Ransomware is not going anywhere. It’s still successful and milking money from enterprises, small and medium-sized businesses, and individuals who find that one day all their memories, photos and documents have been encrypted by extortionists. For enterprise, there are solutions that can fight effectively against this epidemic, like SentinelOne. But the battle against ransomware is far from over. Spreading ransomware is a low-risk, high return endeavour for criminals, and with ransomware-for-sale on the Dark Net, it hardly requires any technical skill either.
Some enterprising criminals even sell ransomware-as-a-service, offering to create the malware and collect the funds on behalf of other criminals, whose only task is to find a victim to infect:
Public Decryptors
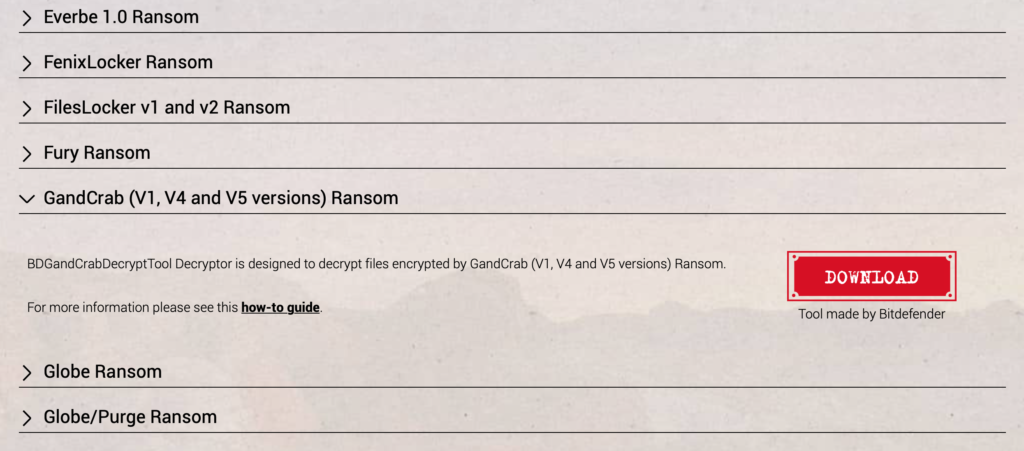
The severity and indiscriminate nature of the threat – ransomware doesn’t care if you’re on welfare or you’re a multinational corporation – has resulted in many free decryption tools. Some sites aim to help victims of ransomware retrieve their encrypted data without paying – and thereby without incentivising – the criminals. Victims of ransomware can upload samples of their encrypted files along with text from the ransom note. Such services are free and promise to provide a link to download the decryption solution, if one is found. There are currently almost 100 public decryptors available, including decryption tools for AutoLocky, CryptXXX, GandCrab, Jaff, Jigsaw, MacRansom and many others.
