The Good
Every time cybercrime is disrupted, we applaud, but when an entire fraudulent supply-chain is ruined, we’re even happier. In a recent operation, Polish and Swiss law enforcement authorities, with the help of Europol and Eurojust, took down a hacking group involved in distributing stolen user credentials, creating and distributing malware and hacking tools. The group, known as InfinityBlack, had two revenue streams. The first was malware development and sale, focusing on credential stuffing malware. The second, more lucrative, was the use of these same tools to steal credentials and sell them.

The group specialized in creating ‘combos’ of login credentials, mainly of loyalty programs. These were sold on the group’s portal, and utilized by less-skilled cyber criminals, who accessed client accounts and exchanged these points for high-end electronic devices. Law enforcement agencies conducted a cross-border operation leading to the arrest of five individuals in the canton of Vaud, Switzerland. These were the lower-level operators, capitalizing on the stolen data. Their arrest and the seizure of electronic communication equipment led to the arrest of the InfinityBlack members, who were located in Poland. As positive as this whole operation is, it is also testimony to the creativity and audacity of cybercriminals, who manage to find new ways to abuse the digital economy. The fact that this group was unmasked and arrested does give hope that it will deter others from conducting such activities in the future.
The Bad
Remote collaboration and conferencing tools have been under a highly critical microscope as of late. By now we have all heard of the various pros and cons with regards to Zoom, Skype and others. This week, researchers at Abnormal Security disclosed a potentially dangerous attack against Microsoft Teams. This particular impersonation flaw is centered around the automated email notification functionality within Microsoft Teams.
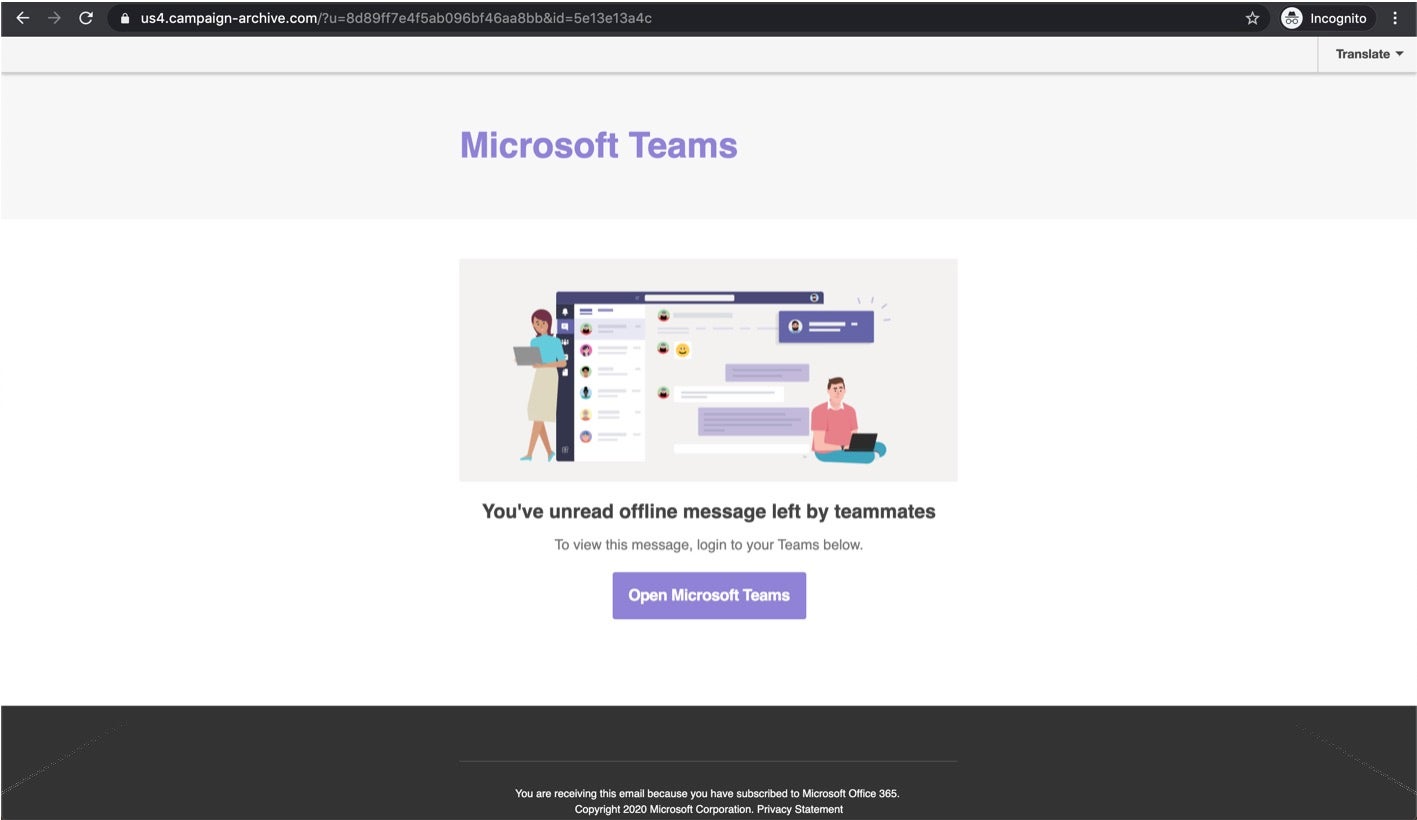
Attackers can target potential victims via specially-crafted email messages. This is actually a compound attack. One component of the attack relies on very well-crafted and convincing phishing emails, paired with equally convincing poisoned webpages. According to reports, the fake Teams notifications are a ‘notch above’ the standard phish and it appears that the actors behind the attack went to great lengths to make the campaign as convincing as possible. This includes registration of new domains proposed for the attack. The second part of the attack is the credential-stealing payload itself. The attackers leverage multi-layered URL redirects, which ultimately lead the victim to a false Office 365 login page (while masking the real hosting urls as much as possible). Once the victim logs into the cloned site, the attackers have achieved their goal.
The Ugly
Nothing is more upsetting than cybercriminals obstructing the valiant efforts of medical crews and researchers trying to treat and find a cure for COVID-19.
This week, a ransomware attack hit Fresenius, Europe’s largest private hospital operator based in Germany. Employing nearly 300,000 people across more than 100 countries, the group provides care and dialysis treatment to patients experiencing kidney failure, which is even more acute nowadays because many COVID-19 ventilated patients develop acute kidney injury and later require dialysis.
The attack was allegedly Snake ransomware. The full extent and damage are as yet unclear, but it seems it did not affect patient care. Fresenius has notified the appropriate authorities and is working to resolve the incident.
Ordinary cybercriminals are not the only ones attacking this critical sector. In an alert issued earlier this week, The United States Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) noted that APT groups are exploiting the Coronavirus Disease 2019 (COVID-19) pandemic as part of their cyber operations. The targets of these attacks are healthcare organizations, pharmaceutical companies, academia, medical research organizations, and local governments. The goal of these attacks is to collect personal information and intellectual property (some of which may be related to possible COVID-19 cures or vaccines). The attack methods include scanning external websites of targeted companies and looking for vulnerabilities in unpatched software such as Citrix and virtual private network (VPN) products from Pulse Secure, Fortinet, and Palo Alto. Another method used is password spraying to compromise accounts and move laterally across the network to steal additional data and enhance their persistency.


