The rising trend in IoT devices on corporate networks brings with it an increased, and often invisible, risk of exposed assets. From printers and security cameras to “smart” office novelties, most of these wired devices come with baked-in default login credentials that are widely known and shared among cyber criminals. Even when a policy exists to change these defaults, many organizations use easily guessable passwords for the convenience of IT maintenance. While it’s true that managing risk can often be a trade-off between security and convenience, there’s no doubt that improperly managed IoT and other devices offer a path to compromise just waiting to be exploited.

Exactly that danger was graphically illustrated this week when a list of over half a million Telnet credentials belonging to severs, home routers and IoT devices were dumped on a hacking forum. The dump included the IP address, username and password for each of some 515,000 devices’ Telnet ports.
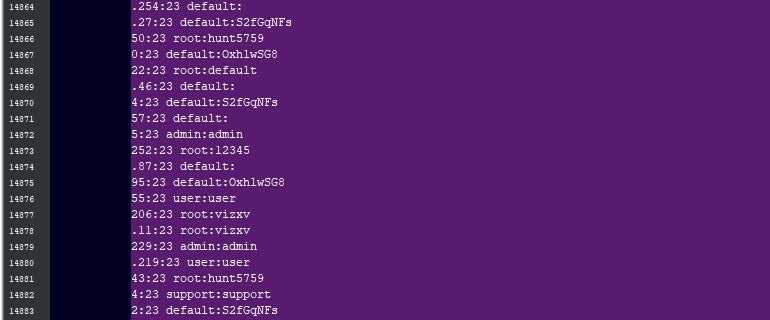
Is Telnet Still a (IoT) Thing?
Most networking admins will know all about telnet, which remains a popular networking tool, but if you’re not familiar with it don’t be surprised. It’s been disabled in Windows Desktop versions by default for a long time, and Apple completely removed the telnet client from macOS 10.12 High Sierra (i.e., September 2017) onwards. Both major OSs regard telnet’s clear text communication protocol as a security hazard and recommend other more secure options like SSH.
However, while telnet may have been the protocol targeted in this case, the issue is less with which protocol these devices use than it is with the failure of admins to use secure passwords to protect them. Indeed, this is the exact same methodology notoriously deployed to such great effect over three years ago by the original Mirai botnet attack. Clearly, lessons have not been learned.
How Do Hackers Discover Device Passwords?
The list of leaked credentials was compiled, and leaked, by a cyber criminal running a DDoS (Distributed Denial of Service) for Hire Attack service. Such services provide low-level threat actors (aka ‘Script Kiddies’) with the ability to target specific web sites or domains that they want to disrupt. Ordinarily, we’d expect the people behind such services to keep a list of compromised devices for their own use. However, in this case, the leaker said he no longer needed to use IoT botnets and had switched to “renting high output servers from cloud providers” instead. That suggests the list was compiled sometime before the leaker had decided on his new strategy, and indeed the ‘Date Modified’ file metadata in the dump span through October and November of last year.
For IT and Security admins, the greatest concern here should be the ease with which such a list can be compiled. Port scanners like Masscan and NMAP can rapidly surveil the entire Internet, and services like Shodan can be used to collect data on servers with open FTP, SSH, Telnet , RTSP and other ports. This data can then be used to access things like webcams, routers and other connected devices.
Attackers can not only quickly scan for open ports but also test them for default credentials like admin:admin and root:root. Offensive security tools like hydra can automate password cracking against remote targets through brute force and password spraying, in which a list of commonly used or weak passwords are tested against each account.
In the video below, we demonstrate how easy it is for attackers to harvest leaked passwords from public resources and use them to login to a Ring device, but the same principle applies regardless of the platform or kind of device targeted.
The effectiveness of this technique is evidenced by the size of the recent dump, and the fact that in 2017 a similar dump yielded over 30,000 account credentials. While that dump probably whittled down to no more than 8000 or so valid, unique credentials, that’s still a sizeable army for a botnet to recruit. More worryingly, every device whose credentials are leaked in dumps like these represents a possible entry point to business compromise and lateral movement if it belongs to a device connected to an enterprise network.
Forgotten Devices | Invisible Threats on Your Network
Aside from the danger of network admins using weak or default passwords for maintenance convenience, there is also the danger of forgotten devices.
The ease with which ‘smart’ devices like printers and security cameras can be set up in a plug-and-play manner and then be forgotten is a danger for any enterprise that does not have full visibility across its networks.
Add to that the fact that many embedded devices can be difficult or impossible to patch, it’s easy to see that even a device bought today and protected by strong credentials could become a risk in the future when its OS or firmware have been found to contain exploitable bugs. Without a full and updated inventory of what’s running on your network, the danger of “forgetting” about devices that could at some point be exploited is one that businesses can’t afford to ignore.
If the situation is worrying, the good news is it is entirely preventable. First, implement and enforce a password policy for your IoT devices just like you would for any other device. Second, ensure you have the tools for full network visibility and control so that forgotten assets can be discovered and managed.
Conclusion
Any connected device with an open, internet-facing port will be found and tested by cyber criminals. Not just “one day”, but likely thousands of times a day. Any device that is not secured with a strong password will almost certainly be compromised. Being recruited into a botnet is probably the least worst fate in such a scenario. The far more worrying possibility is that an exposed asset will serve as an entry point into your network for ransomware, Emotet, TrickBot or any other number of trojans, or lateral movement by a targeted attacker. We are not helpless here, however. Device security is manageable provided you have visibility and enforce secure password protocols. If you’d like to see how SentinelOne can help improve the security of IoT and all other devices across your network, contact us or request a free demo.


