As news hit last week of a zero-day remote code execution (RCE) vulnerability in Google Chrome that only requires a user to land on or be redirected to a malicious website, we take a look at the threat posed by browser extensions. Search redirection is a favorite trick of adware extensions, as we found out in this analysis of an extension hosted in both Google’s Chrome Store and Apple’s Safari Gallery*.
Browser extensions are a staple of almost every user’s set up. Even in managed environments, users are often able to install extensions or ‘Add Ons’ without authorisation when these are sourced from trusted sources like Apple’s Safari Extensions Gallery and Google’s Chrome store. Of course, there’s nothing new about attackers exploiting the browser extension as a means to gaining a foothold in a target environment. The problem has been around for years: what is surprising is just how difficult it is to contain the problem. In this post, we take a look at the risks involved with what appears to be a harmless extension available for both Safari and Chrome. As we find out, not everything appears as it seems.

1 Click to Excessive Permissions
Both Apple’s and Google’s browser stores have offered an extension called 1 Click PDF, which at first sight appears to be a simple, free service that converts many different document formats to PDF. The extension, like most, can be installed with a single click and immediately gains some powerful privileges, none of which seem required for its advertised function. Safari indicates these in the browser’s Preferences:
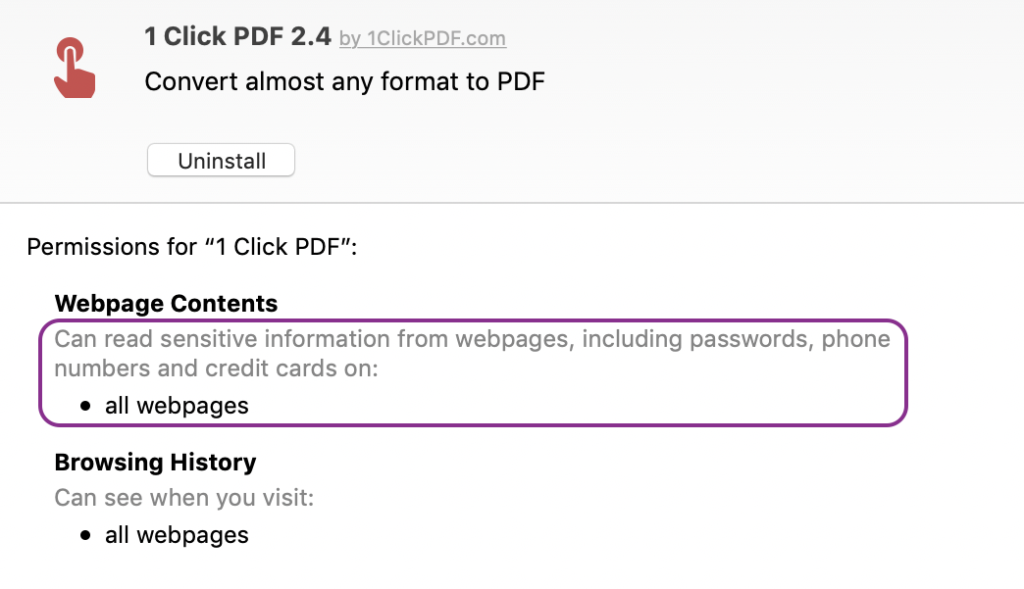
Google Chrome is a little more explicit and warns the user on installation that the extension has permissive rights. Of course, it still does not require anything other than a perfunctory click-through to achieve installation.
