The Good
This week sees another victory for law enforcement in the fight against cybercrime. An approximately two-year long investigation dubbed ‘Operation Lyrebird’ has culminated in the capture of an individual with a long trail of fraud and cybercrime offenses. The suspect was taken into custody by the Moroccan police according to INTERPOL. The individual, who goes by the hacker alias “Dr HeX”, is tied to a number of activities including credit card fraud, website intrusions, phishing attacks and more. He is also known as the creator of a multi-script tool called ‘ZombiBot’, which exists in various versions.
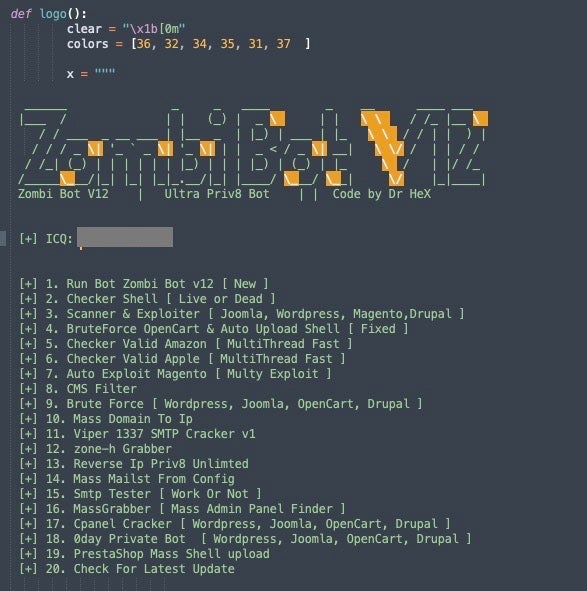
“Dr HeX” has been active, in current capacity, since at least 2009, but more recently was known for phishing kits. These ‘kits’ are sold to low-level actors for very little money. They serve to simplify and automate as much of the phishing attack process as possible. Typical phishing kits include templates for masquerading as various well-known websites such as bank login pages, shopping login pages, and company portals) along with the requisite scripts and config files to properly trick and redirect victims. These items are often sold in open forums, Telegram channels and the like.
During the course of their investigation, investigators were able to follow a rather direct trail of OSINT clues to identify “Dr HeX”. Once they tied the ‘Dr HeX’ moniker to a valid email address, they were quickly able to identify the individual and confirm his ties to multiple additional phishing and fraud campaigns. Hats off to the Morroccan Police, INTERPOL, and Group-IB on the successful operation.
The Bad
It did not take cybercriminals long to begin using the Kaseya attack as a social engineering lure. Within two days of the incident, spam campaigns were observed which lure victims into installing Cobalt Strike payloads masquerading as security updates from Kaseya. From that point, anything is possible with regards to data theft or additional code execution.
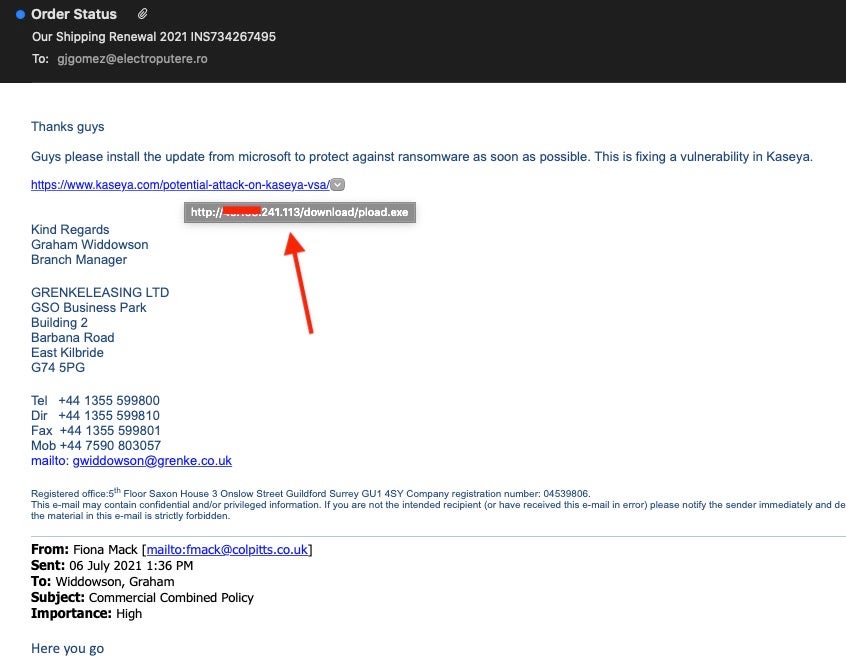
The scope of this attack is quite large, as is the accompanying flurry of information for, about, and around it. The attackers are very much preying on the ‘state of confusion’ (or shock for some). At the end of the day, we can always expect the adversary to capitalize on anything at all times.