Unlocking Ransomware Files
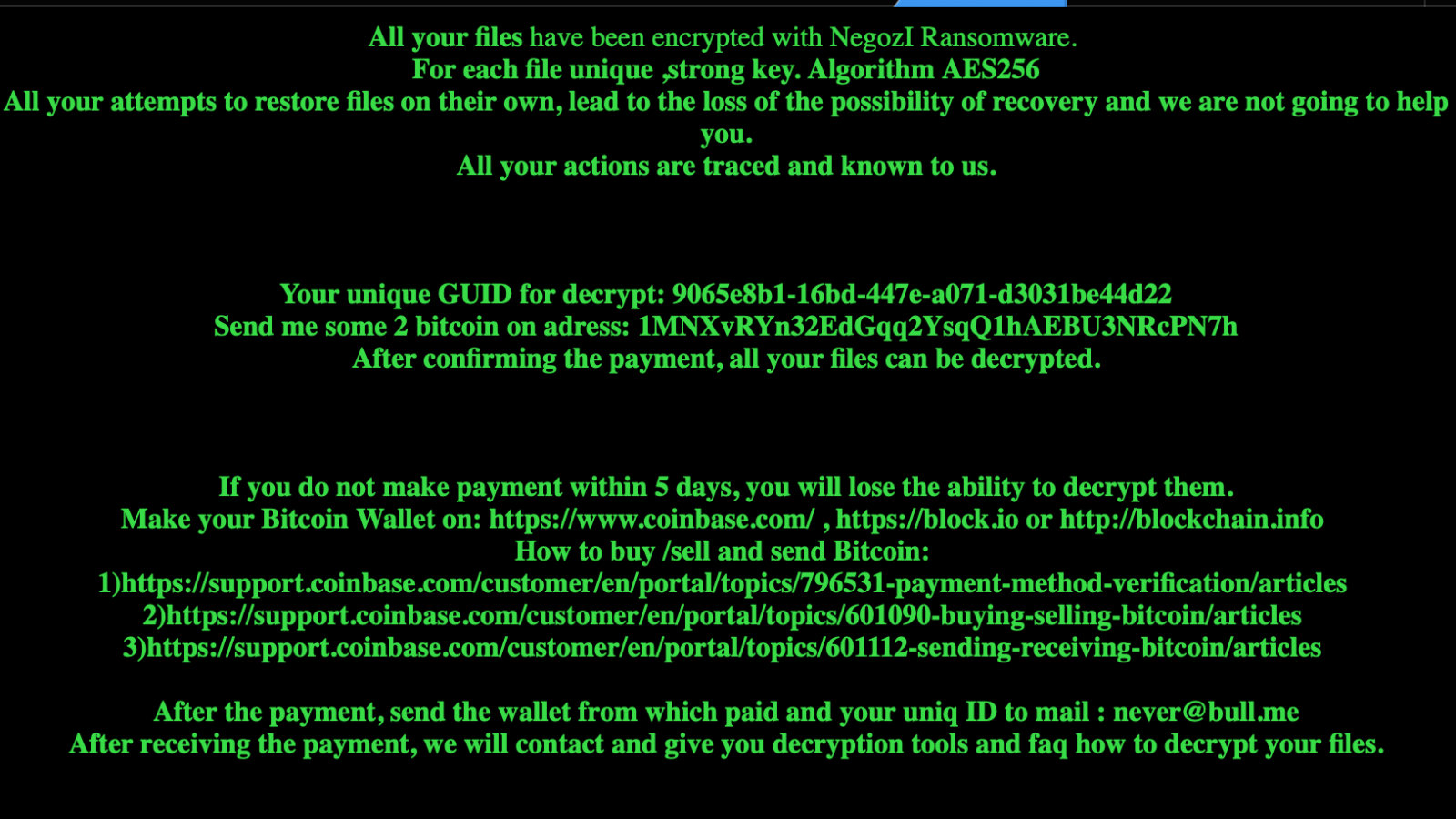
In order to use a decryptor, you typically need to know a little about the ransomware that you’ve been infected by. This can include the name of the ransomware, the bitcoin and email addresses of the criminals and the file extension used at the end of the encrypted filename. Most of this information can usually be found in the “ransom” note, so start there:
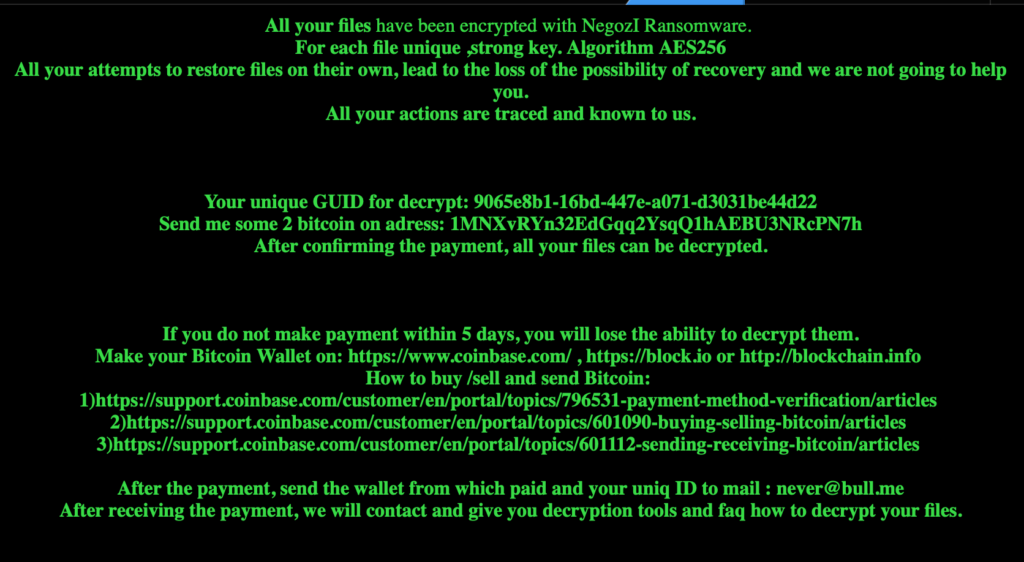
If the ransom note doesn’t have the information you need, some tools will try to recognize the malware from a sample you provide. Remember, of course, if you’re uploading samples of your encrypted files to a public service, ensure you pick a file that didn’t originally contain sensitive information or information you’d be uncomfortable sharing with others.
If You Can’t Find a Decryptor
While decryptors are a great resource, the problem facing victims is the huge variety of ransomware strains.
There are many ransomware variants for which no reliable decryptor is yet available, such as Hermes and Ryuk, and some ransomware strains are just undecryptable entirely. What are your options in that case?
