The Good
This week, two high-profile Chinese nationals were charged in relation to a series of large-scale cyber attacks. The unsealed, 11-count indictment alleges that the two individuals (Dong Jiazhi & Li Xiaoyu) participated in theft and intrusion of numerous companies spanning the globe, all at the direction of the Chinese government.

It is reported that the actors did not act exclusively for Chinese government entities, but carried out attacks both for the GSSD (Guangdong State Security Department) and MSS (Ministry of State Security) and for their own personal profit. While the alleged activities span many years, some of the more recent attacks include the intrusion of U.S.-based companies researching possible treatments and vaccines for COVID-19.
The two individuals are also alleged to have provided the MSS with valuable information pilfered from the victims of their attacks. This includes “personal data, such as the passwords for personal email accounts belonging to individual Chinese dissidents”. According to the indictment, the TTPs involved covered the spectrum of common TTPs that we see in modern attacks. A potent combination of commercial off-the-shelf (COTS) tools, LOTLbins, and more specialized tools such as China Chopper web shell were used. At times, the indictment almost reads like an IR engagement report.
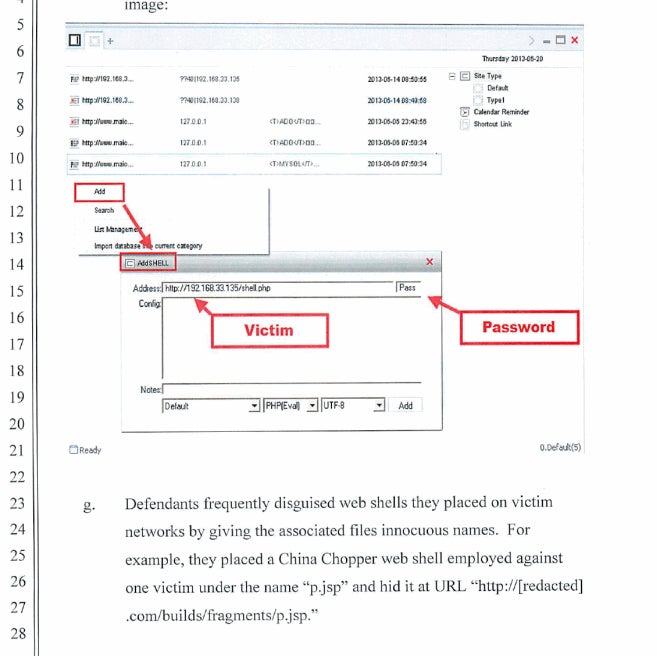
This indictment is a huge victory for law enforcement and the defense industry in general. The more light that can be shed on these activities the better. It also helps the public gain a better understanding of some of the more commonly utilized TTPs by actors of this ilk. Kudos to those involved with the investigations. We encourage all to read though the Department of Justice’s press release and indictment.
The Bad

It has been another busy week for state-sponsored (malicious) activity out of North Korea. Details have emerged around a new multiplatform and multi-purpose framework referred to as MATA. Named for the supporting infrastructure (MataNet), the toolset consists of multiple components. The primary components of the MATA framework are the Loader, Orchestrator, and an assortment of Plug-ins. Possibly the most interesting aspect of this framework is the support for multiple platforms. Researchers at Netlab reported the Linux version of MATA in December 2019 (then referring to the tool as Dacls). At the time, it was considered to be a self-contained RAT with fairly robust support for plug-ins. In April 2020, a macOS port of the Linux Dacls tool was discovered on VirusTotal.
The MATA framework has been linked to North Korean APT group Lazarus though filenames and metadata contained within the orchestrator components, some of which have also only been seen in other tools also tied to the Lazarus group. There also appears to be some infrastructure overlap between the infrastructure used by the MATA framework and other tools directly tied to Lazarus. The discovery of just how broad and far-reaching the MATA framework is should be seen as par for the course with regards to the modus operandi of the Lazarus group.
The Ugly
Unfortunately, it is difficult to go a week, or even a day, without news of a high-profile ransomware attack.
According to latest publications, Argentinian Telecom Company is the Latest Victim of REvil Ransomware, with 18,000 Endpoints Infected, Since REvil has also been known to extort victims, through threats to release the ransom to blackmail or sell it off for the highest bidder, confidential data from Telecom Argentina are possibly exfiltrated, but REvil has taken no measures to confirm this.
According to current reports, the initial payload was delivered via phishing email opened by an employee. Once a foothold had been achieved, the attackers were able to take over administrative accounts, move laterally, and ultimately disrupt any host they could reach with the ransomware payload.
At the time of this writing, Telecom Argentina has continued to refuse to pay the reported $7.5 million dollar ransom. Adding further complication to the attack, REvil is one of many ransomware families that is publishing victim data in the event of “non-compliance”.
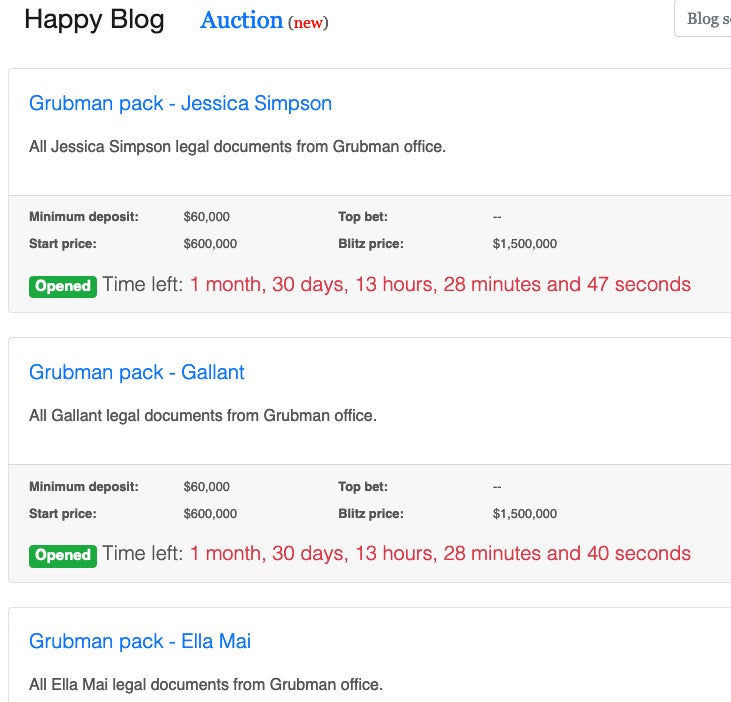
While Telecom Argentina currently does not appear on the blog maintained by the actors behind REvil, only time will tell if the company end up finding their data up for auction by the aggressive thieves.