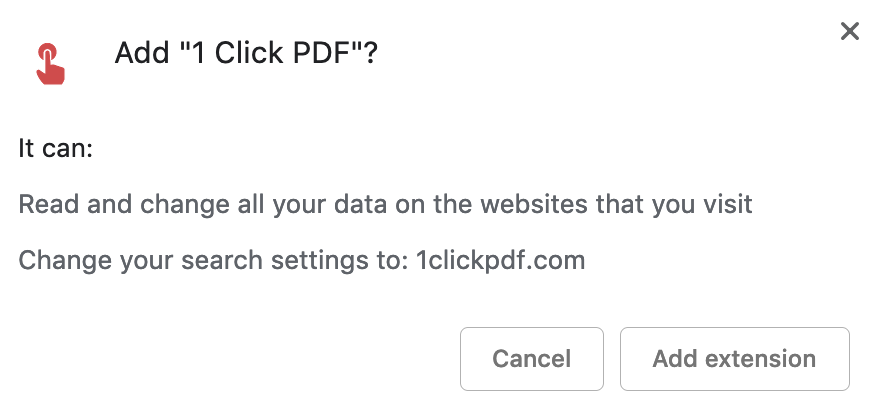
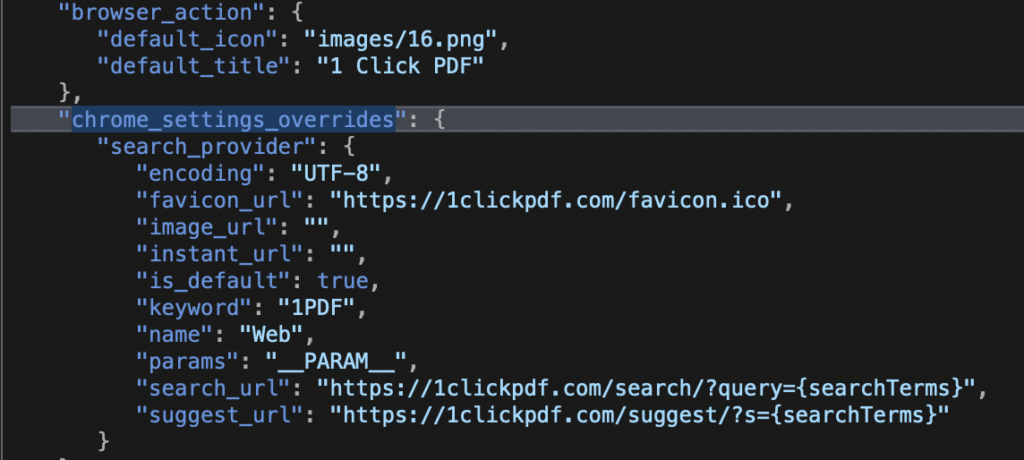
As “advertised” in the alert dialog, user searches made from the browser’s address bar will be redirected so that the developer can gather user traffic data and sell that on for personal profit. The code for this is plainly visible within the extension’s JavaScript.
A PUP for Your Troubles
While users should always avoid extensions that grant themselves unnecessary privileges like this, it is unfortunately fairly common. Even reputable vendors like DuckDuckGo were doing the same thing not so long ago, but the behavior of 1 Click PDF doesn’t just stop with permissive rights.
The Safari version has an added twist, which is that it redirects the user on first install to an advert for a potentially unwanted program (PUP).
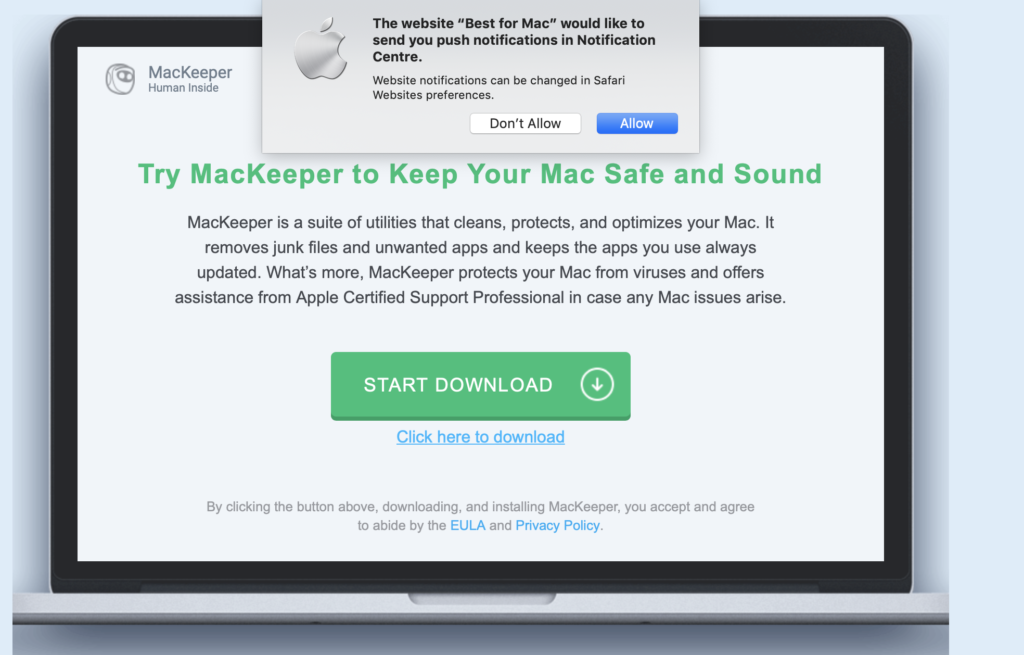
For those not familiar with this particular item, a trip to VirusTotal tells you all you need to know.
