
The Good
With missiles flying in the Middle East and everyone on high alert for new Iranian cyberwarfare activity, good news would appear to be in short supply as we come to the end of our first full week of 2020. Greeted with a somewhat lukewarm response, Facebook have announced a new ban on deepfake videos. The company says it will remove content that has both been manipulated to mislead viewers into believing that a subject “said words they did not actually say” and that is the product of machine learning. While the policy is welcome insofar as it goes, it doesn’t cover videos that remove or rearrange the order of words, nor does it include editing that isn’t generated by machine learning algorithms, both far more common ways of manipulating media. Nonetheless, we’ll still give Facebook a something out of ten for this as good news, particularly as the company has partnered with the Reuters news agency to provide a free course to help journalists and others identify and tackle manipulated media.
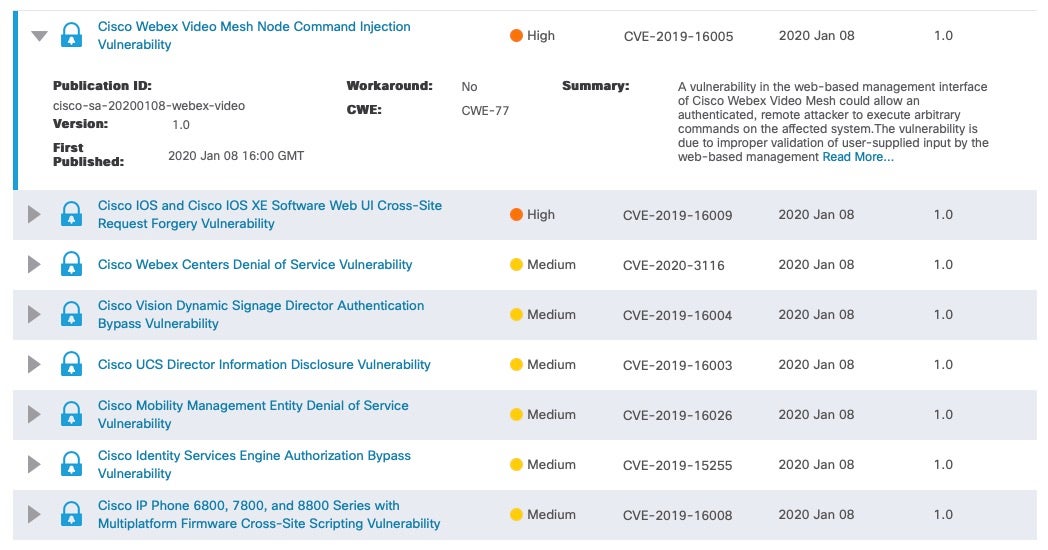
Meanwhile, Cisco kicked off the New Year by plugging 14 vulns, including two high severity flaws involving remote code execution (RCE) and cross-site request forgery (CSRF), which is good news for customers who patch often and patch early. The RCE bug affects the web-based management interface of Cisco’s Webex Video Mesh product and is caused by improper validation of user input.
The Bad
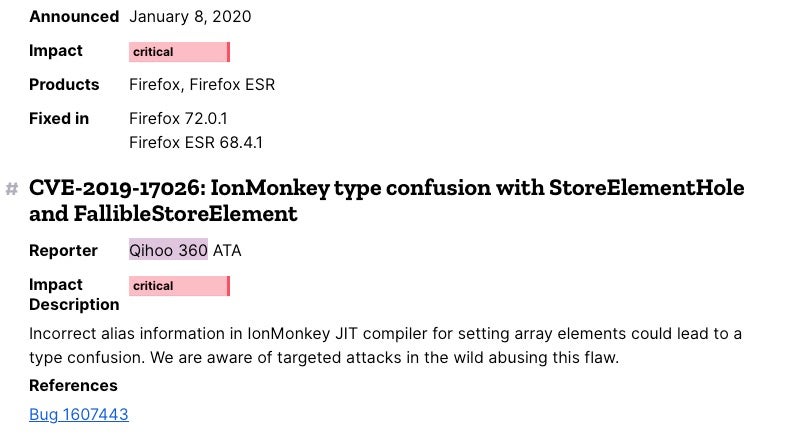
Patching vulns is good, but those being actively exploited in the wild is definitely bad news for victims and worrisome for everyone else. Mozilla this week announced a new version of their popular free Firefox browser, updating the latest stable release to 72.0 on January 7th. Hardly had users been given time to check out the list of new features when hard on its heels came a critical patch in 72.0.1 on January 8th. Mozilla gave few details, saying only that a bug designated as CVE-2019-17026 was a result of a type confusion in its JIT compiler. Not for the first time, an urgent update was required as the vuln was being actively exploited in targeted attacks in the wild. Adding to the worry is that the Chinese researchers credited with the discovery, Qihoo 360, posted and then shortly after deleted a tweet claiming to have found an associated Internet Explorer zero day also being actively exploited in the wild. More details on that as soon as they become available.
According to a statement on Monday, what appears to be a targeted ransomware attack hit elite German cycle maker Canyon over the holiday period, encrypting both software and servers. While there is no information about the amount of the ransom demanded or whether the company chose to pay, the company did say that “experts from the field of IT, forensics and cyber security were able to quickly analyze and control the attack”. The attack is expected to cost the company at least in terms of lost production and missed delivery deadlines.

The Ugly
Insider threats always top our list of cybersecurity ugly, so Amazon and their controversial IoT Ring products are first up this week in news that over a period of four years, a number of employees had been snooping on user videos. The company said that employees in the Ukraine and other non-US locations had access to Ring video feeds from other employees, contractors and friends and family of employees and contractors, as well as Ring videos that any user chooses to make public but which may contain information they did not intend to be viewed. The company noted four incidents of employees accessing user video data that was not necessary for their job functions. Amazon says in each case the employees were terminated.
We’ve all seen vendors load bloatware onto retail PCs and smartphones before, but a vendor pre-installing unremovable malware on a low-cost phone funded by the U.S. government is something else. According to research posted this week, the $35 government-funded Unimax U686CL comes pre-installed with known riskware, associated with a developer they say has been caught creating backdoors. It also carries its own “heavily obfuscated malware” within the phones Settings.app and drops malware the researchers dub “Android/Trojan.HiddenAds”. Removing the Settings.app effectively bricks the phone, so remediation is out of the question.


