A 2-part series looking at the technology behind macOS browser extensions and how malicious add-ons can steal passwords, banking details and other sensitive user data
Browser extensions are one of the easiest 3rd party modifications a user can make to a secure system, yet potentially one of the most dangerous. Many users view extensions as trivial little “applets” that offer some simple but useful extra functionality while surfing the web – blocking advertising content, allowing markup, filling form fields and so on – without realising just what immense power these extensions are granted.
In the first of two posts,, we’ll take a look at the security implications of Safari browser extensions up to and including macOS 10.13 and examine a case of a particular browser extension used in an adware campaign. In part two, we’ll cover how the security of Safari extensions has changed in macOS 10.14 Mojave to address some of these concerns.
Security Vulnerabilities
While the emphasis here will naturally be on raising awareness of how bad actors can exploit users through browser extensions, let’s start by pointing out the security implications involved even when using extensions from reputable and well-intentioned developers.
A good jumping-off point here would be the initiative taken earlier this year by DuckDuckGo to provide users with a browser extension to block ads and other tracking content. It’s a great idea from a trusted developer, but the extension had one fatal problem: users installing it were granting the extension privileges far beyond what it needed and which were themselves a security issue:
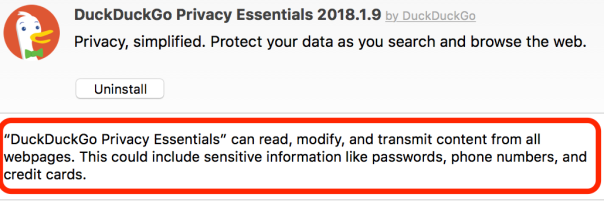
The extension’s claim to protect user data while they “search and browse the web” seems somewhat undermined by the fact that sensitive data like passwords could be exposed to the extension itself.
Unfortunately, it is not uncommon to see such privileges granted to extensions that don’t need them. As Apple’s Developer documentation invitingly states, extensions can do things like inject product ratings and reviews into websites, inject advertisements into webpages, download and inject scripts and modify web content. They can send notifications without explicit permission from the user, and they can run invisibly in the background.
That list of abilities sounds like a malware developer’s dream exploit tool, all the more so because there are several security vulnerabilities within Safari extensions that could either be intentionally exploited by malicious developers or unintentionally opened up by inattentive ones.
Extensions don’t need to include the scripts they use directly within their own package; they can source them remotely over http. If a developer doesn’t use the secure https protocol, that opens up the possibility of a man-in-the-middle attack, whereby a malicious script is inserted in place of the intended one.
It also means bad actors can develop malicious extensions that alter the behaviour of their extension after it’s been installed simply by changing the content of the script that is called over the http (or https) request.
Extensions are also supposed to respect Private Browsing, but it appears this is up to developers to implement. Apple documentation merely counsels that:
Your extension should not store any information about the user’s actions when in Private Browsing mode.
You can check whether a particular tab is in Private Browsing mode by querying the tab object’s private property (for example, safari.application.activeBrowserWindow.activeTab.private).
That’s quite a catalog of behaviour that’s enough to tempt any black hat, and it’s no wonder that “bad” extensions have been one of the primary tools of adware developers like Genieo and Spigot. As we’ll see in the next section, an extension can even prevent the user from uninstalling it without first removing an associated app, and that provides a ripe opportunity for tricking users into further compromising their own system.
The Intriguing Case of Pitchofcase
We recently observed a Safari adware extension called “Pitchofcase” which exhibited several interesting behaviours.
