Introduction
The SentinelOne behavioral AI engine is aware of every operation on the device. SentinelOne can restore the endpoint to its pre-infected state, without impacting other benign activities on the endpoint. SentinelOne recovers registry keys (often used by malware for persistence), scheduled tasks, and other internal operating system functions. To achieve this, we use Microsoft’s Windows Volume Shadow Copy technology (VSS). This technology is natively integrated into all enterprise Microsoft operating systems. The agent is protecting the VSS to ensure no malicious activity can interfere with the ability to rollback.
The Economics of Ransomware
According to a latest survey, 56% of enterprises suffered a ransomware attack in the last 12 months. 38% had also reported a more significant scale of infection — lateral movement across a network.
Take the case of the city of Atlanta — upon an infection of SamSam malware, they ended up spending more than $2.6 million on emergency efforts. The attackers asked for a ransom of roughly $50,000 worth of bitcoin.
Plenty of enterprises (and consumers) will pay to avoid the disclosure, brand impact, downtime and other impacts of Ransomware
What Ransomware Is Trying To Do
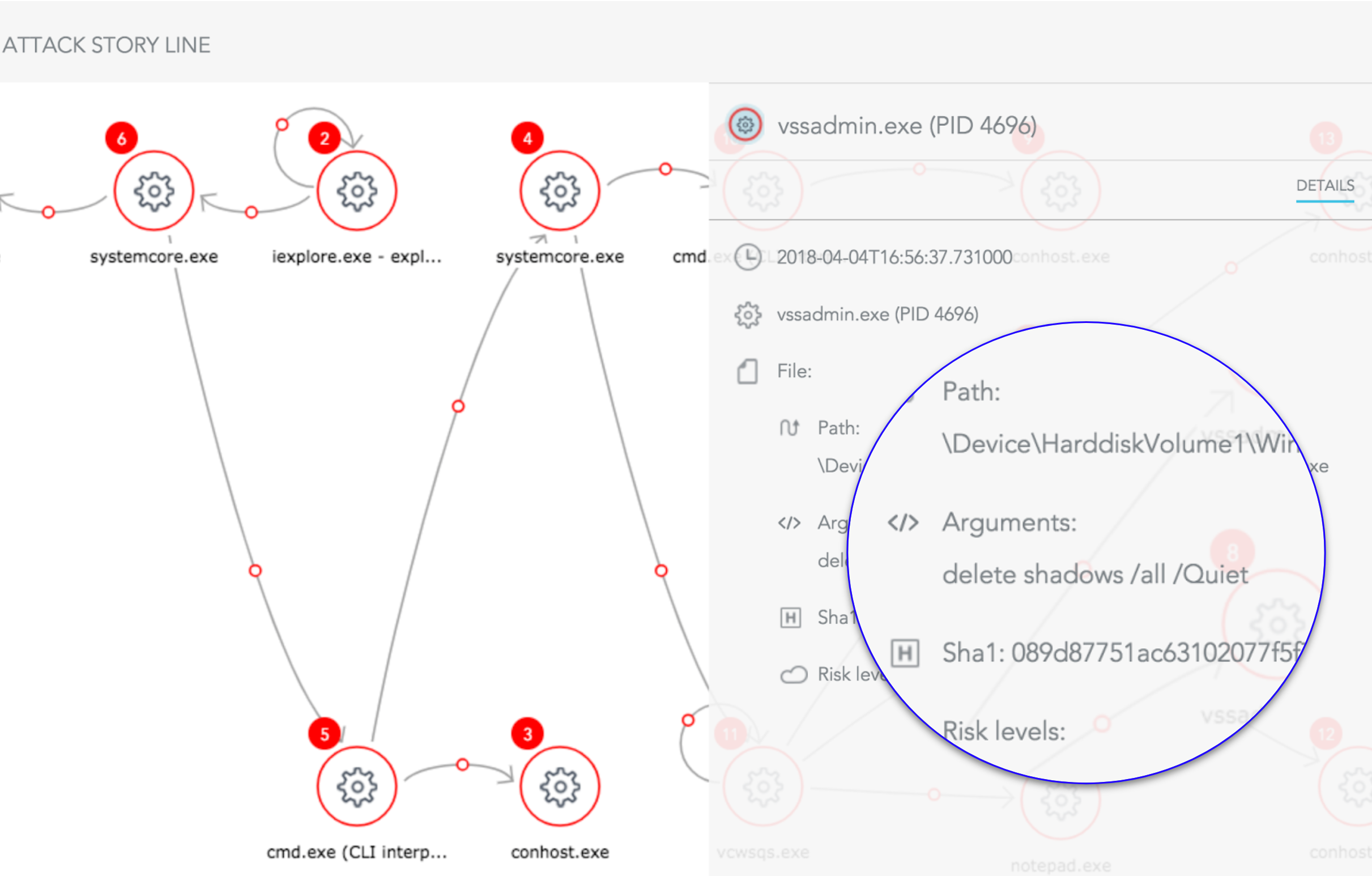
The ransomware space is rapidly changing to spread faster, hit harder and increase its payout potential. New unknown malware pop-up daily and many leverage fileless techniques to bypass the traditional defenses. Cryptowall is one example of such techniques. The malware starts by deleting shadow copies and only then starts encrypting.