If you have an external backup that was not connected at the time you ran the software, then hopefully you can recover most of you personal files from that, depending on how long it was since you last connected the drive. However, remember to remove the malware before restoring files from your backup, or even better wipe the internal disk and do a complete reinstall of the operating system from your backup.
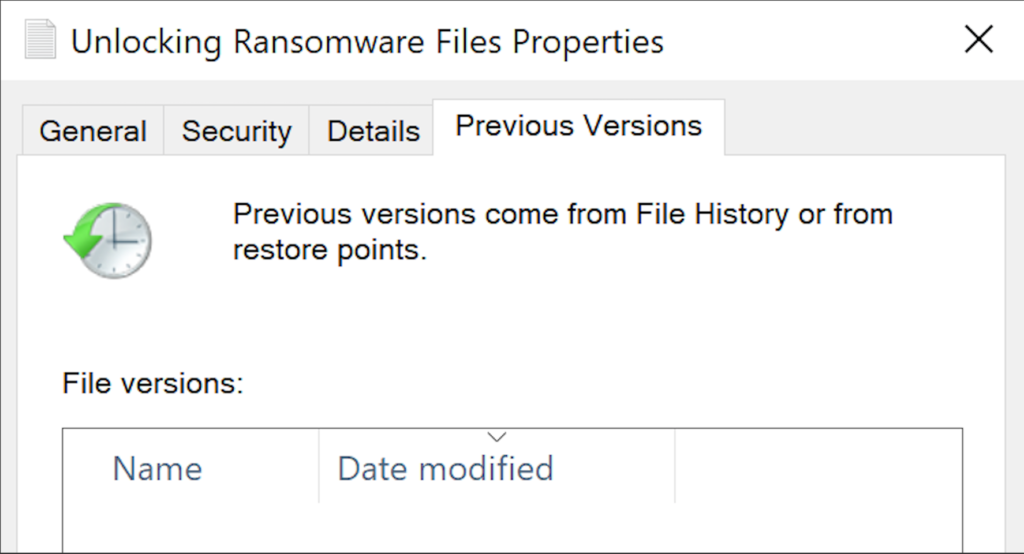
If the backup drive was connected at the time of the infection, or you do not have an external backup, you can check recovery options on your computer. For Windows, you should check whether you can access previous versions of a file, directory or drive by right-clicking on it and either clicking the ‘Restore Previous Version’ or clicking the ‘Properties’ menu item and the ‘Previous Versions’ tab.
For macOS users, check whether individual files can be restored through the built-in Document Versions function or if entire folders can be restored through the Time Machine interface.
Did the Malware Delete All Shadow Copies?
If you didn’t see any Previous Versions in Windows, check to see whether the malware also deleted the shadow copies that Windows automatically creates for backup purposes. Many modern ransomware variants will remove these backups early on in the infection, but it’s always worth checking for several reasons.
The ransomware may be an unsophisticated variant, or it may have failed to complete the removal for some reason. Also, the lack of Previous Versions in File Explorer isn’t always a reliable guide as to whether there are any shadow copies present. These copies are created on all versions of Windows, but they are not exposed by default in some editions of the operating system.
To confirm the status of your shadow copies, open a PowerShell instance as administrator and run the following command:
vssadmin list shadows
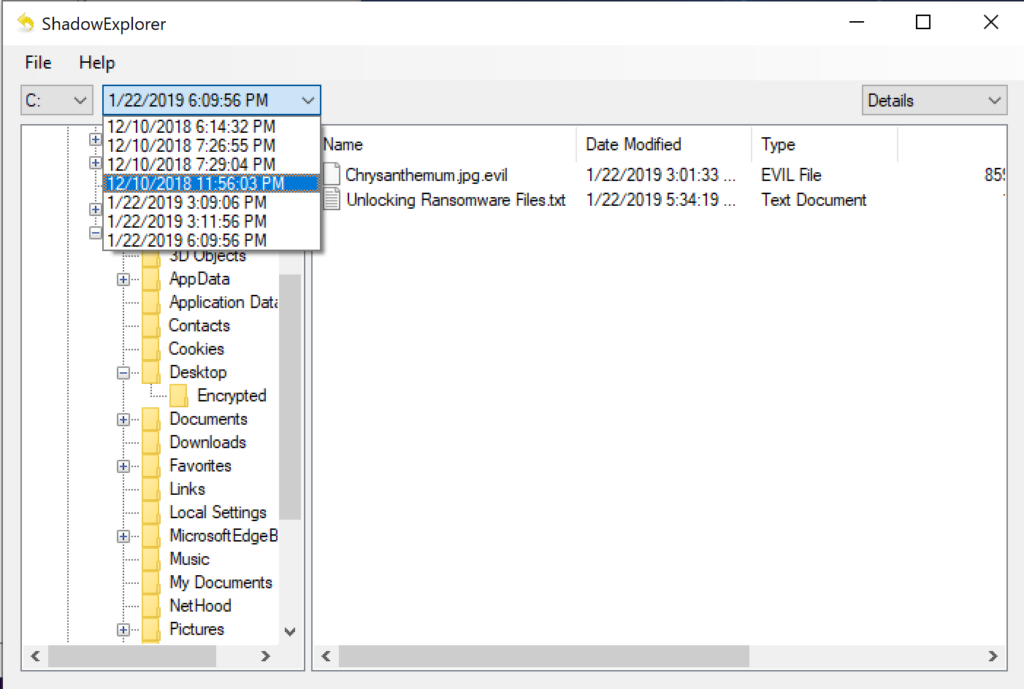
If you see that some shadow copies exist but are not available in the File Explorer you may be in luck. Try using the free utility ShadowExplorer to expose and restore the most recent previous versions of your files:
For macOS users with APFS-formatted disks, you may have access to APFS snapshots (similar to Windows shadow files) even if you do not have a Time Machine backup disk. From the Terminal, use the following command to see if any are available:
tmutil listlocalsnapshots /
In the event that any are listed, you can restore the entire machine to the snapshot through the Recovery partition.