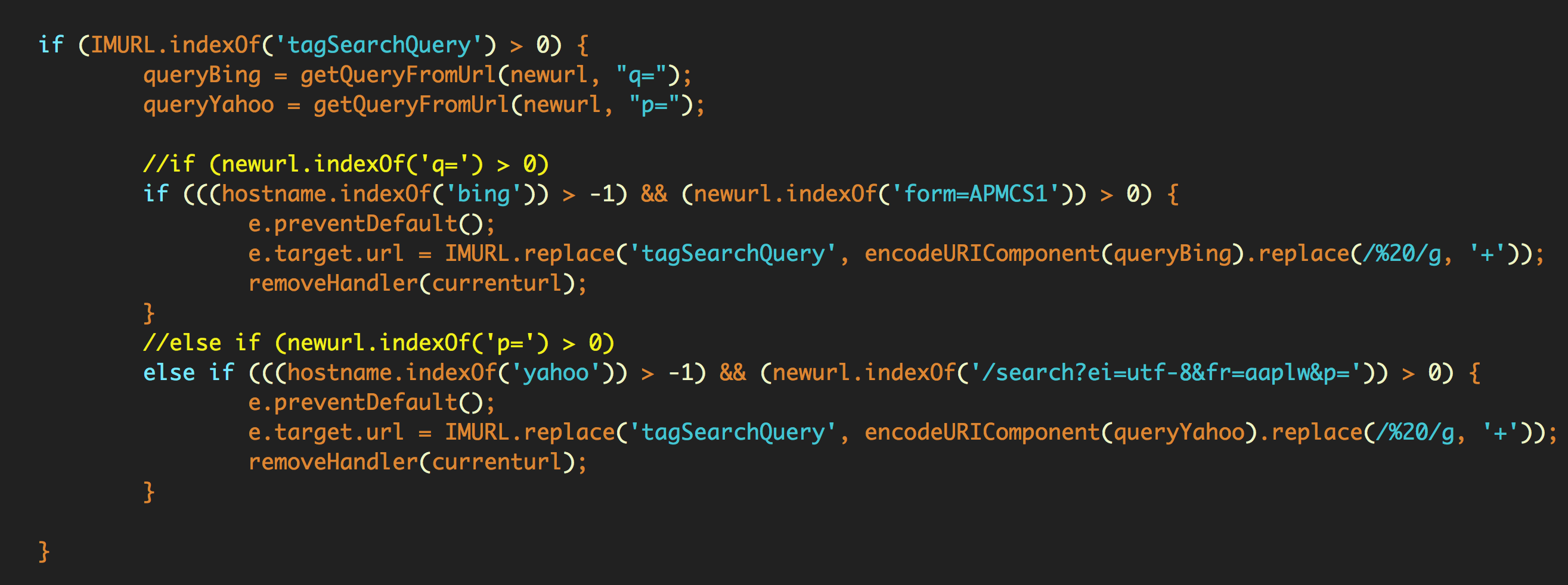
At first blush, Pitchofcase seems like any other adware extension: when enabled it redirects user searches through a few pay-for-click addresses before landing on pitchofcase.com.
http://searchv.oliverto.com/?b598a1d361f67b08aeee82e41686cd1a=FVNQWlVbFAAeXFNRWAFUV1dXV1gBUl9TUFBKQFwLUQFWWwAADAADXF9QUQxQVgNYVAUKU1VXWwFRDFRbB0EE&spt=ext&q=tagSearchQuery
The extension runs invisibly in the background without a toolbar button or any other means to interact with it.
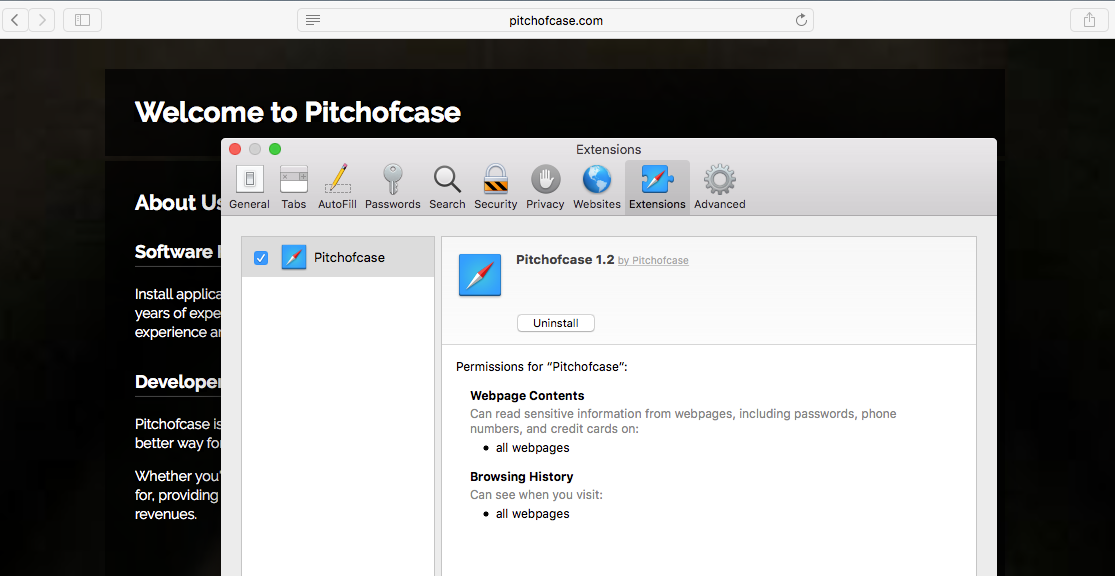
In the image above, note the permissions the extension gains. It’s worth pointing out that these are gained without elevating privileges and only require the user to click “Trust” from the same user alert that appears for every extension regardless of its permissions:
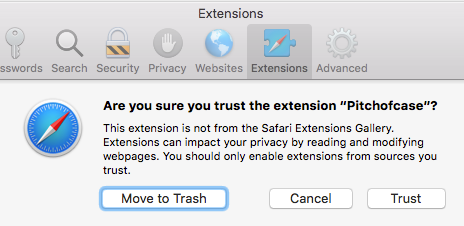
Granted the alert contains informative text outlining the consequences, but it’s unfortunate that macOS, through Safari, allows this level of privilege without password authentication.
