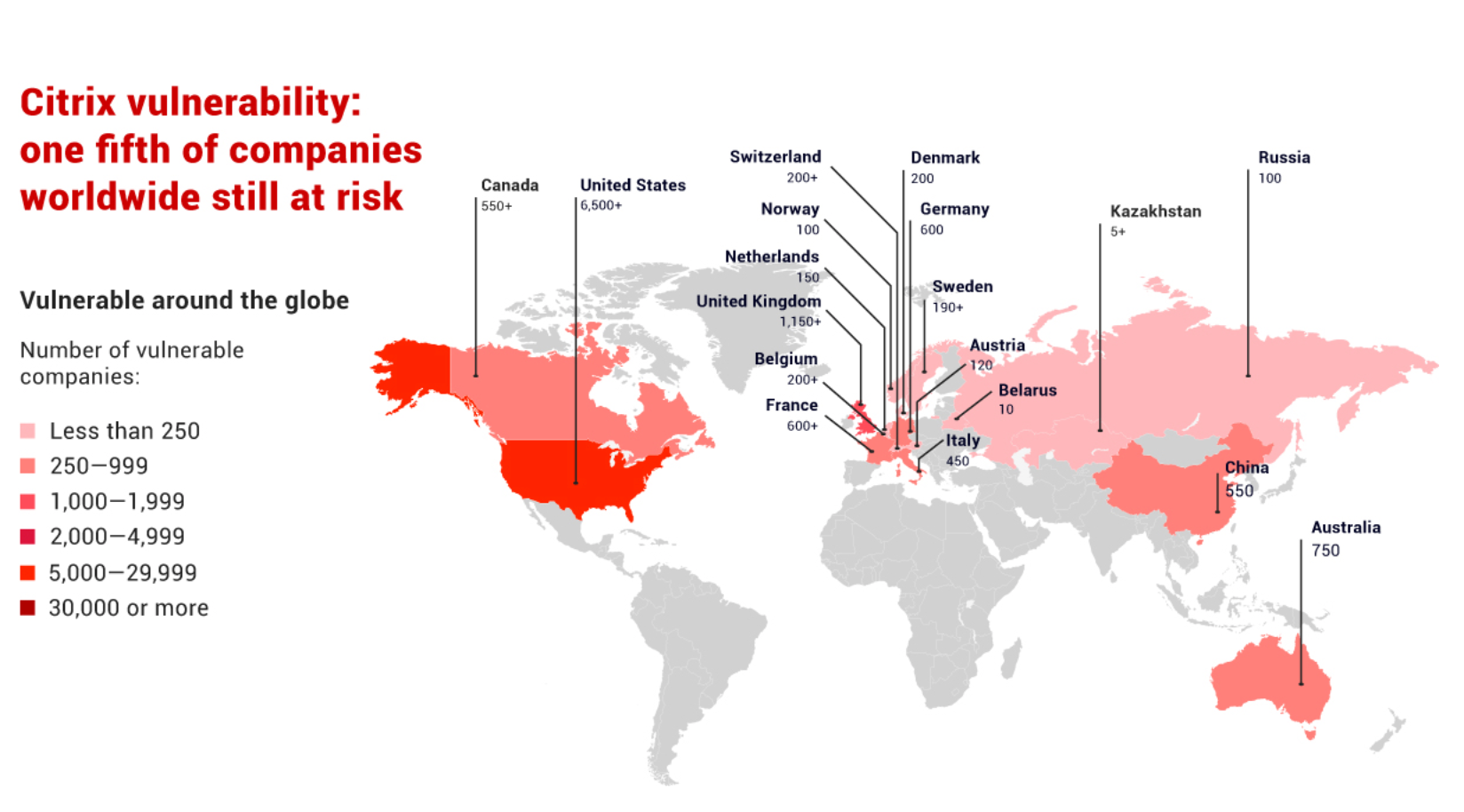
The Good
Welcome news this week as Citrix’s campaign to get businesses aware and on-task patching CVE-2019-19781 over the last two months has really borne fruit. It’s now estimated that 80% of all internet-exposed machines with the flaw have been patched to date. That only leaves the 20% of unpatched boxes to go, but the admins responsible for them had better get a move on. There’s already “plug-and-play” exploits for the bug publicly available.
It’s been a great week for vulnerability fixes. 99 is the astonishing number of bugs Microsoft have addressed in this week’s Patch Tuesday, including a fistful of RCEs like CVE-2020-0674 and CVE-2020-0729. Adobe also crushed 12 critical CVEs (including CVE-2020-3742, CVE-2020-3752, and CVE-2020-3751) plus five other less severe vulnerabilities in Reader and Acrobat, and one critical CVE in Flash Player (CVE-2020-3757). Elsewhere, in a good advert for bug bounty programs, SoundCloud fixed a number of critical bugs that could allow attackers to take over user accounts, although the company said there was no evidence of these bugs being actively used in the wild.
The Bad
If there’s one thing that the Emotet trojan and malware loading platform will be remembered for in cyber history, it’ll no doubt be its sophistication. Adding to that rep is news that the ubiquitous malware loader has been making use of a Wifi spreader. According to researchers, previously Emotet was thought to spread purely via malspam and infected networks. It now turns out that Emotet can also infect nearby wireless networks if the networks use insecure passwords. Essentially, the Wifi-spreader module enumerates the Wifi networks in range of any Emotet-infected machine, and then tries to brute force the passwords of each from a built-in password dictionary.
Business Email Compromise (BEC) cost U.S. companies a combined total of $1.7 billion in 2019, according to the FBI’s “2019 Internet Crime Report.” The huge scale of cybercrime is worth pausing over: those losses came from a staggering 23,775 targeted attacks. “By using an email address similar to a trusted company address, criminals can trick an employee into giving away valuable information at almost no cost,”, the FBI said in its report. If you still think your business is flying under the cybercriminals’ radar, those figures are a bullhorn telling you to think again.
The Ugly
American accusations that Huawei spies for the Chinese government are being viewed with a certain amount of chutzpah this week after news broke that the U.S. and German intelligence agencies have been spying on over 100 other nations, including allies, for decades through deliberately weakened encryption. It turns out that Crypto AG, a Swiss firm manufacturing encryption devices, was secretly owned by the CIA. While the secret operation led to many intelligence coups against U.S. enemies, it also raises some worrying ethical issues. According to the Washington Post, these include:
“the deception and exploitation of adversaries, allies and hundreds of unwitting Crypto employees. Many traveled the world selling or servicing rigged systems with no clue that they were doing so at risk to their own safety.”
The success of the program probably helps account for the US government’s penchant for haranguing the likes of Apple to build backdoors into their own encryption products. It’ll be interesting to see whether this case serves to strengthen or weaken public perception on the legitimacy of that stance.

Adding grist to the mill, prosecutors have held pretty compelling evidence to obtain a conviction against this suspected pedophile for some time, but they were determined to also examine his computer hard drive. The problem was the alleged offender either couldn’t or wouldn’t disclose the password for the encrypted disk even after being ordered to do so by a judge, so he’s been sitting in prison for the last 4 years on a contempt of court charge. That was until this week, when a federal appeals court ruled that 18 months is the maximum jail term for contempt as a result of refusing (or forgetting, as the defence would have it) to provide a decryption password. That could be either good news (the government can’t indefinitely imprison, say, a journalist) or bad news (the government can’t indefinitely imprison, say, a pedophile, either) depending on how you look at it, so we’ll file this under ‘ugly’ for now. The “eww” factor will certainly vary from case to case, but one thing is for sure: it’ll be interesting to see how strong that precedent proves to be when the next decryption controversy crops up to challenge it.