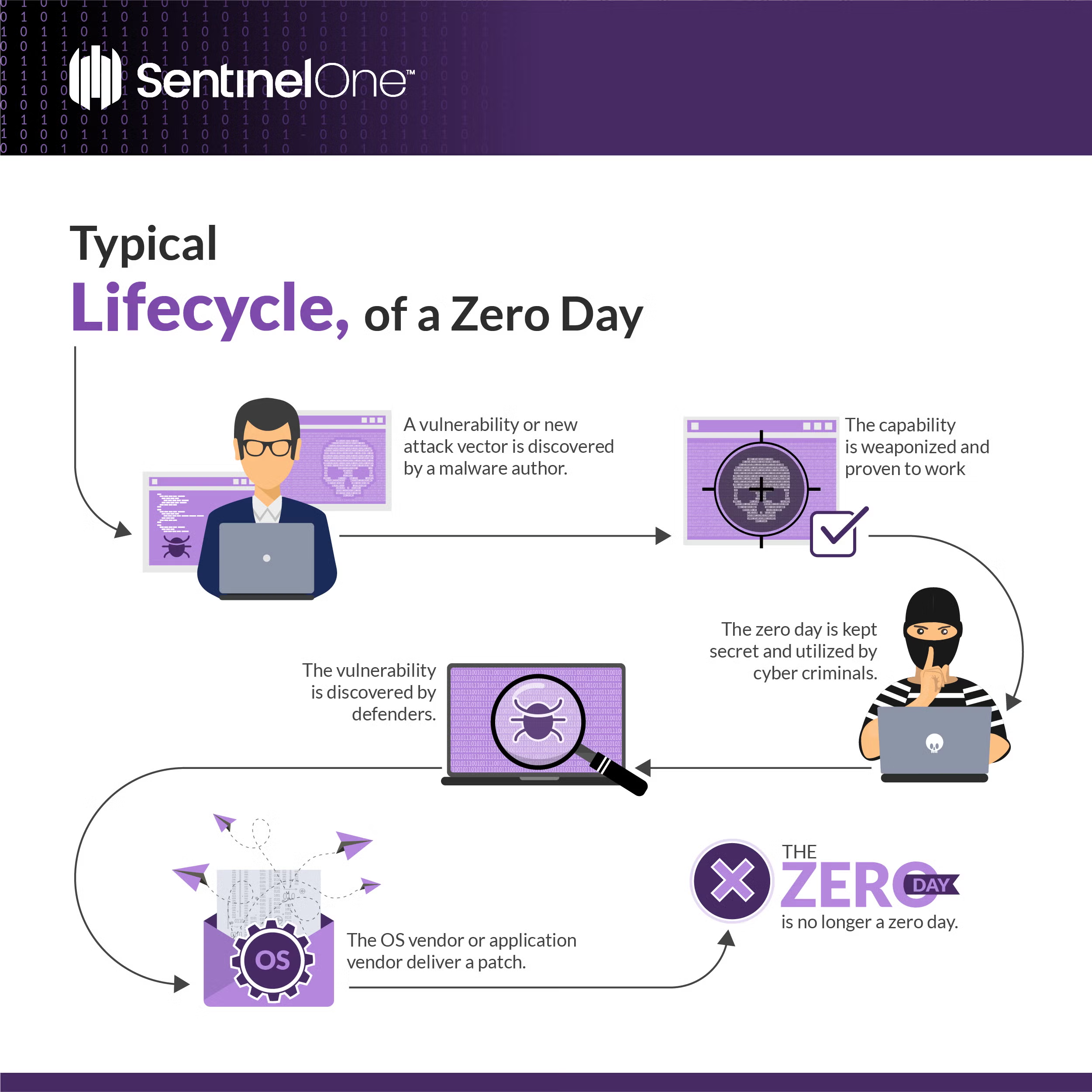
What is a Zero-day Vulnerability?
A zero-day vulnerability is a security flaw that has not yet been discovered or disclosed to the public. This means attackers can exploit the vulnerability before it is patched or fixed, allowing them to gain unauthorized access to systems or networks. Zero day vulnerabilities are particularly dangerous because they are unknown to the victims and, therefore, difficult to protect against.
Is Malware a Threat or Vulnerability?
Malware is a type of threat rather than a vulnerability. A vulnerability is a weakness in a system or network that can be exploited by an attacker to gain unauthorized access or cause harm. On the other hand, malware is a type of malicious software designed to exploit vulnerabilities to compromise a system or network. So, while malware can take advantage of vulnerabilities to gain access to a system or network, it is not itself a vulnerability.
It is difficult to say which is more dangerous, malware or a vulnerability, as it depends on the specific situation. Without a vulnerability, malware would not be able to compromise a system or network. On the other hand, without malware, attackers would not be able to take advantage of vulnerabilities to gain access. In terms of potential impact, malware can cause significant damage to a system or network, such as stealing data, encrypting files, or disrupting operations. Vulnerabilities, on the other hand, may not directly impact a system or network, but they can make it more susceptible to attacks. Overall, malware and vulnerabilities are serious cybersecurity threats and should be addressed as part of a comprehensive security strategy.
Unleash AI-Powered Cybersecurity
Elevate your security posture with real-time detection, machine-speed response, and total visibility of your entire digital environment.
Get a DemoConclusion
The risk of vulnerabilities in software can be reduced through regular patching and updates, as well as implementing secure development practices. However, it is unlikely that the risk will ever be completely eliminated as attackers constantly discover and exploit new vulnerabilities. It is important for organizations to continuously monitor for vulnerabilities and implement effective mitigation strategies to minimize their risk.
Security Vulnerability FAQs
A security vulnerability is a flaw or weakness in software, hardware, or processes that attackers can exploit to gain unauthorized access or cause harm. It might be a coding bug, misconfigured setting, or missing patch. When left unaddressed, vulnerabilities open doors for malware, data theft, or service disruption, so identifying and fixing them quickly keeps systems safer and more reliable.
Buffer overflows let attackers run arbitrary code by overrunning memory buffers. Injection flaws—like SQL or command injection—happen when untrusted input alters queries or commands. Cross-site scripting (XSS) enables attackers to run scripts in users’ browsers.
Broken access controls allow privilege escalation. Misconfigurations—such as default credentials or open ports—also rank high. Together, these account for many breaches and data leaks.
Vulnerabilities get scores from systems like CVSS, which rates severity on a 0–10 scale based on exploit complexity, impact on confidentiality, integrity, and availability, and whether user interaction is needed. Teams then factor in their own environment—asset value, exploit likelihood, and business impact—to rank which fixes matter most. That way, critical holes in high-value systems get patched first.
They turn up through code reviews, automated scanners, and penetration tests that probe for flaws. Bug bounty programs invite external researchers to hunt vulnerabilities in live systems. Security researchers and vendors also publish advisories when they find new bugs. Incident investigations also sometimes reveal previously unnoticed weaknesses that need a fix.
Responsible disclosure begins with privately notifying the vendor or maintainer and agreeing on a fix timeline. Vendors then develop and test patches before public release. Coordinated vulnerability disclosure means sharing advisories and patches together, so users can update before details go live. This reduces the window where attackers could exploit the issue.
Key metrics include mean time to patch—how long it takes from discovery to deployment. Track patch coverage percentage across systems and the number of outstanding high-severity fixes. Measure the rate of recurring vulnerabilities to spot process gaps. Be sure to monitor exploit trends in threat feeds to see if unpatched issues face active attacks, guiding prioritization.