Pitchofcase starts to get interesting when we try to uninstall it. Clicking the ‘Uninstall’ button doesn’t remove the extension as expected, and instead throws the following alert:
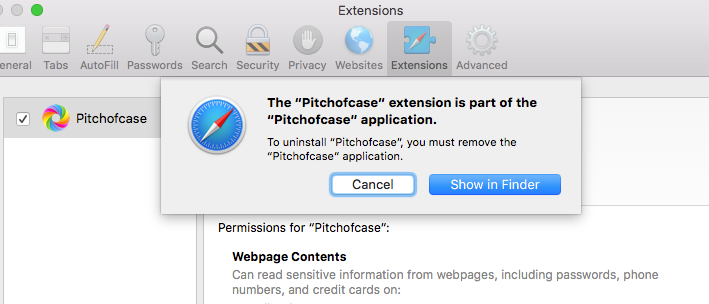
This is unusual, but not unheard of. Some perfectly reputable apps force particular extensions on their users in the same way (Parallels Desktop, for example, which insists on installing an ‘Open in Internet Explorer’ extension in Safari). Users can disable the extension without issue, but removing it requires removing the parent app.
Clicking “Show in Finder” reveals the app’s location, and helpfully, an Uninstaller:
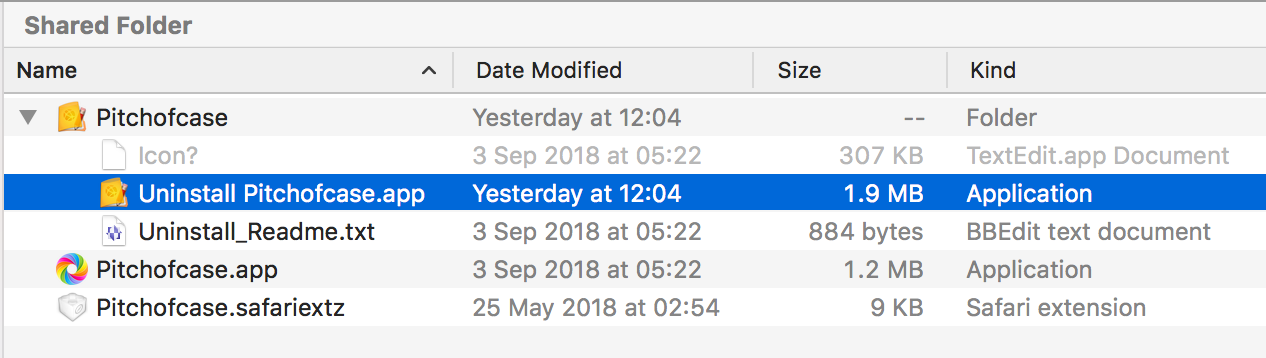