“VSS” or ShadowVolume Copy is a Windows OS service that is capable of taking backups, including files that are in use, or open
Here are few common methods seen in the wild:
- Call WinExec (“vssadmin.exe Delete Shadows /All /Quiet”).
- Create the registry key in HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSystemRestore with “DisableSR” as the entry and “1” as the value disable Safe mode, using the “bcedit” utility with the appropriate parameters.
- Disable Recovery Mode and hide the boot menu options (also using bcedit)
- Stopping the Windows Error Reporting (WER) service, and disabling its autostart on future boots. We’ve seen this happen for Windows Defender and other Windows services as well.
- Disable VSS using WMI, to evade detection by AV signatures.
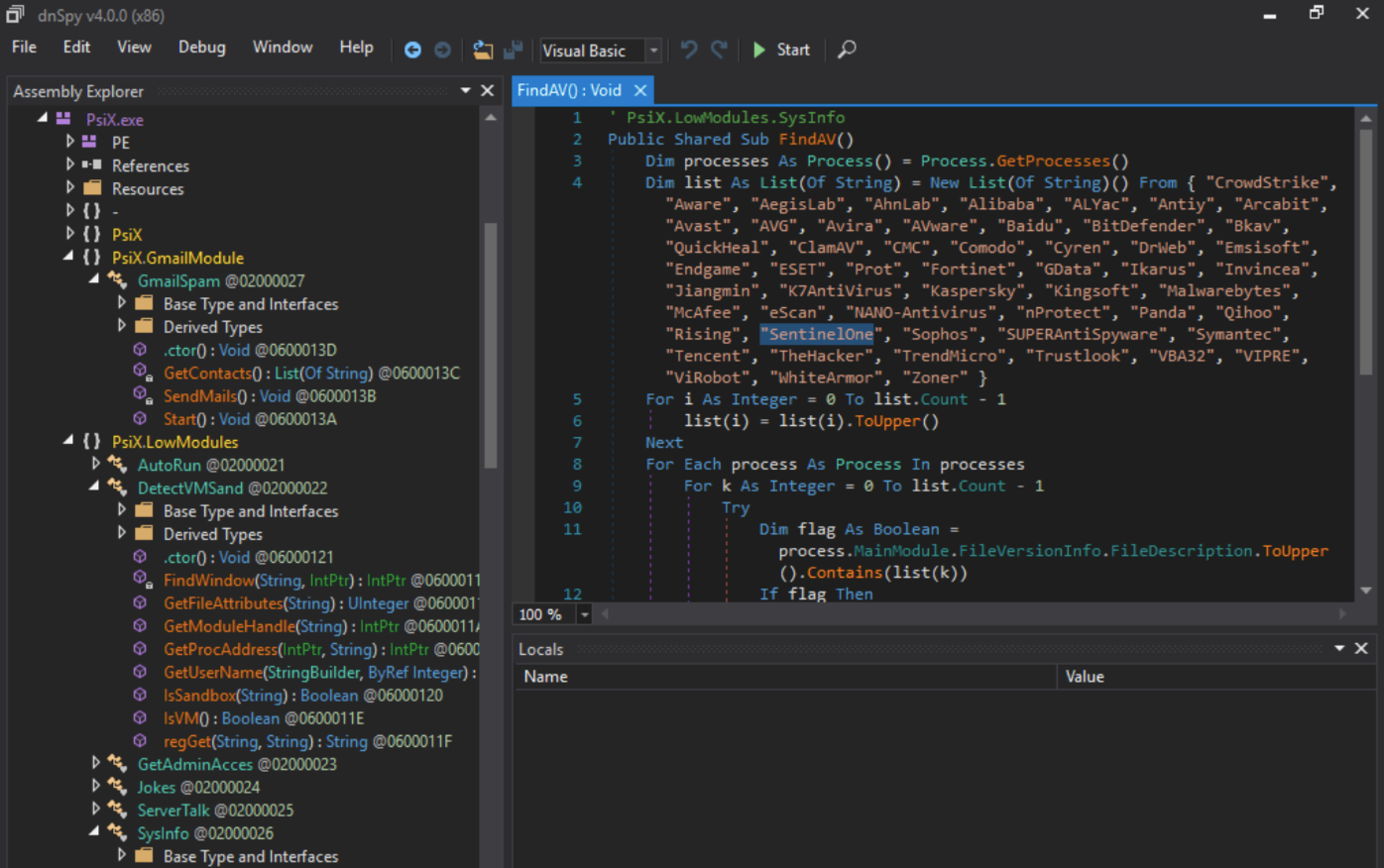
Malware is also trying to disable security products before running their malicious code. One of the common ways they do it is by looking into WSC (Windows Security Center) to find out what anti virus is installed. There are two reasons for this check:
- To bail out if there is a protection that may detect it.
- To disabled the protection.
Anti-tampering — Essential Part of Endpoint Security Products
Reliable endpoint protection should never allow anyone to cripple it. As such, it needs to protect its services, processes, registry entries and others by default; There should not be any master key that can bypass this protection. It also to protect VSS shadow copies, so users can quickly rollback and recover their files.