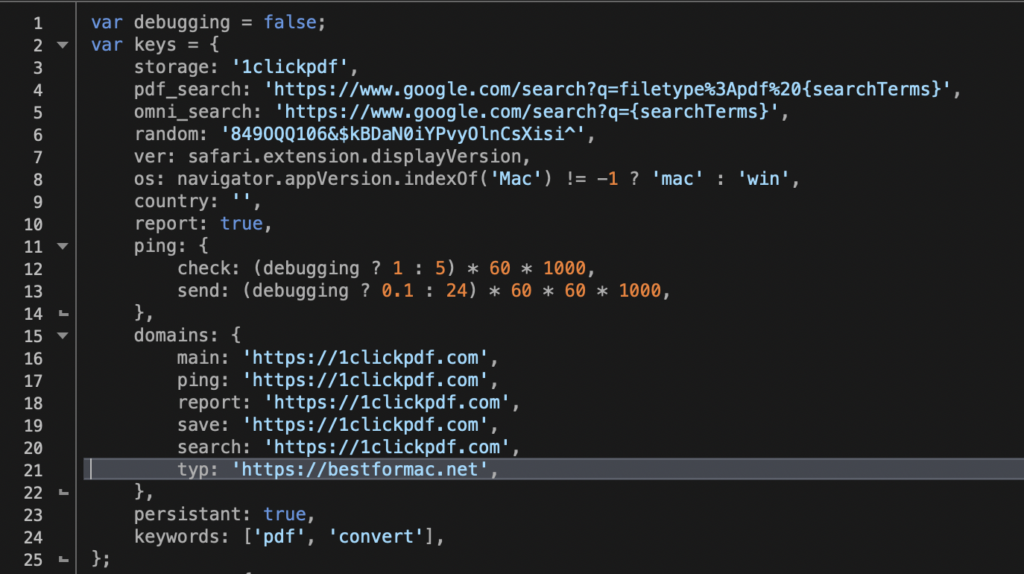
Interestingly, the Chrome version does not contain the code to redirect the user to the “bestformac” site, possibly to avoid falling afoul of Google’s Safe Browsing features. In code, we can see that the Safari extension sets the typ variable to bestformac.net to achieve the redirect, whereas the Chrome version leaves the value of typ at the default of 1clickpdf.com
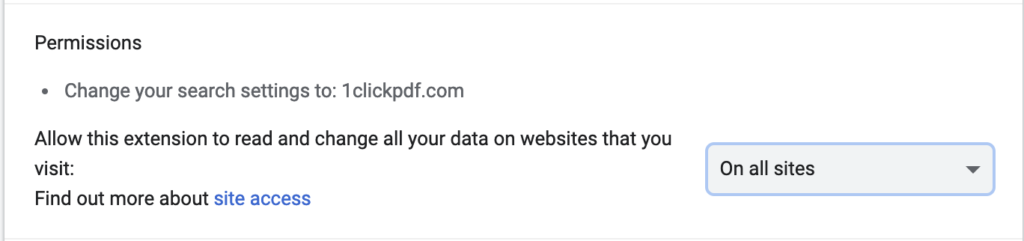
Even so, redirection is a core function of both extensions through search hijacking, and the possibility of the user landing on a maliciously-crafted webpage is a real concern. As the RCE vulnerability in Chrome shows, it’s possible for attackers to use a malicious site to escape the browser’s sandbox and execute arbitrary code, allowing full control of the machine itself. As most browsers’ built-in phishing and malware detection is also easily defeated, users cannot assume that the browser itself will keep them safe.
Data Collection – Anything Goes?
So far we have an extension that gives itself unnecessary permissions, changes search engine settings and tries to foist potentially unwanted software onto users. A little more digging turns up a few other causes for concern.
1 Click PDF’s website is remarkably spartan, but they do have plenty of legalese about EULAs, Privacy Policies and such like. That’s as it should be. The problem is, when you dig into those, it’s not clear how anyone would ever contact the company to take them up on any legal issues. The extension is apparently developed by “Algo Marketing” (misspelled in at least one place in their own documentation as “Algo Makreting”).
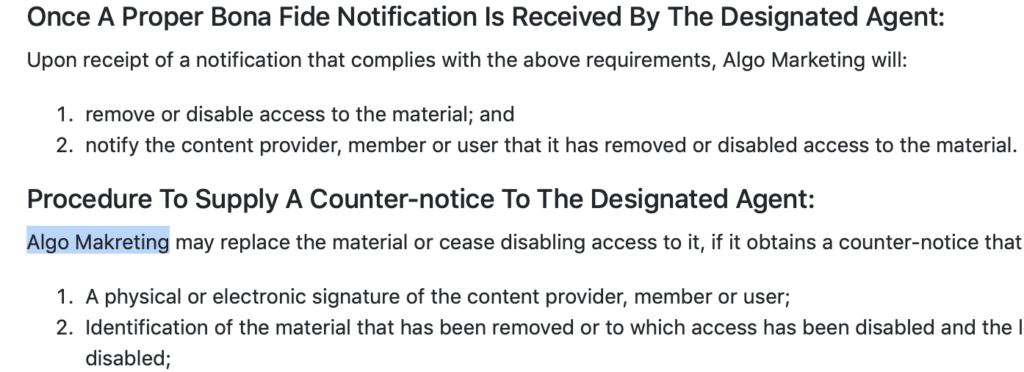
Every writer knows the irritation of the accidental typo, but for a company to misspell its own name in legal documentation suggests a lack of professional review, at least. Far more problematic is that there appears to be no way to contact “Algo” other than through an anonymous email address. There’s no postal address, no staff names, no telephone numbers and no list of company executives. Who are “Algo Marketing”? Despite digging through everything on their website (not to mention a reasonable bit of web searching), we haven’t the faintest idea.