At this point, the security-conscious user might be interested to see how the Pitchofcase.app, Safari extension and Uninstaller fare on VirusTotal. The app comes up ‘clean’, but the Uninstaller sets off alarm bells:
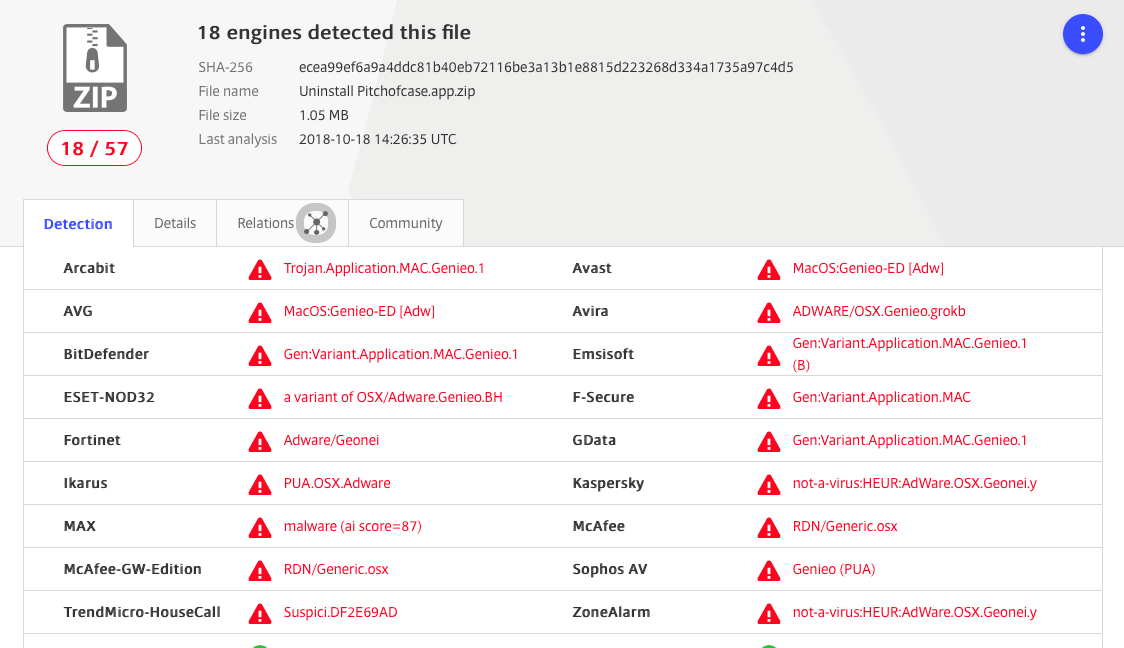
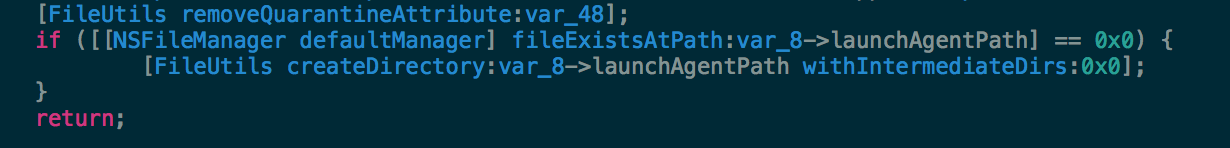
Since our main topic here is Safari extensions, we won’t take too much of a deep dive into what the Uninstaller is up to, other than to say that examination of the code reveals it’s clearly more interested in installing persistence agents:
and exfiltrating user’s browser history:
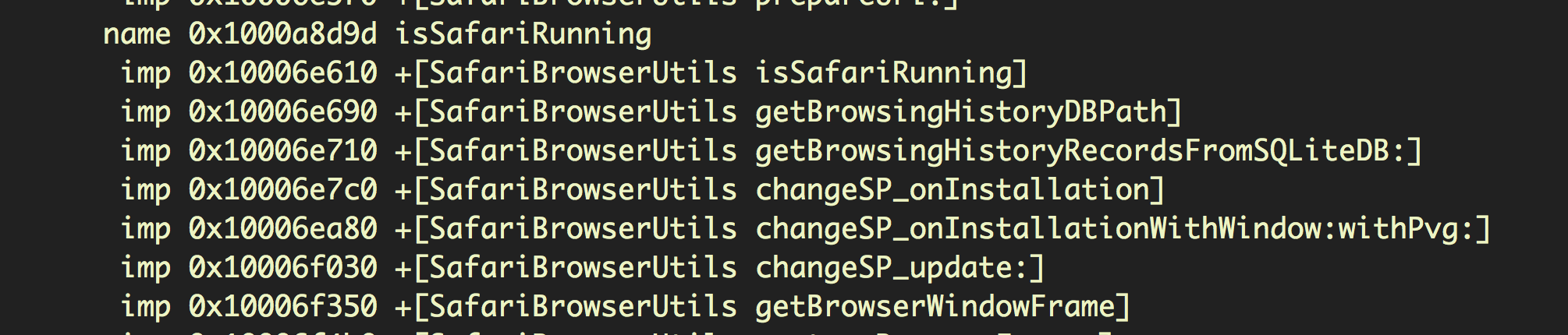
than it is in doing its supposed job as an uninstaller.