Also this week, our researchers discovered a potential new RaaS-in-the-making in the form of something calling itself “EP918” Ransomware service. The actor(s) behind this early-stage setup claim to be offering a “powerful FUD ransomware” for between $300 and $500. At the lower tier, the ransomware is available as a “script to be embedded in a website”. The upper tier offers buyers a unique ransomware payload embedded in a malicious PDF file. It is then up to the buyer to distribute the malware as they see fit. Both Bitcoin (BTC) and Monero (XMR) payments are supported. While many of these underground Ransomware-as-a-Service offerings ironically turn out to be scams aimed at (would-be) criminals, others are genuine ransomware services that are later seen in real-world attacks. SentinelLabs will be keeping its eye on this one.
The Ugly
If there is one event that dominated our landscape this week, it would have to be the wide-reaching attack against Kaseya VSA. Attackers leveraged a sly combination of LOLBins, Microsoft Defender and a zero-day exploit to distribute the REvil ransomware to thousands of endpoints. This was a well-staged attack, with very deliberate timing as well (holiday weekend in the United States). This attack became quite complex rather quickly, affecting both Kaseya and the connected customers they provide services to. There is a level of trust there that these attackers are taking direct advantage of.
It is believed that this is one of the largest mass-scale ransomware-deployments to date. REvil has yet to fully ‘comment’ apart from a very short update on their public “blog” in which they claim “more than a million systems were infected”. For a mere $70 million (later revised to $50 million) in Bitcoin, the gang offer “everyone will be able to recover from attack in less than an hour”.
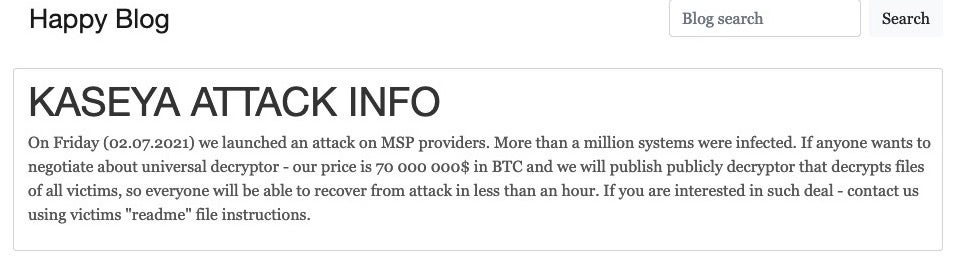
Following the initial incident, Kaseya has been releasing frequent updates via both video and their blogs. At this stage most of the services for On-Premise customers are back online and SaaS services should not be far behind. That said, the issue is still unfolding and there will be much to learn in the coming weeks.
Incidents like this illustrate the need to have full visibility and understanding into your infrastructure, shared and otherwise. A good deal of security is built on a certain level of assumed “trust”. It is wise to not take that trust for granted and continually review your ties and connections to third party dependencies. Understand and analyse your ingress points from both the outside and from the perspective of connected vendors and partners. The action being taken on this issue has been ‘good’. But the ‘ugliness’ here lies in the knowledge that this will not be the last attack of this nature.