Moving Forward
Of course, these are all “last-ditch” attempts, and it may be that your files are unrecoverable. This can be a hard lesson to take, but at least take away the positives:
- Learn to backup, and backup often.
- Keep backup disks disconnected in between scheduled backup operations. That way, if you do get infected with any kind of malware, your backup disk is protected.
- Use a security solution that is ransomware-proof, like SentinelOne
How SentinelOne Can Help
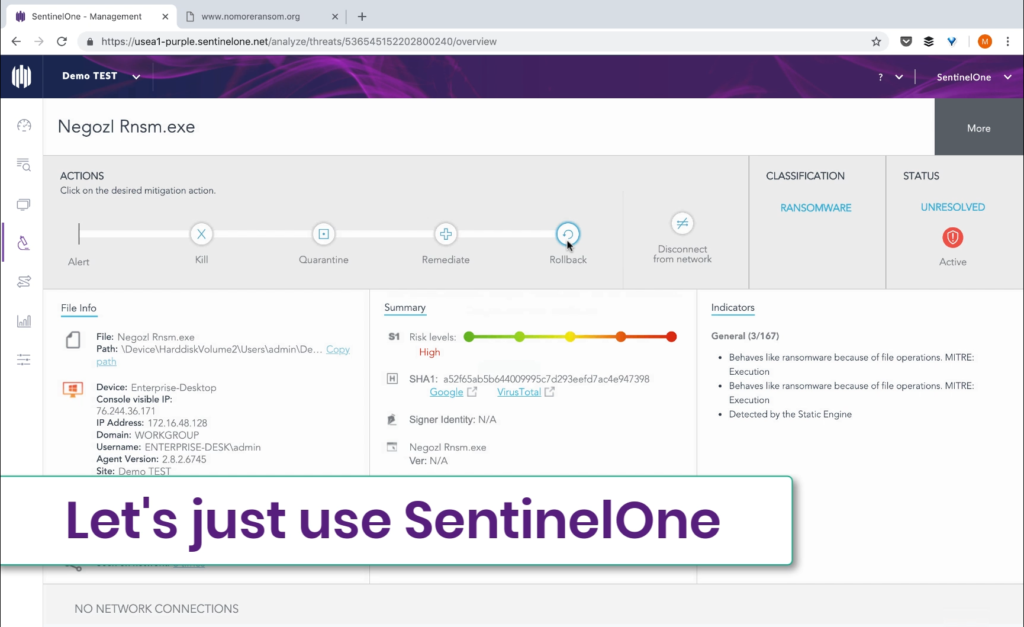
We recently ran a test to see how SentinelOne would handle a ransomware attack by Negozl ransomware, a variant for which there is no public decryptor. To make it more interesting, we obfuscated the sample to eliminate the option of a reputation discovery by the security software. This technique is also used by malware authors to bypass legacy AV – if you add a byte of information at the end of a file, you change its entire signature.
For an extra challenge, we disconnected the network so that any detection by our next-gen AV software could not benefit from access to cloud services. While some vendors tout cloud-based detection, the reality is that malware acts faster on the local machine and can prevent cloud-based AV software from communicating with the sensor on the local device.
The video below shows how the SentinelOne agent performed.
The SentinelOne agent both detected the ransomware and – after we allowed the test machine to execute the ransomware for the purpose of the test – was able to rollback the encrypted files to their normal state within seconds.