However, use of the Uninstaller as an infection agent is a clever trick that dovetails with the inability to remove the extension without removing the app. The extension itself, as we’ll see, is relatively harmless, and appears to be merely a ruse to get the user to run the Uninstaller.
Inside a Safari Extension
The Safari extension itself raises a few warnings on VT, but these are immaterial, as its the ‘clean’ app that’s installing the extension. Let’s take a look inside the extension and examine its behaviour.
Safari extensions are just compressed files, so in order to look inside one, the first thing we need to do is find out what kind of compression it uses with the file command:
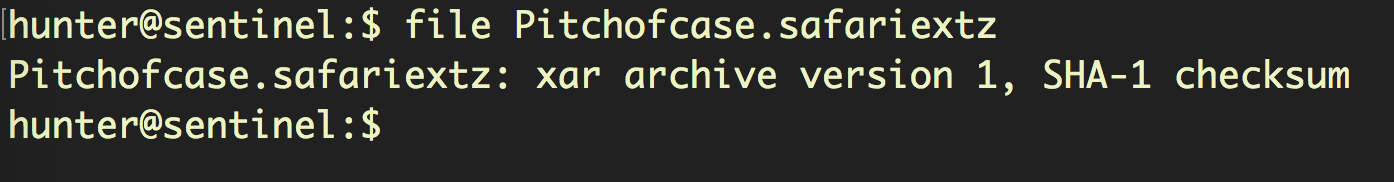
In this case, it’s xar format. Knowing that we can now rename the file and unpack it:
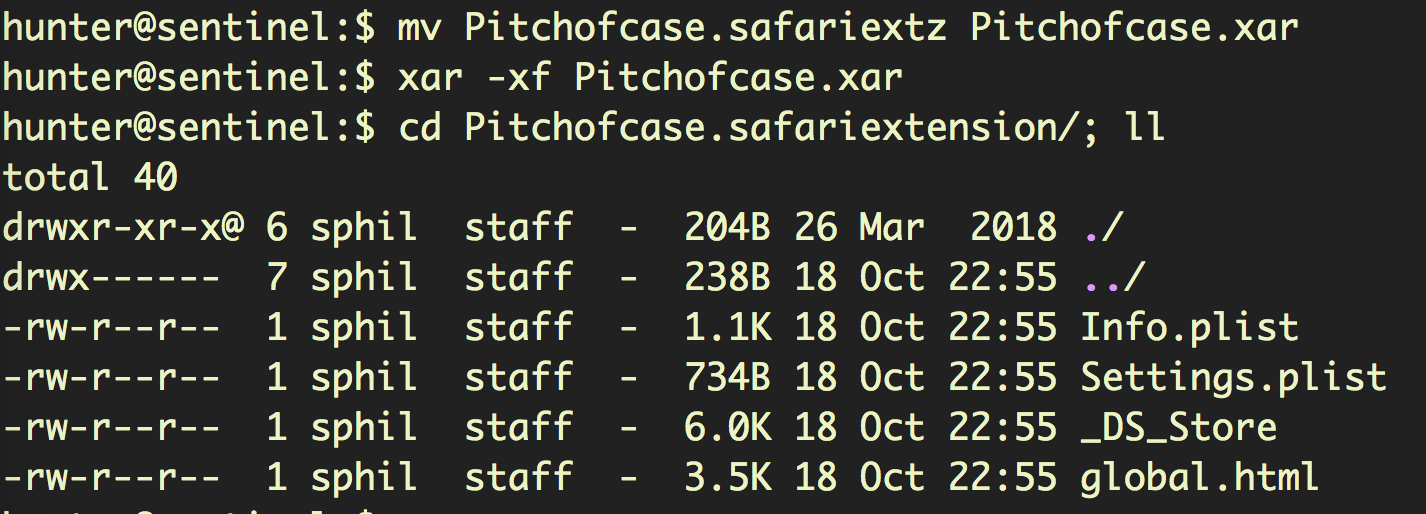
The global.html file is our first stop. This file is optional in Safari Extension architecture, but when included it’s the place for, among other things, loading one-time resources like the logic or data used by injected scripts.