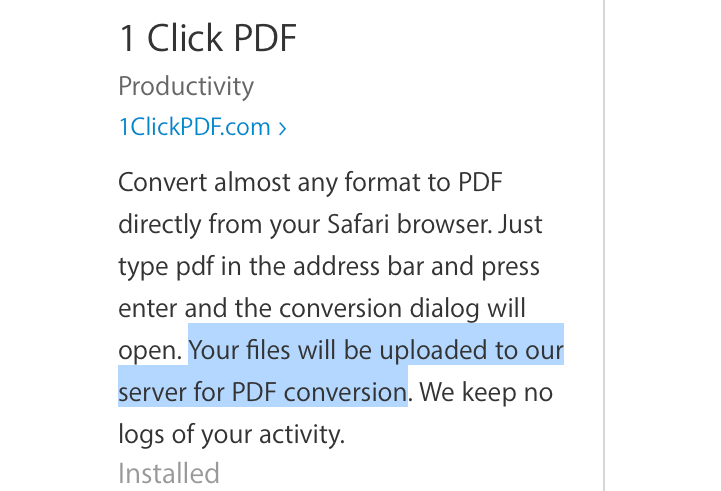
Equally worrying are the policies defined in the documentation. The files you want to convert are first uploaded to 1 Click PDF’s own servers. There is text in the EULA that claims these uploads are deleted after an hour, but there’s also text in the Privacy Policy that, after claiming the vendor “respects your privacy”, appears to show they do anything but. The policy indicates the developer may profile your system, including other software you may be running, and share any information they choose with their “partners and affiliates”. Clearly, users need to be aware that the content of any document they upload to 1 Click PDF for conversion could be shared with others.
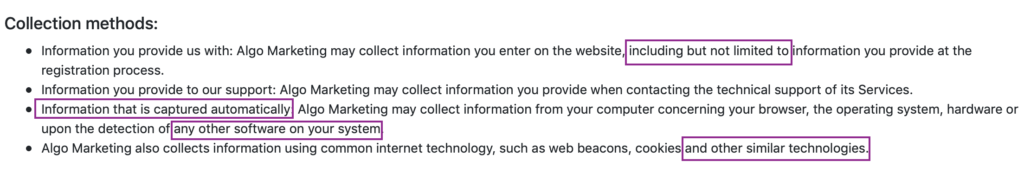
The various documents say that all partners will abide by the stated “policy”, but even given it’s extremely lax nature, since the only means of contacting those behind 1 Click PDF is an anonymous email address, it’s well-nigh impossible to check whether this company or its unknown “partners and affiliates” actually operate in accordance with their own stated policies. Trust without transparency and oversight is nothing more than fairy-tale security.
A Sign of the Times
Unfortunately, there’s nothing particularly unusual about 1 Click PDF’s business model. It flirts on the right side of the law by ticking all the necessary boxes, while at the same time engaging in behavior that is clearly worrisome for users.
Browser re-directions, data collection, profiling and promoting PUPs are clear indications that a vendor has little interest in user welfare and is only interested in maximizing revenues by any means possible. Of these threats, profiling and unwanted installs should be of concern to enterprise users.
As we’ve shown before, bypassing native OS blocking tools like Apple’s Gatekeeper is trivial business once a process has gained a foothold on the system. Google themselves have previously reported that telemetry from its own Safe Browsing feature suggests that Chrome issues around 60 million warnings per week for unsafe or unwanted downloads. Despite those warnings, based on use of Chrome’s Clean Up feature, they estimate that there are still tens of millions of unwanted software installations.
That all begs a couple of questions: what are all these programs doing? And do you have visibility into their behavior on your network?
Conclusion
In this post, we have taken a look behind a simple browser extension and noted how it can easily present a security risk to users. That risk can include data loss, user profiling and browser redirection. In many cases, extension behavior may completely bypass installed security tools unless you have complete visibility into your network traffic, including encrypted https protocol.
* Since first investigating this issue, 1 Click PDF cannot be installed from the Safari Extension Gallery, but at the time of writing it was still available in Google’s Chrome Store.