In this case, we can clearly see the intent:
And in our next stop, the Info.plist makes it clear the extension wants to see secure pages, too:
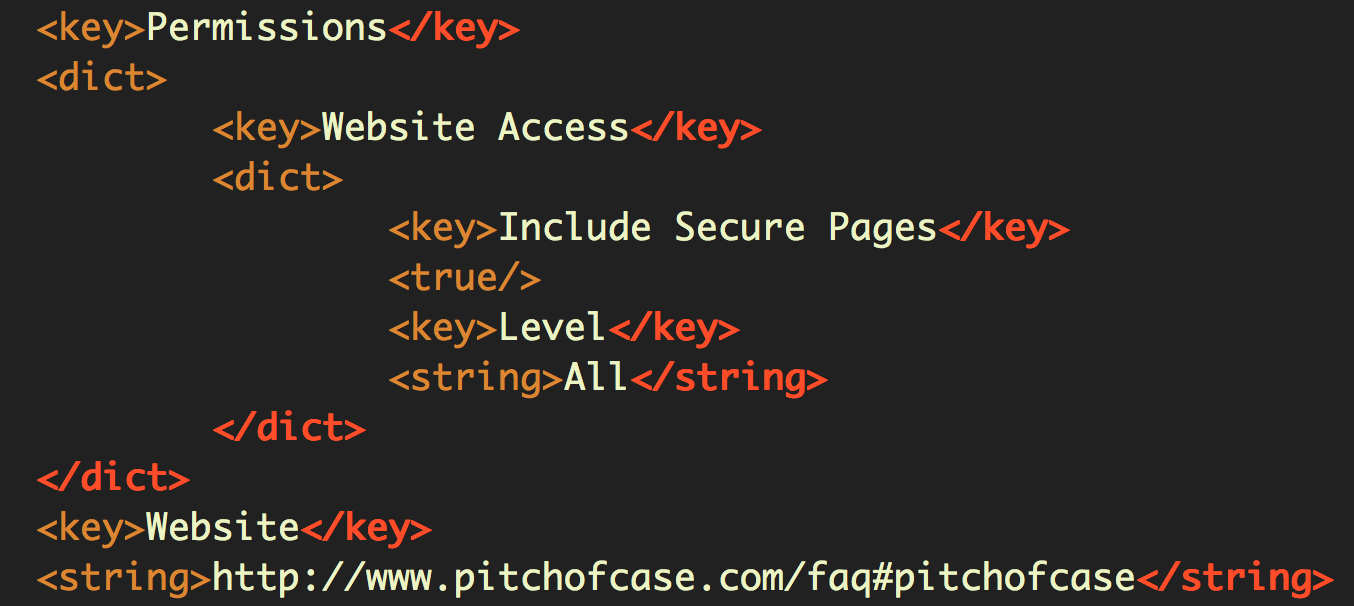
While this may be concerning, the most notable thing about the contents of the extension is the lack of any of the usual assets that are often packed into these browser add-ons. There are no dedicated JS tracker scripts or helper functions, and no attempt to, say, execute malicious code via the eval method. Compared to most extensions (both legitimate and illegitimate), Pitchofcase is untypically spartan.
And that brings us back to the requirement to remove the app in order to uninstall the extension, and the alarm-ringing capabilities of the Uninstaller. Pitchofcase is clearly a well-thought out trick: install a mildly annoying but largely useless extension, and then dupe users into running a malicious uninstaller in order to remove it.
Removing Pitchofcase Safely
There’s good news here for users that strictly follow the text of the dialog alert after clicking the ‘Uninstall’ button in Safari. It’s true that the only way to remove the extension is to remove the associated app, but remove doesn’t mean uninstall.
Users should ignore the supplied Uninstaller.app, and simply move the Pitchofcase.app and all other components – including the Uninstaller – straight to the Trash. Upon doing so, the extension is also removed.
The developers, unusually and cleverly, are banking on catching out users who follow the oft-repeated advice to always use a developer’s uninstaller when available to remove apps. It’s usually good practice when dealing with a complex installation from a trusted developer. In the case of Pitchofcase, it’s an artful dodge intended to steal your data.
Coming Next…
In Part 2, we’ll continue to explore how macOS extensions have changed in 10.14 Mojave and what users need to know about staying safe when adding them to the latest version of the Safari browser.


